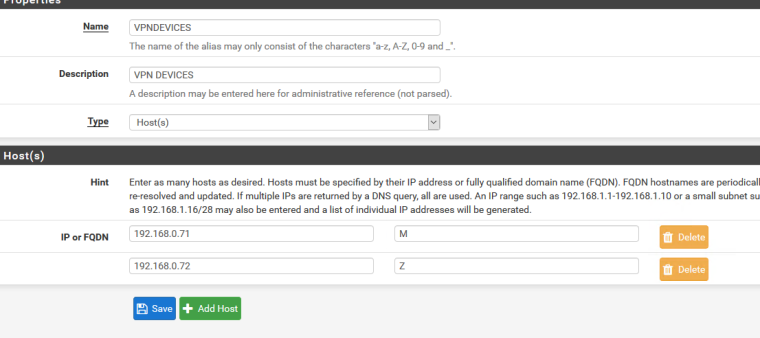
real address sometimes shows
-
Hi
I am using openvpn but for some reason some sites show my real ip address, (but only on some)
i have blocked webrtc on the browser
when I do a ping to sites it does not seem to pass through the pia server?
this has just recently started happening
any ideas what it could be?
-
Do you tunnel everything or use a split tunnel ?
I don't use OpenVPN but it sounds like you're using a split tunnel.
-
Your vpn went down? The site is run by the NSA and the black helicopter ninja's are just that good ;)
Why would you think that all sites on the internet answer ping?
-
I have a separate gateway with the aliases I would like to route through PIA, but it is sometimes showing my address for some reason
-
the vpn is up, but some show my real ip and some dont, it has only just started happening
-
Well has to so most likely with your alias and your policy routing.. Maybe your aliases are not resolving correctly, maybe whatever site changed something..
Check your state table.. Going to show you what interface you took to get to any specific IP.. If it goes out your wan, then yeah they will see your "real" ip... those helicopters will be circling soon ;) They might be outside your window now - they love to use that whisper mode ROFL...
-
I have a rule set up with the devices in under LAN which uses the PIA gateway
-
And again look at your states.. So your policy routing is based on your clients IP... Maybe the client got a different IP via dhcp then you think it got.
Without some actual info - its anyones guess to what you think your seeing or what you think some website is seeing, etc.
Show us your rules that say policy route this out vpn.. Then show us state table where you have client A going out vpn, and client B not going out vpn but according to you it should be, etc.
Maybe your vpn went down, client created a state out your wan. Vpn came back up but client will continue to use previous state out the wan, etc.
No info - just all guessing.
-
thanks I will get some screenshots once i get rid of these ninjas ;-)
the states are showing the devices ip coming from the lan
but there is a few coming from the wan interface which show as
LAN tcp 192.168.0.71:52787 -> masked:443 ESTABLISHED:ESTABLISHED 62 / 38 6 KiB / 9 KiB
WAN tcp masked:52740 (192.168.0.71:52787) -> masked:443 ESTABLISHED:ESTABLISHED 62 / 38 6 KiB / 9 KiBLAN tcp 192.168.0.71:52806 -> masked:443 ESTABLISHED:ESTABLISHED 159 / 159 11 KiB / 31 KiB
WAN tcp masked:18966 (192.168.0.71:52806) -> masked:443 ESTABLISHED:ESTABLISHED 159 / 159 11 KiB / 31 KiBLAN tcp 192.168.0.71:52936 -> masked:443 ESTABLISHED:ESTABLISHED 16 / 15 2 KiB / 6 KiB
WAN tcp masked:20288 (192.168.0.71:52936) -> masked:443 ESTABLISHED:ESTABLISHED 16 / 15 2 KiB / 6 KiB -
So that .71 box your saying should go out vpn? Why are you masking where it went? Some p0rn site your embarrased about? Why would the dest:443 IP be your actual WAN IP?
Where is a connection from this .71 box - if suppose to be blocked going out your vpn... Or some other box going out your VPN?
-
here is state from my normal wan from 192.168.9.100
WAN tcp 64.53.xx.xx:9918 (192.168.9.100:62645) -> 52.173.26.181:443 ESTABLISHED:ESTABLISHED 1.94 K / 993 148 KiB / 162 KiB
So now I policy route it out my vpn..
Here is new state going out vpn
NS1VPN tcp 172.27.224.29:41952 (192.168.9.100:61160) -> 52.41.78.152:443 ESTABLISHED:ESTABLISHED 12 / 12 2 KiB / 4 KiB -
.71 is my media box which everything should go out via the VPN
i have some other screenshots!
-
And did you vpn bounce? Do you have it set so NO connections can be made if vpn is down..
Existing states will have traffic go back out that connection vs through a vpn.. If your are that worried about leaking this media box from going out your wan. Then I would suggest you block it from going out your wan. So that the only way it can go anywhere is via vpn. If vpn bounces etc. Then your media box will just be not able to go anywhere.
