Firewall Feedback
-
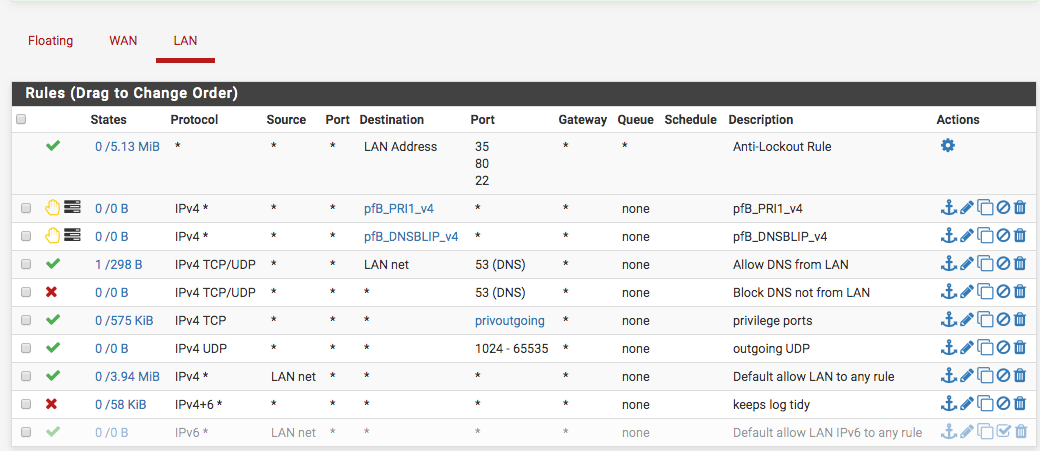
Here is my LAN firewall that was inspired by the thread "Taming the Beast." However, I notice privilege ports, just the TCP is seeing traffic...could the default rule below maybe overriding...did I get it wrong or I just don't have any UDP traffic now? I disabled IPv6 addresses.
-
Use an application that actually uses UDP ;)
-
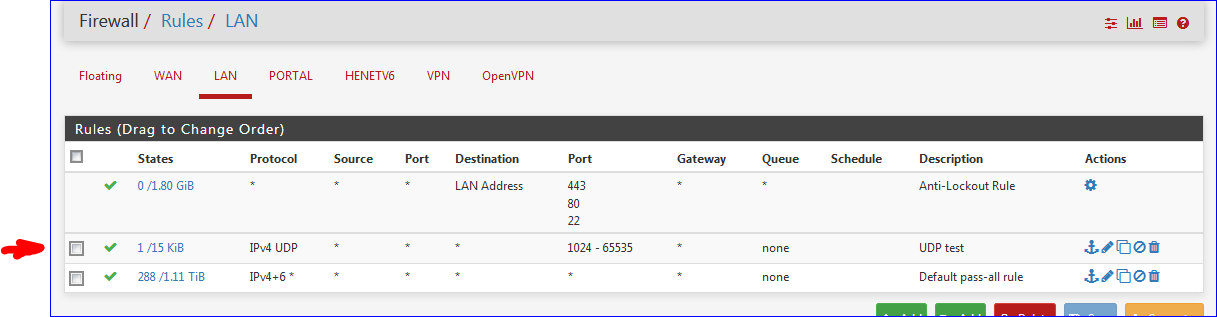
@Gertjan Thank you Gertjan for responding...got traffic now!
-
Do you have a device on the LAN subnet providing DNS or is it done by pfSense, I'm guessing its pfSense as there are hits from * to Lan net ?
I'd change it to This Firewall or LAN Address if you're using pfSense to provide DNS.
-
I really don't see the point to some of those rules.. Your allowing privout and then all the above ports, but then under that you have any rule.. Your not logging those - so what exactly do you think the point of those are?
