@nambi said in Snort Blocking too much.:
@nogbadthebad said in Snort Blocking too much.:
Create a VPN, IPsec or OpenVPN, don't allow access through the firewall so you can view your CCTV cameras.
If Snort is blocking too much don't set Block Offenders and leave it running for a week or two, then decide what rules to switch off before enabling blocking.
Thank You I currently have a VPN for this access but was hoping to leave my mail server and CCTV access open.
Read up on how to use Snort and how to use Suppression Lists. Google is your friend for that. Lot's of tutorials out there on how to do that.
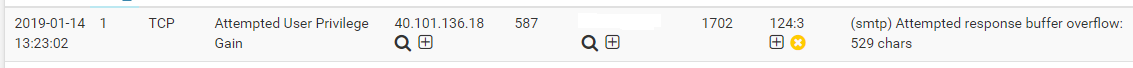
For your mail server and CCTV systems, look at what rules are alerting (and thus blocking). Determine if they in fact represent false positives in your environment. If so, you can suppress those rules using three different techniques. You can suppress the alert entirely for any IP address, you can suppress the alert when the destination IP address is a specific host or subnet, or you can suppress the alert when the source IP address is a specific host or subnet. There are also suppress (also called thresholding) options for only alerting after a specific number of alerts in a given time period have occurred. In short, there are many options for tuning an IDS/IPS like Snort or Suricata. Google "thresholding and suppression" for Snort.
An IDS/IPS is not a package you install and then walk away from and expect it to work without any hassles. Every IDS/IPS requires tuning by an experienced network security admin using knowledge about the unique network environment being protected by the system.