Removing 127.0.0.1 as DNS?
-
Hi all,
I want the DNS servers to be two internal servers and two external servers. However, even changing the DNS servers in the general setup is still showing 127.0.0.1 as the first DNS server in /etc/resolv.conf.
What am I missing to get this done?
-
This is where you would tell pfsense not to use itself for dns.
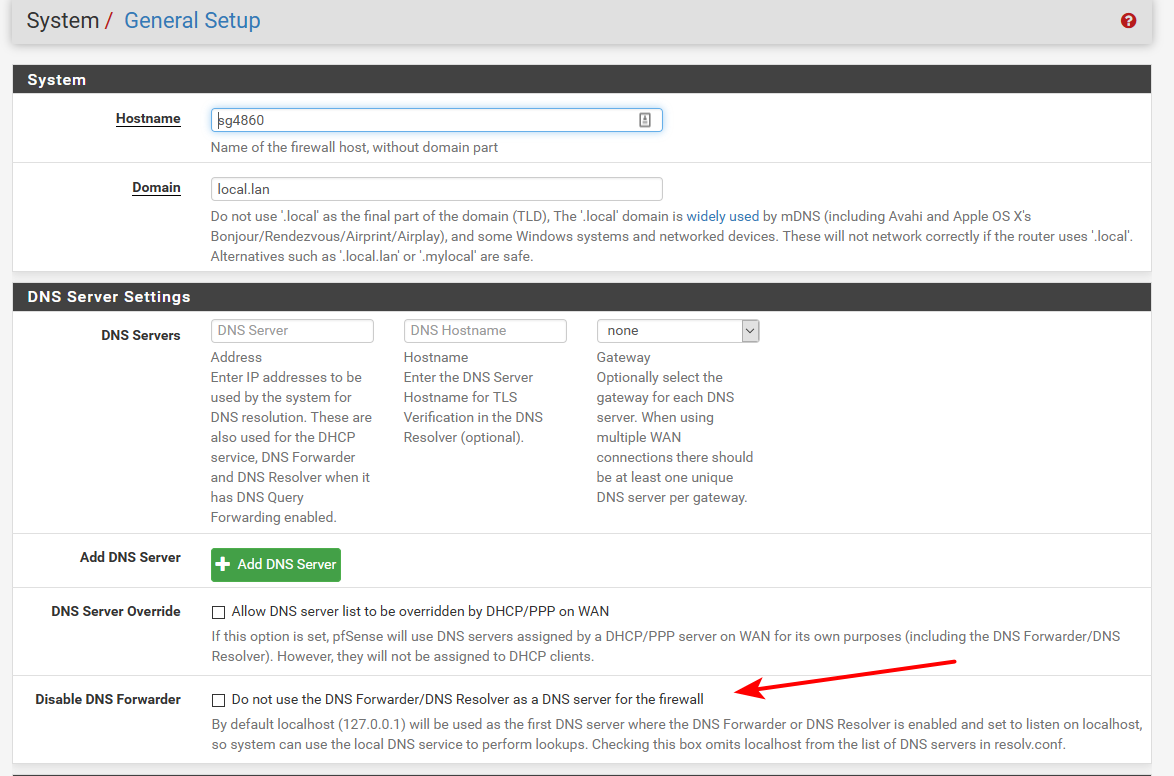
But I think you are not understanding how dns works if you want to point to 2 external and 2 internal.. What if it asks external for your internal domains, or aks your internal domains for public stuff.
Pfsense should really just point to itself.. And then you can setup domain overrides to use your internal NS for internal domains. And then either let it resolve as it does out of the box, or setup forwards for stuff that is not your local domains.
-
To be sure that I'm not missing something, I have two internal servers for resolving internal hosts but the two external ones are to resolve public stuff if those are ever down.
-
Doesn't really work that way.. But ok..
You can never really be sure which NS are asked, and if you ask something that you get back any response at all, say a NX.. Its not going to go ask the next server.
If you want to ask your 2 internal servers, and have them forward for external that is fine. But setting any client be it pfsense, some pc, or server to have the possibility of asking ns that can not resolve the same stuff - your asking for issues.
-
LOL, I may be a bit over my head in this but I'm not even sure where to start explaining.
