Snort Package 4.0 -- Inline IPS Mode Introduction and Configuration Instructions
-
I guess I've never used SID MGMT, so I suppose what you're saying is possible, since you're the one that made the package.

I tend to be more GUI-oriented, so clicking buttons and whatnot is more intuitive to me than a bunch of different config files. If it's really that easy to just add a line to a config file in SID MGMT to have all rules in a category have a drop action, I'd be happy with that then.
-
@virgiliomi said in Snort Package 4.0 -- Inline IPS Mode Introduction and Configuration Instructions:
I guess I've never used SID MGMT, so I suppose what you're saying is possible, since you're the one that made the package.

I tend to be more GUI-oriented, so clicking buttons and whatnot is more intuitive to me than a bunch of different config files. If it's really that easy to just add a line to a config file in SID MGMT to have all rules in a category have a drop action, I'd be happy with that then.
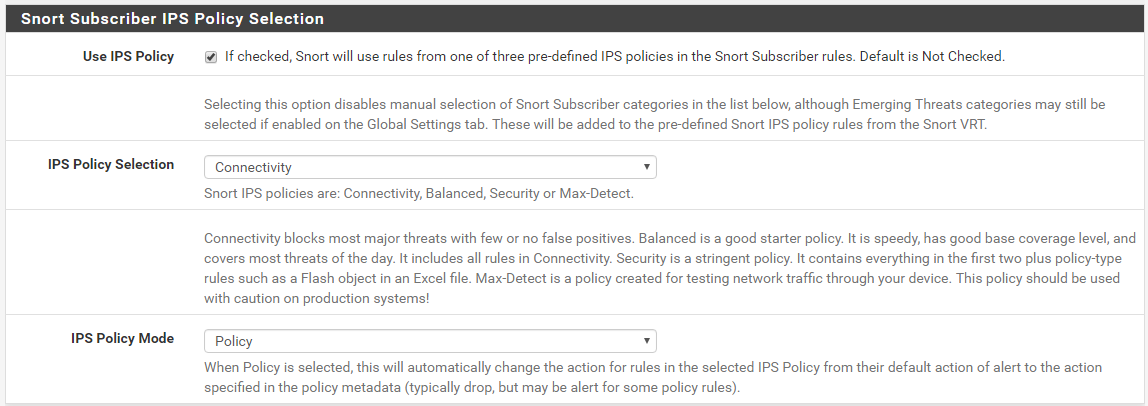
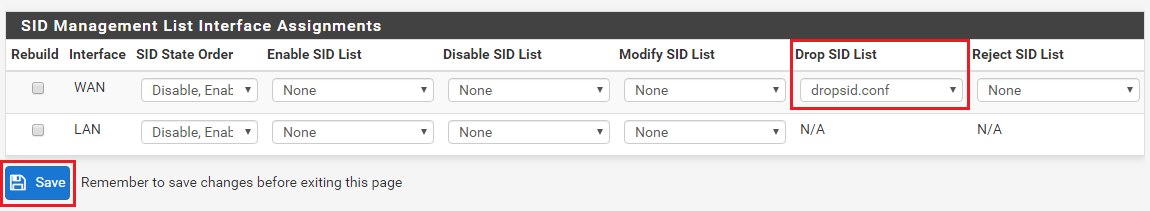
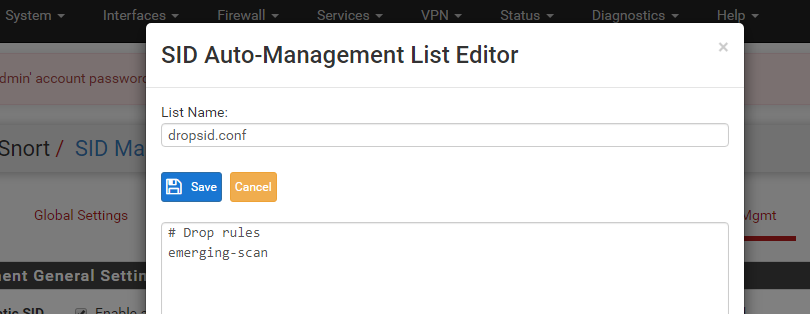
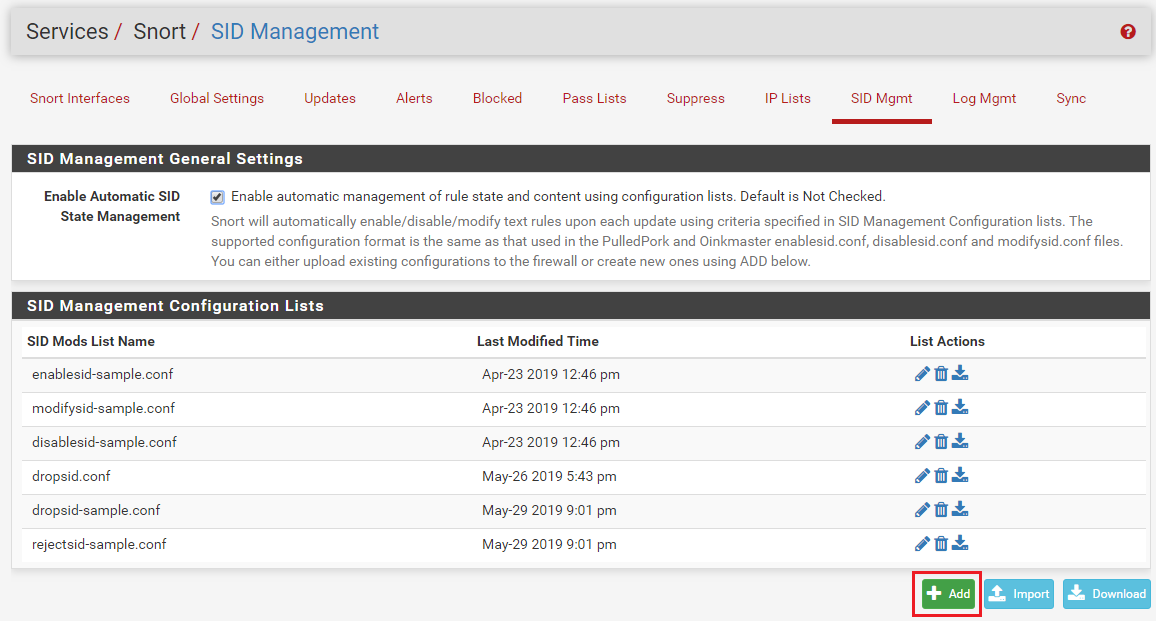
It is that easy. Just create a file named
dropsid.conf(or any name, the name does not matter). Then add the category names (visible on the CATEGORIES tab) or individual GID:SID rule ID pairs. Then save the new file. At the bottom of the tab, assign the list you just created to the DROPSID drop-down. Click the checkbox over on the far left (the "Rebuild" box) to force the creation of a new rules file for that interface and have Snort be sent a "reload rules" command. Open up the sample lists on the SID MGMT tab to see examples of the various selector syntax you can use to choose rules for modification. You can change rule state, action and even content using features on that tab. -
For Snort Inline IPS, are the same config settings needed for netmap like in the Suricata post here? (https://forum.netgate.com/topic/138613/configuring-pfsense-netmap-for-suricata-inline-ips-mode-on-em-igb-interfaces)
