Firewall Rules Order
-
@lordofpc734 said in Firewall Rules Order:
cant find anything named Alias native anywhere in PFblockerNG-devel
(and others)
On the IPv4/IPv6 tabs select Alias Native:
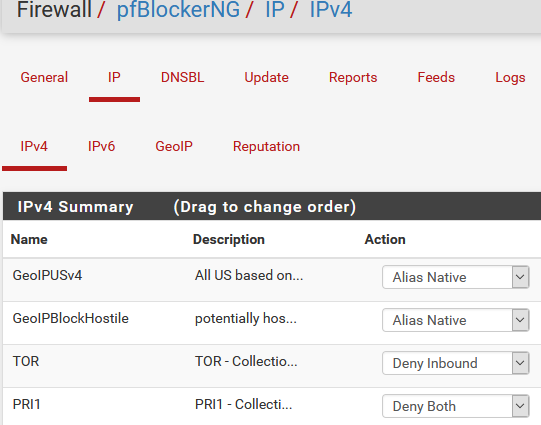
Then create whatever rules you want:
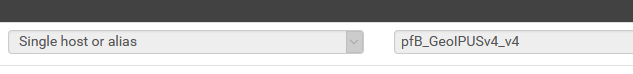
(yes I know it says v4 twice in the alias, that's an artifact when upgrading from pfBlockerNG to -devel as it adds _v4 to all the aliases)
-
@rkgraves said in Firewall Rules Order:
I have a pfSense Allow rule that needs to precede the pfB_ Block rules on the WAN interface.
Make that rule a floating one if you can't find a better solution.
-
@teamits
Thank You Very Much!When you manually create WAN Firewall rules using the Aliases created this way what do you do with the default rules automatically created by pfBlocker, just disable them?
Again Thanks,
RKGraves -
Manage them in pfBlocker, disable or delete them, if you don't need them anymore.
-
@Bob-Dig
Thank You for this tip!I can see how creating an IPv6 Floating rule (Floating rules evaluated first) would work. But can an IPv4/NAT rule work as a floating rule?
Again Thanks,
RKGraves -
@rkgraves absolutely.
-
@Bob-Dig
Thank You, I'll work on this and report back.I appreciate your time and help!
RKGraves -
Thank You Everyone!
I'm now able to manually set the order of my WAN firewall rules while running pfBlockerNG-devel with GeoIP. To verify what I did is correct, and for anyone else who might come across this thread, I'll list my abbreviated steps.
- clean pfSense install
- generated a new MaxMind key
- installed pfBlockerNG-devel
- Firewall / pfBlockerNG / IP / GeoIP - for each GeoIP location I set the Action to "Alias Native"
- Firewall / Rules / WAN - manually created IPv4 and IPv6 Deny rules using the source as the GeoIP Aliases
- Firewall / NAT / Port Forward - created my IPv4 Allow Rules
- Firewall / Rules / WAN - created my IPv6 Allow rules
- Firewall / Rules / WAN - sorted my Allow and Deny rules as needed - Saved
Tested:
- Firewall / pfBlockerNT - Save (my original install would fail at this point and remove my WAN Rules sort order - defaulting instead to one of the 4 predefined rule orders)
- Rebooted pfSense & tested
For those with more experience; Please let me know if anything I did appear incorrect.
Again, Thank You for your Help!
R.K.Graves -
@rkgraves said in Firewall Rules Order:
Firewall / Rules / WAN - manually created IPv4 and IPv6 Deny rules using the source as the GeoIP Aliases
Depending on your intentions, you may want deny rules on the LAN side to block outgoing traffic. Otherwise if the LAN allows the outbound the connection state will allow the inbound.
Also after creating the pfBlocker entries an Update is necessary to generate the lists/tables.
-
so happy to find the explanation relating the tables and lists!! thanks!