Issue with Openvpn Reconnect?
-
Hi,
i was wondering if someone knows how to add the keep alive on the advance? Many users complain about disconnections, which i thought might of been the internet, but before the company had sophos firewall running the client VPN and they claim that they never had an issue.
i was maybe thinking to add this?tun-mtu 48000;fragment 0;mssfix;keepalive 10 120These are the logs
inactivity timeout (--ping-restart), restartingand a few of these
TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity) Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #62184 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warningsThank you
-
Post all of your settings.
Without any fancy stuff I have Users connected 12+ hours with no problems.-Rico
-
Thanks for the reply, im attaching pictures of my server OpenVPN
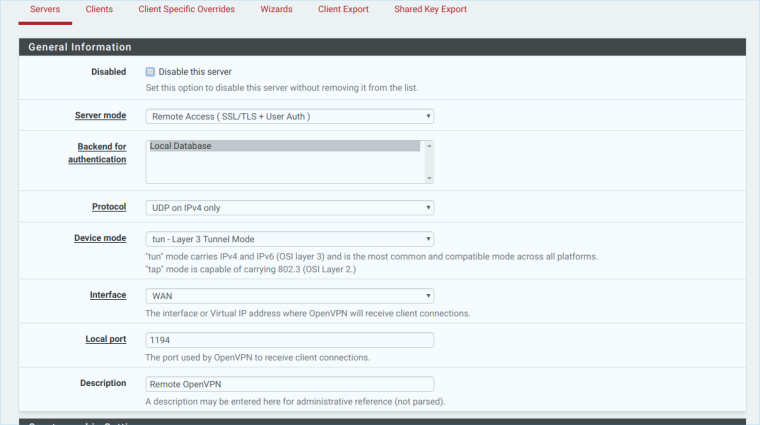
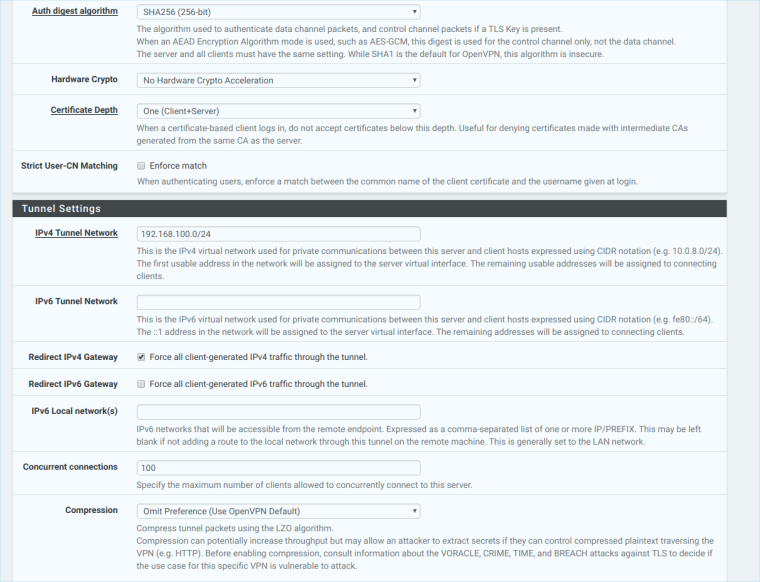
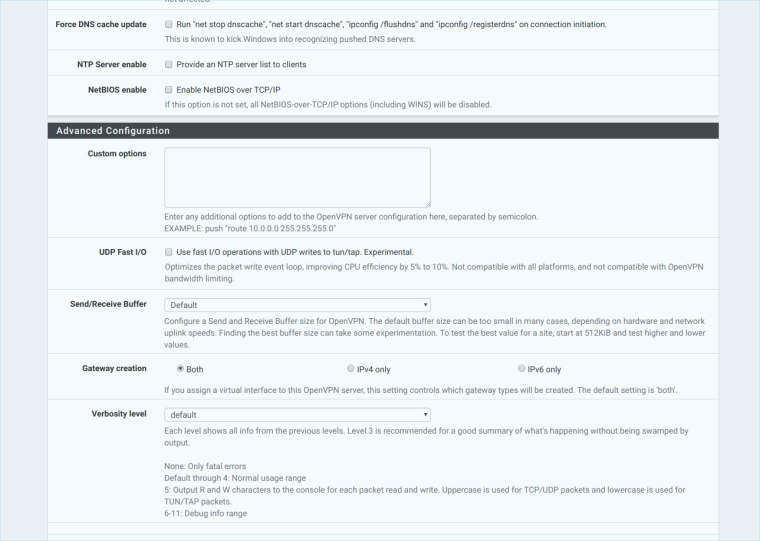
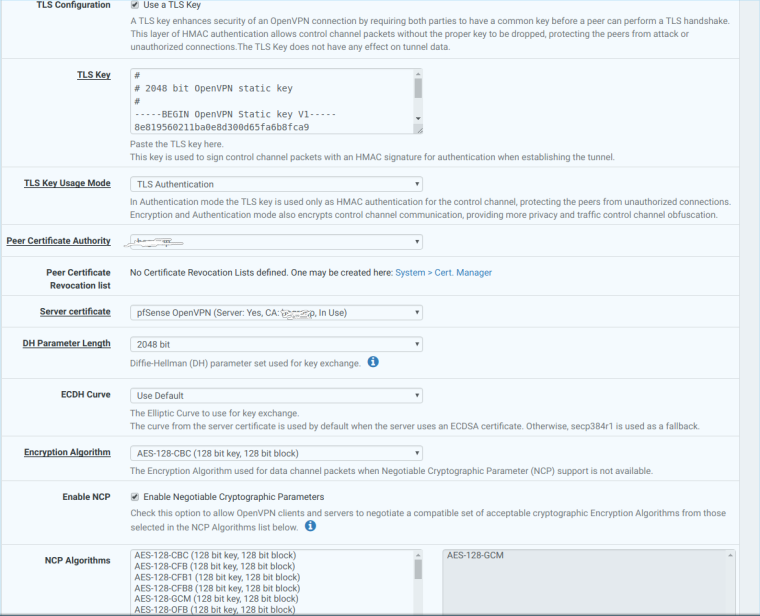
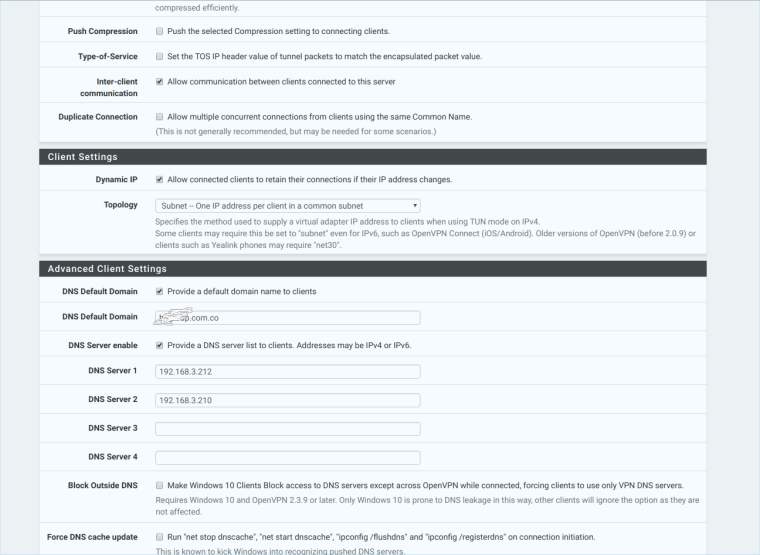
-
You are sure your clients are not using the same OpenVPN account on different devices at the same time? This would bump off existing connections from this user with the Log entry you posted above.
Maybe some flaky internet connection on your server (this would be very bad) or some clients? The problem occurs for ALL of your clients?-Rico
-
Thanks for the reply correct only have on the computer, maybe I would need to implement the keep alive option?
-
Well keepalive 10 60 is the default and already set by pfSense.
-Rico
-
hmm..so everything is good on my part? or how can i demonstrate the issue is not pfSense?
-
Please share your Client Config file.
-Rico
-
Thanks for the reply i download the bundled and the ovpn is this for the client
