No action on LAN
-
I'm not an network expert but do my own configs on router/firewall products and with good success. However my pfSense is not responding as expected. I think I am missing an important issue.
So as to NOT disturb my operating network, I have taken the WAN directly from another Ethernet port on my modem. Tested this with my laptop to verify that it works and doesn't disturb the existing production network.
Set up pfSense with this STATIC WAN IP & Gateway address. Also set up the LAN with my desired Network address and Gateway & DHCP (3 addresses). This test scenario is isolated from the production network.
I've set up rules for WAN & LAN that pass DNS(53) and have rules for TCP/UDP on ports 80 & 443. However I get nothing on the LAN port except the pfSense Dashboard. I can make changes and have reviewed every setting with no joy... PFSInfo shows data moving in the LAN, yet I cannot get squat when attempting to access a known good IP or domain name.
I've used a Cisco RV-130 successfully for the past 8 years, but want to retire it and get pfSense working for me. I do some web hosting for friends, and play with other web content for entertainment.
I wonder if the MAC address or lack thereof is my issue...
Anyone ?
-
Also set up the LAN with my desired Network address and Gateway & DHCP (3 addresses)
Check: https://docs.netgate.com/pfsense/en/latest/troubleshooting/connectivity.html#lan-interface
-
@ptt said in No action on LAN:
https://docs.netgate.com/pfsense/en/latest/troubleshooting/connectivity.html#lan-interface
Thanks for this...
I couldn't understand the thing about LAN Gateway. It said if it was to access Internet... use a Gateway... Tried it with and without... problem being too many other issues keeping it NOT working.I built a Facebook Page for pfSense 2.6 - Post Install Configuration... Any tips you could add there would be greatly appreciated by many...
I'm heading upstairs to my LAB, and will reconfigure appropriately... wish me luck.
Dave
-
@dhenzler
Printed out instructions and went through all that I could understand. When it got to NAT... I discovered that I had no NAT setup. The instructions were too vague for me to follow.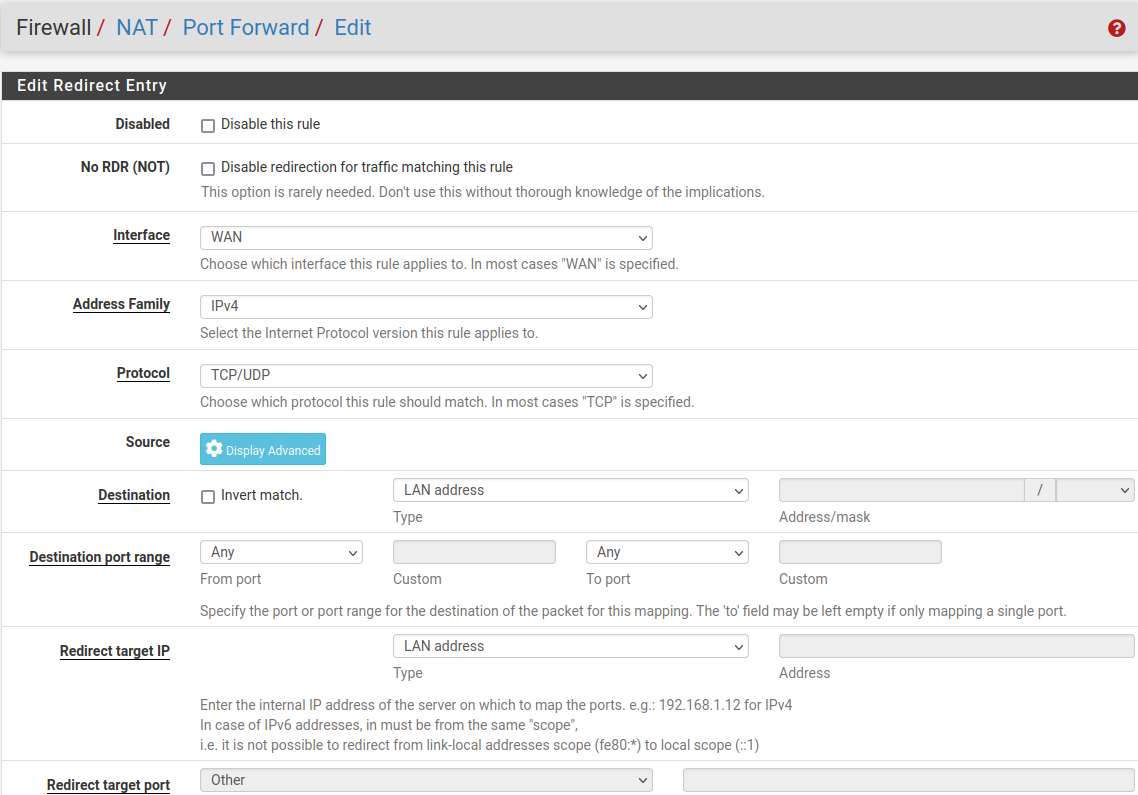
I did not get a good feeling about what was setup.
