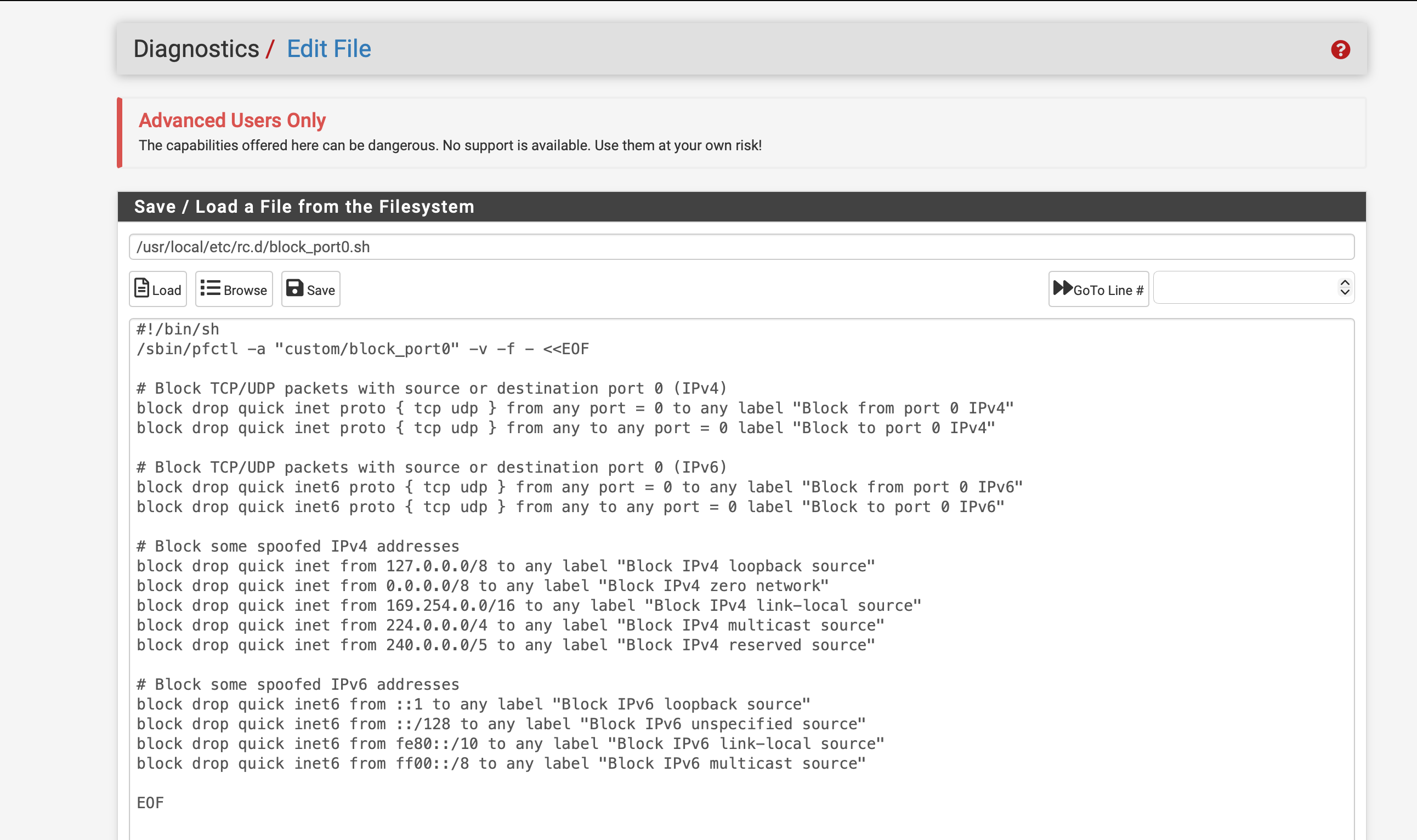
Port 0 Extra Precautions
-
@JonathanLee said in Port 0 Extra Precautions:
Some of them would stay active, even though the device is completely turned off for a couple days ...
