DMZ for VMs with VM pfSense
-
@luckyzor said in DMZ for VMs with VM pfSense:
What I wanted for, secure reasons, is to NAT (http / https / other services) in the ISP router -> VM pfSense -> DMZ
Huh??
Your isp is already natting... So using pfsense behind this is a double nat.. That is not any more secure than your first nat.. You want to put your "dmz" stuff behind pfsense and prevent it from talking to your normal network is my guess..
Why do you need this 3rd network? You want something like this right?
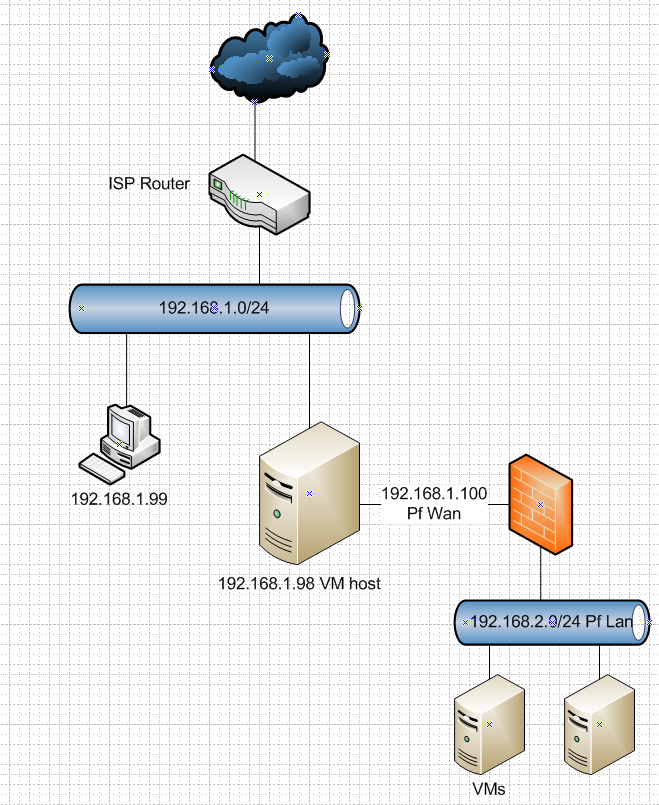
Where your VMs running on your host can not talk to 192.168.1/24 and you forward traffic on your isp router to 192.168.1.100 (pf wan IP) and then forward to 192.168.2.X your different vms on pfsense.
If not then please draw up what your wanting to accomplish.
BTW I would NOT do it that way... I would put everything behind pfsense both your physical network and your vm network(s) but hey thats just me..
-
@johnpoz said in DMZ for VMs with VM pfSense:
I would put everything behind pfsense both your physical network and your vm network(s) but hey thats just me..
Nope it's me too. ;-)
-Rico
-
@luckyzor said in DMZ for VMs with VM pfSense:
I've tried to create a virtual-network with NAT to all devices
You have to create an isolated network instead. The NAT network bypasses your DMZ devices to the LAN.
-
This is what I have for now:
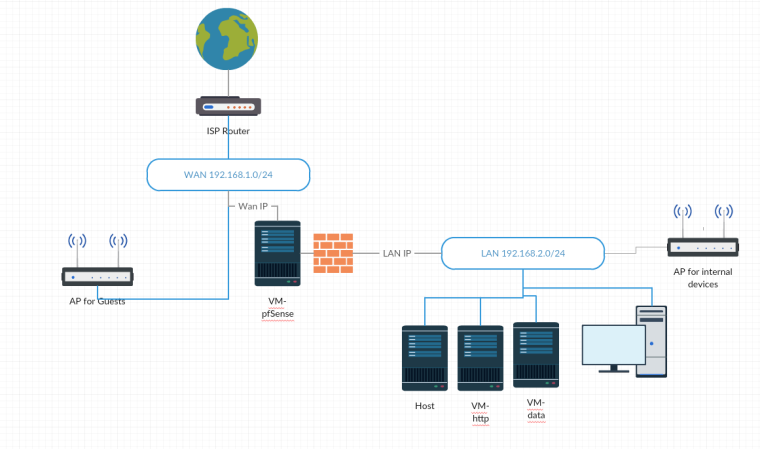
And I wanted to isolate the VM-http, something like that:
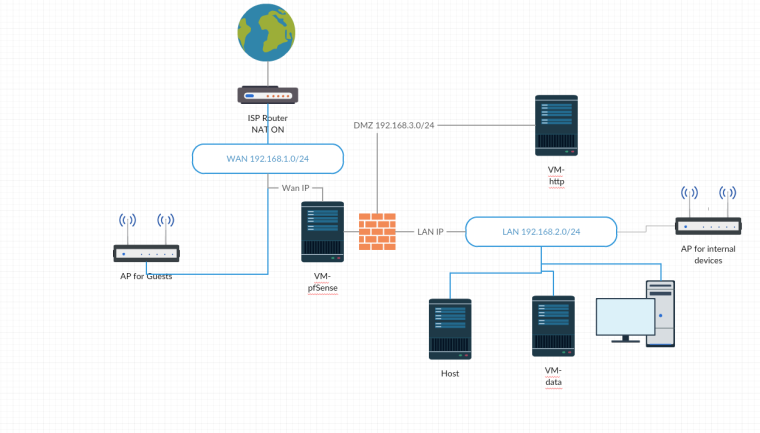
About the NAT is not better NAT in the ISP router then only in the VM-pfSense?
