DNSBL just Work when DNS Resolver Enable
-
Hello people,
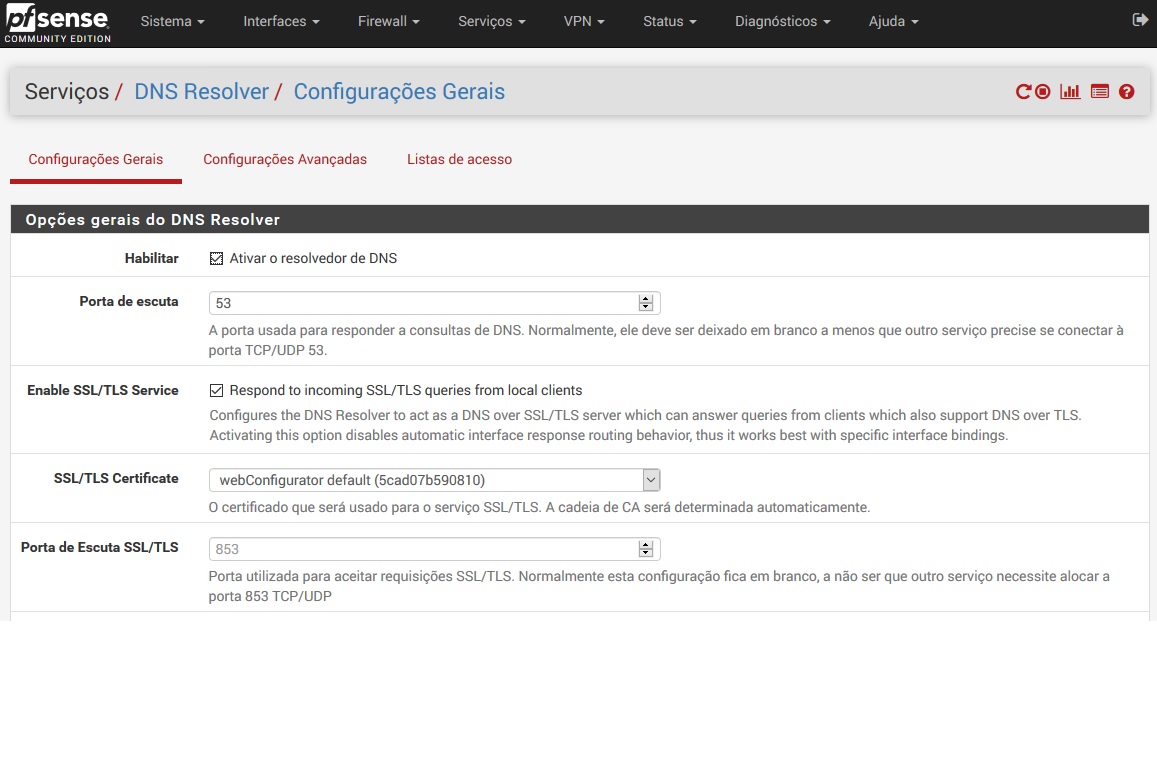
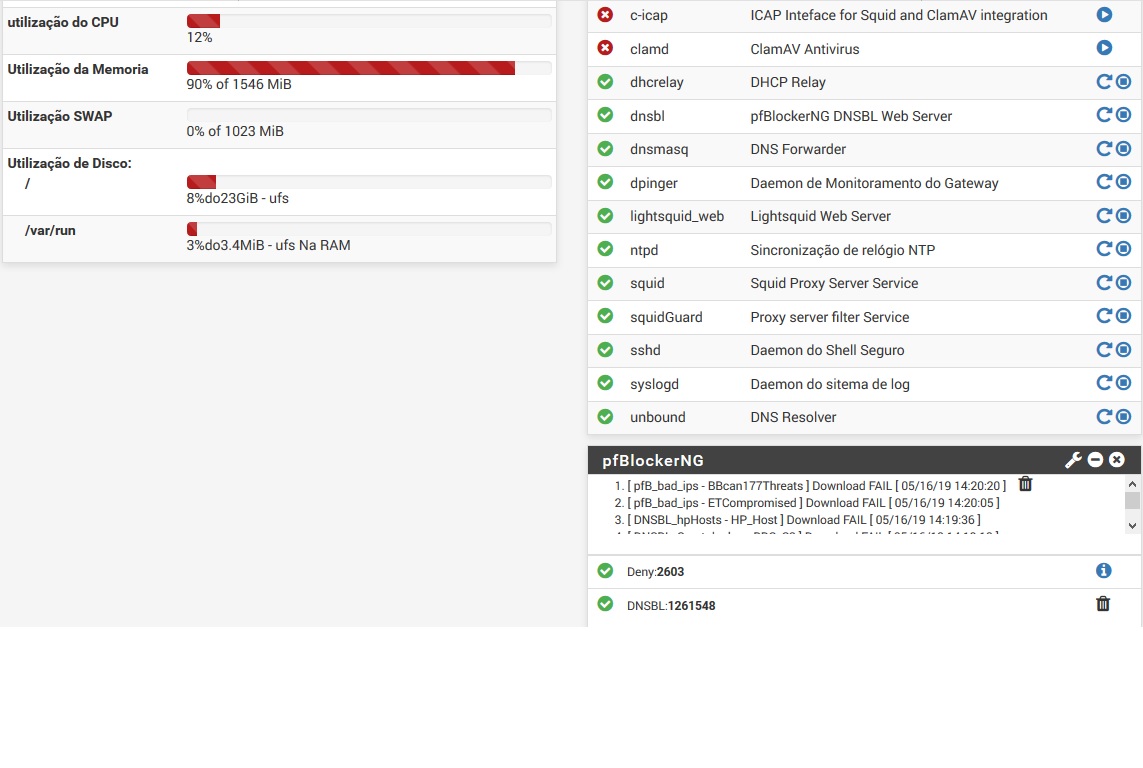
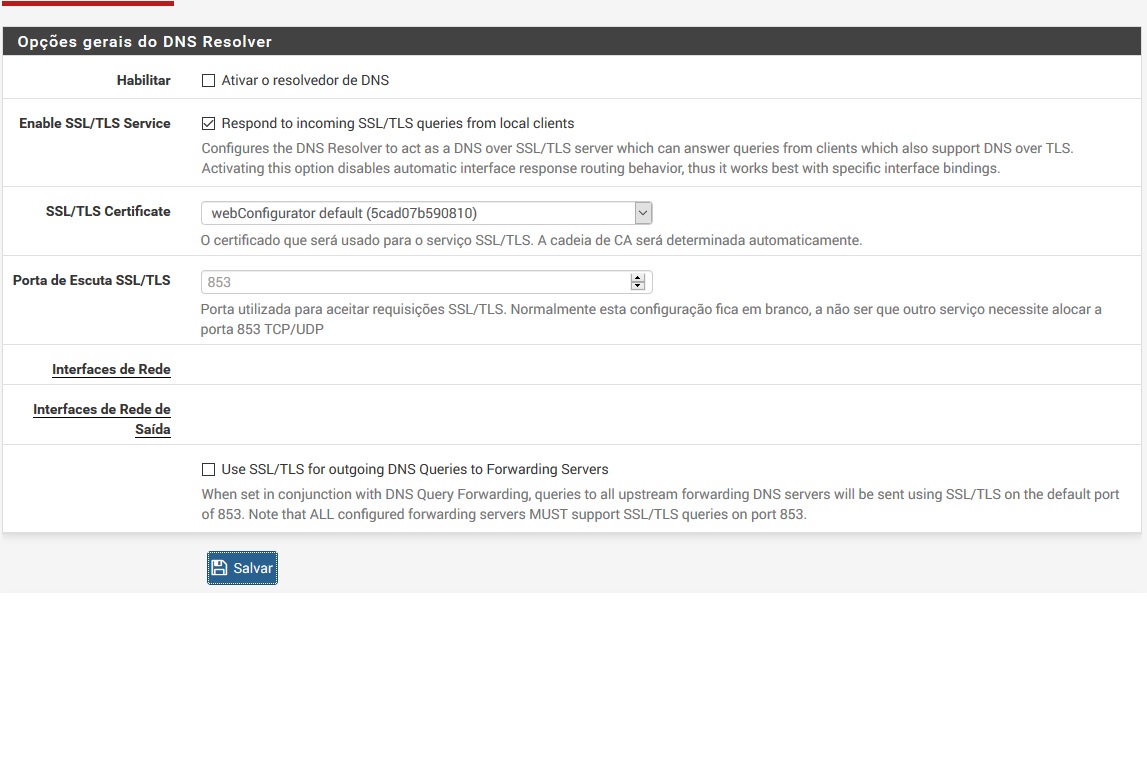
I'm setting up a pfsense, but the DNBL package pfBloquerNG only works when I activate DNS Resolver. My problem is that AD (Active Directory is a DNS Server by default when we enable AD). How do I run the DNSBL pfBloquerNG without activating the DNS Resolver in pfsense?
