active directory domain trust
-
So you created a new network? on pfsense
And what rules did you put on it? You didn't set a gateway on it did? so you have
lan 192.168.1.0/24
trust 10.0.0.0/24?
And you have a box in 192.168.1/24 say 192.168.1.100 and using pfsense as its gateway? which is what 192.168.1.1
Can this .100 box ping 10.0.0.1?
Rules on lan would default to any any... Where are you creating this "tcp" rule exactly? On the trust interface??? And who is 10.0.0.2?
Rules are evaluated as traffic enters an interface from the network its connected too, top down, first rule to trigger wins, no other rules are evaluated..
How about you draw up your testing setup!!
192.168.1/24 -- lan (pfsense) trust -- 10.0.0/24
??
And post up your rules for lan and trust
-
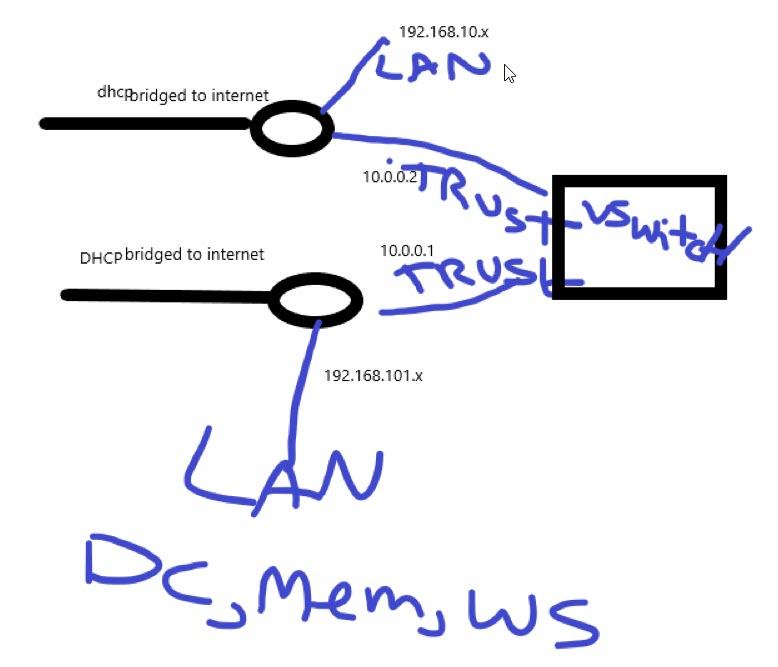
Hope this 3Dpaint picture makes some sense, whas thinking about Visio or packetracer but it is easier sometimes do draw in paint
-
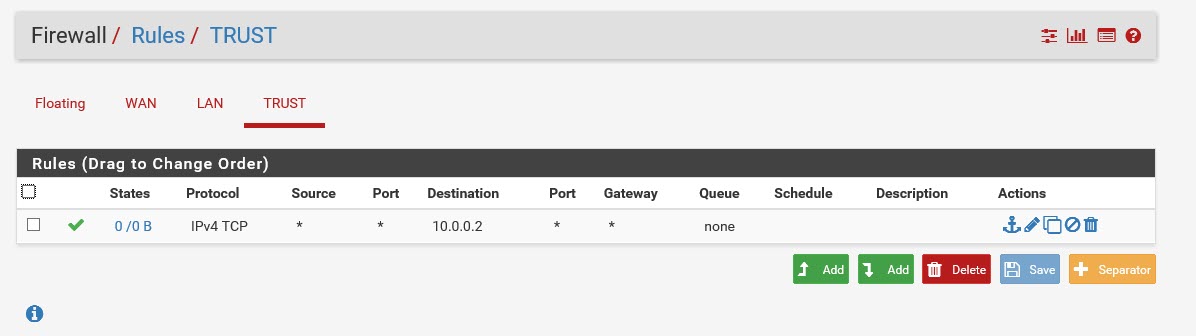
-
vswitch? So this is vm pfsense setup?
Sorry but no that drawing doesn't make a lot of sense... where exactly is pfsense in that drawing, and why do you have 2 different bridged to internet connections?
