PfSense on esxi 6.7, can get it to work propperly.
-
So i need to edit this one:
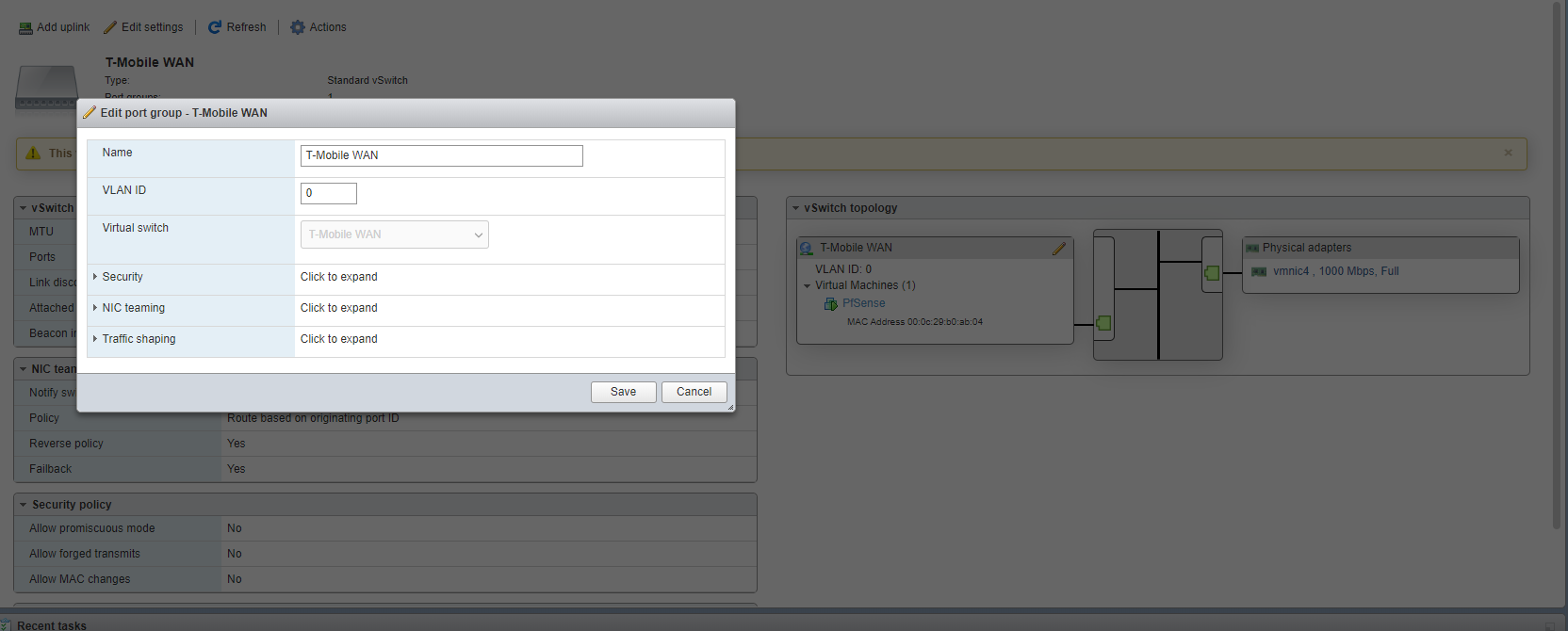 This is the nic port that is comming from the fiber optic.
This is the nic port that is comming from the fiber optic.And can you tell me WHY i need to add VLAN 4095?
