Alias Native Logging
-
Hi, I have a question regarding the logging when using Alias Native in the creation of ip lists.
I am using pfBlockerNG-devel version.
I have, and am, using the alias native option to allow more fine grain control on the list order but I am finding that the rules are working in blocking and allowing as per my rule order, they are not being logged in the reports section.
Is this by design or have I misconfigured something. I really liking the new reporting section and would like to make use of it so any help would be appreciated.
Thanks.
Nick
-
I have experienced a similar thing.
I only allow a subset of Oceania GeoIP to connect to my OpenVPN sever, I do this using an Alias Native which is used in my firewall rule for OpenVPN.
Connection to my VPN are no longer showing up on the Permit Report, as well I have noticed the Oceania list appearing on the Feeds column of the IP Deny feed.
When Oceania shows up on the IP Deny feed, these connection attempts are not to my OpenVPN port (1194).
My understanding (please correct me if wrong) is that any successful connections to port 1194 from oceania would go on the Permit list. Any unsuccessful connections to port 1194 would go in IP Deny with Oceania as the Feed.
Connections to any other port should not have anything to do with the Oceania GeoIP List.
BBcan117 you have done an outstanding job on the development version of pfBlocker, Thank you for you hard work.
-
If you change the type to Alias Permit or Alias Deny, does it generate alerts ?
-
Changed to Alias Permit, reloaded
Nothing in Permit, now I have feeds in Deny with
UnknownNot Listed -
@morgion said in Alias Native Logging:
UnknownNot ListedThis is a new behaviour of the pfBlockerNG DNSBL service, it's dynamic and switch the Feed to
Unknownduring Cron Update or Force Reload. -
@morgion said in Alias Native Logging:
Nothing in Permit
Did you read the
 infoblock?
infoblock?
Maybe if you use "pfb_" for rules prefix ? -
Just tried again, verified cron not starting for another 20 minutes. exact same result.
-
@ronpfs I use pfb_Oceania_v4 in my OpenVPN Rule as Host/alias Source for the OpenVPN Pass rule
-
@morgion It's also become
Unknownwhen it's no longer in any DNSBL tables.So when it find an alert in the dnsbl.log file, it will display it in the Report tab even if it's no longer in any feed.
Can you hit the ^0 besides Quote in this forum (This will give me the minimum 3 Reputations so I don't have to wait "120 Sec" between post)

-
Just flicked through Diag/Tables all the pfb ip tables are populated.
Also included my Openvpn rules to show how it was setup
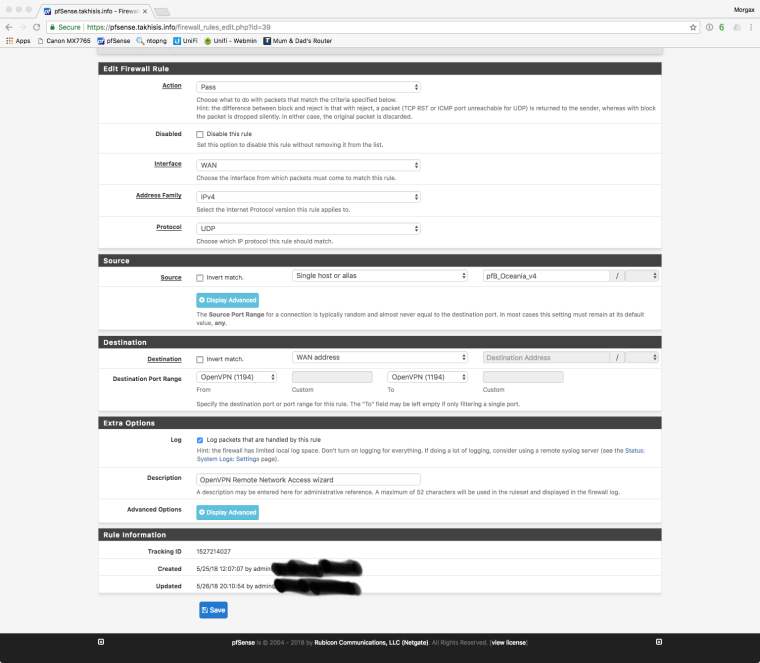
-
@morgion I guess the reports only search for Auto Rules as it has no way to figure out what are the FWRule TrackerIDs of your rules