I don't mind a paint or napkin drawing but its hard to make heads of tails of that nonsense.
If trust network is 10.0.0/24 - then rule to get to 10.0.0.2 is WORTHLESS!! a box on 10.0.0/24 wouldn't talk to pfsense trust IP to get to something on the 10.0.0/24 network.
-
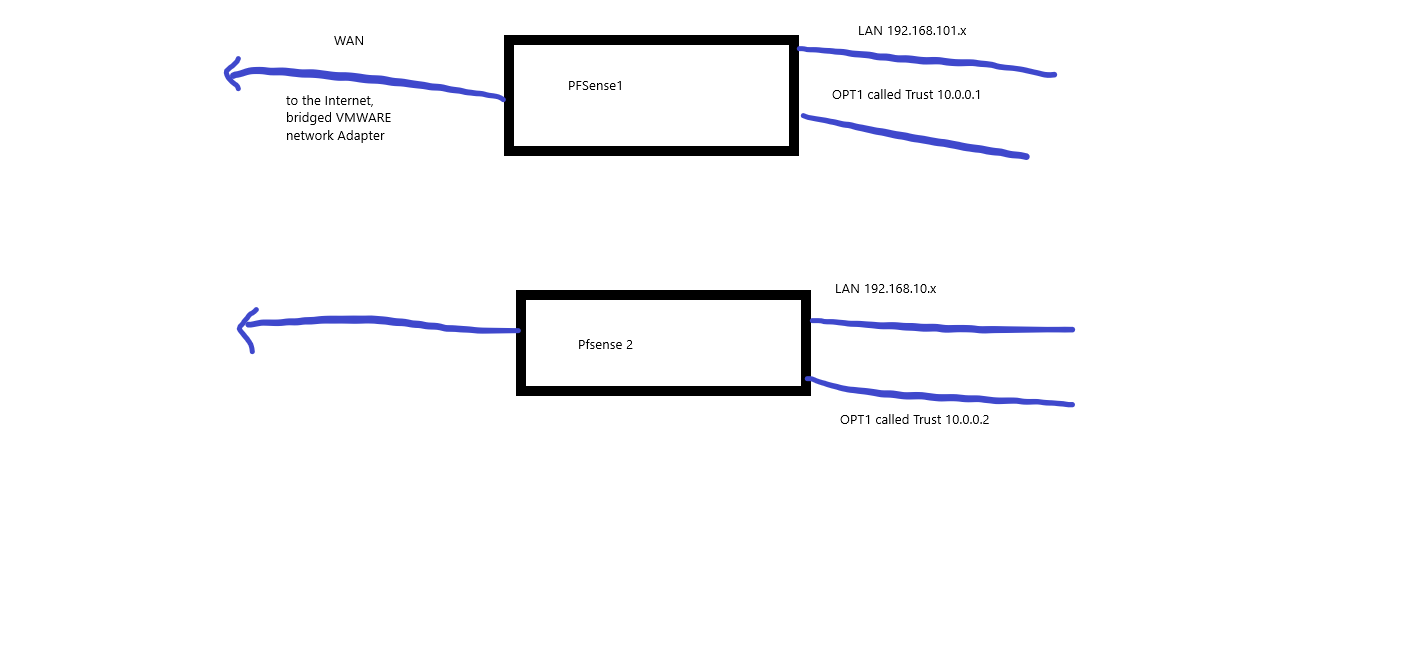
Is this more understandable?
the idea is to let the vpn-connecting for the trust be used by opt1 to have a dedicated connection.
-
And about the routing part, i am still playing with that. All the traffic that needs to go to subnet 192.168.101.x and is coming from 192.168.10.x, should go through the trust(OPT1) connection. other traffic for the Internet should go through the Wan connection. At least, that is what i am thinking, but maybe everything(besides the internet) can be done through the LAN only .
-
@deheugden said in active directory domain trust:
should go through the trust(OPT1) connection.
What?? So you want to create a transit network of 10.0.0/24 Did you setup routing and gateways for that to work?
