Firewall Rule for redirecting single device via WAN not working
-
I have setup a VPN connection with a kill switch but I am trying to exclude single device going through VPN, instead, I want WAN connection to it.
When I set rule in Firewall rules, that the device with specific LAN IP should use WAN as the Gateway, the internet connection in that device drops.
I followed an online guide to set the VPN up but if someone can help me troubleshoot this, that would be helpful.
-
Well if you created a kill switch which whole point is to prevent access direct out the wan, and then you try and have a specific IP go out the wan.. You would have to adjust your kill switch setup to allow this access.
Without any details of your setup this is about as much help as your going to get ;)
-
Well, that's what I am trying to understand. What more details would you like me to provide?
Does this help? (the rule is disabled since it's not working but that's what I tried implementing)
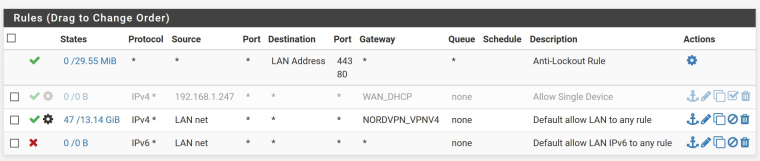
-
And where is your killswitch? That is going to be in the floating rules on the outbound of your wan is it not?
Your typical killswitch would be like this
Firewall > Rules, Floating tab Action: Pass Disabled: unchecked Quick: checked Interface: WAN Direction: out TCP/IP Version: IPv4 Protocol: UDP Source: any Destination: any Destination port range: 1194 Then below that rule: Action: Reject Disabled: unchecked Quick: checked Interface: WAN Direction: out TCP/IP Version: IPv4 Protocol: any Source: any Destination: any Destination port range: anyWith such a rule - no your not going to be able to go out the wan unless it was port 1194. IE your vpn connection
If you want a specific client to be able to go out your wan you would need to put that above your reject rule. And set to quick.
-
There is no rule in the floating rule section. I thought this was the kill switch? Any IPv4 goes through VPN gateway (a kill switch?).
The only other thing I did in Firewall section was the NAT thing. Which was,
-
Select the Manual Outbound NAT rule....
-
Edit "Auto created LAN to WAN"
-
Change the interface option of WAN to VPN
-
Repeat this process for "Auto created rule of ISAKMP - LAN to WAN"
Does above have to do something with it?
-
-
So again without details of how you set it up - The above is a kill switch... If your preventing outbound by messing with your outbound nats then would have to see the details of what you did there.
if you have not outbound nat to the wan - then NO your not going to be able to talk out your wan from a client with an rfc1918 address ;)
If that is what your calling your killswitch, then adjust your nat for your specific client to be able to be natted to your wan IP.
-
Thank you, I think I have found the root cause of the problem.
"If that is what your calling your killswitch, then adjust your nat for your specific client to be able to be natted to your wan IP."
Any pointers/guides/etc., on how/what should I specify based on the settings I mentioned above?
-
Well what I would do if you want to use a vpn is just policy route. if you want to make sure no wan traffic leaks if your vpn is down then just put in the the above sort of kill switch.. There have been multiple discussions of this in the past.. Derelict has made multiple posts about it - the rules I posted above are from one of his posts found on quick search vs putting them in by hand ;)
You shouldn't have to mess with your outbound nat other than hybrid and adding your vpn outbound nat.
Switching to manual is going to more than likely lead to issue in the future as you forget about it ;) and say add a new segment that doesn't work because there is no outbound nat.
There multiple ways to skin this specific sort of cat.. You could also just use the checkbox about no rule on gateway down as full system killswitch if your forcing traffic out a vpn connection via a rule.
-
Hi,
Here is my "killswitch"

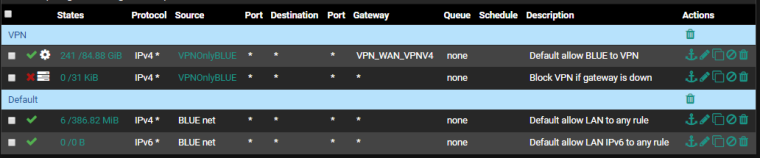
I use IP Alias as source address.