Alias firewall block rule not blocked!
-
Hi!
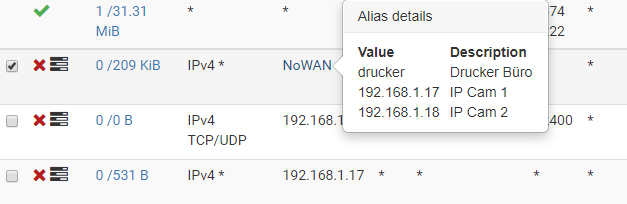
I use an Alias for some clients to block access to WAN. For this I made a block rule on LAN. For two of the clients it works, but for one (192.168.1.17) of them it doesn't. I was wondering why pfTop shows traffic from that client to WAN so I setup a separat rule for that client and then it works as you can see below. I setup the Alias as Hosts and entered every single IP. On firewall logs I see that the 192.168.1.18 gets blocked by the rule with the Alias, the 192.168.1.17 gets blocked by the new rule I made only for that client even it is below the rule with Alias where that client already is in.
But why?
-
Existing active states are not affected by new firewall rule changes. Clear the active states for that connection and then try your test again.
-
I did, I even rebootet the pfSense and the client. Nothing worked! I now deleted the Alias and created it new 1:1. Now it works! Very strange...
-
@mrsunfire said in Alias firewall block rule not blocked!:
I did, I even rebootet the pfSense and the client. Nothing worked! I now deleted the Alias and created it new 1:1. Now it works! Very strange...
Could you have had a space (like a trailing space, perhaps) in your alias? I have not looked at the pfSense PHP code for the Alias page to see if it scrubs input for trailing spaces. I have been the victim of that trailing space thing in other situations not involving pfSense (like a Windows filename, for example). This problem is very hard to detect because a trailing space is going to be invisible on the screen. Sometimes you can tell it's there by going to the end of a line and then you notice an extra space, but then sometimes that trick does not work. The fact deleting and then recreating the alias fixed the problem points to having a hidden character in there maybe.
-
Well the Alias „worked“. One IP and the FQDN worked. Only the other IP not. There was nothing special in it and I did the same again and now it works.
-
'192.168.1.17"@mrsunfire said in Alias firewall block rule not blocked!:
Well the Alias „worked“. One IP and the FQDN worked. Only the other IP not. There was nothing special in it and I did the same again and now it works.
Unless I misunderstood what you wrote and posted originally, you created an alias called NoWAN and put three entries in it. One of those was a hostname "drucker" and the other two were actual IP addresses. The host name would have been internally converted to an IP by the pfSense code. What I am saying is maybe when you put the 192.168.1.17 IP address in you inadvertently had a trailing space on the end when you typed it into the text box on the alias creation page. So instead of just "192.168.1.17" you actually had "192.168.1.17 " (notice the extra space after the 17). To a computer "192.168.1.17 " is not the same as "192.168.1.17". You would not have been able to see this trailing space on the screen. When you deleted the alias the trailing space entry would have also been removed. When you created it again the trailing space was not there and so things worked as expected.
This is just a theory based on having this type of event happen to me in the past on other platforms. It's easy to typo a trailing space on something and then you can't see it's there to fix it. Some software will automatically scrub user-typed input to remove trailing spaces, but not always. I need to check the pfSense code to see if it does that when letting the user create alias entries.
-
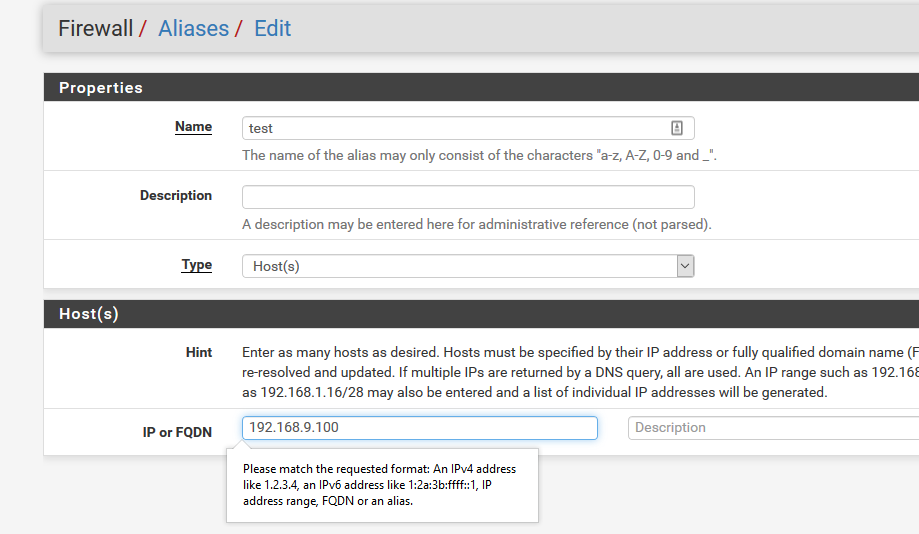
If you put a trailing space on it - pfsense balks at you
-
@johnpoz said in Alias firewall block rule not blocked!:
If you put a trailing space on it - pfsense balks at you

Thanks for the quick test! So my theory is not valid. pfSense apparently does a good job of input scrubbing.