2
3
4
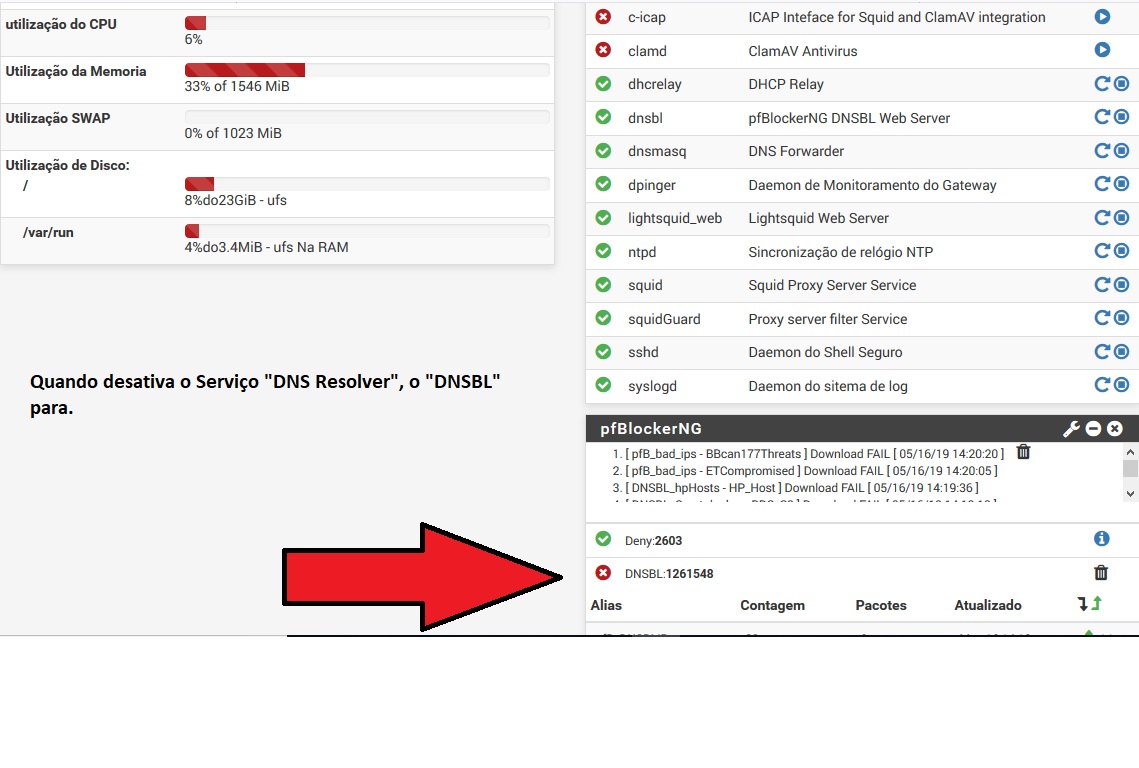
Note: The AD is a DHCP Server and DHCP Relay is enable on pfsense.
-
@Marcus-Vinicius said in DNSBL just Work when DNS Resolver Enable:
How do I run the DNSBL pfBloquerNG without activating the DNS Resolver in pfsense?
You can't, pfblockerNG require the DNS Resolver.