-
@rebytr said in Snort Package 4.0 -- Inline IPS Mode Introduction and Configuration Instructions:
For Snort Inline IPS, are the same config settings needed for netmap like in the Suricata post here? (https://forum.netgate.com/topic/138613/configuring-pfsense-netmap-for-suricata-inline-ips-mode-on-em-igb-interfaces)
Likely "yes". Snort simply opens the netmap device and then depends on the kernel settings for any additional configuration options. That's the same way Suricata works. So those tuning parameters outlined in the post you linked may prove helpful depending on the specific NIC hardware you have.
-
@jasonsansone vmxnet3-driver is working without problems in inline mode. i am running this setup since several weeks without problems
-
@bmeeks Thanks a lot for your work. I was missing that feature for a long time.
I have one question regarding the payload dump-option (barnyard-settings).
Is this feature working? I am not getting any dumps for download in the alert-section. Thanks in advance!BR
-
@dotlike said in Snort Package 4.0 -- Inline IPS Mode Introduction and Configuration Instructions:
I have one question regarding the payload dump-option (barnyard-settings).
Is this feature working? I am not getting any dumps for download in the alert-section. Thanks in advance!BR
I honestly do not know. I have not run Barnyard2 on my personal system for several years. The package is no longer really supported on FreeBSD (and I'm not sure it is supported anywhere anymore). By "supported" I mean updated and maintained. The only updates to the package in FreeBSD Ports have been done by the FreeBSD team themselves and involved only minor tweaks to the Makefile for various ports tree dependency issues. Nothing has been touched in the actual Barnyard2 source code in years. I know that it has issues with more recent versions of MySQL client.
