Port tagging on APU2?
-
@bingo600 I removed the custom DNS addresses from the DHCP server and that made no difference. What I am wondering is why the SG-1100 has a switch submenu in Interfaces to enable port tagging, and this APU2 does not. Might that be the crux of this?
-
@orangehand said in Port tagging on APU2?:
@bingo600 I removed the custom DNS addresses from the DHCP server and that made no difference.
I expected that , as your DNS servers are on the INET , and INET can't be reached.
What I am wondering is why the SG-1100 has a switch submenu in Interfaces to enable port tagging, and this APU2 does not. Might that be the crux of this?
Nope .. I'm running a Unifi on a pfSense wo. switch menu , and JKnott does the same (see further up).
Your tagging is working , since you get a Guest Ip address (in Vlan 20)
Post a picture of your DHCP Server settings for Guest
You don't have any group or floating rules , do you ?
-
@bingo600
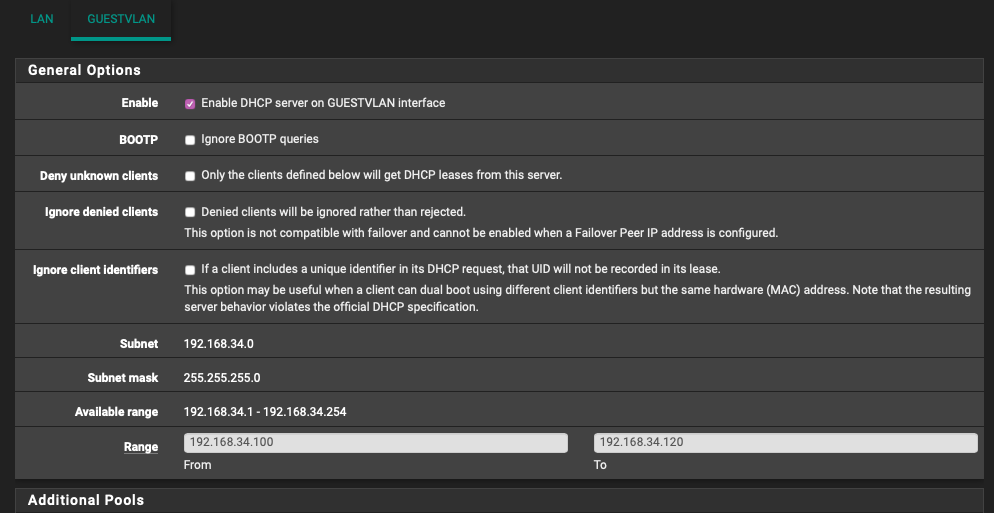 Anything not shown is default
Anything not shown is default -
Then something is fishy ....
Did you remove the Lan block rule , and tried to ping lan IF and maybe a lan device.
Edit:
Now that you have removed the 9.9.9.9 & 1.1.1.1 as DNS , can you resolve DNS now?
I mean what does ie. ping dns.google.com show ?
Does it resolve like here , where it resolves to 8.8.4.4
$ ping dns.google.com PING dns.google.com (8.8.4.4) 56(84) bytes of data. -
@bingo600 Yes. I can ping devices on both subnets from the guest subnet when that rule is disabled
-
-
@orangehand
Then def-gw ought to be set correct.Can you ping the WAN IF ?
How is your outbound NAT set ?
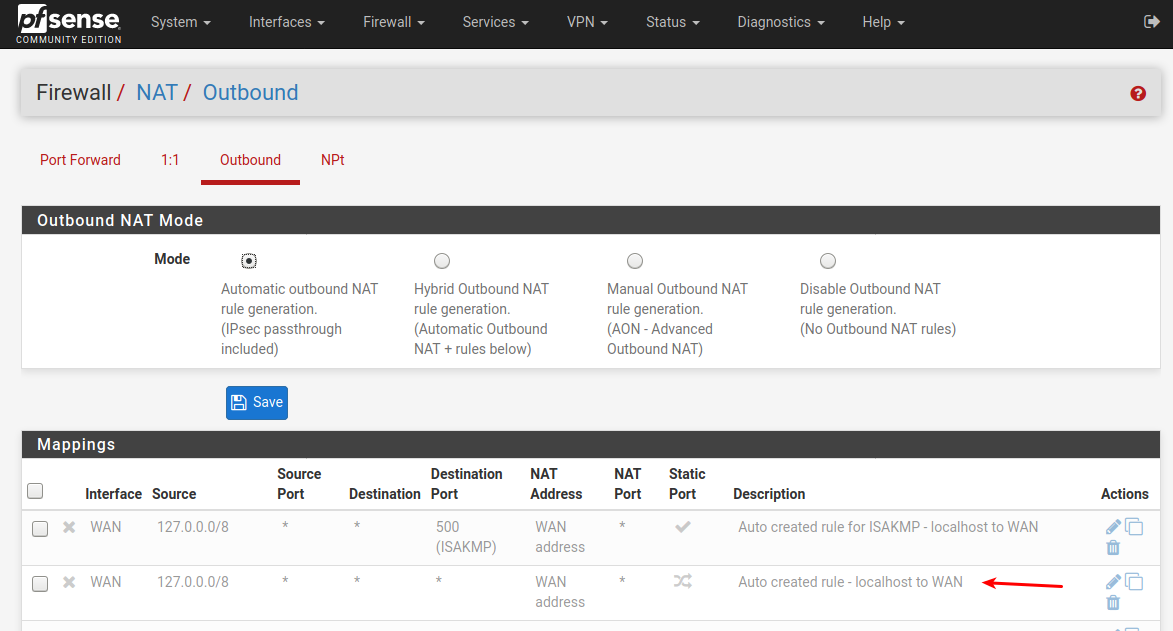
Do you have "Auto created XXX to wan" for all the interfaces ?