-
This is a specific of ESXI. If empty, VLAN are NOT supported. 4095 allows ALL VLAN numbers from the VM. I still get confused about VLAN, tagged, untagged, etc. But this should work,
-
indeed 4095 means that you set your vswitch as a trunk port letting any vlan pass through
-
Yes, this did the trick :)
-
so after a few day's working perfectly.
it now randomly stops working.In the PfSense VM i see this:
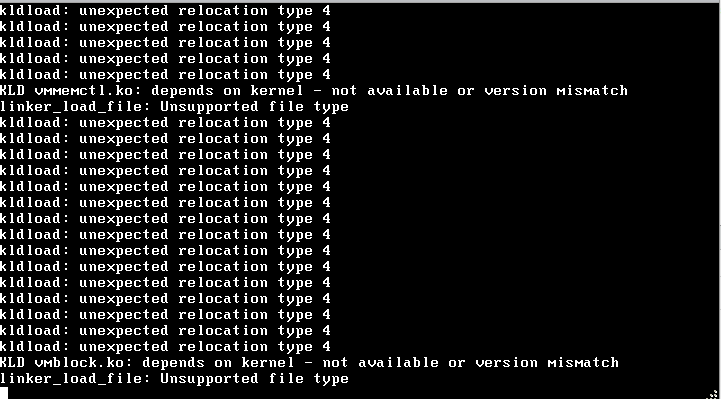
When i reboot the VM everything works again.
What can this be? -
try to reinstall open-vm-tools
maybe do a fsck also -
i have reinstalled the open-vm-tools and nothing changed
what you mean by fsck?And what about the new update?
i'm now on:2.4.4-RELEASE-p3 (amd64)
built on Wed May 15 18:53:44 EDT 2019
FreeBSD 11.2-RELEASE-p10 -
fsck: from console is option 5 and F key ( F: Reboot and run a filesystem check )
