Firewall Rule to Allow RDP from WAN to LAN......Need help
-
Can a wifi client ping pfsense 192.168.30.1 from your wifi client? Have you validated the pings are being answered by pfsense via say a sniff on pfsense, validating the mac address is actually pfsense?
Your never going to figure out what is happening without some basic troubleshooting.
example
$ arp -a Interface: 192.168.9.100 --- 0xf Internet Address Physical Address Type 192.168.9.8 00-1f-29-54-17-14 dynamic 192.168.9.10 00-11-32-7b-29-7d dynamic 192.168.9.11 00-11-32-7b-29-7e dynamic 192.168.9.253 00-08-a2-0c-e6-24 dynamicYou can see that mac for pfsense IP is actually pfsense interface.. Status interfaces
Status up MAC Address 00:08:a2:0c:e6:24 - ADI Engineering IPv4 Address 192.168.9.253Sniff on pfsense ping and dns query..
$ ping 192.168.9.253 Pinging 192.168.9.253 with 32 bytes of data: Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Ping statistics for 192.168.9.253: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 0ms, Maximum = 0ms, Average = 0ms12:07:05.640192 IP 192.168.9.100 > 192.168.9.253: ICMP echo request, id 1, seq 1239, length 40 12:07:05.640235 IP 192.168.9.253 > 192.168.9.100: ICMP echo reply, id 1, seq 1239, length 40 12:07:06.646101 IP 192.168.9.100 > 192.168.9.253: ICMP echo request, id 1, seq 1240, length 40 12:07:06.646124 IP 192.168.9.253 > 192.168.9.100: ICMP echo reply, id 1, seq 1240, length 40 12:07:07.652045 IP 192.168.9.100 > 192.168.9.253: ICMP echo request, id 1, seq 1241, length 40 12:07:07.652069 IP 192.168.9.253 > 192.168.9.100: ICMP echo reply, id 1, seq 1241, length 40 12:07:08.657025 IP 192.168.9.100 > 192.168.9.253: ICMP echo request, id 1, seq 1242, length 40 12:07:08.657045 IP 192.168.9.253 > 192.168.9.100: ICMP echo reply, id 1, seq 1242, length 40192.168.9.100.51363 > 8.8.8.8.53: [udp sum ok] 25160+ [1au] A? www.lasjldsjfsljflsjdslfj.com. ar: . OPT UDPsize=4096 (70) 12:10:49.834316 00:08:a2:0c:e6:24 > 00:13:3b:2f:67:62, ethertype IPv4 (0x0800), length 173: (tos 0x0, ttl 118, id 33758, offset 0, flags [none], proto UDP (17), length 159) 8.8.8.8.53 > 192.168.9.100.51363: [udp sum ok] 25160 NXDomain q: A? www.lasjldsjfsljflsjdslfj.com. 0/1/1 ns: com. SOA a.gtld-servers.net. nstld.verisign-grs.com. 1569777031 1800 900 604800 86400 ar: . OPT UDPsize=512 (131) 12:10:50.739582 00:13:3b:2f:67:62 > 00:08:a2:0c:e6:24, ethertype IPv4 (0x0800), length 73: (tos 0x0, ttl 128, id 48270, offset 0, flags [none], proto UDP -
@johnpoz said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
Can a wifi client ping pfsense 192.168.30.1 from your wifi client? Have you validated the pings are being answered by pfsense via say a sniff on pfsense, validating the mac address is actually pfsense?
Your never going to figure out what is happening without some basic troubleshooting.
example
$ arp -a Interface: 192.168.9.100 --- 0xf Internet Address Physical Address Type 192.168.9.8 00-1f-29-54-17-14 dynamic 192.168.9.10 00-11-32-7b-29-7d dynamic 192.168.9.11 00-11-32-7b-29-7e dynamic 192.168.9.253 00-08-a2-0c-e6-24 dynamicYou can see that mac for pfsense IP is actually pfsense interface.. Status interfaces
Status up MAC Address 00:08:a2:0c:e6:24 - ADI Engineering IPv4 Address 192.168.9.253Sniff on pfsense ping and dns query..