-
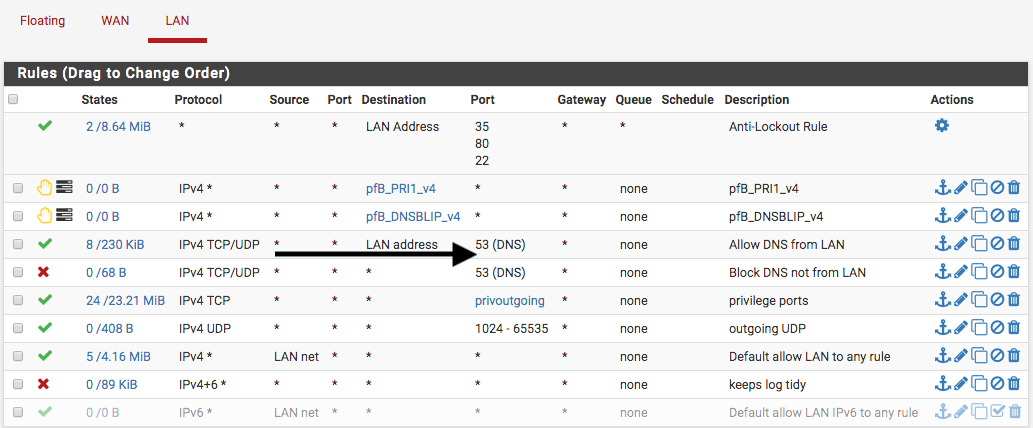
@NogBadTheBad Thanks NogBadTheBad...that's the kind of feedback I am seeking...yes, it'd done by pfSense; so, I'll make the change.
-
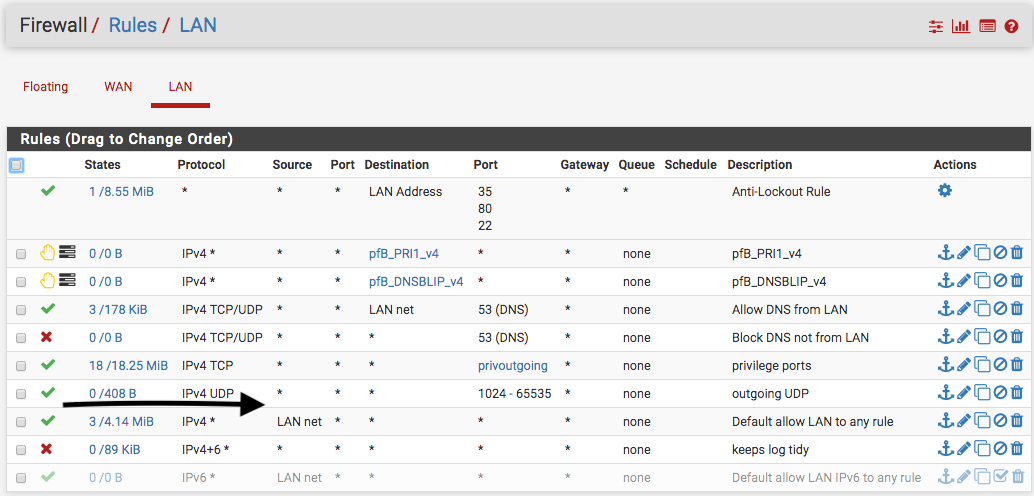
@johnpoz Thanks Johnpoz for responding...actually, I had been thinking about that and glad you point it out. So, would it be best to disable the any rule? How you could tell that those (privout and UDP) aren't logged? Is it by the traffic of the default any rule?
-
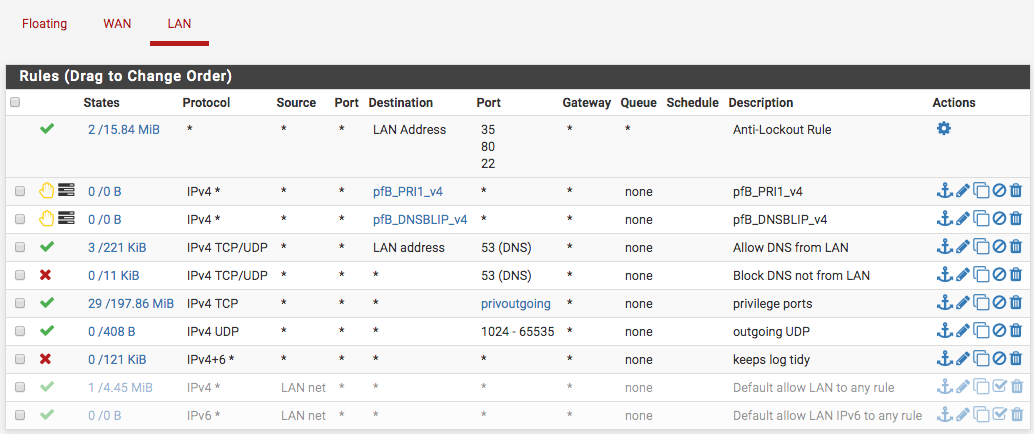
@johnpoz Okay Johnpoz, I disabled the any rule and move up the block all.