and yes, upgrade to 2.4.5 -
ok now i understand what you mean. i just did that a couple of hours ago and it seems to work again.
What about the update?after the update i need to reinstall vm-tools again? and another fsck?
-
nope, no need, make a backup of your config just in case and do the upgrade
-
Still this is not working fine. My internet disconnects every 4-5 hour.
So can you please check my settings and tell me if the are right:First off all, the network settings:
-
ESXI WAN settings: + VLAN ID 4095
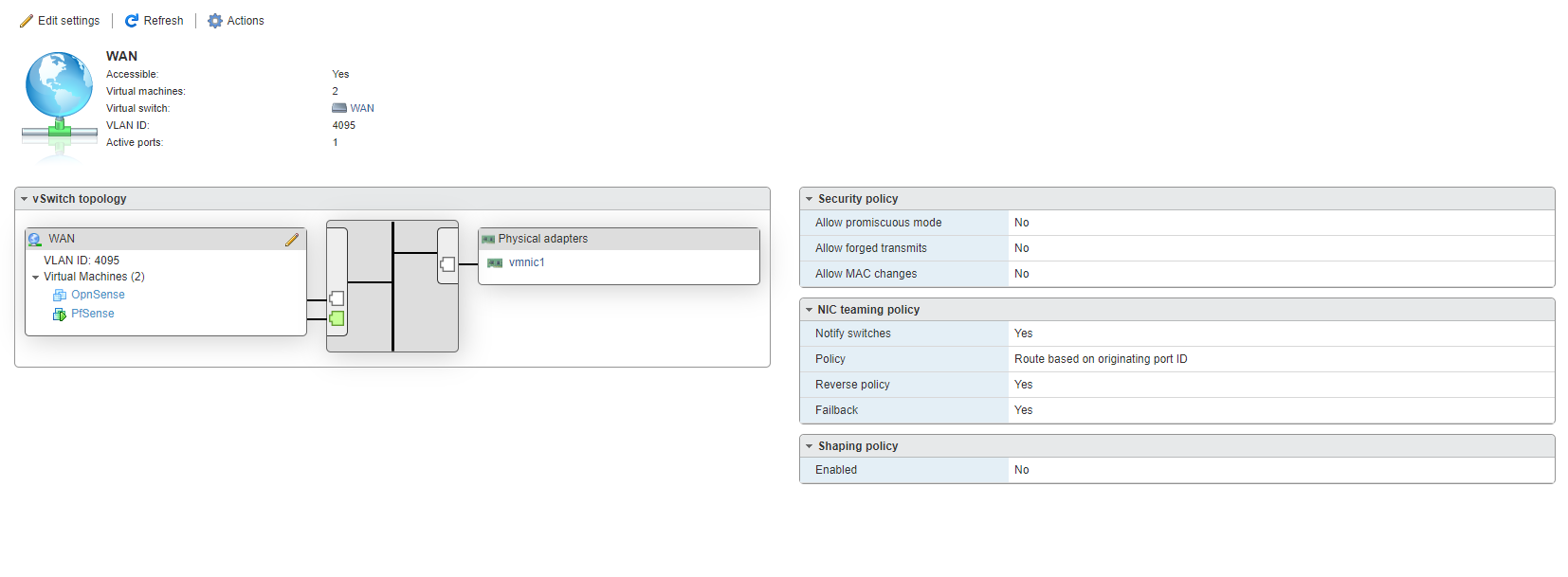
-
ESXI LAN settings:
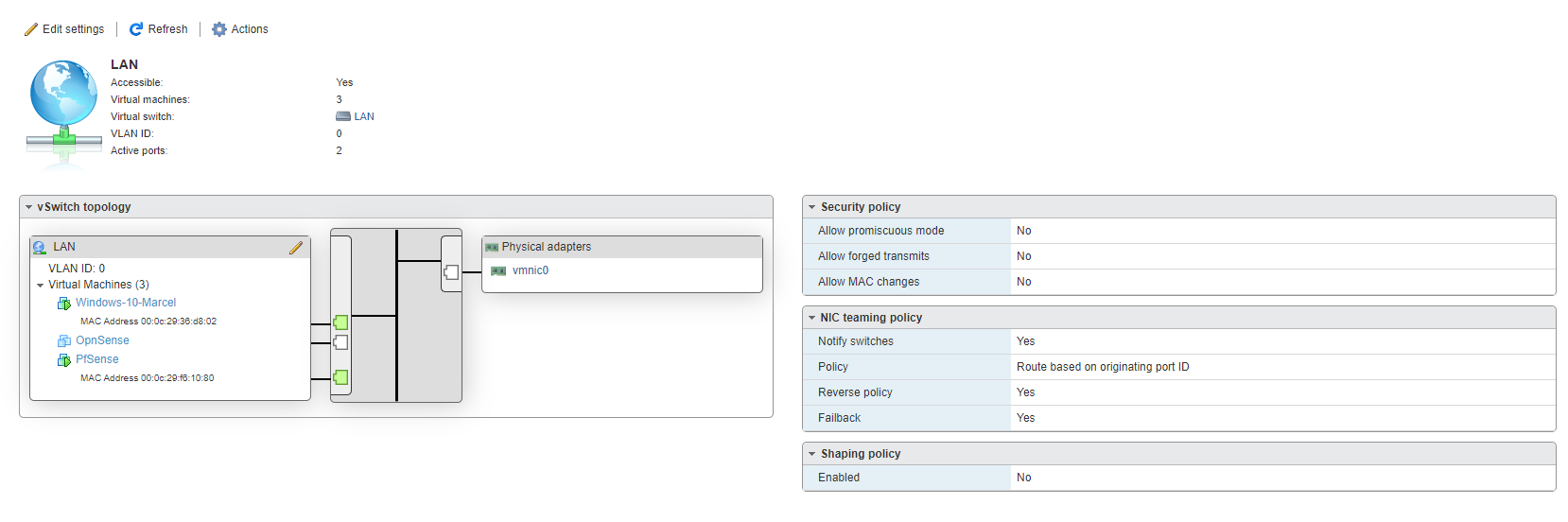
-
PfSense settings:
Cable managment:
WAN T-mobile > WAN Port intel NIC ESXI
LAN Port intel NIC > port 1 into standard network switch. ( not managed )
port 2 network switch > Onboard LAN port of ESXI server for managment.
