Clients can't reconnect after pfsense reboot
-
@prophet said in Clients can't reconnect after pfsense reboot:
Configured everything (I'll use pfsense as captive portal) and everything worked perfectly as captive portal without user authentication (a simple splash screen with login button and no auth is enough for me).
I had PFBox 2.3 and clean installed 2.4.4 and have the same problem i resolved it somehow by setting Idle timeout to 3 to 4 hours and it work like charm.
@Gertjan said in Clients can't reconnect after pfsense reboot:
Instead of deleting files - and editing pfSense core fils, I prefer to use the API.
Consider this :
Install the Shellcmd package which permit us to execute 'commands' at startup.Place a file called "captiveportal_disconnect_all.php" in the directory /root
#!/usr/local/bin/php -q <?php /* Disconnect all clients on all captive portal instances */ require_once("/etc/inc/util.inc"); require_once("/etc/inc/functions.inc"); require_once("/etc/inc/captiveportal.inc"); global $g, $config, $cpzone, $cpzoneid; /* Are there any portals ? */ if (is_array($config['captiveportal'])) { /* For every portal (cpzone), do */ foreach ($config['captiveportal'] as $cpkey => $cp) /* Sanity check */ if (is_array($config['captiveportal'][$cpkey])) /* Is zone enabled ? */ if (array_key_exists('enable', $config['captiveportal'][$cpkey])) { $cpzone = $cpkey; $cpzoneid = $cp['zoneid']; captiveportal_disconnect_all(); } log_error("All users disconnected after system start-up"); } ?>Add a command in the Shellcmd package :

Done.I wanna try @Gertjan API :)
-
do we still need this also for pfsense 2.5 sir? I'm using this also for my captive portal in 2.4.4 p3 before with the system patches fix for "You are connected". just recently upgraded to 2.5.
-
@1ntr0v3rt3ch Why asking the same question again ?
-
@gertjan said in Clients can't reconnect after pfsense reboot:
@1ntr0v3rt3ch Why asking the same question again ?
oh! sorry sir! I thought this is different from the patches. my mistake.
-
I thought the same like @1ntr0v3rt3ch , I hoped that 2.5 version, will have all those fixes, but I was wrong, and it was messing with my hardware, so I came back to 2.4.4 p3, with patches ...
-
@didiosn said in Clients can't reconnect after pfsense reboot:
I hoped that 2.5 version, will have all those fixes
Hoping ?
I'll present you the uther simplicity of open source code.
You can checks things out yourself.
The 2.4.4-p3 (2.4.5) code base is here : https://github.com/pfsense/pfsense/tree/RELENG_2_4_5
The current 2.5.0 is here (I used the Switch branches/tags button) : https://github.com/pfsense/pfsense/tree/RELENG_2_5_0Based of the "RELENG_2_4_5" version, you will be able to find the patch. The patch that works if it 'finds' 2.4.5 code
This patch, and all the others, are what makes up '2.5.0'.
So, 2.5.0 == 2.4.5 + "all the patches = "2417 commits behind master. " Master = 2.5.0 plus newer patches, what make up the current version, to be released in the future.If "2.4.5 + patch to resolve "Clients can't reconnect after pfsense reboot" which is actually 2.5.0 does not resolve your issue, your actual issue is something different.
The silly thing is : I can't not easily test if your wrong or right : my pfSense rarely restarts. I do not have to, I do not want to shut it down or reboot : it serves as a company router with connected users, our own systems and out clients. The power stays up, it has even its own UPS ..... so, no issues for me. I advise you to do the same.
I will reboot the system this mornin, with some connected users (myself with some devices) to test if the issue still exist with vanilla "2.5.0".