-
@NollipfSense said in Firewall Feedback:
How you could tell that those (privout and UDP) aren't logged?
Because they don't have the log icon next to them..
I would of just gone the other way and removed those rules.. And left the any... With your current rules you can not even ping anything not even pfsense own lan IP.
I can think of a few UDP ports that your blocking, NTP and QUIC or HTTP/3 that could be causing you issue going forward with such rules. ESP and AH come to mind as well that could be causing your clients issue.
If your wanting to lock down to only used ports/protocols - its prob better to log your any rule for a while and then figure out what is being used on your network, and then create the rules to allow what you want.
Also since your not logging the block rule you have there - you will not know what clients are banging on the door to let them out ;) Which just becomes unwanted noise on your network, which might be better to reject or turn off such protocols/applications your not going to allow out off on the client side, etc.
-
@johnpoz said in Firewall Feedback:
@NollipfSense said in Firewall Feedback:
How you could tell that those (privout and UDP) aren't logged?
Because they don't have the log icon next to them..
I would of just gone the other way and removed those rules.. And left the any... With your current rules you can not even ping anything not even pfsense own lan IP.
I can think of a few UDP ports that your blocking, NTP and QUIC or HTTP/3 that could be causing you issue going forward with such rules. ESP and AH come to mind as well that could be causing your clients issue.
If your wanting to lock down to only used ports/protocols - its prob better to log your any rule for a while and then figure out what is being used on your network, and then create the rules to allow what you want.
Also since your not logging the block rule you have there - you will not know what clients are banging on the door to let them out ;) Which just becomes unwanted noise on your network, which might be better to reject or turn off such protocols/applications your not going to allow out off on the client side, etc.
Okay Johnpoz, I really appreciate your input...I turned on logging; however, I was able to ping pfSense lan IP!
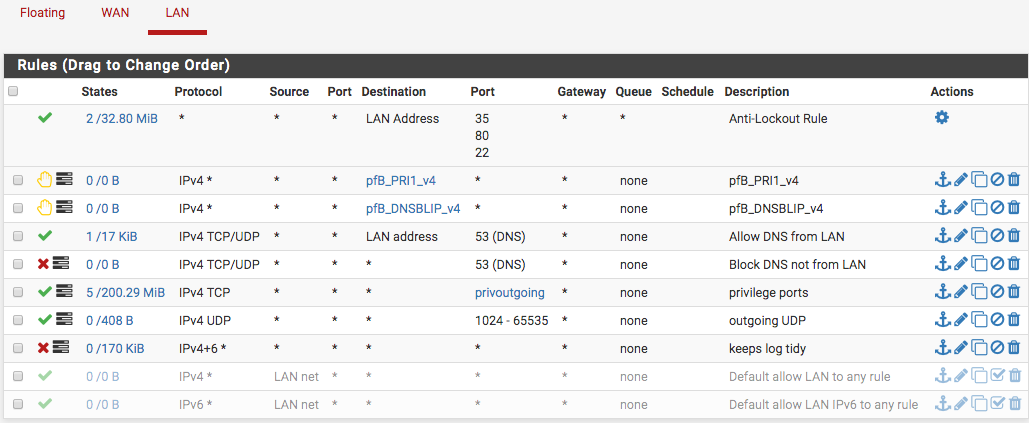
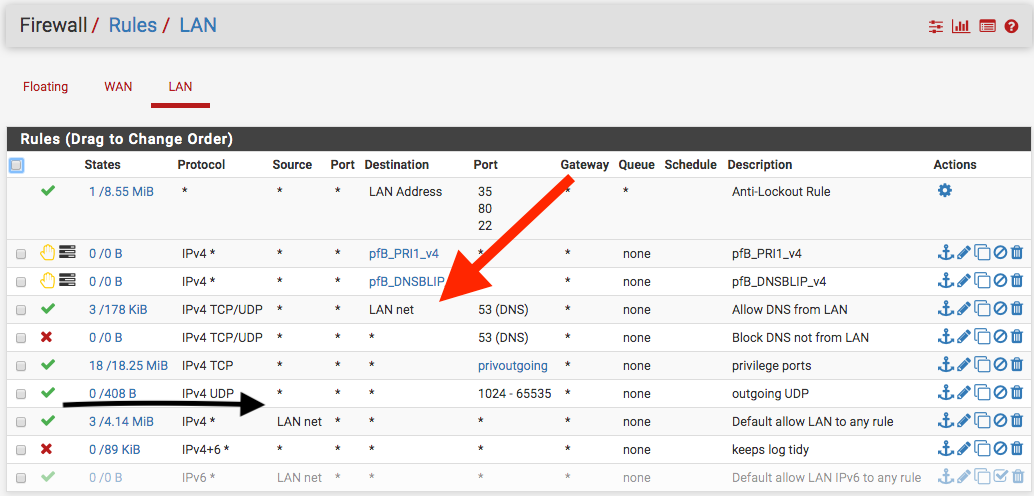
I am curious about the NTP (TCP/UDP) as well as the other UDP ports such ESP and AH (1701, 4500)...wouldn't they get covered by the privout and the UDP outgoing? In the pic below, is that an example of noise that you mentioned? Should I allow a rule with NTP protocol?