The rest of the network ports of the switch are 2 Ubiquiti WIFI accespoint, and some computers.As you can see, i also installed OpnSense just to find our of PfSense was the problem.
But also OpnSense has the same problems. -
-
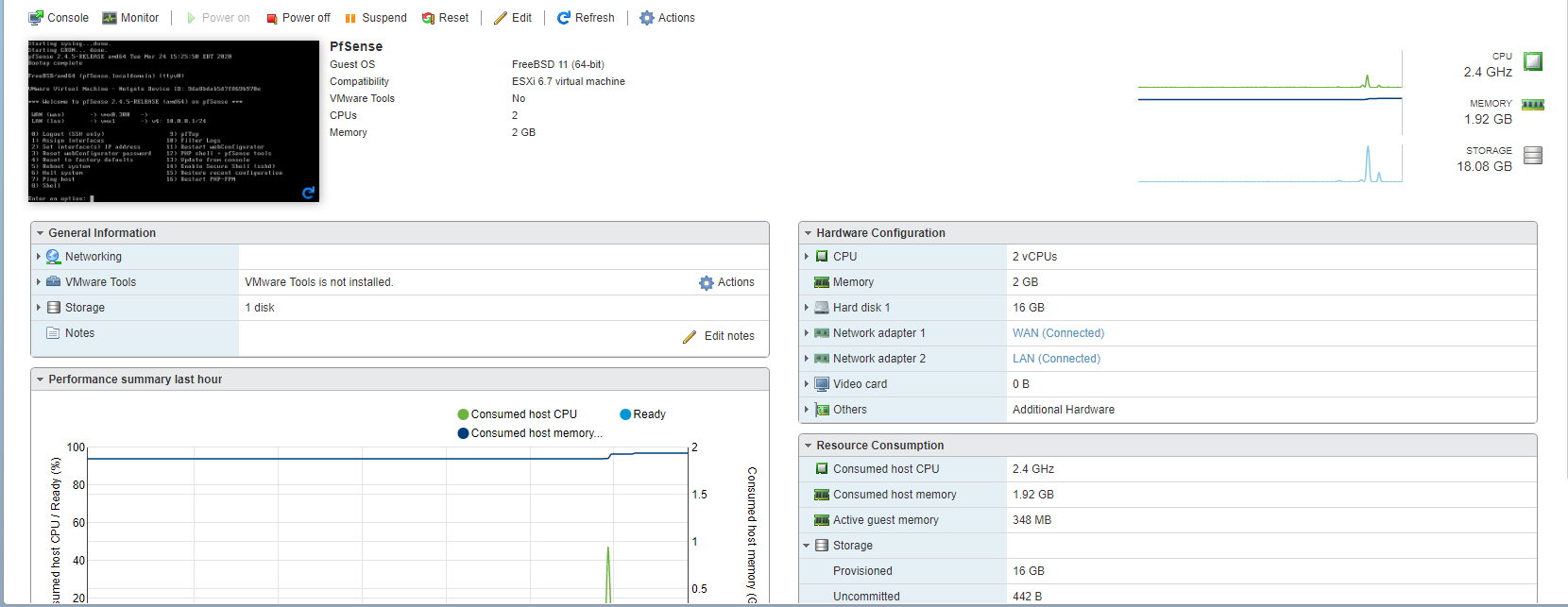
it's ok, was the cable removed during this screenshot i suppose? physical adapters are not green
if you are using igbn (native esxi driver) try to install net-igb (intel driver for esxi)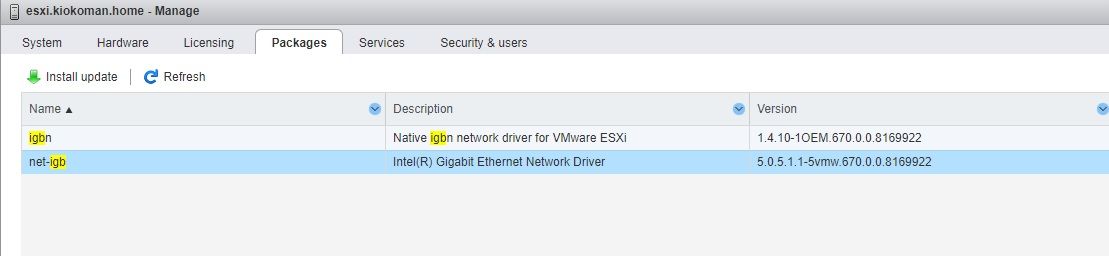
also install open-vm-tools from pfsense packages if you didn't already
-
Yes, the cable is removed otherwise i dont have good internet ofcourse :)
Both the drivers are installed:
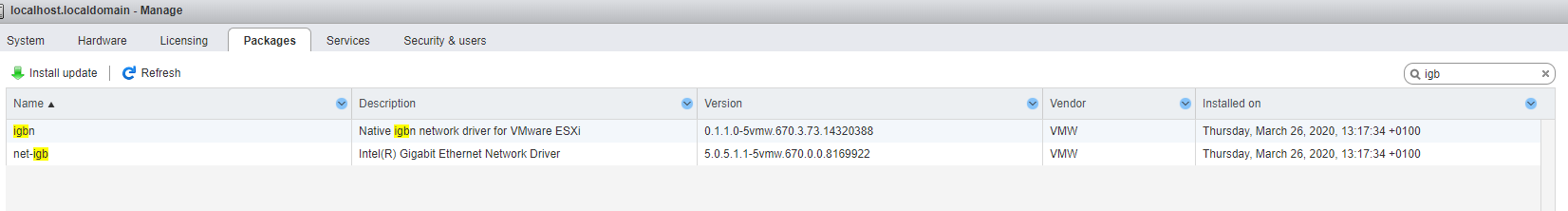
Also the package in PfSense for open-vm-tools is installed.
-
idk, settings are ok, maybe do a backup of your configuration ad reinstall a new clean vm with pfsense 2.4.5 or try 2.5.0
-
Can I get a Teamviewer into the box... then I will have your ESXi/pfsense running in 5 mins
-
@kiokoman
I have tried freshinstall of 2.4.5 and 2.5.0
I have tried backing up and restoring.Maybe te problem is the fact i dont enter a MAC-ADDRESS into the wan port of the T-mobile fiber?
and i leave the MTU also clear?@Cool_Corona
if you can do it in 5 minutes. you can also tell me how ;) -
that would be something specific to your isp

-
So i tried adding a MAC-ADDRESS but then there is no internet at all.