What DHCPv6 server ? ISC ? Kea ?
Default lease duration ?
What do ou mean by 'active' ? Even with the device turned off, the IPv6 address still replies to a (example) ping ?@JonathanLee said in Port 0 Extra Precautions:
My main issue was that also dhcpv6 leases for managed addresses on the one side of the network
?
That one side is called the DHCPv6 server. You might call that "one side". How is that a problem ?The DHCPv6 protocol isn't using the "zero port".
edit :
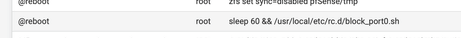
I presume @reboot means : during the boot, this line gets executed.
Look at your logs, you'll find :
Afaik : the /tmp/rules.debug is regenerated very often. This file is used to "repopulate" all the firewall rules and settings.
I don't think the rules you put in place with the @reboot will survive this.Also, files with the .sh extension and execute bit set, place in the /usr/local/etc/rc.d/ folder are executed at boot. There are already a couple of .sh file there :
[25.07.1-RELEASE][root@pfSense.bhf.tld]/usr/local/etc/rc.d: ll *.sh -rwxr-xr-x 1 root wheel 327 Nov 5 08:41 avahi-daemon.sh* lrwxr-xr-x 1 root wheel 10 Dec 6 2023 munin-node.sh@ -> munin-node -rwxr-xr-x 1 root wheel 660 Oct 17 03:57 nut.sh* -rwxr-xr-x 1 root wheel 1784 Oct 1 08:28 pfb_dnsbl.sh* -rwxr-xr-x 1 root wheel 2385 Oct 1 08:28 pfb_filter.sh* -rwxr-xr-x 1 root wheel 1421 Aug 20 07:34 radiusd.sh* -rwxr-xr-x 1 root wheel 120 Oct 17 03:57 shutdown.nut.sh*and I know these are executed during system boot.
Then why adding a cron task ? Doesn't that means you rules get added twice ? -
@JonathanLee if you feel the default rules of pfsense are not hard enough - I would put in a feature request so that they can be adjusted by the developers.
But again I am going to stress, rules you want to add should be done in the gui.
Direct manipulation of the rules that get loaded by default, is a fantastic way of shooting yourself in the foot.
-
Open /etc/inc/filter.inc.
Locate function filter_rules_generate()
This function make the /tmp/rules.debug file, the file that gets loaded into pf.
Start reading ...
Right at the start you find$ipfrules .= discover_pkg_rules("pfearly");Locate this function "function discover_pkg_rules($ruletype)"
Read it - and discover that if you create a file on the correct place with the correct content, it will get include in the main firewall rule set, "no questions asked".As @johnpoz said : this is fantastic. Keep us posted, make photos !
-
@Gertjan said in Port 0 Extra Precautions:
That one side is called the DHCPv6 server. You might call that "one side". How is that a problem ?
I have two subnets I have a guest area and a secure side for openVPN use with my private cloud. The side I am talking about is the secure side. So my WLAN interface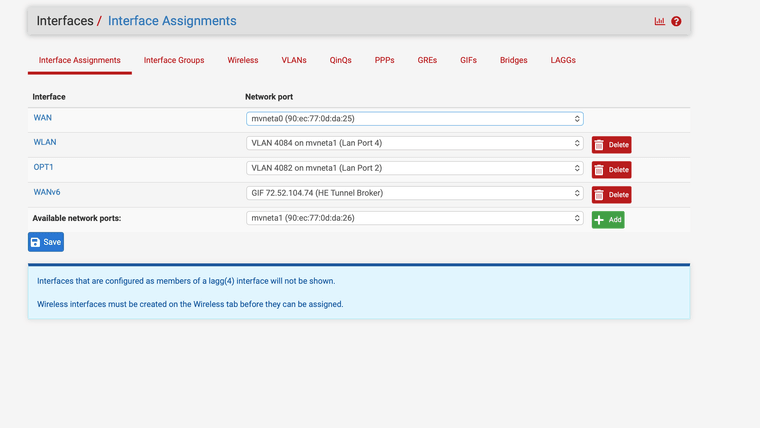
What DHCPv6 server ? ISC ? Kea ?