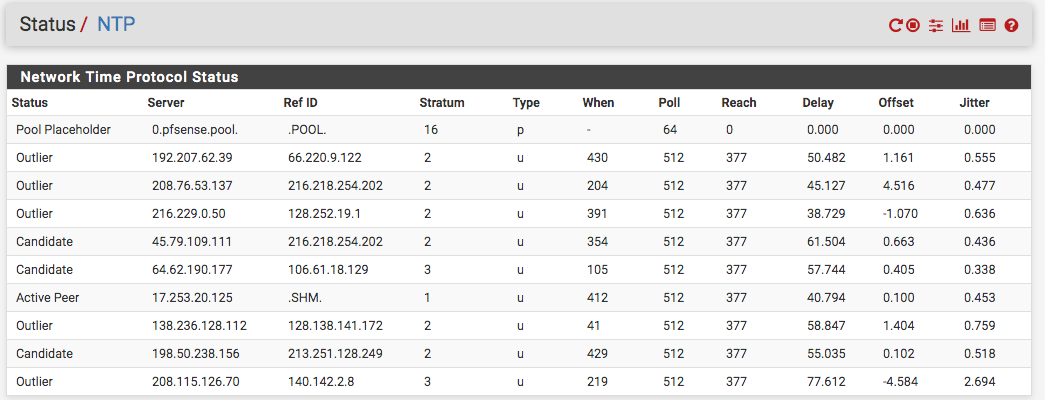
-
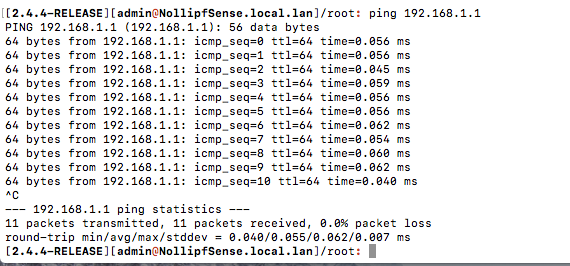
Your pinging pfsense from itself - no shit you can do that ;) heheheheeh Ping it from a client on your lan.. Your rules do not allow it.
No they wouldn't ntp is port 123 UDP, which you have set to 1204 and above. QUIC, or now called http/3 is UDP 80, etc.
You need to understand you can not stop the firewall from talking outbound.. looking at pfsense talking to ntp out of the internet has zero to do with your client on your lan network talking to pfsense for ntp or some other ntp server, etc.
esp and ah are not udp ports, they are other protocols that would be blocked by only allowing tcp and udp.. So if your clients wanted to use those for a vpn outbound, they would be blocked.
I personally do not get why users want to put in rules that are more than likely only cause them grief and extra work when something doesn't work..
I take it your allowing all ports out 1-1023 that your calling privileged ports... What do you think would be talking outside of that? A game for sure.. So you play no games? Plex is 32400 by default, so you don't talk to any plex servers? You limiting the ports to under 1024 for tcp is going to break quite a few things I would image.. Unless all you do is browse the internet... If that is the case why do you not just lock it down to 80/443 for we traffic?
Are you trying to herd a bunch of cats behind your firewall? Or are the devices behind the firewall all under your control?
