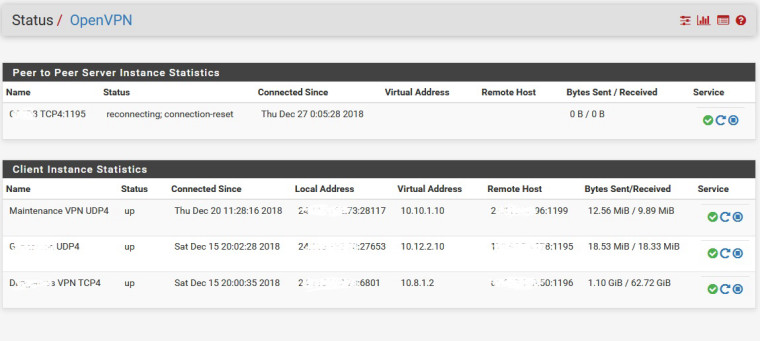
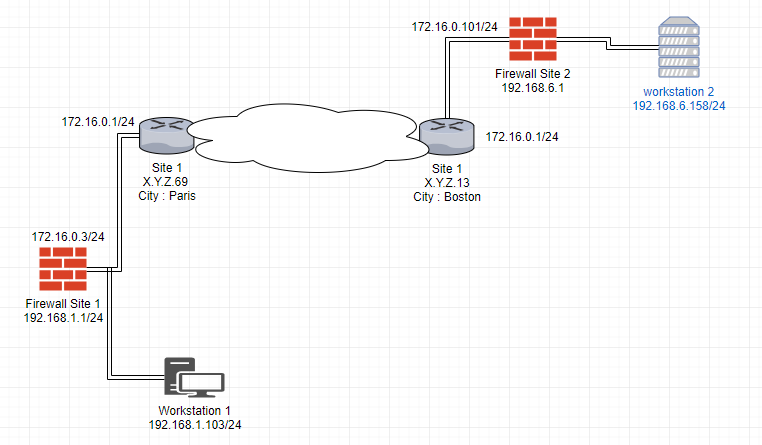
Site to site Pfsense using Openvpn
-
Hi
I have two network
This is the diagram :
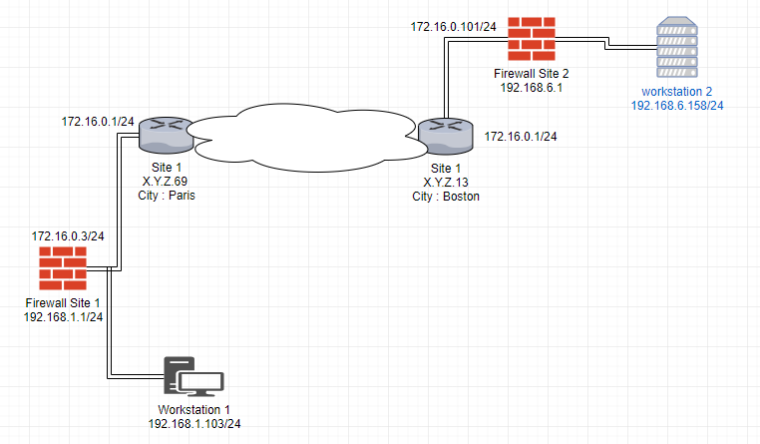
I would communicate from the workstation 1 to the workstation 2
I use Openvpn site to site
Server (Pfsense 1) :
Server mode : Peer to Peer (Shared Key)
Interface : WAN
Port : 1193 (i use 1194 for openvpn remote connection)
IPv4 Tunnel Network : 172.16.20.0/24
IPv4 Remote network(s) : 192.168.6.0/24
-> Save
I add a firewall rules to allow udp from any source to wan address (destination) via port 1193Client (pfsense 2)
Server mode : peer to peer (shared key )
Server host or address : X.Y.Z.69
Server port : 1193
Shared key : the same in pfsense 1 of corse
IPv4 Tunnel Network : 172.16.20.0/24
IPv4 Remote network(s) : 192.168.1.0/24
-> Save
the state is always " reconnecting; ping-restart " (i restart the service in both pfsense , the 1193 is open in the two router )
openvpn 70003 Re-using pre-shared static key openvpn 70003 Preserving previous TUN/TAP instance: ovpnc1 openvpn 70003 TCP/UDP: Preserving recently used remote address [AF_INET]X.Y.Z.69:1193openvpn 70003 UDPv4 link local (bound): [AF_INET]172.16.0.101:0
openvpn 70003 UDPv4 link remote: [AF_INET]XY.Z.69:1193
openvpn 70003 Inactivity timeout (--ping-restart), restarting
openvpn 70003 SIGUSR1[soft,ping-restart] received, process restarting
openvpn 70003 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
openvpn 70003 Re-using pre-shared static key
openvpn 70003 Preserving previous TUN/TAP instance: ovpnc1
openvpn 70003 TCP/UDP: Preserving recently used remote address: [AF_INET]X.Y.Z.69:1193
openvpn 70003 UDPv4 link local (bound): [AF_INET]172.16.0.101:0
openvpn 70003 UDPv4 link remote: [AF_INET]X.Y.Z.69:1193
openvpn 70003 Inactivity timeout (--ping-restart), restarting
openvpn 70003 SIGUSR1[soft,ping-restart] received, process restartingHow i can resolve that ??
-
The upstream routers will have to be configured to forward port UDP/1193 on the server side to pfSense.
-
@derelict yes , the port 1193/udp is open in the two routers
-
Any Help

-
https://www.netgate.com/docs/pfsense/routing/connectivity-troubleshooting.html