You don't have enough memory to run DNSBL with 1.25M entries. I have 8GB mem with 1.2M entries and I ran into problems like unbound hanging on restart.
-
@RonpfS said in DNSBL just Work when DNS Resolver Enable:
How do I run the DNSBL pfBloquerNG without activating the DNS Resolver in pfsense?
Easy. Don't use DNSBL. pfBlockerNG are two tools in one. One side is blocking requests on IP level (the upper green hook you see), the other side is DNS blacklisting. If you don't want that because AD does your DNS so disable DNSBL and be done. That has nothing to do with pfBNG needing it. It doesn't. You can use one, both, none. But don't consider DNS requests blackholed or blocked if your AD does your DNS. You only use IP blacklisting then.
Besides: I don't get your point. MS AD needs forwarders or resolving, too, so instead of panicking, how about setting your DNS up letting pfSense serve DNS requests and make a domain override for your AD DNS domain in "DNS Resolver" configuration and point that to your domain? Any reason you'd need the AD DNS for anything at all?
-
This post is deleted! -
Marcus Vinicius 5 minutes ago
Thank you. I set up "DNS Forwarder" on pfsense but i don't know we can use MS AD with DNS Resolver Enable? Cause by default AD is a DNS Server. In AD point my pfsense server as a DNS Server.
-
We have a similar set up and this is how we got it working.
-
Have the DHCP server issue the IP address of the AD DNS Server as the DNS server to all of the domain machines.
-
On the AD DNS Server create a forward to the the pfsense box so that non authoritave dns requests on the AD DNS Server are routed to pfsense (the default is that they use root hints for those requests). In Server 2012 this would be done in the DNS Manager by right clicking the the named DNS server, selecting properties, then going to the Forwarders tab. Select All interfaces, and enter the pfsene box's ip address.
-
In the pfsense box enable resolver.
-
Configure pfblockerNG as normal.
In this way, the domain machines will first look to the AD DNS to resolve all DNS requests. If the name is resolved there then the request is answered, so any domain names hosted locally on the AD network will be resolved. If the name is not found on the AD DNS then the DNS request is forwarded to pfsense for resolution.
-
-
^ Yup that is how you would do it..
-
@dma_pf said in DNSBL just Work when DNS Resolver Enable:
We have a similar set up and this is how we got it working.
-
Have the DHCP server issue the IP address of the AD DNS Server as the DNS server to all of the domain machines.
-
On the AD DNS Server create a forward to the the pfsense box so that non authoritave dns requests on the AD DNS Server are routed to pfsense (the default is that they use root hints for those requests). In Server 2012 this would be done in the DNS Manager by right clicking the the named DNS server, selecting properties, then going to the Forwarders tab. Select All interfaces, and enter the pfsene box's ip address.
-
In the pfsense box enable resolver.
-
Configure pfblockerNG as normal.
In this way, the domain machines will first look to the AD DNS to resolve all DNS requests. If the name is resolved there then the request is answered, so any domain names hosted locally on the AD network will be resolved. If the name is not found on the AD DNS then the DNS request is forwarded to pfsense for resolution.
One last item I would suggest is to put your AD domain in as a Domain Override in the DNS Resolver on pfSense and point back to your AD DNS for that entry. That will allow pfSense to resolve your internal host IPs on the LAN to their actual host names when logging stuff or displaying the ARP table, etc.
-
-
@johnpoz said in DNSBL just Work when DNS Resolver Enable:
^ Yup that is how you would do it..
I'm curious as to why. Why use MS AD DNS for everything instead of only the things absolutely needed (e.g. internal domain)? So why not use clean DNS Resolver setup on pfSense and Domain overwrite for ADs <lan.domain.tld> to the internal resolver?
Just wondering where one is preferable to the other, as with the resolver method, I've got a modern DoT-capable and DNSSEC enabled resolver working instead of that MS DNS monster with that caching of hell ;)
-
If you want to just use domain overrides for your AD, sure you could do that - but you understand that there is more domains than just domain.tld right in an AD..