-
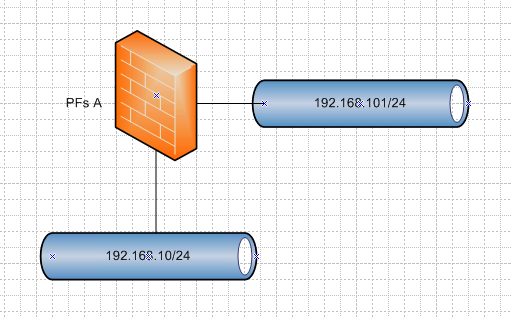
So you want something like this
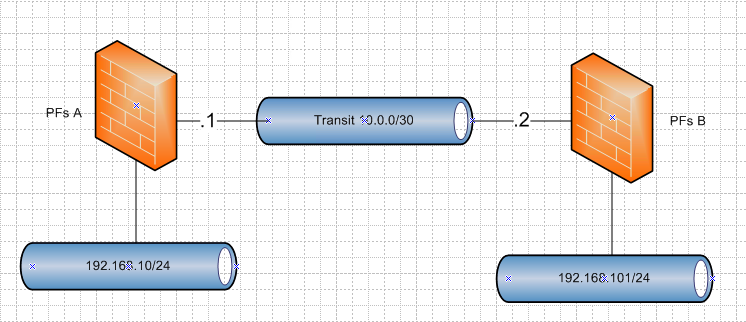
In that case you would have to create
PFs A
gateway 10.0.0.2
route 192.168.101/24 gateway 10.0.0.2PFs B
gateway 10.0.0.1
route 192.168.10/24 gateway 10.0.0.1Be much easier to work out your firewall rules with just single pfsense so you don't have to play with any routing in this phase
-
Your drawing looks better than mine, which tool do you use?
About the 2 Pfsenses, i would prefer the scenario to be realistic. Thats why i am trying to get this done through 2 Pfsenses with a site to site link through VPN. That VPN would be used for my AD Trust.
Maybe 2 Nics will fine, the Wan for both domeins to connect to the Internet and the Lan for the clients and servers. maybe the vpn site to site can be use the WAN or i should start using the Opt1. There is a lot of info on the Internet but often it isnt right for a specific situation. letting 2 domains communicate to each other through their Pfsenses is something i still have got fixed.
-
I use visio for drawing.
Well in your drawing you setup no site to site vpn, using a transit network is not a simulation of vpn.. And to be honest you not going to run an AD trust in the clear over the public internet..
If you want to sim this with a vpn... Then setup your 2 pfsenses and connect them via a vpn and make sure traffic can flow from each others lans to the others lan.
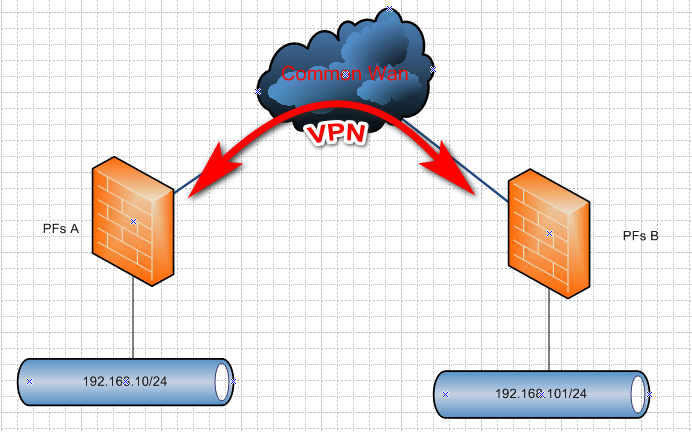
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/configuring-a-site-to-site-ipsec-vpn.html
https://docs.netgate.com/pfsense/en/latest/book/openvpn/site-to-site-example-configuration-shared-key.html -
@johnpoz said in active directory domain trust:
nses and
thanks, for the VPN part i also found this tutorial:
https://www.ceos3c.com/pfsense/pfsense-site-to-site-vpn/