It shouldn't - as it has the patch.The test is easy :
This "connected users list" visible in the GUI, after reboot :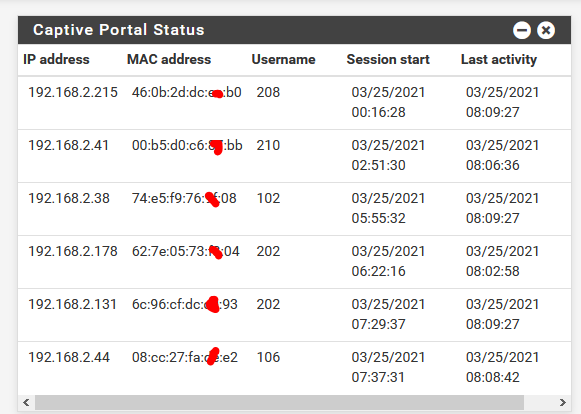
6 clients connected.
should look like this list :
[2.5.0-RELEASE][admin@pfsense.local.net]/root: ipfw table all list ......... --- table(cpzone1_auth_up), set(0) --- 192.168.2.38/32 74:e5:f9:76:xx:08 0 416726 35157523 1616656367 192.168.2.41/32 00:b5:d0:c6:xx:bb 0 21666 3376893 1616655996 192.168.2.44/32 08:cc:27:fa:xx:e2 0 24971 3309541 1616656369 192.168.2.131/32 6c:96:cf:dc:xx:93 0 165657 13800625 1616656371 192.168.2.178/32 62:7e:05:73:xx:04 0 3235 788929 1616656317 192.168.2.215/32 46:0b:2d:xx:ee:b0 0 391648 31807701 1616656371 ....... --- table(cpzone1_auth_down), set(0) --- 192.168.2.38/32 0 803791 1085868854 1616656367 192.168.2.41/32 0 30903 30311706 1616655996 192.168.2.44/32 0 39878 52533628 1616656354 192.168.2.131/32 0 362751 508494209 1616656371 192.168.2.178/32 0 3342 2165841 1616656317 192.168.2.215/32 0 819045 1150064899 1616656371 .....== 6 clients connected -> 6 entries for the down traffic and 6 for the up traffic.
The two tables xxxxx_auth_up and xxxxx_auth_down should contain the same IP's as the GUI shows.
-
OK. You're right. I'll try to reinstall 2.5 again, on VirtualBox and i'll be right back. Do not restart your system for that.
Thank You.
-
@didiosn said in Clients can't reconnect after pfsense reboot:
Do not restart your system for that
To late ;)
It's a good test anyway, rebooting ones in a while. It can expose other, hidden issues.The list with users :
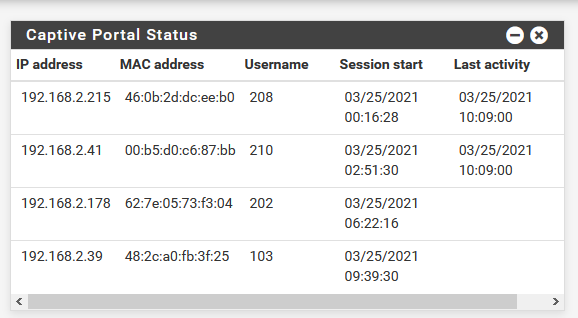
--- table(cpzone1_auth_up), set(0) --- 192.168.2.39/32 48:2c:a0:fb:3f:25 2020 3169 354192 1616663674 192.168.2.41/32 00:b5:d0:c6:87:bb 2018 18094 1053099 1616663673 192.168.2.178/32 62:7e:05:73:f3:04 2022 35 11549 1616663663 192.168.2.215/32 46:0b:2d:dc:ee:b0 2016 3086 757624 1616663674 --- table(cpzone1_host_ips), set(0) --- ........ --- table(cpzone1_auth_down), set(0) --- 192.168.2.39/32 2021 0 0 0 192.168.2.41/32 2019 14242 20162232 1616663438 192.168.2.178/32 2023 26 10703 1616663347 192.168.2.215/32 2017 1392 943978 1616663437 ......which corresponds with what the GUI tells me.
Traffic was generated as I swa the counter rise.
For me, it works.Btw : my pfSense runs native, it's not a VM, although that detail shouldn't matter.
-
Alright. I'll try it this night.