As well I found a log that says dns is blocked.
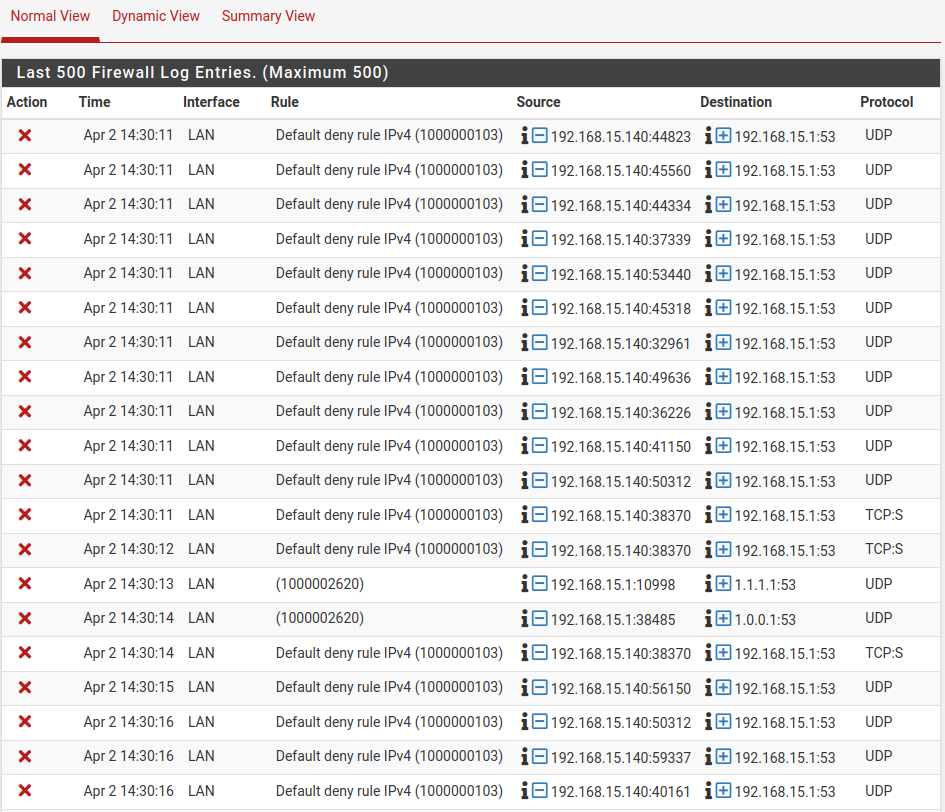
Please help...
-
@dhenzler said in No action on LAN:
Also set up the LAN with my desired Network address and Gateway & DHCP (3 addresses).
A gateway on LAN? Any reason for that?
I've set up rules for WAN & LAN that pass DNS(53) and have rules for TCP/UDP on ports 80 & 443.
Add the rules to the interface tab where the traffic is coming into pfSense.
So you only need a rule on WAN tab if you desire incoming traffic on WAN.As well I found a log that says dns is blocked.