thanks for your help
-
Well then your just creating another network and or vlan in pfsense on your vm host, its going to nat that auto just like it does for your 192.168.2 network. There is not reason for a another nic - a vnic sure, connect it to your vswitch in your vm software. Can connect your VMs to that vswitch.
-
@johnpoz said in DMZ for VMs with VM pfSense:
Well then your just creating another network and or vlan in pfsense on your vm host, its going to nat that auto just like it does for your 192.168.2 network. There is not reason for a another nic - a vnic sure, connect it to your vswitch in your vm software. Can connect your VMs to that vswitch.
My question is that, what network should I create?
Should I create in Virt-manager? if yes what? virtual network (which?)? network interface(wich?)?
Should I create a Vlan in pfSense? (any tips on how to do it?)Which is better?
Can you give your personal opinion about my diagram? Just to know if something should change.
Thanks
-
What are you using for VM software - saying you use centos doesn't tell me what your running for VM.. Is it Virtualbox, OpenVZ, Xen, KVM, Linux-Vserver, Bochs? UML?
If you want a vm host - I for starters if you want a vmhost would just be using type 1 vs 2.. Say Esxi
-
@johnpoz said in DMZ for VMs with VM pfSense:
What are you using for VM software - saying you use centos doesn't tell me what your running for VM.. Is it Virtualbox, OpenVZ, Xen, KVM, Linux-Vserver, Bochs? UML?
If you want a vm host - I for starters if you want a vmhost would just be using type 1 vs 2.. Say Esxi
I'm using KVM/QEMU.
-
Well then RTFM on how to create vm network and attach it to a VM... That has zero to do with pfsense at all..
If I used KVM than I would be happy to point you how to do it - but other than maybe on some vps I have never used it.. I could fire it up I guess but have zero need currently.. Sorry.
If you switch over to say type one running esxi than be happy to help. Or running Virtual Machines on Synology NAS could point out exactly how to do it, which is what I am currently using and playing with.
-
@luckyzor
I've already tried to tell you to add an "isolated network".
Add a new virtual network in the VMM, enter DMZ in the network name box, no DHCP (if needed, this can be done by pfSense), no routes, check "isolated virtual network".Then add a NIC to pfSense and connect it this network and configure it in pfSense. Also connect the virtual NICs of the other DMZ VMs to it.
-
@viragomann I've done that but no internet access with the VM in the DMZ.
Maybe this need more configuration in pfSense... Can you give me some clue? Thanks alot
@johnpoz I've already thought to change to Exsi but I need to buy a license, and I have already all my VM in KVM. One day maybe :)
-
@luckyzor said in DMZ for VMs with VM pfSense:
I've already thought to change to Exsi but I need to buy a license
Depends on your Feature needs, there is a free ESXi License. You can't run vCenter with the Free and some other stuff is missing, you just need to check.
-Rico
-
@luckyzor said in DMZ for VMs with VM pfSense:
Maybe this need more configuration in pfSense... Can you give me some clue? Thanks alot
https://www.netgate.com/docs/pfsense/routing/connectivity-troubleshooting.html I guess you forgot to add rules to your new interface in pfSense. Hard to say unless you provide some more details.
-
@luckyzor said in DMZ for VMs with VM pfSense:
Maybe this need more configuration in pfSense... Can you give me some clue?
pfSense only permits access on LAN devices by default, on other interfaces added by yourself you have also to add filter rules to permit access to connected devices.
Go to Firewall > rules > DMZ and add a pass rule and allow any from any source to any for testing. Restrict access later.
-
@grimson said in DMZ for VMs with VM pfSense:
@luckyzor said in DMZ for VMs with VM pfSense:
Maybe this need more configuration in pfSense... Can you give me some clue? Thanks alot
https://www.netgate.com/docs/pfsense/routing/connectivity-troubleshooting.html I guess you forgot to add rules to your new interface in pfSense. Hard to say unless you provide some more details.