Going to be a bunch of subs _msdcs. _tcp, _udp - etc. So its a bit more involved than just asking the AD NS for server.domain.tld
To be honest if your a MS house using AD - just use that for dhcp, and dns.. Its just way easier - and your sure clients will be able to register themselves in the dns, etc. etc..
Don't forget all your ptrs you would also need to setup as overrides..
Just doesn't make a lot of sense for ease of configuration and possible troubleshooting to point your clients to pfsense for dns and or use it for dhcp when your a MS shop and you have any server to be able to provide these functions and along with failover and redundancy... Just because pfsense can provide some dns and dhcp doesn't mean you should do that.
If your network has grown beyond 1 single segment... your AD dhcp also can provide all the different segments dhcp in central location, etc. With MS dhcp can register clients in dns for you, etc..
-
@johnpoz said in DNSBL just Work when DNS Resolver Enable:
To be honest if your a MS house using AD - just use that for dhcp, and dns.. Its just way easier - and your sure clients will be able to register themselves in the dns, etc. etc..
That I agree totally.
-
@bmeeks hello bro, would you mind to give the example of Domain Override back to AD DNS as you suggest?
-
@sokeada At the bottom of the DNS Resolver settings page, add an override.
Domain: your AD domain, e.g. example.local
IP: your AD DNS server LAN IPRepeat for each DNS server.
-
@SteveITS said in DNSBL just Work when DNS Resolver Enable:
@sokeada At the bottom of the DNS Resolver settings page, add an override.
Domain: your AD domain, e.g. example.local
IP: your AD DNS server LAN IPRepeat for each DNS server.
Thanks brother,
Domain: your AD domain -> my AD FQDN or just domain? example: domain is abc.com and FQDN of the AD is dc1.abc.com.
-
@sokeada Fully depends on what you're trying to do. If you want to resolve all of your domain and subdomains via that override, then use your domain
example.tld, if it's only AD stuff you want to resolve then usedc1.example.tld.So if e.g. you're running an AD on
lan.lab.testand you're trying to fix resolving addresses likedc1.lan.lab.testanddc2.lan.lab.testorexchange.lan.lab.testthen you would create two overrides and enter the AD domainlan.lab.testas domain in both and the IP of both DCs as the lookup server IP. In this example let's assume your DCs are dc1/dc2 and they run at 10.5.0.11/12: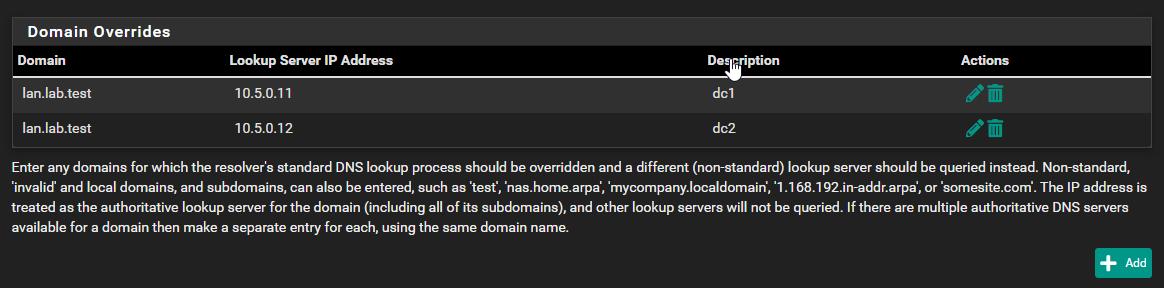
Thus your domain override would span
lan.lab.testand all queries to*.lan.lab.testwould be forwarded to eitherdc1ordc2in case one of them is down for maintenance. DNS queries toxyz.lab.testwould still resolve but not be forwarded to those DCs but rather resolved via the public DNS of the zonelab.testso a public runningwww.lab.testwould still resolve and have the public DNS entries that zone provides as you only directed the subdomainlanto your DCs.Of course if you used an entire domain for your ad, you can set that up, too but shouldn't really use that domain in a public non-LAN context.