Lets say you fire up some new app/game and it uses port XYZ.. But you have it blocked - what does that cost you other than pain and extra work? If you do not trust the game/app - why did you run it in the first place.. If its bad software that somehow ran on your box, its going to talk out the standard ports 80/443 - why would it choose some random high port - that could be blocked if in work network for example.. Why not just hide in among all the other web traffic, etc.
What is the reasoning behind you wanting to be restrictive? What does it actually get you other than extra work? The default rules on pfsense are any any for a reason ;) If you have a need to lock that down, sure - but before go doing this and that.. You might want to make sure you understand the plus and minuses to doing such stuff.. Its not all up side for sure. And to be honest way more down side than any sort of extra "security"
-
@johnpoz said in Firewall Feedback:
heheheheeh Ping it from a client on your lan.. Your rules do not allow it.
Okay Johnpoz, I am getting your points, and no...you're correct!
rnollisuzs$ ping 192.168.1.1
PING 192.168.1.1 (192.168.1.1): 56 data bytes
Request timeout for icmp_seq 0
Request timeout for icmp_seq 1
Request timeout for icmp_seq 2
Request timeout for icmp_seq 3
Request timeout for icmp_seq 4
Request timeout for icmp_seq 5
Request timeout for icmp_seq 6
Request timeout for icmp_seq 7
Request timeout for icmp_seq 8
Request timeout for icmp_seq 9
Request timeout for icmp_seq 10
Request timeout for icmp_seq 11
Request timeout for icmp_seq 12
Request timeout for icmp_seq 13
^C
--- 192.168.1.1 ping statistics ---
15 packets transmitted, 0 packets received, 100.0% packet loss@johnpoz said in Firewall Feedback:
I personally do not get why users want to put in rules that are more than likely only cause them grief and extra work when something doesn't work
Well, as I had said, I was following the thread "Taming the Beasts...aka Suricata Blueprint." The goal was to make things easy for Suricata. I had planned VPN and figured I would add that later. I also run Plex but not often or since my pfSense box. Also, I am not really a gamer but could have guests who do, and it would be cool to accommodate in the safest way.
@johnpoz said in Firewall Feedback:
Or are the devices behind the firewall all under your control?
Yes, I have a Mikrotik behind the pfSense. LAN boss for clients/devices...I was even thinking how I could have a double gate when I am ready to set up VPN later. So, could I setup aliases for those you said I would be locking out? pfSense is WAN boss and I understand things have surely changed since the author crafted "Taming the Beasts"...that's what I thought when I saw the any any default rule but incorporate it though.
-
@NollipfSense said in Firewall Feedback:
I could have a double gate when I am ready to set up VPN later
huh? You just policy route out of pfsense for stuff you want or don't want to use your vpn.. Not sure what this taming the beast guide is - my initial thought if they told you to do what you have setup is just a giant facepalm ;)
-
@NollipfSense :
The "Taming the Beast" thread for Suricata is an old thread that was all about how to structure Suricata rules and suppression lists for maximizing detection of bad things with as few false positives as possible. Not really sure how that relates to what you are doing here with all those firewall rules. I'm with @johnpoz here, you are way over complicating your setup - especially if this is for a home network. -
try this
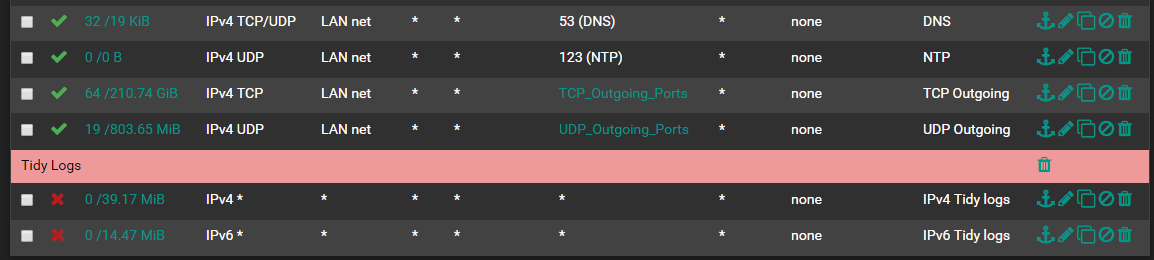
-
@jasonraymundo31 Thank you Jasonraymundo31 for responding...I had to laugh aloud...so clean...