Please hide MAC adress in your screenshot... There are bad people out there.
Thanks
-
@didiosn said in Clients can't reconnect after pfsense reboot:
There are bad people out there
3 of the 4 MAC listed are already bad.
Bad always like to meet bad, and I've nothing against bringing them together so they can exchange. I ought to charge them actually for the favor ..... thanks for the pointing that out.The fourth one is a real Snowden fan, sees conspirators everywhere since the men-on-the-moon-1969 series - but has a Samsung device with all the Google telemetry activated in mode 'open-bar'. So, its also time for him to meet the "creator" of things.
edit : probably also a flat-earther. We all should find any possible method to help these guys. No restrictions.
sorry for the out-of-subject.
edit2 : Two ( ? ) out of 4 devices are iPhones/Pads, so the MACs are quasi random.
-
Hello! In version 2.5.1, Captive portal zone settings have an option "Preserve users database": "Preserve connected users across reboot". When set, users won't be disconnected during a pfsense reboot.
This solves the "You're connected" bug after reboot.
-
@suporteatech said in Clients can't reconnect after pfsense reboot:
have an option "Preserve users database": "Preserve connected users across reboot".
This is a new option, not related to the "You are connected" bug.
Normally, on reboot, the connected users database is ( should be) wiped. It wasn't (some pfSense version ago - but no one used these old versions anymore)
It wasn't wiped, s, after reboot, users were considered connected right from the start, but there were no firewall rules to let the user pass (the firewall was restarted / reset). This created the "You are connected" bug.
This bug was corrected several version ago. -
SupporteATECH asked :
Older version had old bugs. This issue, "You are connected" doesn't exist any more.
I just tried it myself :
This is my captive portal zone name :
So this is the SQL3 database file that contains all the users that are connected :
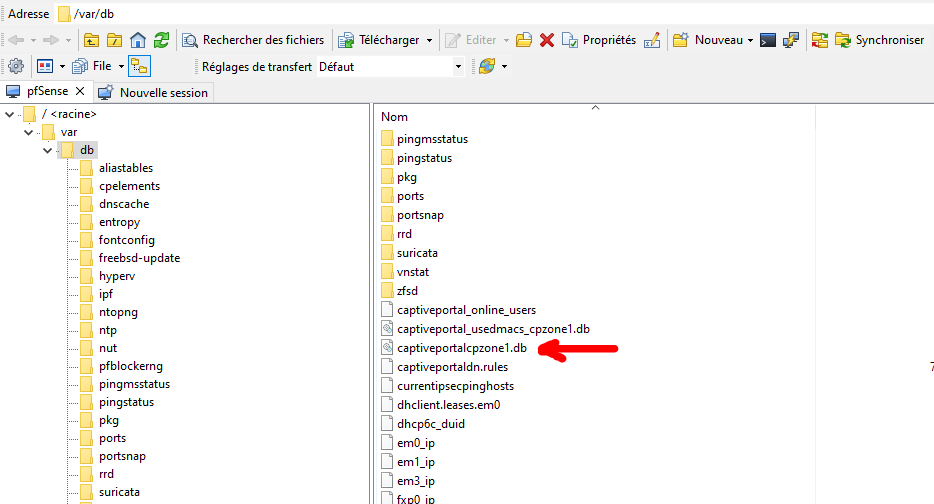
This file is wiped and created on restart.
If this option is set :
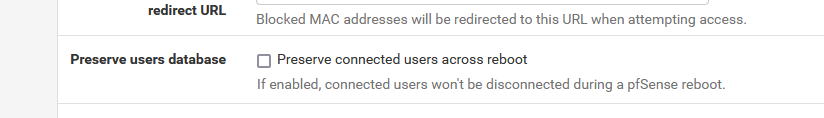
then the file is not reset.
Upon reboot, the file is read, and for all captive portal users that were connected upon reboot - listed in this file, 'ipfw' firewall rules and tables are re created.
See the ipfw rules for yourself.It works for me


I'm using 2.5.1 CE.