-
@ronpfs That would be my guess, though It used to work pre development version, you just had to ensure logging was enabled for that rule. Im hoping its a bug that BBcan117 will get around to one day. if not it still works great and pfSense/pfBlocker is a fantastic product.
here is a pic of the pfBlocker reports fyi
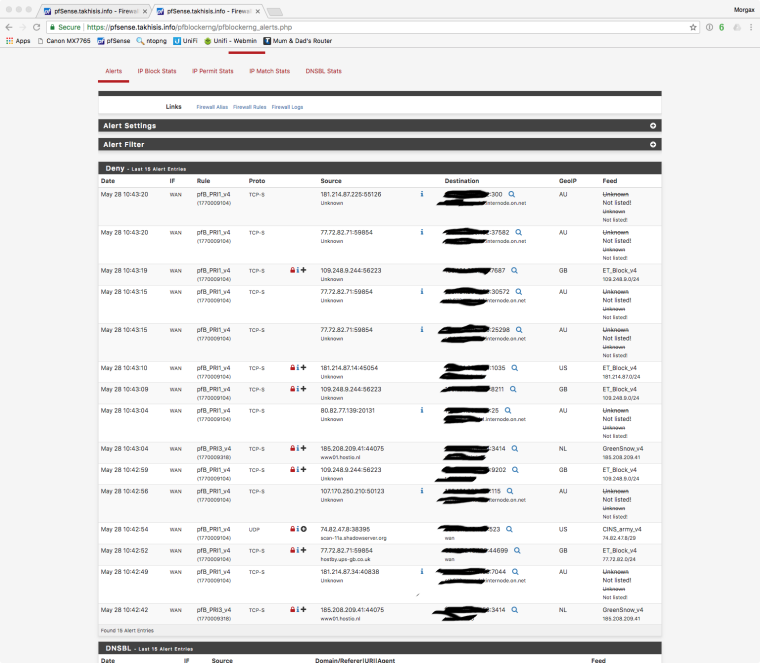
-
@morgion You can check that the 77.72.82.71 (or 77.72.82 or 77.72.) is in you Permit/Deny/Match/Native db with something like
grep "^77.72.82" /var/db/pfblockerng/permit/*.txt /var/db/pfblockerng/original/*.orig -
@BBcan17 said in [Email] :
In Extra Options, change the Description to something that start with "pfb_" -
@ronpfs said in Alias Native Logging:
grep “^77.72.82” /var/db/pfblockerng/permit/.txt /var/db/pfblockerng/original/.orig
grep: /var/db/pfblockerng/permit/.txt: No such file or directory
grep: /var/db/pfblockerng/original/.orig: No such file or directory -
@morgion said in Alias Native Logging:
@ronpfs said in Alias Native Logging:
grep “^77.72.82” /var/db/pfblockerng/permit/.txt /var/db/pfblockerng/original/.orig
grep: /var/db/pfblockerng/permit/.txt: No such file or directory
grep: /var/db/pfblockerng/original/.orig: No such file or directoryOups missing 2 "*" because I did'nt use a </> Code block

grep “^77.72.82” /var/db/pfblockerng/permit/*.txt /var/db/pfblockerng/original/*.orig -
@ronpfs said in Alias Native Logging:
rep “^77.72.82” /var/db/pfblockerng/permit/.txt /var/db/pfblockerng/original/.orig
No output
-
@ronpfs said in Alias Native Logging:
@BBcan17 said in [Email] :
In Extra Options, change the Description to something that start with "pfb_"No effect
-
@morgion said in Alias Native Logging:
@ronpfs said in Alias Native Logging:
@BBcan17 said in [Email] :
In Extra Options, change the Description to something that start with "pfb_"No effect
Maybe do a Force Reload IP

Restart the pfBlockerNG firewall filter service

-
@morgion said in Alias Native Logging:
@ronpfs said in Alias Native Logging:
rep “^77.72.82” /var/db/pfblockerng/permit/.txt /var/db/pfblockerng/original/.orig
No output
grep “^77.72.” /var/db/pfblockerng/permit/*.txt /var/db/pfblockerng/original/*.origIt maybe in a big block range.
If you go further down in the Alerts Tab (maybe change the settings to get more alerts) was it in a table as some point in time?