Where in PfSense can i find a log? so maybe i can see where the problem is occurring. -
all logs are under status / system log
what kind of connection is it? pppoe ? dhcp? static or dynamic ip? -
I have a cable modem and for testing purposes I have been switching between a pfSense VM and physical appliances.
Not sure why - but my connection is stable with the mac address used when the connection was first setup. This may be a provider thing...
Either way - if you want your pfSense VM to use a custom mac address on the WAN interface you'll need to allow forged transmits.
I'd also suggest you enable promiscuous mode.
https://docs.vmware.com/en/VMware-vSphere/6.7/com.vmware.vsphere.security.doc/GUID-7DC6486F-5400-44DF-8A62-6273798A2F80.html
and
https://docs.vmware.com/en/VMware-vSphere/6.7/com.vmware.vsphere.security.doc/GUID-92F3AB1F-B4C5-4F25-A010-8820D7250350.html
and
https://wahlnetwork.com/2013/04/29/how-the-vmware-forged-transmits-security-policy-works/
For good measure also allow mac changes.
Once its all working... you can revert these settings until you know exactly which setting breaks your environment.
To sum this up: on the WAN vSwitch and Portgroup you need to:
-
Allow Mac Changes
-
Allow Forged Transmits
-
Allow Promiscuous Mode
-
In pfsense - on the WAN Interface use a Mac Address that has previously worked with your provider
-