unexpected outbound traffic blockage
-
I recently changed my home firewall over from untangle to pfsense, which I like much better. However, after reviewing the firewall logs I see a lot of outbound traffic being blocked even though it should allow all outbound. Does anyone have any experience with this?
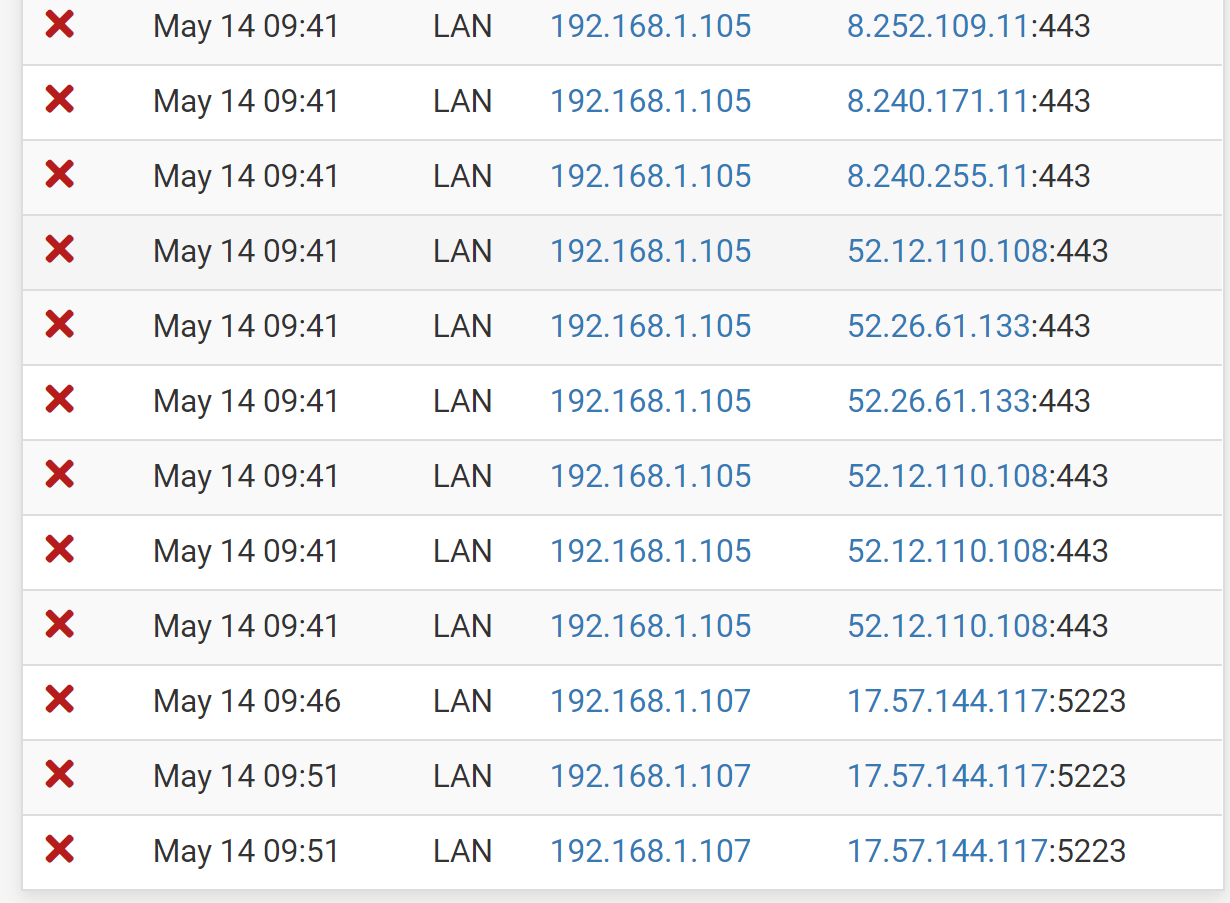
-
@robmarchetti Do you have any packages installed such as pfBlocker? What are your LAN rules?
-
@robmarchetti
Check out which rule is responsible for the block.
You may also add the rule column in the log settings at "Where to show rule descriptions". -
@kom No I haven't installed any packages, it is just the base pfsense image. LAN rules are below.
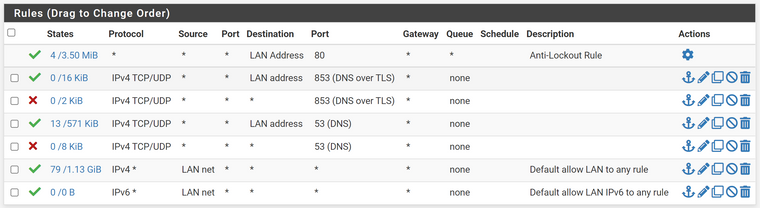
-
That looks normal, you can see states are going over the allow all and so long as DNS is configured correctly on the pfSense that should work fine.
Curious though about the OP screenshot where you were looking at those blocks. Status > System Logs > Firewall > Normal View will show the rule in the log that is blocking said traffic.
-
@robmarchetti
You should add a description to each custom rule, otherwise you only can see the ID in the log.Also post the whole log screen including the protocol, please.
-
@viragomann Thanks! I didn't know you see which rule is causing the block. After looking at the logs it is rule ID 1000104533 causing the problem, but that ID doesn't match any of the rules I have on any interface.