-
@johnpoz Hey Johnpoz, this is how it is now...I understand what you were saying about the default any-any rule...I could not do without it as Internet radio breaks...I suspect it uses the lower UDP ports.
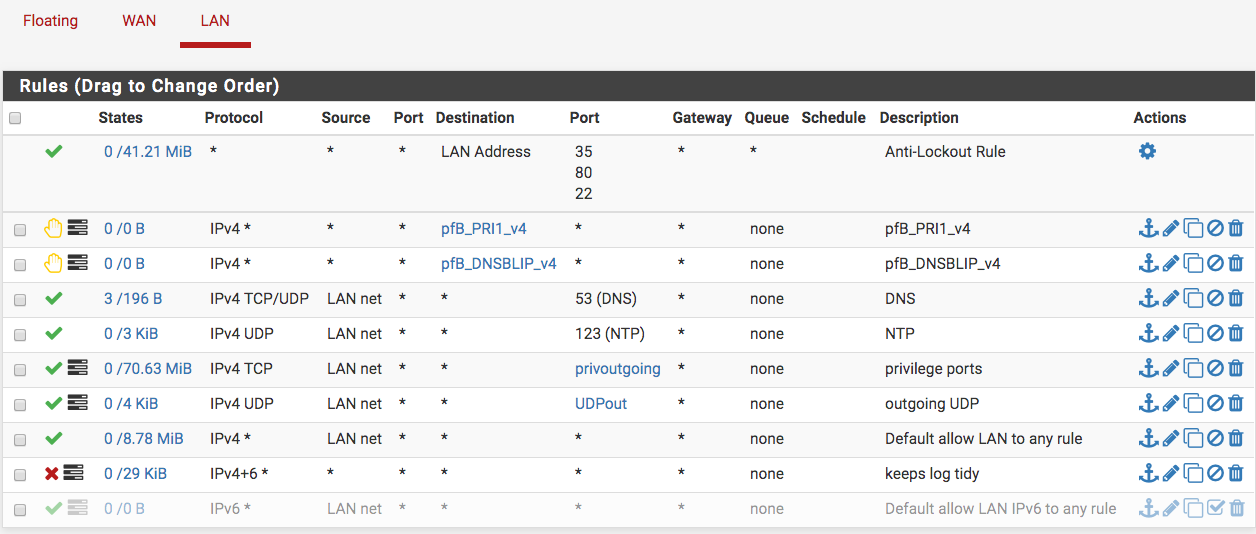
My double-gate idea I mentioned was about the obvious VPN gate at pfSense, then another gate at the Mikrotik...the fun part will be at the Mikrotik...seems doable though.
-
So a double nat? Yeah pointless ;) Or 2 firewalls inline with only your edge doing nat? Again pretty pointless and just added complexity and work and hassle for like zero benefit.
If your moving a shitton of traffic and you need a downstream/core router and possible firewall between your local networks.. Sure ok, then have a edge router/firewall... But in a home setup - its over complication and cost for no added value.
-
@bmeeks In the first part of that thread (Taming the Beasts), the author specified to create the firewall rules to make things easy...the second part was to structure Suricata rules and suppression lists for maximizing detection of bad things with as few false positives as possible. I'll be opening a thread with your section on the fourteen rules I had implemented. Lots of stuff had moved to pfBlockerNG too.
-
@johnpoz said in Firewall Feedback:
So a double nat? Yeah pointless ;) Or 2 firewalls inline with only your edge doing nat? Again pretty pointless and just added complexity and work and hassle for like zero benefit.
If your moving a shitton of traffic and you need a downstream/core router and possible firewall between your local networks.. Sure ok, then have a edge router/firewall... But in a home setup - its over complication and cost for no added value.
Well, right now it is double-natted...I'll turn off the Mikrotik nat rule though, and let the edge pfSense handle it. I have the pfBlockerNG and that by default added the nat. The thing is I was introduced to Mikrotik first and had for seven years before being introduced to pfSense late 2017. So, I just incorporated the two in my network...why throw away a good working kick-ass Mikrotik RB450G.
Yes, its way overkill...it is really recycling not too old equipment I had; so, cost already depreciated...the value to my home-office-lab network is tremendous and rival most small business, some medium-sized business network.