$ ping 192.168.9.253 Pinging 192.168.9.253 with 32 bytes of data: Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Ping statistics for 192.168.9.253: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 0ms, Maximum = 0ms, Average = 0ms12:07:05.640192 IP 192.168.9.100 > 192.168.9.253: ICMP echo request, id 1, seq 1239, length 40 12:07:05.640235 IP 192.168.9.253 > 192.168.9.100: ICMP echo reply, id 1, seq 1239, length 40 12:07:06.646101 IP 192.168.9.100 > 192.168.9.253: ICMP echo request, id 1, seq 1240, length 40 12:07:06.646124 IP 192.168.9.253 > 192.168.9.100: ICMP echo reply, id 1, seq 1240, length 40 12:07:07.652045 IP 192.168.9.100 > 192.168.9.253: ICMP echo request, id 1, seq 1241, length 40 12:07:07.652069 IP 192.168.9.253 > 192.168.9.100: ICMP echo reply, id 1, seq 1241, length 40 12:07:08.657025 IP 192.168.9.100 > 192.168.9.253: ICMP echo request, id 1, seq 1242, length 40 12:07:08.657045 IP 192.168.9.253 > 192.168.9.100: ICMP echo reply, id 1, seq 1242, length 40192.168.9.100.51363 > 8.8.8.8.53: [udp sum ok] 25160+ [1au] A? www.lasjldsjfsljflsjdslfj.com. ar: . OPT UDPsize=4096 (70) 12:10:49.834316 00:08:a2:0c:e6:24 > 00:13:3b:2f:67:62, ethertype IPv4 (0x0800), length 173: (tos 0x0, ttl 118, id 33758, offset 0, flags [none], proto UDP (17), length 159) 8.8.8.8.53 > 192.168.9.100.51363: [udp sum ok] 25160 NXDomain q: A? www.lasjldsjfsljflsjdslfj.com. 0/1/1 ns: com. SOA a.gtld-servers.net. nstld.verisign-grs.com. 1569777031 1800 900 604800 86400 ar: . OPT UDPsize=512 (131) 12:10:50.739582 00:13:3b:2f:67:62 > 00:08:a2:0c:e6:24, ethertype IPv4 (0x0800), length 73: (tos 0x0, ttl 128, id 48270, offset 0, flags [none], proto UDPI can see the mac of pfsense LAN network in my wifi client and also able to ping that IP of that mac, but DNS query is not working.
-
And is unbound running on pfsense?
Or did you turn it off - why do you keep asking 30.10 anything?
Lets see query from your boxes you say work, and then from your wireless client... This isn't freaking rocket science here.. I don't care you if you query 30.1 or 8.8.8.8 - you have yet to show a sniff that your actually getting to pfsense..
do a dns query from one of your other physical boxes, not some VM... Lets see it query pfsense 30.1 for dns, and then do the query from your wifi.