So long lead-in to say Barnyard2 seems to be slowly decaying on the vine. The new direction in the Snort3 branch is JSON logging (much like Suricata has).
As for the current situation in pfSense, you can examine the Barnyard2 configuration file for the interface to see what is set in there. You can find the file in
/usr/local/etc/snort/snort_xxxx(where thatxxxxxwill be a random UUID combined with the physical interface name). -
If only 2 or 3 rules in a category need to be ALERTed, the rest need to be DROP, what will be the easiest way to set up?
-
@pfcode said in Snort Package 4.0 -- Inline IPS Mode Introduction and Configuration Instructions:
If only 2 or 3 rules in a category need to be ALERTed, the rest need to be DROP, what will be the easiest way to set up?
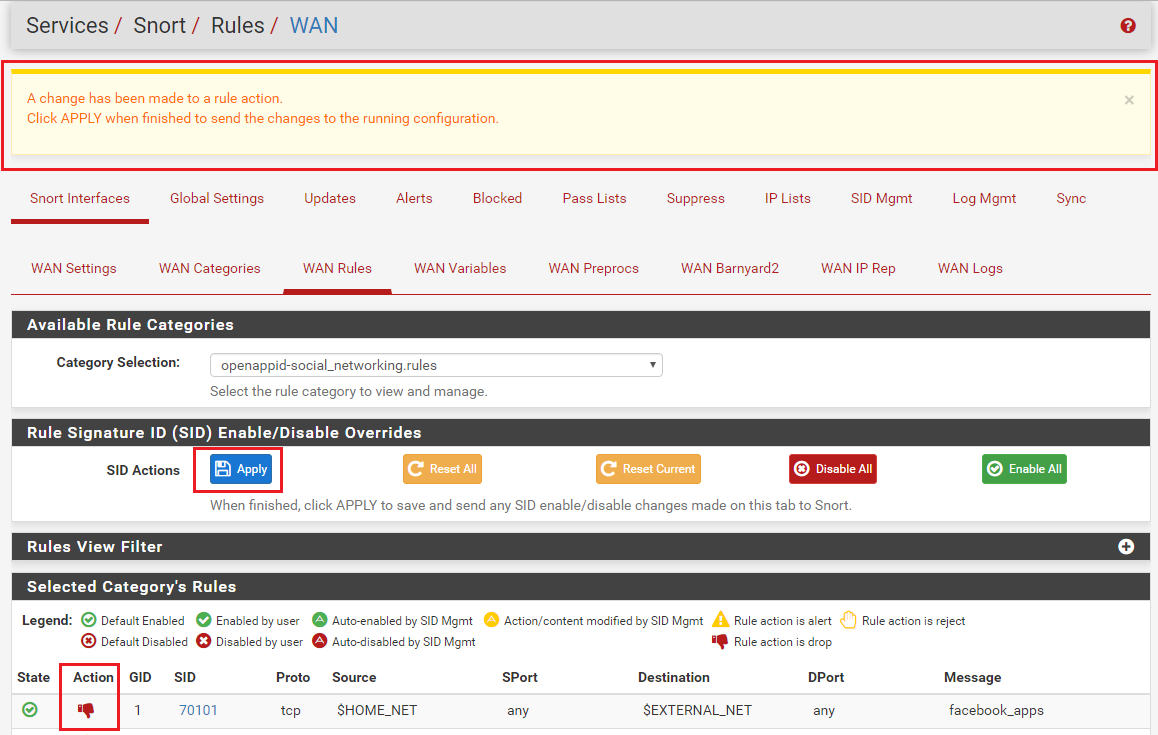
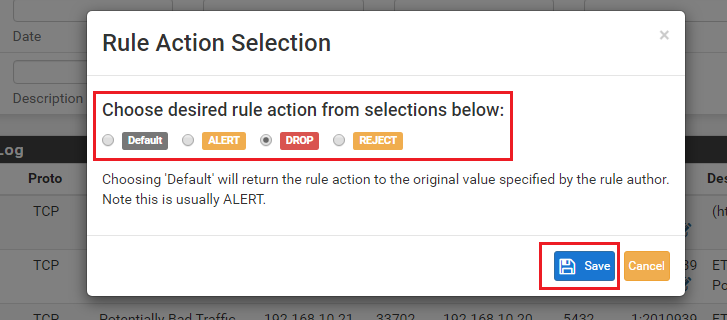
Use SID MGMT features to set the category to DROP. Then go to the RULES tab, select that category in the drop-down selector and find the 2 or 3 rules you want to be ALERT and change the action of just those rules using the icon under the ACTION column. Changes you make to individual rules on the RULES tab take precedence over all other modifications. Those are the last changes applied to rules.
