Filterdns has stopped resolving hostnames in firewall aliases
-
@slu said in Filterdns has stopped resolving hostnames in firewall aliases:
Maybe this is the issue, because ACME doesn't work if all lists are enabled/blocked.
I've checked them all, and activated, for years now :
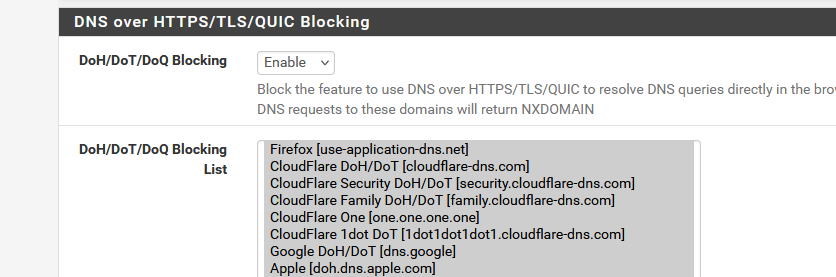
I also use the ACME pfSense package for a long time now.
No issues what so ever.the acme.sh shell script uses the available DNS to find the Letsencrypt server (or alternative) for the renewal request. As pfSense resolves by default, it doesn't care and won't use any 'DoH' DNS servers.
If you set up pfSense, the resolver, as a forwarder, and you forward to a 'DoH/DoT/DoQ' listed server, then unlist that DNS server.
-
@Gertjan said in Filterdns has stopped resolving hostnames in firewall aliases:
I also use the ACME pfSense package for a long time now.
No issues what so ever.Off topic:
Thanks for the feedback, interesting this works in your setup. For some reason the ACME script try different DNS server and get a timeout because pfBlockerNG reply (for example) for one.one.one.one NXDOMAIN. Maybe its relevant how ACME is configured.Since we use the DNS servers from our ISP this can't be the issue here.
-
@slu said in Filterdns has stopped resolving hostnames in firewall aliases:
aybe its relevant how ACME is configured.
Nice catch !
This :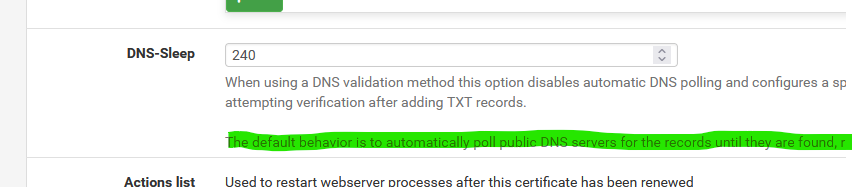
implies that when you set DNS Sleep to '0', it's the script itself that starts polling every 'x' seconds the domain name servers.
If its using one of the Doh etc, (which you've blocked with pfBlockerng) then yeah, that fails ...Set DNS Sleep to "200" or so and solved ^^
-
S SteveITS referenced this topic on
-
@SteveITS This has been an issue for me for YEARS. But it only crops up every so often (like today). It's long enough apart that I forget about the filterdns issue and waste several hours looking at the wrong things.
Maybe I just need to set up a cron job to kill and restart filterdns every hour? Would that work? Break something else?
-
S SteveITS referenced this topic on
-
S SteveITS referenced this topic
-
I ran across https://redmine.pfsense.org/issues/14734 which sounds like a possible cause...the IP is incorrectly removed if an FQDN resolving to it changes IPs.
Also per https://forum.netgate.com/topic/199152/unexpected-alias-behaviour-two-ranges/ aliases that contain IPs and an FQDN may fail to populate all the IPs.
-
14734 was marked as a duplicate of https://redmine.pfsense.org/issues/13792.
I am trying to think of a way around that...have a separate alias+rule for FQDNs that might ever overlap, say for each laptop...?
-
Agree
That bug really does make alias much less useful. Two example I currently use aliases for which will fail with this bugWhite list for remote access to work server from periheral sites. The laptops will roam between sites
- Peripheral site DDNS FQDN
- Peripheral site relatively static IPv4 addresses
- Laptop 1 DDNS FQDN
- Laptop 1 DDNS FQDN
White list from a VoIP supplier with redundant servers in multiple cities. During fault conditions the supplier redirects traffic to better functioning servers in another city
- city1.Voipsuppler.com
- city2.Voipsuppler.com
- city3.Voipsuppler.com
- city4.Voipsuppler.com
- city5.Voipsuppler.com
- city6.Voipsuppler.com
- city7.Voipsuppler.com
- city8.Voipsuppler.com
Imo
The variable FQDN component of an alias should be completely recalculated from scratch then combined with the constant (explicitly specified) IPs each time. After which only changes from the current IP addressees written to filterdns to update the firewall filtering. -
Having this issue and follows symptoms already mentioned.