Default lease duration ?
What do ou mean by 'active' ? Even with the device turned off, the IPv6 address still replies to a (example) ping ?What DHCPv6 server ? ISC ? Kea ?
I am using ISC on plus 23.05.01 still I can't upgrade util the Squid status page issue is resolved the bug report is still open in Redline after Squid did there updates for the security issues the status page is not working.
Default lease duration ?
7200 seconds.
Max lease time 86400 seconds.What do you mean by 'active' ? Even with the device turned off, the IPv6 address still replies to a (example) ping ?
By active I mean if I have it set to RA mode managed if I go to status/DHCPv6 Leases some devices even when turned off show Online in green for days on end until a reboot at that point the system says wedged reset its weird like it hangs with the dhcpv6 lease I have not attempted to ping it I will next time, but the ipv4 lease for that device is gone when this occurs.
This area..
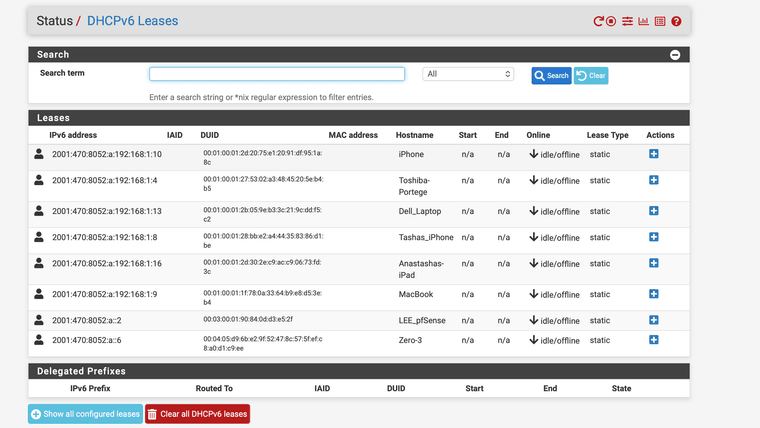
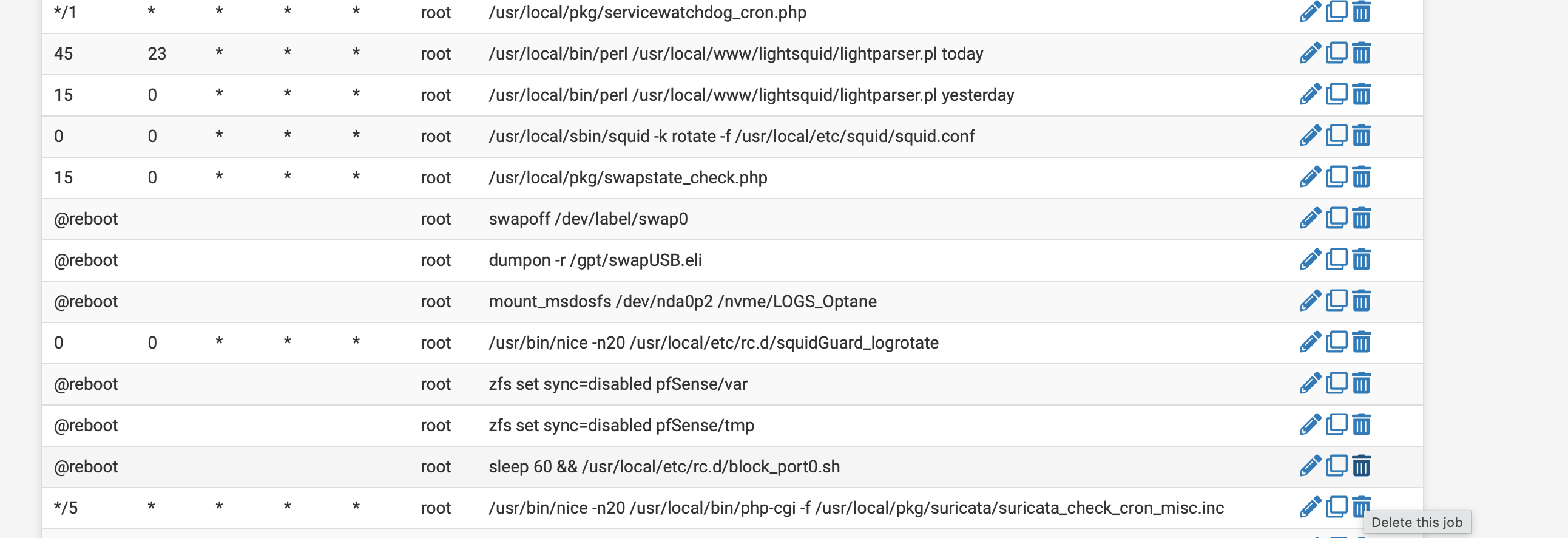
On shutdown it does try to stop the script you can see the script name also so it is running at times. I have removed the cron, based on the recommendations I am thinking I will delete the file I just wanted port 0 to be disabled on ipv6 also but it appears to break something when it is running.