Your screen shot on that vpn shows 0 current states - so yeah prob everything using existing states out your wan.
0/6.24 GiB
See here showing 17 current states out the vpn

From what your showing there is no states out your vpn - maybe its down??
What I would suggest is make sure your vpn is up... Then kill all the states from that .71 box and let it make new connections are they going out your vpn?
-
if i go onto the PIA site it shows my PIA address, if i go onto google and type in ip it shows my true ip,
The gateway is up at the moment to
-
Did you clear your OLD states??
If your vpn had bounced, and your .71 client made a connection to somewhere it would be allowed to go out the wan right. What rules do you have below your policy rule that sends it out the vlan? Have to assume you allow your lan net to go out your normal wan, etc..
So .71 makes a connection to 1.2.3.4... out the wan.. Even when your vpn comes back up - all connections to 1.2.3.4 will use the existing state and continue to go out the WAN..
If you don't want .71 to ever use the wan even if vpn is down.. Then create a rule to block it from doing that after your vpn policy route and before your allow. Clear all your STATES!!! for the .71 box..
-
Hi thanks!
I have reset the states and now get this
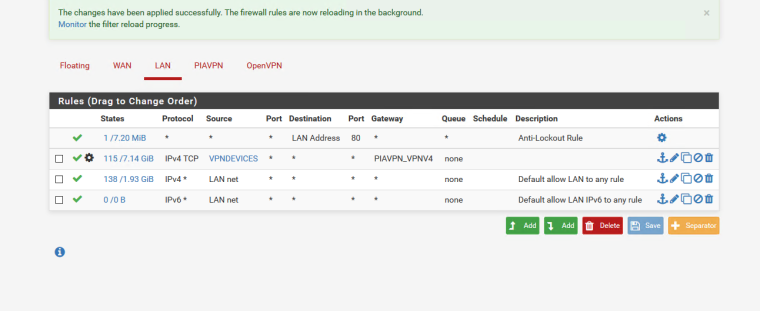
it still shows my ip on google ipleaks etc
pia website shows the vpn ip
-
Well your only sending TCP out your PIA... Maybe its using UDP.. Again!!!! If you do not want this .71 box to go out your wan then BLOCK below your PIA rule. this .71 source..
You do understand that google can use UDP right via QUIC for its web pages.. And dns is via UDP... If you want this .71 box using your PIA then your PIA rules should be ANY.. Or yeah anything other than TCP would use your normal wan.
-
Here I fired up chrome - do you use chrome on this .71 box... And bam to google its creating quic which is over UDP
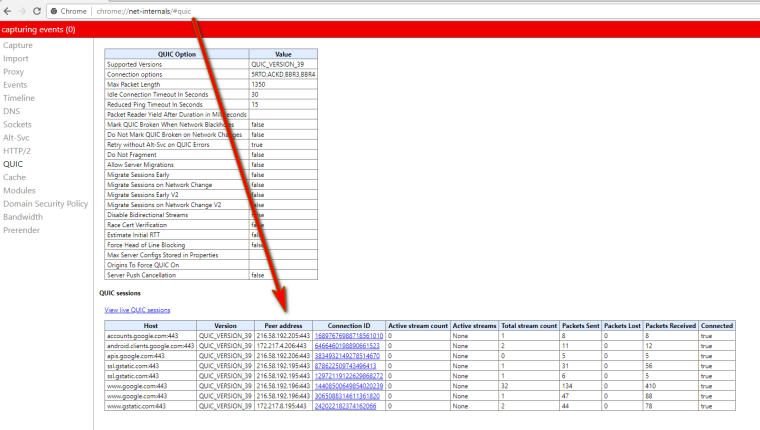
Change your PIA rule to ANY, kill all your existing states.. What do you see now for your IP?
here is sniff on pfsense showing the 443 UDP connections
05:56:39.543573 IP 192.168.9.100.63533 > 216.58.192.196.443: UDP, length 1350 05:56:39.543837 IP 192.168.9.100.63533 > 216.58.192.196.443: UDP, length 621 05:56:39.564956 IP 192.168.9.100.63533 > 216.58.192.196.443: UDP, length 1350 05:56:39.568775 IP 216.58.192.196.443 > 192.168.9.100.63533: UDP, length 1350 05:56:39.568992 IP 216.58.192.196.443 > 192.168.9.100.63533: UDP, length 31 05:56:39.569728 IP 192.168.9.100.63533 > 216.58.192.196.443: UDP, length 41 05:56:39.569903 IP 192.168.9.100.63533 > 216.58.192.196.443: UDP, length 38 05:56:39.585723 IP 216.58.192.196.443 > 192.168.9.100.63533: UDP, length 25 05:56:39.764571 IP 192.168.9.100.63533 > 216.58.192.196.443: UDP, length 39Happy to help you track this down - because if the ninja's get you we are all in trouble ;)
-
ah great that looks to be working now, I cannot believe I missed that :-) thanks very much really appreciate your help!
-
No problem... So do you use chrome?