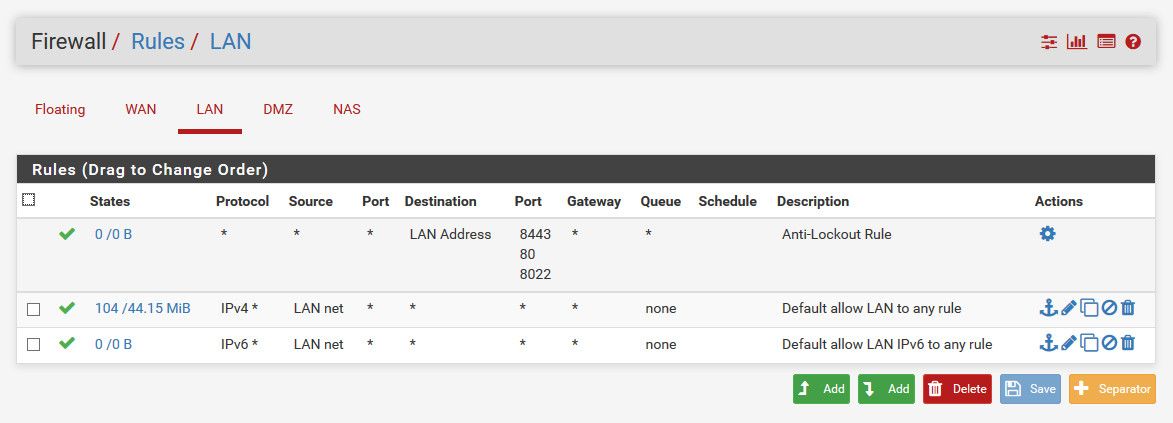
Also lets actually see your LAN rules..
-
@johnpoz said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
And is unbound running on pfsense?
Or did you turn it off - why do you keep asking 30.10 anything?
Lets see query from your boxes you say work, and then from your wireless client... This isn't freaking rocket science here.. I don't care you if you query 30.1 or 8.8.8.8 - you have yet to show a sniff that your actually getting to pfsense..
do a dns query from one of your other physical boxes, not some VM... Lets see it query pfsense 30.1 for dns, and then do the query from your wifi.
Also lets actually see your LAN rules..
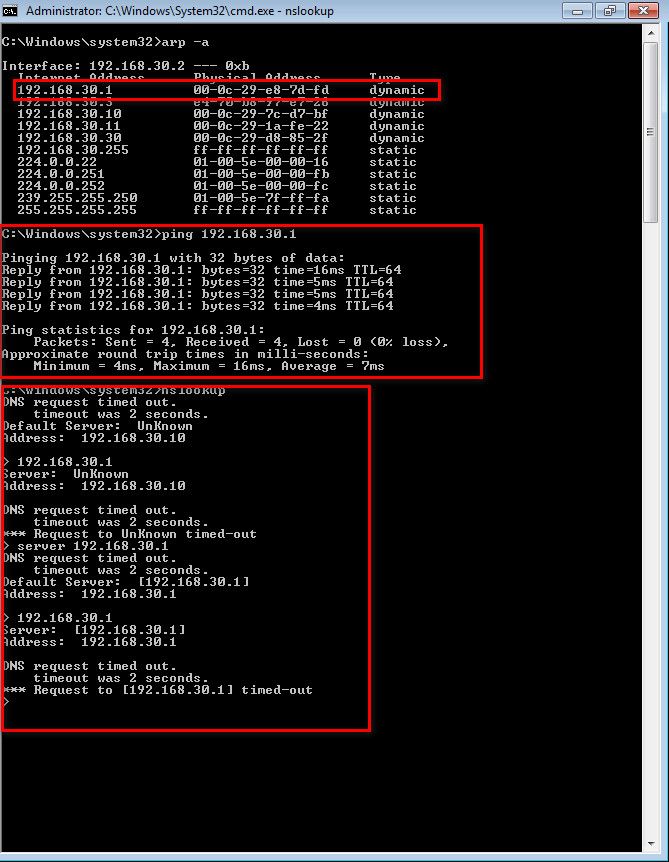
I have removed my wifi router cable connected to second NIC of physical machine. Now, I have connected network switch and from switch I have connected my Windows 10 laptop to do simple test whether internet is working through direct connection. Attached Outbound and LAN firewall rule.