I have public DNS servers for everything including mail servers and stuff like that but internally, we need to also have DNS resolving local hosts. Most hosts have the public servers as their dns but all of them also need to know about internal servers.
Therefore, on some hosts, I've started adding dns resolve like
nameserver 10.0.0.2
nameserver 10.0.0.3
nameserver <a public IP>My thought was that the internal dns servers can resolve public stuff but when it comes to mx servers and stuff like that, the hosts would try local first then public second.
The one thing about DNS, based on your input that I never knew then is that hosts will not use hosts in some order. I always thought they would try the first in the list, the second if not found, the third if not found.
-
@lewis What I did that works well, with two Server 2016 VMs that provide DNS and DHCP internally, is have DHCP hand out my internal DNS server IPs to internal clients. Clients don't need any other DNS than my servers. Anything those two DNS servers can't resolve, they forward to PFSense, which resolves by going to root servers. I only have certain ports open from the clients and servers to the internet, and 53 isn't one of them. PFSense does just fine resolving using root servers, no need to give my browsing data to some third party. If you want to use a third party, just check that 'Disable DNS Forwarder' and input the public DNS you want to resolve for you in the DNS Servers list. In case something odd happens and clients start hitting PFSense directly, that's where the domain/host overrides on the "Services/DNS Resolver/General Settings" page come in to play.
-
@lewis said in Removing 127.0.0.1 as DNS?:
nameserver 10.0.0.2
nameserver 10.0.0.3
nameserver <a public IP>And that is not how to do it - unless what you want is problems! ;)
Point your clients to your internal, have your internal either forward to public or pfsense, and let pfsense resolver or forward to public.
The issue with your setup, is you can not be "sure" your client doesn't ask public for something that is internal. You can't.. A client doesn't only ask that public one if both internal fail.. And if it asks 10.0.0.2 for something that it doesn't resolve and it sends back NX, its done, etc. If it happens to ask public for something that is internal and gets back NX, its done.
@Tzvia is doing it correctly. Been working with dns, really ever since there has been dns ;) And what your doing is the most common mistake made.. And it makes me sad really...
@Tzvia I think you meant to say disable resolving, and forward. If you do not want pfsense to resolve and to forward to say google..
-
@johnpoz Makes you sad, that people are always learning? Kind of an odd thing to say.
Anyways, thanks for the input, it was helpful. I do not want/need DNS forwarding and Disable DNS Forwarder was what I needed to do.
-
No not that people are learning, I love that - and why I am here to be honest to help people learn. What I meant is its sad is I see it so much, when it really everyone that deals with dns should understand this.
Especially in setups where its not just some home user trying to setup his first dns..
Kind of how wifi has been around for 20 years.. And still people that for sure should understand that the Numbers they put on the box are not real bandwidth that you will see. But every day - all over the net hundreds if not 1000's of post.. Why am I not seeing 1300mbps - my router says it can do 1300mps right there on the box ;)
Its not like this information is not easy available. These people are not learners ;)
Think of it this way - its like your a 4th grade math teacher, and your students don't know that 2+2=4.. They should know this already ;)
I get it, not everyone here is in 4th grade, maybe they are just starting preschool when it comes to this stuff. But if you are to the point your running your own internal DNS, not just your soho router ;) I would of hoped you would of picked this information up by now.
I do not want/need DNS forwarding and Disable DNS Forwarder was what I needed to do.
That is not even on by default.. Had you turned it on? Out of the box pfsense is a resolver. Not a forwarder - for it to forward.. Takes effort by the user.. You either need to disable the resolver and enable the forwarder, or you need to set the resolver to forward.
-
@johnpoz
We do not always have the same skill levels at everything we do. Some things we know less about and know more about other things. That is the beauty of forums, after struggling to learn and try on your own, you hope that someone that does have the knowledge will step up and explain and not chastise.I'm not saying you chastised me but that each step learned from using pfsense is one that gives me some extra knowledge to know how to look for the next problem.
Anyhow, in my case, I just want pfsense and all of the internal servers to use the local DNS servers. The firewall itself doesn't need to resolve or forward anything, it can use the locals as well. The problem was that is was adding 127.0.0.1 as the first nameserver for all of the DHCP hosts.