-
Without seeing is full rule set, floating even and his current states its not really possible to understand what the issue might of been.
Its quite possible this .17 had a state open to internet he was testing with.. Which is why it was working when he first put in the rule.. Or for that matter maybe the .17 uses proxy..
KOM really hit it on the nose - and it causes many users misunderstanding of how rules and when they get applied..
-
@johnpoz said in Alias firewall block rule not blocked!:
Without seeing is full rule set, floating even and his current states its not really possible to understand what the issue might of been.
Its quite possible this .17 had a state open to internet he was testing with.. Which is why it was working when he first put in the rule.. Or for that matter maybe the .17 uses proxy..
KOM really hit it on the nose - and it causes many users misunderstanding of how rules and when they get applied..
I agree it could have been an active state, but it is puzzling still as the state should still have been in place when he added that independent rule with just the IP and not the alias. So I would expect that extra rule to not block either. Of course, we don't know the full extent of what the rules in force were at the time.
That trailing space thing is just etched in my brain now because I've been victimized several times by it over the years. Most recently about two months ago on my wife's Windows 10 machine where she complained about not being able to delete a directory. Turns out, after much investigation, it was the trailing space thing again.
-
There was no active state. I checked it multiple times with pfTop. Even after reboot the .17 got wide open access to internet. The Alias had no problem, no extra space or something else. I now created it exactly the same and now also the .17 gets blocked.
I only have 1 Floating rule for ICMPv6, nothing special on LAN. The Alias always is on top of course. There is no proxy setup.
-
If the IP address was in the alias and there was no active state it would have been blocked.
If something else was the result then there was a reason for it. Finding that reason is the trick.
When you have an active state you can use
pfctlto find which rule passed the connection should you desire to dig that deep. If I had traffic I thought should be blocked that wasn't, I would want to know why. -
There should be no active state after a reboot. I now did the same as before and now the IP gets blocked. If I could simulate that error again, I would do that.
-
It was user error. You did not find a bug in pf that passed blocked traffic.
-
Then how do you explain from my first screen that the alias is on top and the .17 IP is on 3th line of rules. But that one blocks the traffic and the alias did not?
-
User error. Not understanding what you are looking at. State established before the rule was in place. Some other rule passing the traffic.
-
So the state stays established even after a reboot? I can't believe that...
-
No. The state was re-established after you rebooted because a firewall rule passed the traffic.
-
I restored the firewall rules to an earlier date and rebooted the machine. The alias is still the same and now the .17 again gets access. How to find out what rule is the problem?
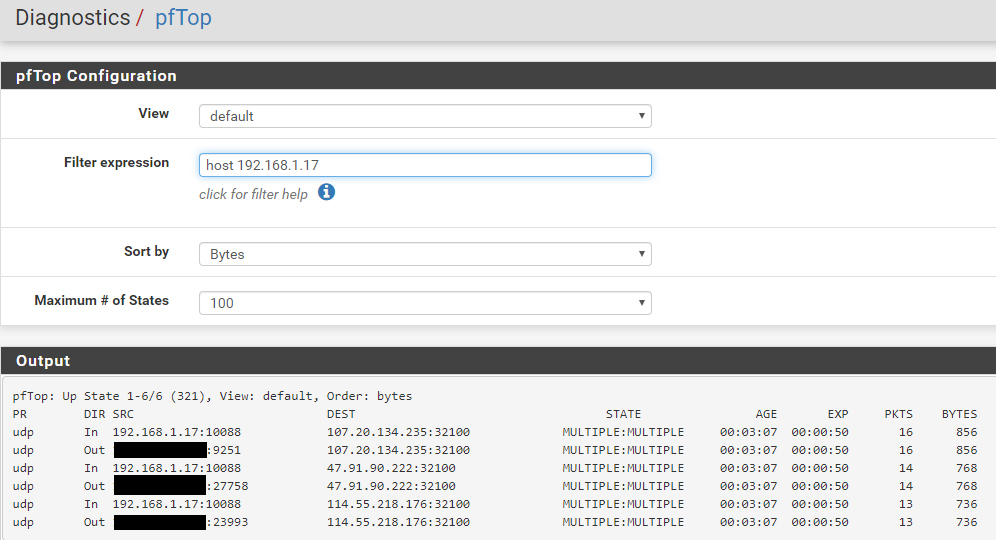
-
pfctl -vvss | grep -A3 192.168.1.17Find the state you think should not be there out of that. Post it.