-Rico
-
@joseph-watever-j
From Pfsense Openvpn DocumentationIPv4 Tunnel Network : The suggested default in the GUI of 10.0.8.0/24 is sufficient, but any random unused network inside of the RFC1918 space is recommended. For site-to-site shared key, only a /30 is used, not a /24, even if /24 is specified.
https://www.netgate.com/docs/pfsense/vpn/openvpn/configuring-a-site-to-site-static-key-openvpn-instance.html
-
Yes, but he should get any connection first anyway.
-Rico
-
@rico For this we need the logs from the server side
-
It's always good to run through the Troubleshooting Network Connectivity guide first, when it is still not working he can show us the logs. Config screenshots (OpenVPN + Firewall Rules) are always welcome too.

-Rico
-
This is the log from the server side
Jan 1 11:09:32 openvpn 1047 /usr/local/sbin/ovpn-linkdown ovpns2 1500 1573 172.16.20.1 172.16.20.2 init
Jan 1 11:09:32 openvpn 1047 SIGTERM[hard,] received, process exiting
Jan 1 11:09:32 openvpn 43090 disabling NCP mode (--ncp-disable) because not in P2MP client or server mode
Jan 1 11:09:32 openvpn 43090 OpenVPN 2.4.6 amd64-portbld-freebsd11.2 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Oct 3 2018
Jan 1 11:09:32 openvpn 43090 library versions: OpenSSL 1.0.2o-freebsd 27 Mar 2018, LZO 2.10
Jan 1 11:09:32 openvpn 43284 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Jan 1 11:09:32 openvpn 43284 TUN/TAP device ovpns2 exists previously, keep at program end
Jan 1 11:09:32 openvpn 43284 TUN/TAP device /dev/tun2 opened
Jan 1 11:09:32 openvpn 43284 do_ifconfig, tt->did_ifconfig_ipv6_setup=0
Jan 1 11:09:32 openvpn 43284 /sbin/ifconfig ovpns2 172.16.20.1 172.16.20.2 mtu 1500 netmask 255.255.255.255 up
Jan 1 11:09:32 openvpn 43284 /usr/local/sbin/ovpn-linkup ovpns2 1500 1573 172.16.20.1 172.16.20.2 init
Jan 1 11:09:32 openvpn 43284 UDPv4 link local (bound): [AF_INET]172.16.0.3:1193
Jan 1 11:09:32 openvpn 43284 UDPv4 link remote: [AF_UNSPEC] -
i have changed the IPv4 Tunnel network to 172.16.20.0/30 in the two side but it is the same issue
-
I know this question has been asked a plethora of times before and I have looked over probably 100 different answers and still can't seem to get this to work.