-
@bmeeks Thank you.
-
This post is deleted! -
@bmeeks Is it also possible to mark packets with the new Inline IPS Mode? This would allow the Traffic Shaper to apply rules based on the hostname, for example.
-
@tbr45 said in Snort Package 4.0 -- Inline IPS Mode Introduction and Configuration Instructions:
@bmeeks Is it also possible to mark packets with the new Inline IPS Mode? This would allow the Traffic Shaper to apply rules based on the hostname, for example.
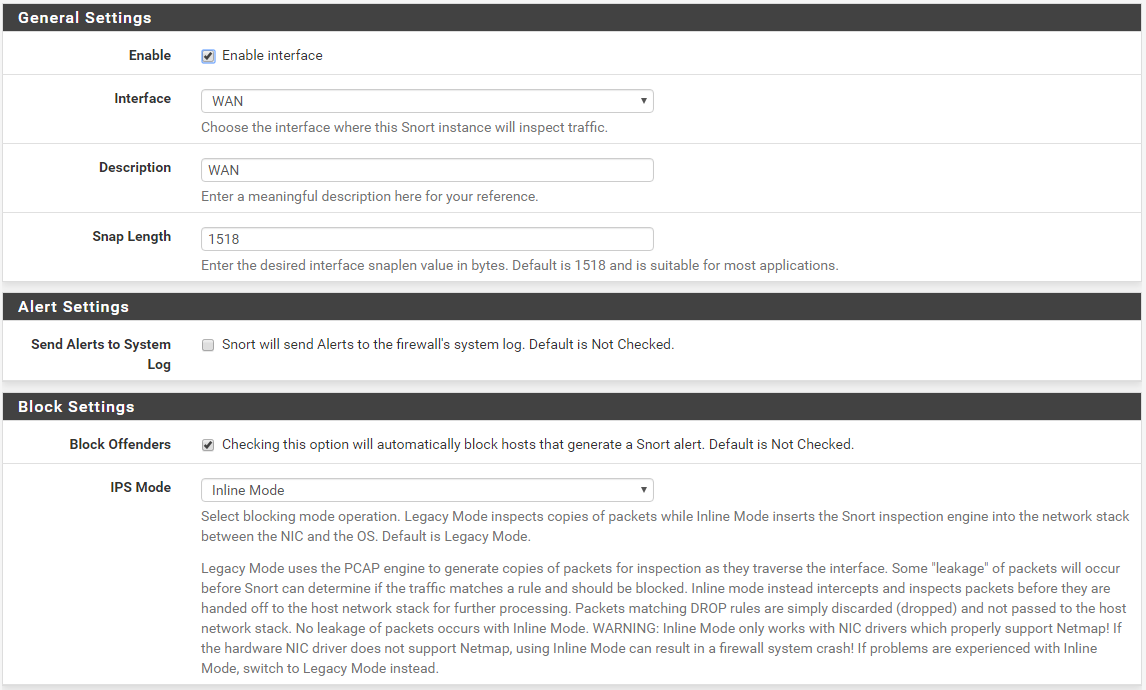
No, you can't mark packets. The binary can only pass them, reject them or drop them. A reject sends a notice back to the sender so it will not keep trying. A drop sends back nothing to the sender (the packet just appears to have fallen into a blackhole).
-
I am experiencing very strange behavior . Manged to track it down to one of emerging-scan.rules.
alert tcp $HOME_NET any -> any 445 (msg:"ET SCAN Behavioral Unusual Port 445 traffic Potential Scan or Infection"; flags: S,12; threshold: type both, track by_src, count 70 , seconds 60; metadata: former_category SCAN; reference:url,doc.emergingthreats.net/2001569; classtype:misc-activity; sid:2001569; rev:14; metadata:created_at 2010_07_30, updated_at 2017_05_11;)Rule was set by Automatic SID managed to DROP, however no alert appeared in Alert List. But until I changed action for the rule from DROP to Alert, I could not get access to remote SMB share...