Use DNS in aliases for access in FW rules. Access to a remote site drops. The Source IP is hitting Default Deny rule at the remote end. Remote end Tables doesn't have the IP for the DNS name, not sure if a DNS issue or filterdns stalls.
None of the reload suggestions found worked
/etc/rc.update_urltables,/etc/rc.update_urltables now forceupdateand/etc/rc.update_alias_url_data. The IP never returned in Tables following those commands. Maybe because filterdns appeared stalled - process still running and was not exiting.Also noticed:
- DNS resolution was working after the issue started and no issues were noticed before
- This occurred twice seemingly sporadically, both were after 1am. pfBlocker update does not run at that time.
- First time noticed occurred after an ISP modem outage/reboot. Didn't figure out the Tables issue then. Rebooting the ISP modem again resolved the issue. Apparently, manually deleting an IP from the table, followed by downing the WAN interface caused pfSense to repopulate the IP in the table.
- Second time there was no modem outage. Restarting unbound service did not resolve the issue. Saw
filterdnsin the process table still running. Did resolve with a suggestion above
killall filterdnsthen Status -> Filter ReloadpfSense is 2.8.1 - packages: frr, mtr, nut, pfBlockerNG, Service_Watchdog (watching OpenVPN), and System_Patches
-
@NWOSwamp Due to the above mentioned bugs, AFAIK the workarounds are:
- any FQDNs that might ever overlap (same IP) need to be in their own alias (therefore, rule)
- avoid mixing IP ranges and FQDNs in the same alias
-
@SteveITS I don't have either of these. I went and did an nslookup on all the FQDNs (including LAN IPs). Sorting and sorting for unique resulted in the same number of IPs, meaning no overlaps/none with the same IP. None of the FQDNs should have changed, but it also doesn't mean the wrong answer was returned by DNS when this happened. I don't have aliases with mixed IPs and FQDN.
I will keep these in mind specifically looking for them next time.
I do have:
- aliases referenced in other aliases
- the same FQDN in an alias and as the Remote Gateway for IPsec - these would end up in different rules, though.
Alias in Alias example:
Alias Name: location1_IP
FQDN: location1.foobar.comAlias Name: allow_ping
FQDN: "location1_IP"
FQDN: anotherserver.foobar.comAlias Name: OpenVPN_backup
FQDN: "location1_IP"
FQDN: mobiledevice.foobar.comallow_pingandOpenVPN_backupwould then be used as the source in separate WAN rules. IPs oflocation1.foobar.com,anotherserver.foobar.comandmobiledevice.foobar.comwould never be the same under normal circumstances. -
For me, pfsense removing transiently overlapping IP addresses make alias based IP filtering unreliable, so not a usable solution. The bug has been there for at least 3 years, and doesn't appears unlikely to be resolved in the near term.
I wonder if as a work around, it is possible to:
- use pfBlockerNG to generate/maintain these aliases.
- Store the "feed" for these work around alias locally
- Set their alias update frequency to hourly
Hopefully that would result in pfBlockerNG generating the aliases from scratch each time, including the associated duplicate removal. pfsense filterdns would then only see an IP being removed when it is duplicated zero times (actually removed from the alias), and so avoid the pfsense redmine bug 13792.
-
@Patch said in Filterdns has stopped resolving hostnames in firewall aliases:
I wonder if as a work around, it is possible to:
- use pfBlockerNG to generate/maintain these aliases.
Indeed it's possible—and pfBlockerNG additionally contains deduplication functionality for IP lists.
-
@tinfoilmatt just be aware pfB dedupe has its own issues:
https://forum.netgate.com/topic/185901/pfblockerng-not-blocking-some-foreign-sites-using-geoip/8 -
@SteveITS said in Filterdns has stopped resolving hostnames in firewall aliases:
https://forum.netgate.com/topic/185901/pfblockerng-not-blocking-some-foreign-sites-using-geoip/8
Was not aware. Thanks for the share.
Tangentially related—but as does CIDR aggregation when using a combination of IP blacklists (i.e., 'action'
Deny) and whitelists (i.e., 'action'Permit). -
S SteveITS referenced this topic