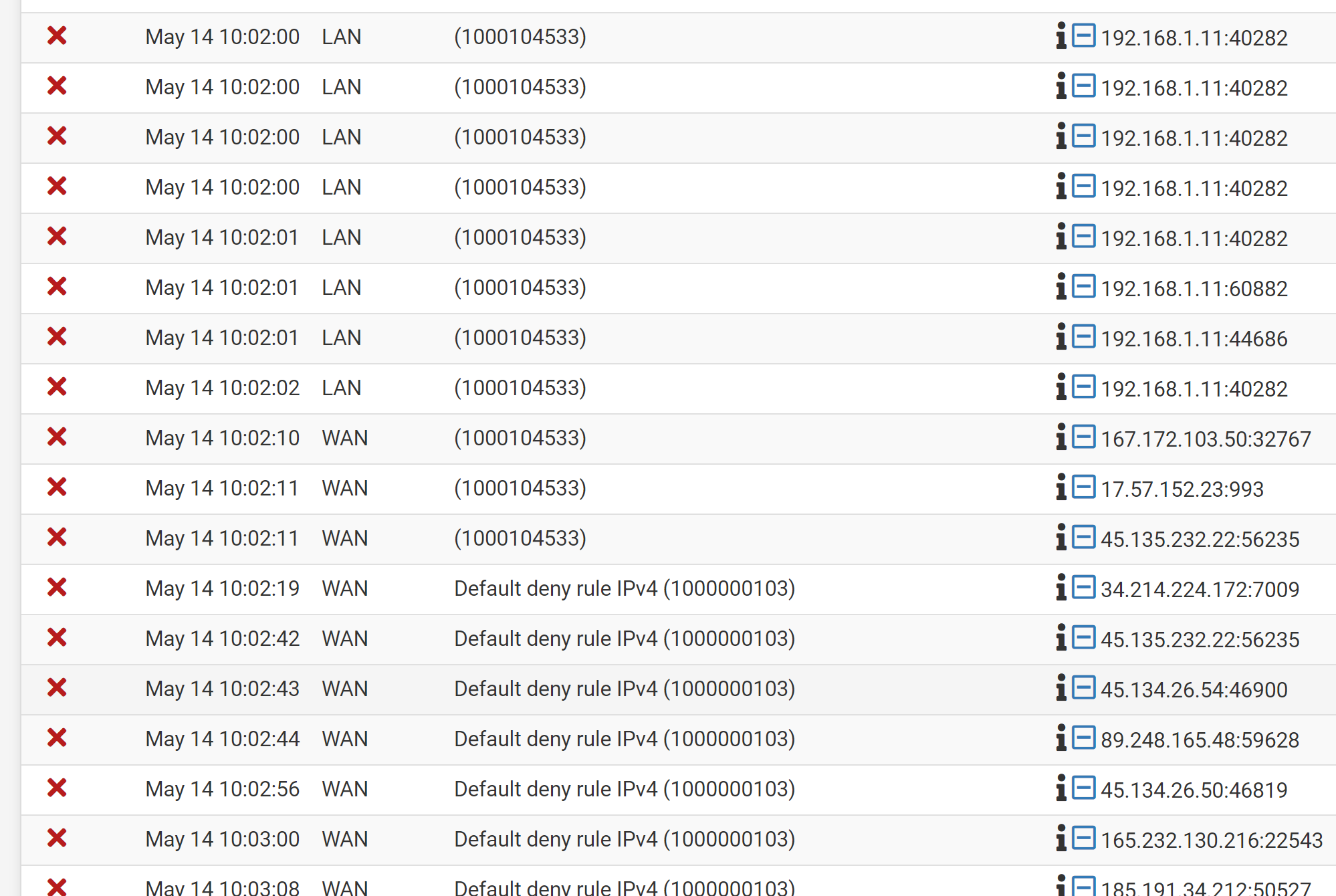
-
@viragomann Good point, I'll go in add a description to the firewall rules and take a screenshot of the log after.
-
@viragomann said in unexpected outbound traffic blockage:
Also post the whole log screen including the protocol, please.
Possibly it is an out-of-state block.
-
If you only have the rule id you can use pfctl to display the respective rule:
pfctl -vvsr | grep <rule-id> -
@viragomann It looks like the protocols for the blocked outbound LAN traffic are TCP:PA, and TCP:FPA. I've never seen that before, but I'm guessing those might be invalid or fragmented packets?
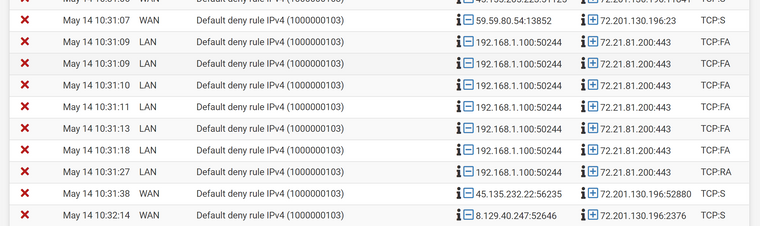
-
@robmarchetti https://docs.netgate.com/pfsense/en/latest/troubleshooting/log-filter-blocked.html
This may be what you're looking for
-
@robmarchetti
Yes, all TCP flags other than SYN means that pfSense has no state for it in its state table.
Maybe the connection was already closed due to timeout. Maybe you have a sort of an asymmetric routing issue. -
Did you make any changes in System > Advanced > Firewall & NAT > State Timeouts?
Also, are you otherwise having any actual outbound issues or were you just noticing the logs?
-
@viragomann Thanks for your help, after looking at the literature I realize now that what I saw in the logs is actually normal as pfsense drops out of state traffic by default. I had a layer 8 problem!
-
@eric-lts Nope, the state timeout settings are all set to default. And the network functions perfectly well, I just didn't understand what I saw in the logs. Thanks for the help.
-
@robmarchetti said in unexpected outbound traffic blockage:
pfsense drops out of state traffic by default
We normally uncheck the "Log packets matched from the default block rules in the ruleset" log option, since there can be a lot, and just turn that on if debugging new rules.