-
@JeGr said in DNSBL just Work when DNS Resolver Enable:
@sokeada Fully depends on what you're trying to do. If you want to resolve all of your domain and subdomains via that override, then use your domain
example.tld, if it's only AD stuff you want to resolve then usedc1.example.tld.So if e.g. you're running an AD on
lan.lab.testand you're trying to fix resolving addresses likedc1.lan.lab.testanddc2.lan.lab.testorexchange.lan.lab.testthen you would create two overrides and enter the AD domainlan.lab.testas domain in both and the IP of both DCs as the lookup server IP. In this example let's assume your DCs are dc1/dc2 and they run at 10.5.0.11/12:
Thus your domain override would span
lan.lab.testand all queries to*.lan.lab.testwould be forwarded to eitherdc1ordc2in case one of them is down for maintenance. DNS queries toxyz.lab.testwould still resolve but not be forwarded to those DCs but rather resolved via the public DNS of the zonelab.testso a public runningwww.lab.testwould still resolve and have the public DNS entries that zone provides as you only directed the subdomainlanto your DCs.Of course if you used an entire domain for your ad, you can set that up, too but shouldn't really use that domain in a public non-LAN context.

thanks brother for the detail. My case is like post owner, I've windows server as dns & dhcp for lan network and my solution is forward dns request in my windows domain to pfsense box to block ads using pfblockerng but in report shown my dc1 & dc2 request, not client ip or address request that's why I try to override dns but it seems doesn't work, I've tried like your example.
thus I've another vlan network for mobile devices by using dns & dhcp form pfsense, browsing internet is working fine but when i perform nslookup it shown default server UnKnown but IP shown correctly. Any suggestion, please. :)
-
@sokeada Sorry not quite sure I understand your specific problem correctly. The DNS server showing up with name "unknown" would only be a reverse lookup not working. Sad but not a real problem with resolution, but should be fixable with setting a correct host name with a Host Override. But that aside I don't exactly understand what is NOT working? Could you be more specific?
You have another VLAN set up. DNS and DHCP come from pfSense. Browsing internet is fine - thus DHCP and DNS seem to work fine, too. Is the "unknown" the only "problem" you're seeing? Then I'd assume it's just your pfSense IP from that specific VLAN network, that doesn't resolve back to the correct name. You could just add a host override for that and set it up like
<IP for pfSense on mobile device VLAN> pfSense.your.name
Save & Apply and re-check your mobile client. Also check your DHCP settings for that VLAN and what DNS and what domain and search domain(!) you hand out to the client. I'd set that to something like "lab.test" (like in my example) or if you want to separate domain from non-domain DNS something like "mobile.lab.test" for that DHCP & interface and set a host override in DNS for pfSense with the IP from that VLAN to something like "pfs.mobile.lab.test".
Otherwise I'd need more details or screenshots of your setup. :)
-
@JeGr thanks for your comments bro. I've some clues that the UnKnow issue when clients that received IP & DNS from pfSense when perform nslookup is could be from unbound python mode in DSBL Mode but I'm not yet try to change to default unbound mode yet, I'm happy with that because clients don't need to be seen my pfSense box.