-
@JonathanLee said in Port 0 Extra Precautions:
I am using ISC on plus 23.05.01
dude.. Run squid on something else if you want the latest and greatest version, etc. Posting stuff about adjusting rules on a 2 year old version is a waste of time.
As to port 0 on ipv6 - what are you not getting that those are already blocked??
rules.debug
block quick inet6 proto { tcp, udp } from any port = 0 to any ridentifier 1000000116 label "Block traffic from port 0" block quick inet6 proto { tcp, udp } from any to any port = 0 ridentifier 1000000117 label "Block traffic to port 0" -
@johnpoz On a side note thanks for info on cron I removed that and the wedged errors are gone and it does run automatically. You can see it running when it reboots.
How would I run squid on something else? Would I just redirect all traffic with pfsense to it, after it redirect it back to pfsense? I do have an external wpad that functions great.
-
@johnpoz said in Port 0 Extra Precautions:
rules.debug
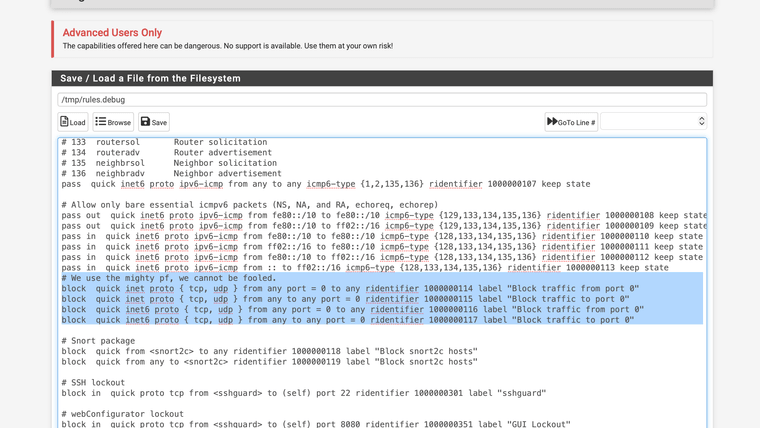
Yes they are there .. there was something that wasn't working originally that was why I had this script I can't remember what it was right now I have to find that old post. The website will not let me view historical posts right now for some reason it only lists the last couple or so now
-
Re: Port 0 and IPv4 Great... but hey what about IPv6 or inet6?
This it wasn't loading the ipv6 port zero rules for me originally a while ago. Maybe I can delete my script now
-
@johnpoz John thanks for the conversation on this.
Deleting the cron job fixed the reboot firewall wedged errors I assume that was because of the duplicates as it was already in rc folder
I also deleted the script as the blocks are now included and no longer missing.
-
@johnpoz Does Netgate have a cook book recipe for configuring Squid externally, like the old one for internally? If I had this it would make it easy, I just wonder how to do this as it has to go into squid and back up to the internet etc, makes my brain hurt I only have done it inside pfsense