when do DNS query to 192.168.30.1 I can see below :
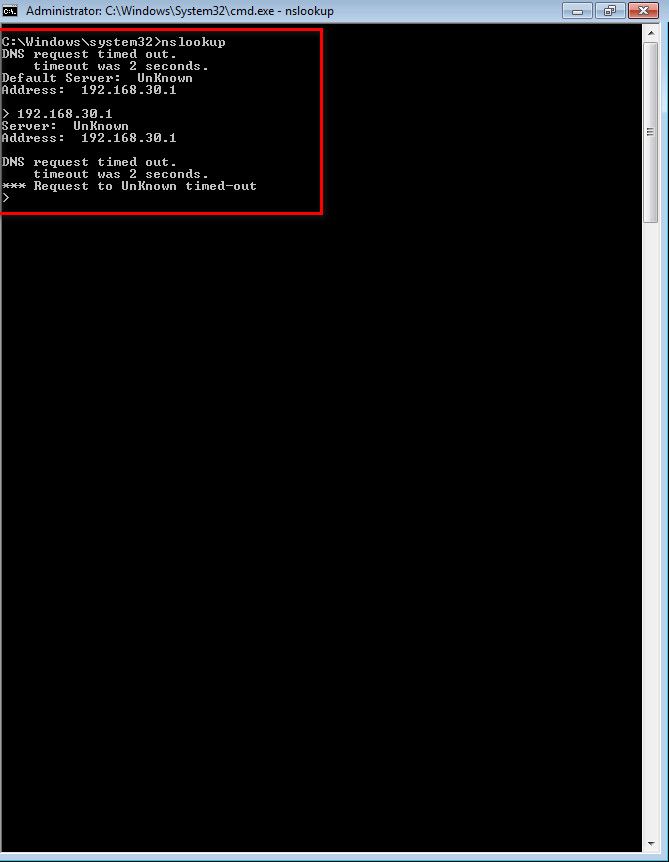
What I can see is any thing goes through second NIC of physical server (ie) through LAN network .. unable to get internet...
Second NIC of physical host is taking IP from Windows DHCP server...
-
Dude freaking sniff already... And is anything even listening on 30.1 for dns???
Going to say this one last time - pfsense can not do anything with traffic it never sees.. I have showed you multiple times how to do a sniff and validate dns query actually gets to pfsense lan interface so it can do something with it.. Be it answer it itself or pass it on to some other dns..
-
@johnpoz said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
dude freaking sniff already... And is anything even listening on 30.1 for dns???
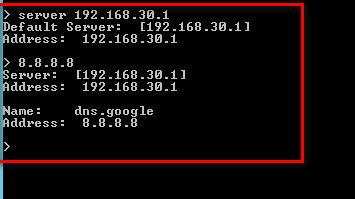
I have tried DNS query from one of the machine (ie) VM which is sitting on LAN network and able to query..
-
I said do it from a physical network device.. And that sure doesn't look right.. how come it didn't come back with pfsense name for the 30.1 address?
$ nslookup Default Server: pi-hole.local.lan Address: 192.168.3.10 > server 192.168.9.253 Default Server: sg4860.local.lan Address: 192.168.9.253See how the IPs resolve to their name... sg4860.local.lan for pfsense IP 9.253
So what your saying is no physically connected device can do a dns query that actually gets to pfsense for pfsense do anything with? How is that a pfsense problem? You have something wrong in your VM host setup..
-
@johnpoz said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
I said do it from a physical network device.. And that sure doesn't look right.. how come it didn't come back with pfsense name for the 30.1 address?
$ nslookup Default Server: pi-hole.local.lan Address: 192.168.3.10 > server 192.168.9.253 Default Server: sg4860.local.lan Address: 192.168.9.253See how the IPs resolve to their name... sg4860.local.lan for pfsense IP 9.253
So what your saying is no physically connected device can do a dns query that actually gets to pfsense for pfsense do anything with? How is that a pfsense problem? You have something wrong in your VM host setup..
when I do nslookup pfSenseFR.localdomain I can get queried and get IP as 192.168.30.1 in my local VM..But when I do same in another physical machine dns is not working .