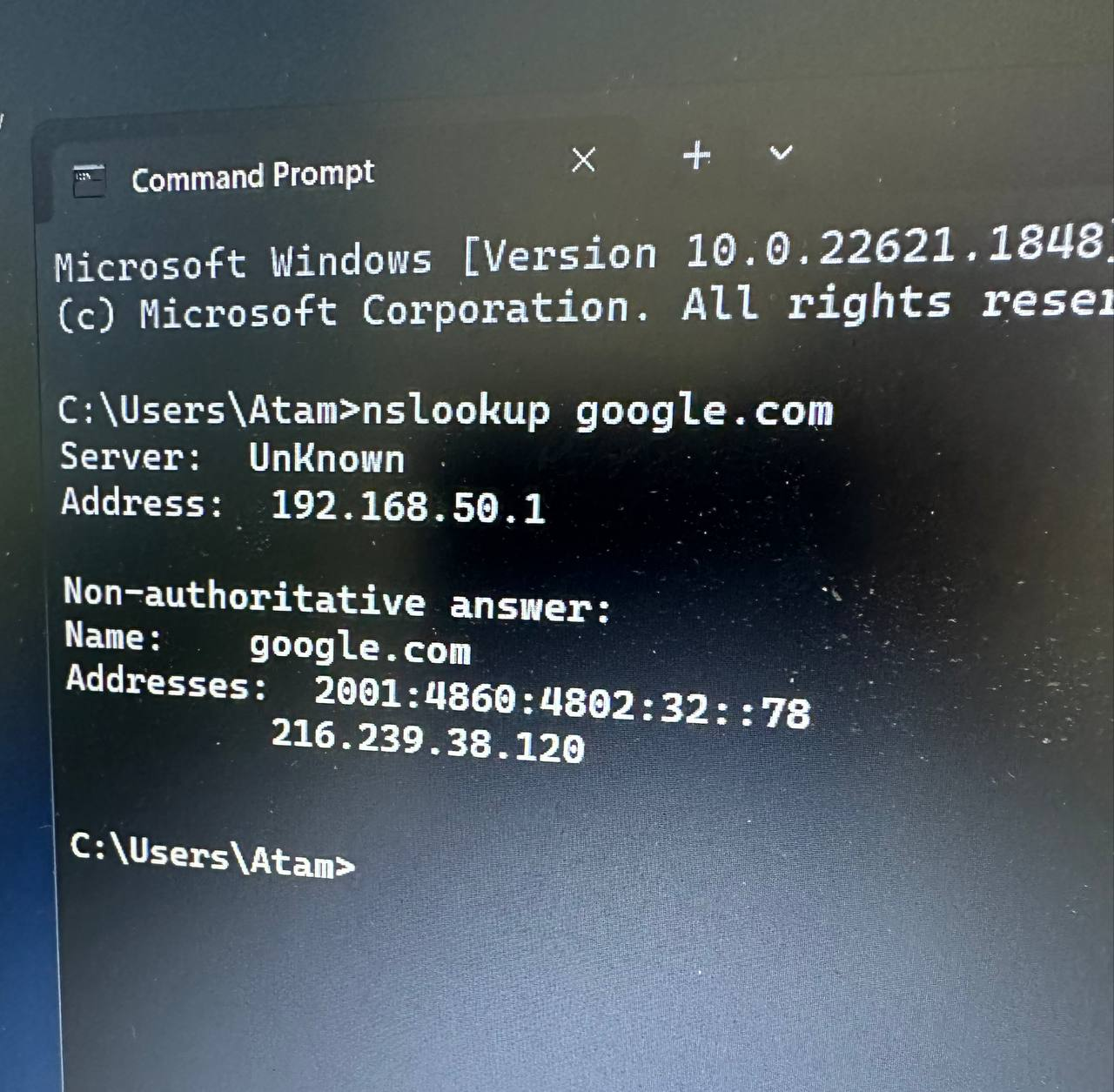
Another issue is, I forwarded dns request from windows server dns to pfSense to block Ads. Everything work fine but in DNSBL report only shown my windows dns request, not clients behind my windows dns. I also get some clue that the only possible way to show clients ip or host name in DNSBL report is only point my clients behind windows dns to pfSense instead.
-
@sokeada what is 192.168.50.1 ?
Is that pfsense itself, or your DC?
All that is as mentioned is there is no PTR for 192.168.50.1, If you set a host override in pfsense for what 192.168.50.1 is then its name would be returned when nslookup does the ptr..
If that is pfsense IP, it should always return its own name..
I normally point my clients to my pihole, I like the eye candy and its easy to see what is being asked for, what is being blocked.. pfblocker can do pretty much the same thing as pihole, but I like the eye candy pihole presents more than pfblocker ;)
But see when I change the server over to unbound on pfsense, it returns the name via the ptr the nslookup does on the server IP.
$ nslookup Default Server: pi.hole Address: 192.168.3.10 > server 192.168.9.253 Default Server: sg4860.local.lan Address: 192.168.9.253 -
@sokeada With Windows AD and pfBlocker you can either
-
forward Windows DNS to pfSense, and set PCs to use Windows DNS, or
-
use a Domain Override in pfSense to send AD domain requests to your Windows servers, and use pfSense for DNS
Re:unknown, is your PC on pfSense LAN or another interface?
-