-
server side :
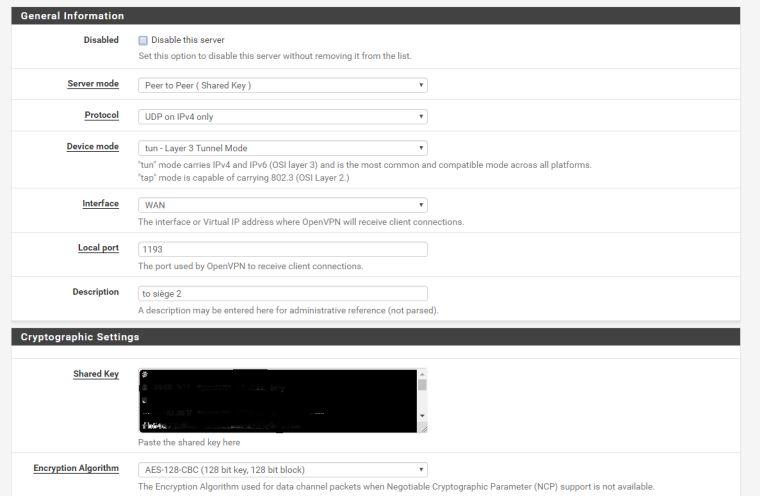
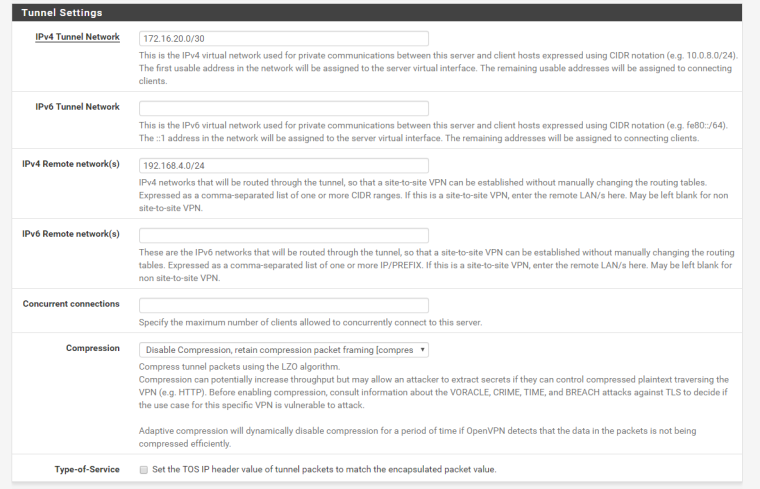
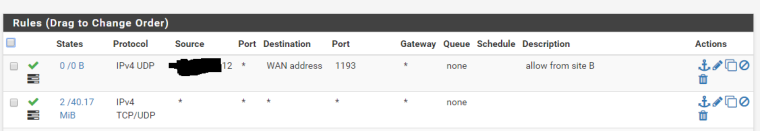
client side :
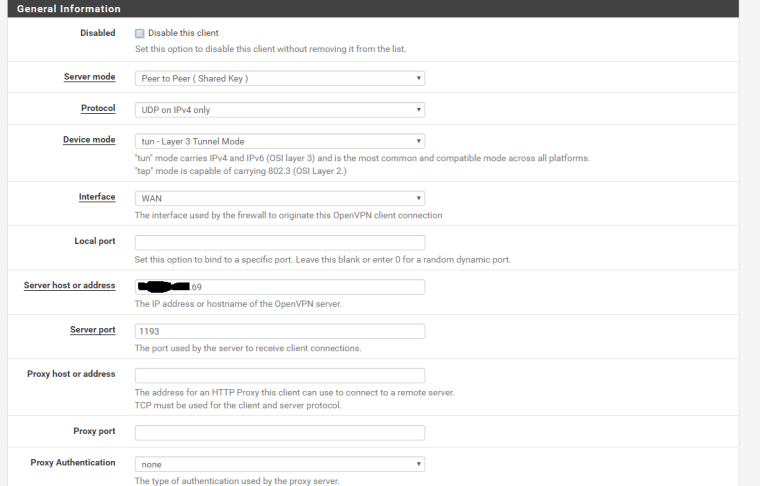
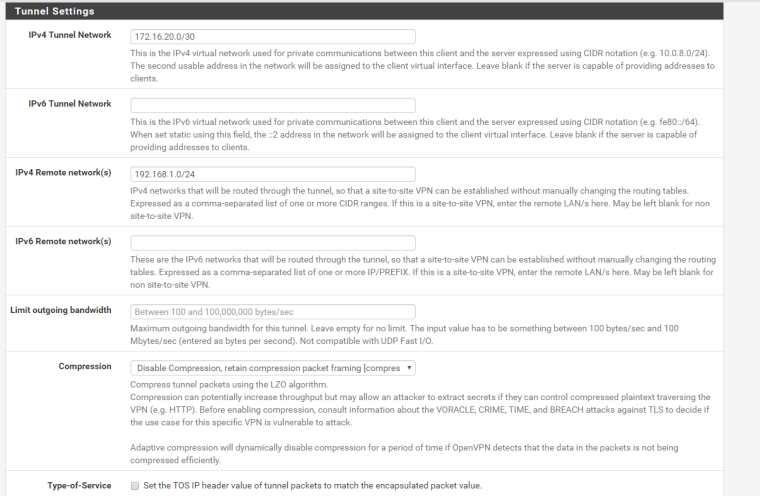
FYI : the IP public in the client side is not static , i look to what is my ip and i used the address
-
@joseph-watever-j
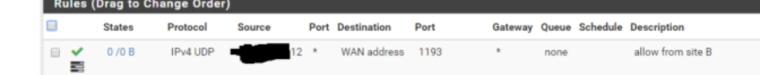
I don't know what the rule is, but- it does not work for you ( 0/0 )
- the number 12 at the end of the address is different from the Boston address x.y.z.13
If the client does not have a white ip, it is better to put any source
This is just a note because the following rule allows everything on TCP/UDP protocols
You show a small part of the log . We need more information. You need to see what happens at the moment of connection
Do I understand correctly that the connections on port 1194 work without problems ?
Farther
in server settings you specify a remote network 192.168.4.0/24 . The picture shows 192.168.6.0/24. Mistake ? -
yes the public ip is not static --> i put the source to any
i have remote vpn connection to the server side using the port 1194 (using ssl/tls + local database) , it is work
in the picture , yes , miskate , no 192.168.6.0/24 but 192.168.4.0/24