So obviously the rule does not match the DNS packets.
Post the LAN rule set, so that we can verify. -
@viragomann
Thanks for the interest...
As can be seen in the screen shot above a default deny rule IPV4 is preventing DNS from providing an IP. Yet there is no such rule in the Firewall setting for WAN or LAN.Gateway...? It was gone in previous post...
Anyway... would appreciate greatly some specific instructions or screen shots...
Are you using 2.6.0 ?
Thanks...
-
https://www.facebook.com/groups/830911937865469 is a Facebook page I've set up. Hoping to get some other input. I host websites and so use Port Forwarding successfully on my Cisco RV-130. Will set those up on pfSense when I achieve JOY !
-
@dhenzler said in No action on LAN:
As can be seen in the screen shot above a default deny rule IPV4 is preventing DNS from providing an IP. Yet there is no such rule in the Firewall setting for WAN or LAN.
The default deny rule is a default rule built in in pfSense. It's at the end of the rule set, so that it is applied if no other (pass) rule matches before.
You need add rules to LAN to allow out outbound traffic and DNS requests to pfSense.
By default pfSense has an allow any to any rule on LAN so that it works out of the box. You might have removed this one.I host websites and so use Port Forwarding successfully on my Cisco RV-130
So you should set another port for the pfSense web GUI in System > Advanced > Admin to avoid that pfSense is catching packets to port 443.
-
@viragomann
I did a reset last night, and will reconfigure from beginning. Don't know if old rules are cleared automatically. One would think so.
My system is a Proliant DL360pGen8 server. I loaded pfSense 2.6.0 on to a 150G RAID6 drive. So don't know if there is any default LAN as you described.
I'll find out in an hour.... -
@ptt said in No action on LAN:
Also set up the LAN with my desired Network address and Gateway & DHCP (3 addresses)
Check: https://docs.netgate.com/pfsense/en/latest/troubleshooting/connectivity.html#lan-interface
Went through the document twice. Then reset to defaults and set up again to see if something wasn't getting cleared. Still no joy.
WAN is set correctly... STATIC IP, Gateway, Gateway is confirmed Using the correct subnet mask 30.
No Gateway set on LAN. Subnet mask 24.
DNS resolution seems to be correct, but there are settings that are not shown. I'm using WAN any LAN any
Supposedly Outbound NAT is automatically set....
Still DEAD as a DOORNAIL -
@viragomann said in No action on LAN:
@dhenzler said in No action on LAN:
As can be seen in the screen shot above a default deny rule IPV4 is preventing DNS from providing an IP. Yet there is no such rule in the Firewall setting for WAN or LAN.
The default deny rule is a default rule built in in pfSense. It's at the end of the rule set, so that it is applied if no other (pass) rule matches before.
You need add rules to LAN to allow out outbound traffic and DNS requests to pfSense.
By default pfSense has an allow any to any rule on LAN so that it works out of the box. You might have removed this one.I host websites and so use Port Forwarding successfully on my Cisco RV-130
So you should set another port for the pfSense web GUI in System > Advanced > Admin to avoid that pfSense is catching packets to port 443.
What order should the LAN rules (added) be in...
DNS
HTTP
HTTPS
ICMPOrder is critical yes ?
-
@dhenzler
The rules are probed sequentially from top of the rule set to the bottom. If one matches it is applied and the followings are omitted.So in your example, the order does not matter at all, since each rule only matches to one specific port or protocol.
However, consider that a rule with destination = "LAN address" only allows access to pfSense LAN IP, but not to the internet.
So if you want to allow access to internet for HTTP and HTTPS you have to set the destination to "any" in these rules. -
Thanks for the rules info. I get concerned as I read, that I'm backwards and getting worn out changing things around with ZERO results.
I did however open a terminal window on the LAN and I can ping the LAN address, the Public Gateway address, and the Public Internet address. However I cannot get any response from a known IP on the Internet.
DNS resolution seems to be working as I get this...