-
@murzik said in Snort Package 4.0 -- Inline IPS Mode Introduction and Configuration Instructions:
I am experiencing very strange behavior . Manged to track it down to one of emerging-scan.rules.
alert tcp $HOME_NET any -> any 445 (msg:"ET SCAN Behavioral Unusual Port 445 traffic Potential Scan or Infection"; flags: S,12; threshold: type both, track by_src, count 70 , seconds 60; metadata: former_category SCAN; reference:url,doc.emergingthreats.net/2001569; classtype:misc-activity; sid:2001569; rev:14; metadata:created_at 2010_07_30, updated_at 2017_05_11;)Rule was set by Automatic SID managed to DROP, however no alert appeared in Alert List. But until I changed action for the rule from DROP to Alert, I could not get access to remote SMB share...
The only possibility I can imagine that would cause a DROP action to not appear on the ALERTS tab (highlighted in RED to indicate a drop) is if the alert line from the log did not parse correctly. The code on the ALERTS tab reads the alert log for the interface line-by-line and parses each line into a set of fields delimited by commas. If a line does not parse out the correct number of fields, it is discarded and not displayed on the ALERTS tab.
To see if this is the case, get to the command line in pfSense either directly via the console or remotely via SSH. Then change to the correct Snort log interface directory in
/var/log/snort. There will be a separate sub-directory under that path for each configured Snort interface. Once in the correct sub-directory, usegrepto search thealertfile for the rule SID in question to see if it is in there. Post back here with your findings. If the SID is there but is not showing on the ALERTS tab, then it is a parsing issue I need to look into. If you don't see the SID in thealertfile for the interface, then that would be a binary issue you would take up with the upstream Snort team. -
@bmeeks
I think that is a binary issue. Alert is not in alert file.
Thanks... -
@crazybrain I believe the Atom 3558 with ix NIC's do work with netmap.
I'm running Suricata with inline no problem. There is also a command you can run (cant recall) and it shows its netmap enabled.Now just waiting for pfSense 2.5 to drop.
@bmeeks can/will you be able to release Snort v4 on pfSense 2.4.5 release? Or is it only when 2.5 comes out?
-
@N0_Klu3 said in Snort Package 4.0 -- Inline IPS Mode Introduction and Configuration Instructions:
@bmeeks can/will you be able to release Snort v4 on pfSense 2.4.5 release? Or is it only when 2.5 comes out?
Only when 2.5 comes out. The inline netmap option requires the netmap library from FreeBSD 12, and pfSense-2.4.5 is still FreeBSD 11 (although it is 11-STABLE).
-
So inline mode won't work with vlans? Even though they are hosted on a supported nic? what about a lacp lagg?
Should inline mode work on Intel 82576 or a Intel I340-T4?
I don't mean to seem lazy but this is the best write up I've found and I wouldn't mind listing some tested hardware here.
Thanks for all the great info!
-
@chromefinch said in Snort Package 4.0 -- Inline IPS Mode Introduction and Configuration Instructions:
So inline mode won't work with vlans? Even though they are hosted on a supported nic? what about a lacp lagg?
Should inline mode work on Intel 82576 or a Intel I340-T4?
I don't mean to seem lazy but this is the best write up I've found and I wouldn't mind listing some tested hardware here.
Thanks for all the great info!
VLANs may work now in FreeBSD-12.3/STABLE. I have not tested them. pfSense-2.5 DEVEL moved to FreeBSD-12.3/STABLE a little while back. NIC drivers (the majority of them, anyway) in FreeBSD 12.3 have been ported to a new API called iflib. The iflib system handles all of the netmap stuff now for NICs that use iflib, and thus the NIC hardware driver is not burdened with that code development. The iflib subsystem is also supposed to support features such as VLANs, but there can still be issues with certain NICs that perform hardware-level VLAN tag manipulations.
So a long answer to basically say "I don't know for sure, but VLANs may work with some NICs now in pfSense-2.5 DEVEL with the Snort-4.x package using Inline IPS Mode".
The answer to your other question about netmap support in a given NIC depends on whether or not that hardware vendor migrated their driver over to iflib. Many have, a few have not per my understanding. And even some of those that have migrated may not have ported all versions of their hardware. So far as I know, most of the Intel NICs are ported over to iflib.