the log is the same , i put the log in the server side
there is the log of client side :
Jan 1 14:44:55 openvpn 28395 Inactivity timeout (--ping-restart), restarting
Jan 1 14:44:55 openvpn 28395 SIGUSR1[soft,ping-restart] received, process restarting
Jan 1 14:45:00 openvpn 28395 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Jan 1 14:45:00 openvpn 28395 Re-using pre-shared static key
Jan 1 14:45:00 openvpn 28395 Preserving previous TUN/TAP instance: ovpnc1
Jan 1 14:45:00 openvpn 28395 TCP/UDP: Preserving recently used remote address: [AF_INET]X.Y.Z.69:1193
Jan 1 14:45:00 openvpn 28395 UDPv4 link local (bound): [AF_INET]172.19.0.101:0
Jan 1 14:45:00 openvpn 28395 UDPv4 link remote: [AF_INET]X.Y.Z.69:1193Question : the time of the two firewall is not the same , (time zone ) , any effect on openvpn


-
time doesn't matter as long as its correct.. Doesn't matter what timezone your in..
-
What about configuration
 ?
? -
This post is deleted! -
Your configuration looks fine. I would be sure the traffic is actually passing though all the upstream infrastructure.
It doesn't look like you are posting any connection attempts in the logs. Almost impossible to say what's wrong based on what we have.
-
Can you post this page?