Block by "Default deny rule IPv4"
-
Hello.
I have network like:
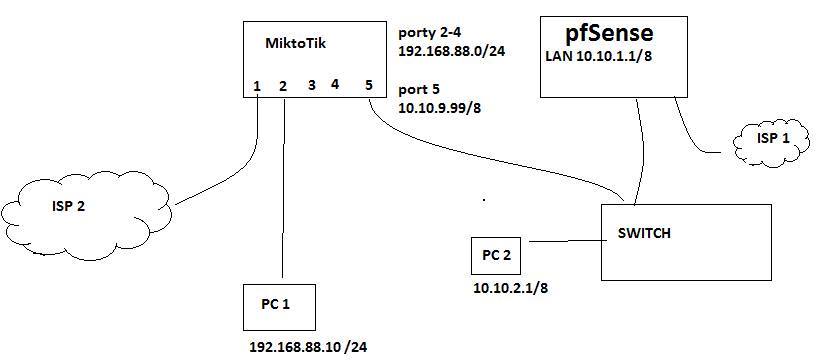
I have problem with firewall.
I can't connect from 192.168.88.9 to 10.10.2.3 (rounting works fine - I cant pinging this host).
I added two rules in firawall.
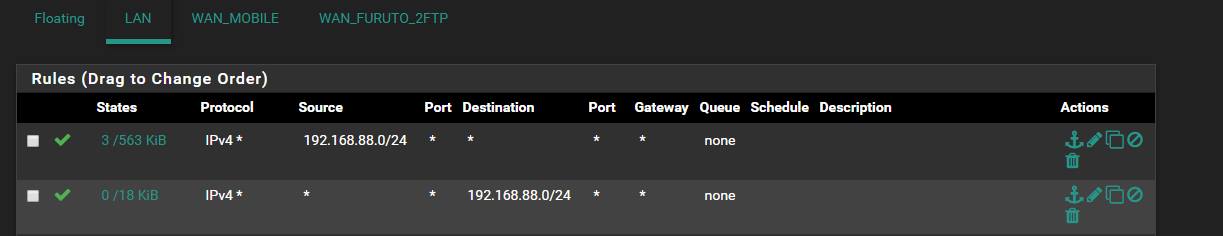
In firewall log i have entry:
block drop in log inet all label "Default deny rule IPv4"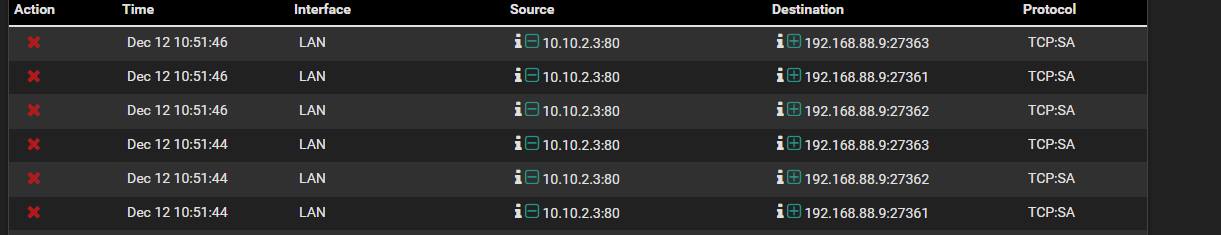
Why firewall blocked this route?
Regards,
Tomasz -
Those are out of state… With such a setup prob have asymmetrical routing..
What are you gateways for your PCs? Why would you be using a /8 that is just nuts..
Why do you not just use 1 router with your 2 different ISPs connected - pfsense can do that for sure.. If your going to use 2 different routers like that you need to connect them with transit network to remove your asymmetrical problem..
-
10.0.0.0/8 - 16 Million IPs? ::)
Overall, you've a strange setup with the two routers. Would be better to use two pfSense in HA with Multi-WAN.
In you setup packets from 192.168.88.9 to 10.10.2.3 won't go through pfSense. So it wouldn't filter the traffic.
Obviously 10.10.2.3 is configured to use pfSense as default gateway and it sends its response packet to it, since it has no route to 192.168.88.9.
So the solution with this setup would be to add a route to the PC2 for the subnet 192.168.88.0/24 pointing to 10.10.9.99.I hope, you don't want to reach all 16 Million hosts. ;D
-
I have static route for 192.168.88.0/24
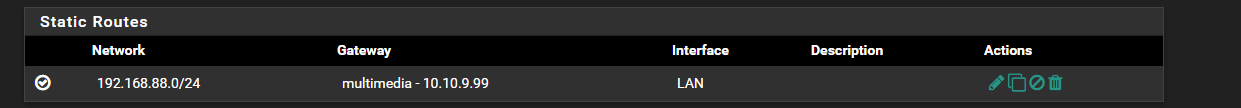
Why do you not just use 1 router with your 2 different ISPs connected - pfsense can do that for sure.
Would be better to use two pfSense in HA with Multi-WAN.
I now, but actually configuration is necessary for some test.
What are you gateways for your PCs?
For 10.10.2.3 gateway is 10.10.1.1 (pfSense adress)
For 192.168.88.9 gateway is 192.168.88.1 (mikrotik adress) -
You need the static route on PC2!
As mentioned the traffic will not go through pfSense.
The blocks you see in the log are the response packets, which PC2 sends to pfSense, presumably cause its the default gateway. However, since the request packet hasn't passed pfSense it has no state for that connection and blocks it. -
you can do routers like you have but you should connect them with a transit so you remove the asymmetrical issues..
So see attached drawing… You then create routes on each router for the other network via the transit. What you have is pretty much your 10/8 being a transit with hosts on it, which gateway that points to wrong end of transit..
When you put hosts on a transit you need to host route on them to tell them which way to go.. So you could put a route on the 10 PC telling it that to get to the 192.168.88 network talk to the mikotek routers IP on the 10 network.. But that is jury rig, the correct way to do what your wanting to do from your drawing would be to connect the routers via a transit network and route the traffic correctly. Then pcs on either network could talk to each other as long as firewall rules allow for it. Without having to do anything special on the PCs themselves.

-
I can't connect from 192.168.88.9 to 10.10.2.3 (rounting works fine - I cant pinging this host).
PC1 will have a default route that points to ISP 1. If it tries to send a packet to anything other than 192.168.88.0 /24, it will forward it to it's default route. This means packets intended for the 10.0.0.0 /8 network will never get there.