I've added the network interfaces, created the DMZ interface:
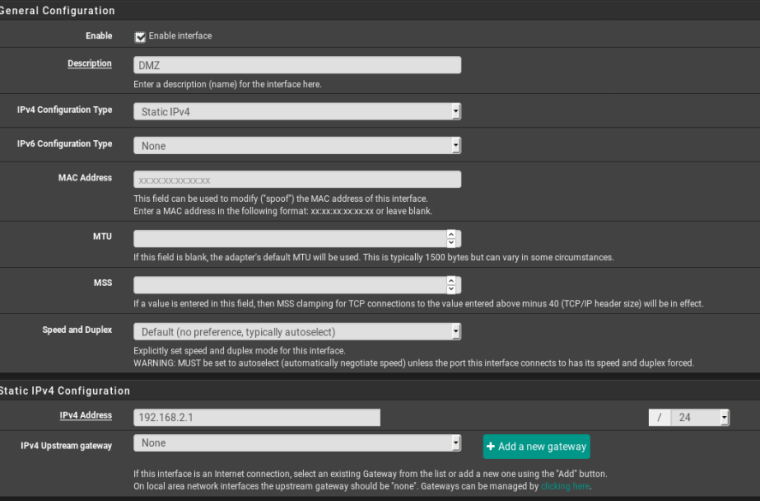
Now my VM in the DMZ can ping my lan but can't ping my wan.
I tried to block from dmz to lan and it doesn't work:
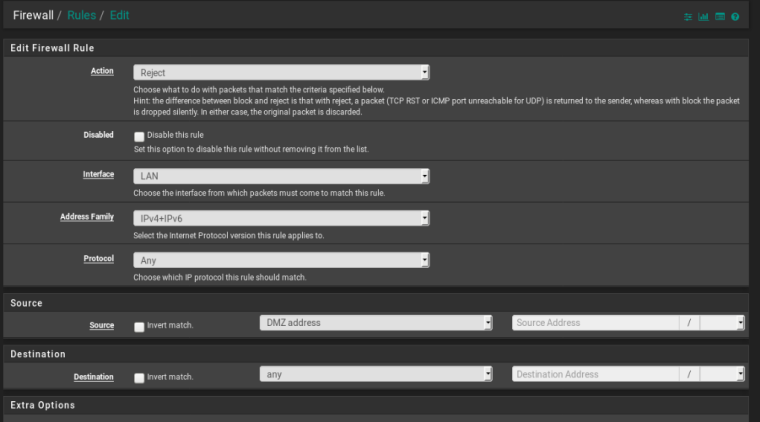
What I want:
DMZ can't see Lan devices
Lan devices can see DMZDMZ can see and be seen by WAN
Can I access DMZ by hostname in the Lan interface?
thanks for your help. I really appreciate.
-
Start reading here: https://www.netgate.com/docs/pfsense/book/firewall/index.html the rule you posted above shows pretty clearly that you lack the basics on how a firewall works.
-
@viragomann said in DMZ for VMs with VM pfSense:
@luckyzor said in DMZ for VMs with VM pfSense:
Maybe this need more configuration in pfSense... Can you give me some clue?
pfSense only permits access on LAN devices by default, on other interfaces added by yourself you have also to add filter rules to permit access to connected devices.
Go to Firewall > rules > DMZ and add a pass rule and allow any from any source to any for testing. Restrict access later.
Can't access internet with that rule:
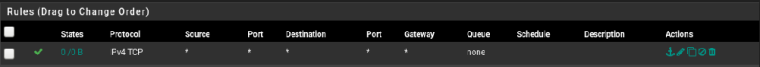
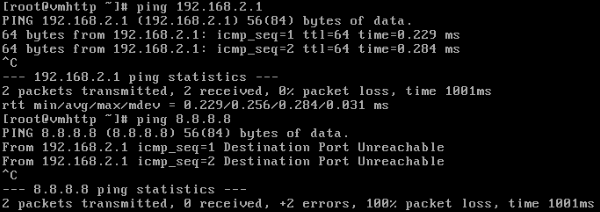
-
Your rule allows TCP only! Ping needs ICMP.
-
@viragomann said in DMZ for VMs with VM pfSense:
Your rule allows TCP only! Ping needs ICMP.

Still the same.
@Grimson I will read what you send me and try to understand this.
I'm facing a problem more "urgent" and I hope do be guide on how to troubleshoot this so I can try to fix it.
everything works (not the DMZ, but that is not urgent) as expected with my host and other VMs in the LAN side.
For the first time I plugged-in a switch in the LAN physical interface and my desktop to the switch.
Unfortunately, I can't get IP from the DHCP, tried to put a ip manually and nothing.
I don't know where to start to check where is the problem.I really need some help for this. Hope you can help me. Thanks in advance
-
@luckyzor said in DMZ for VMs with VM pfSense:
Unfortunately, I can't get IP from the DHCP
Then you have a layer 2 problem.. Or you did not enable dhcp on that interface..