dev tun persist-tun persist-key cipher AES-128-CBC ncp-ciphers AES-128-GCM auth SHA256 tls-client client resolv-retry infinite remote 181.xx.xx.xx 1194 udp verify-x509-name "pfSense OpenVPN" name auth-user-pass pkcs12 Olympus-UDP4-1194-test.p12 tls-auth Olympus-UDP4-1194-test-tls.key 1 remote-cert-tls serverI was looking at the logs to see and got alots of this
Feb 12 13:26:29 openvpn 18543 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #101914 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings -
Authenticate/Decrypt packet error could be the clock drifted off on one or both sides, wrong MTU or again, flaky internet connection. AGAIN the question, you have this issue with all your clients or only some?
You could also try to switch from UDP to TCP which is not recommended in general for OpenVPN, but can help with unstable connections.-Rico
-
Thanks for the reply, ill keep it right now UDP as for the encryption everything else is good?
-
Well you can‘t do much wrong with the encryption part, everything is fine as long both sides match.
-Rico
-
While TCP for sure is not going to be as fast as UDP.. Huge advantage with it is works over proxies... And if you run it on standard 443 port.. You prob can access it from almost anywhere.. While standard port and UDP not so much..
I just run 2 instances, one on standard 1194 UDP, and than another on 443 TCP. If can not get to the UDP from where I am at - never had issue with getting to the tcp one.
-
Thanks for the reply, so recommended to run UDP better?
-
UDP should be better yeah - unless you can not get to it, then is useless ;)
Takes nothing more than some simple setup to run both. And if you configure the client settings correctly - it will first try your UDP connection, and if can not connect it will then try TCP.