Especially look at Guest , if it's missing there
Maybe post a screenshot
-
Did you get this solved ?
-
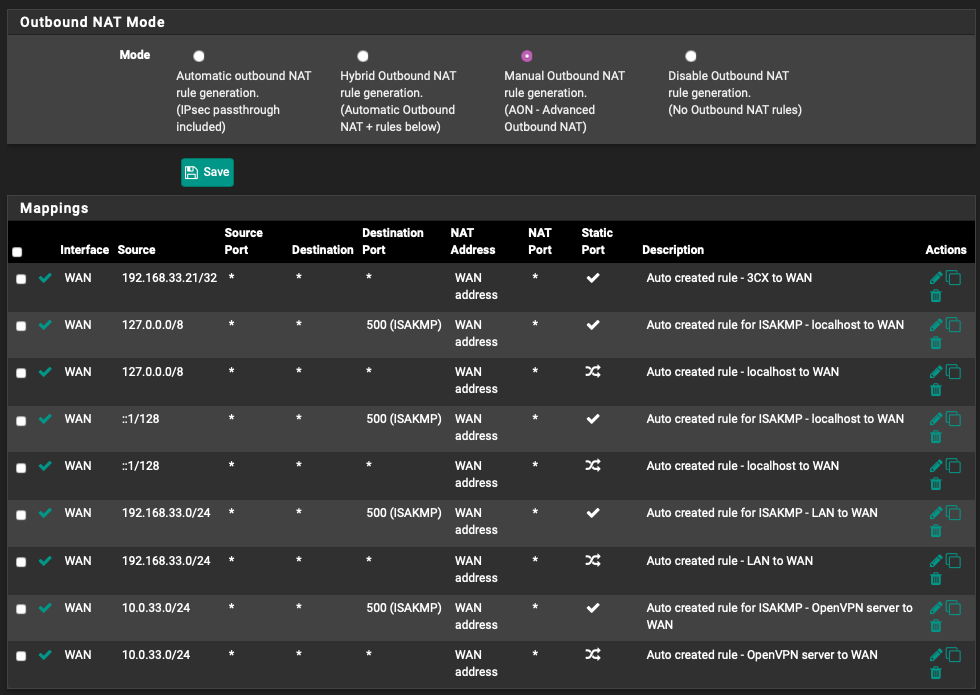
@bingo600 No. Here is the Outbound NAT screenshot:
-
@orangehand said in Port tagging on APU2?:
I need to go out to dinner now. Any further thoughts much appreciated!
I like pizza.

-
@orangehand said in Port tagging on APU2?:
On the Sg-1100 I set up yesterday there was a switch submenu in Interfaces where you added the tags. On my APU2 box there isn't a switch submenu so where do I do the tagging?
Just for anyone else wondering: SG1100, 2100, 3100 and 7100 have built in Switch chipsets! Those ports are actually switched internally that's why they have a special pfsense version from Netgate to include the config of said switch chip. You don't have that on any other hardware!
Other than that @JKnott and @bingo600 seem to have things under control, wouldn't want to intrude and confuse everyone :)
-
@JeGr Thanks for that! So in the absence of that switch config, how does one tag the lan interface so that VLAN traffic flows through it?
-
If you don't have a managed switch, you tag not only the LAN interface on pfsense, but also on every device you want to use the VLAN. This is easy enough to do with computers, but many other devices don't support VLANs.
These days, go with managed switches. They're cheap, but avoid TP-Link.
-
@JKnott all my switches are Unifi
-
I have a Unifi AP and a Cisco switch.
-
I have an APU2 and a unifi ap as well. I can confirm the APU2 and pfsense VLANing does work since my unifi main wifi network is a VLAN coming from pfSense. However, I also had issues creating a seperate wifi VLAN with the unifi. I think it's mostly my not understanding the unifi stuff or something odd with the unifi since at one point I couldn't even get it to work at all after what I thought was a small change. I had to completely reset it.
I don't have a unifi switch however, mine is a Dlink. I would say make sure all your unifi software and firmware is up to date. Not sure if this video might help? His videos are very good and it sounds like exactly what you're trying to do.
https://www.youtube.com/watch?v=LNAAfja_ZOYEdit, it also might be worth making sure your BIOS is up to date on the APU2 or at least check the release notes to be sure your not missing some fix that could be related to this.
-
Yeah, the Unifi config is a bit strange. However, working with VLANs is fairly simple. Just make sure your VLANs match across all devices, including any switch you pass through. I have my guest WiFi on VLAN 3, so I configured that on my AP, switch and pfsense.
-
Why do you use Manual nat , and not Hybrid ?
It seems like you are missing outbound nat for your guest lan : 192.168.34.0/24
Re: Switches & stuff.
Since you can ping devices on your Lan , and you get ip addresses on your guest WiFi. I'd say your switch & Vlan works fine.The reason you can't go on Inet from WiFi , seems to be that you are not doing outbound nat for that /24. And trying to send an RFC1918 ip to you ISP would not lead to anything good.
-
@bingo600 said in Port tagging on APU2?:
Why do you use Manual nat , and not Hybrid ?
Was wondering this also.
@bingo600 said in Port tagging on APU2?:
It seems like you are missing outbound nat for your guest lan : 192.168.34.0/24
Good catch.
-
Not that it matters "much" .. nitpicking
But your 3CX NAT rule at the top, is covered by the 192.168.33.0/24 NAT rule further down.@Raffi_
Thnx
This was a "tricky one" ..
I'm 99% sure it's solved after OP makes the missing NAT rule./Bingo