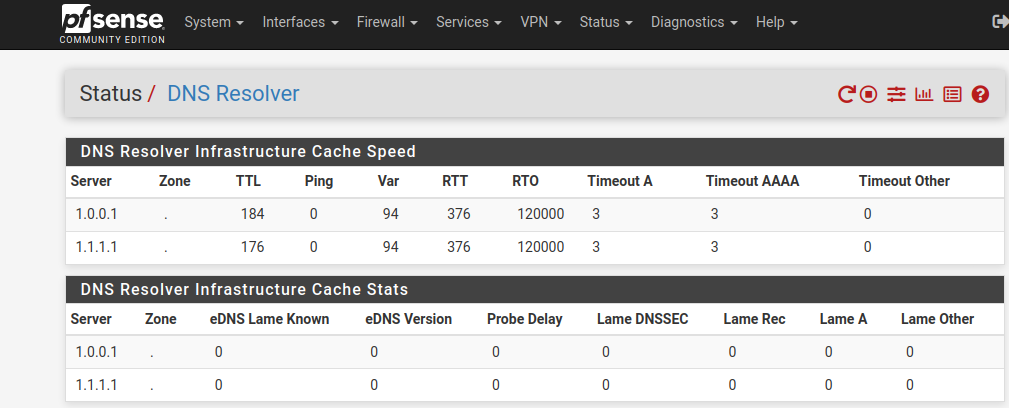
Am worn out with this... I don't understand some of the settings for DNS, and that seems to be the blockage...
If there was an easy way to get someone to finish it for $50. I'd jump at it...
-
@dhenzler
Normally that all works out of the box. Don't see why you're messing with settings before you get it up.To rule out DNS issues ping 8.8.8.8 from a LAN device.
If that's not successful ping it from pfSense. -
@viragomann
It failed to work with my WAN is why I'm "messing" with it...
Determined to figure it out.
I have always started with FRESH install, and didn't add anything not indicated by the manual pages I was sent...However it fails to work. I am connecting to a second port on my modem... it has 4 ports. I tested the port with my laptop, and it worked concurrent with my existing network... so I assumed that it would also work through the firewall. It is my intent to get it operational... configure the Port Forwarding required by my network, and cutover...
Seems like a reasonable path... eh?
It worked when I used my LAN as a WAN and hooked my laptop to a new IP as LAN... worked very welll and FAST.
However that is NOT what I need. I need it to work with existing WAN and LAN addresses so I can swap out my ol faithful Cisco RV-130
-
@viragomann
When you say "out of the box" it makes me think you believe I'm using a Netgate appliance. I'm not... It's a Proliant Server with pfSense loaded on it.So "out of the box" is a very minimal configuration...
-
This post is deleted! -
@dhenzler said in No action on LAN:
When you say "out of the box" it makes me think you believe I'm using a Netgate appliance.
No, I'm talking about the default configuration of pfSense.
When you install pfSense on whatever hardware, it asks you for the WAN interface settings and a LAN IP and network mask.
Then you get into the general setup, where you can state DNS servers.
That's in nearly cases all what is needed to get access from a LAN device to the internet.As mentioned, there is by default a rule on the LAN interface, which allows anything. But you've removed it.
There is no gateway to state in the LAN interface settings. I mentioned that already as your post let me assume you did that. But you did not respond,
So it's really hard to get forward here. -
@viragomann What are your Firewall rules for the LAN interface? "Default deny rule" means there's no rule to pass your traffic. If you created a different interface and then called it LAN and removed the original LAN that would explain the inability to look up any traffic. You could also have only TCP passing and not UDP, too.
-
@rcoleman-netgate
That's not the case... set up was done NON-GUI... set interfaces, and assigned IP'sI'm reading about DNS and hopefully will find the right combination. Being able to ping LAN, and WAN & WAN Gateway has given me some faith that I'm close.
I only get a couple hours a day to work on this, and unfortunately cannot access the Internet while doing it. Oh I can if I use my laptop. But not conveniently. I'm heading up to the LAB area now and will try a couple things.
Getting DNS working will be the ticket.