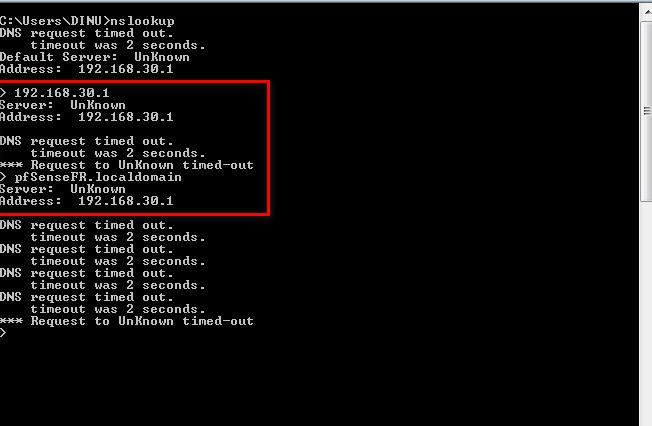
So what your saying is no physically connected device can do a dns query that actually gets to pfsense
Yes you are correct.. I am saying this from beginning....Can you guide me how to connect physical device through second NIC to use as LAN network to connect pfsense network
-
How are you pinging it if not connected??? Your saying you never pinged it from a physical device?
How do you have it setup, what are you using for a VM host software?
-
@johnpoz said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
How are you pinging it if not connected??? Your saying you never pinged it from a physical device?
I never said that I am unable to connect to LAN network. I am saying that unable to browse the internet from my physical device connected through LAN network..
How do you have it setup, what are you using for a VM host software?
I have windows 2012 R2 in my physical host and VMware workstation as host software..
I have two physical NIC in my host..
one is connected (ie) bridged to pfsense WAN and
Second NIC is bridged with pfsense LAN -
Pls find below my network connected :
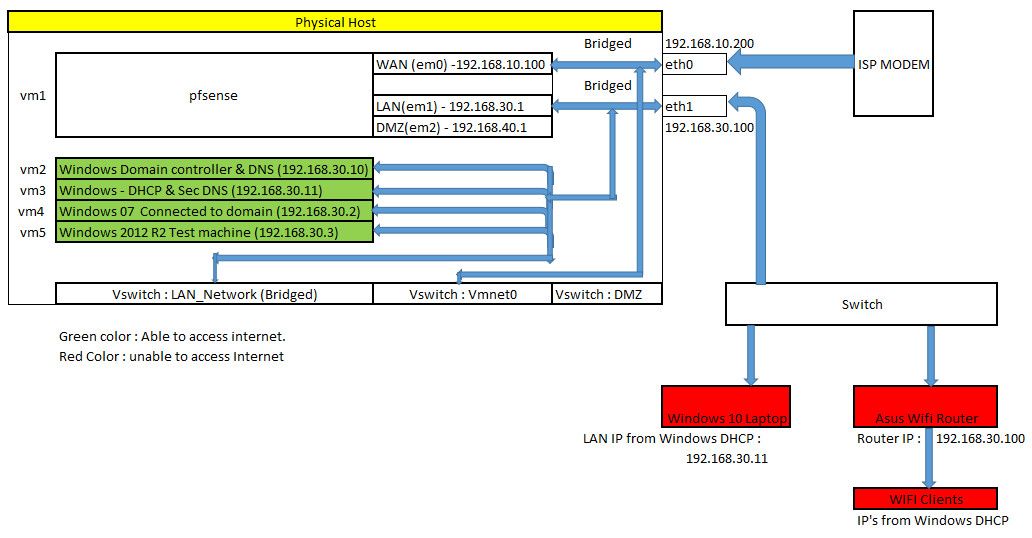
-
@DINU said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
Pls find below my network connected :

In your drawing, two devices have the same IP address. Virtual Machine #3 (DHCP and Sec DNS) is shown as having IP 192.168.30.11, but so is the Windows 10 Laptop machine shown hanging off the external switch. That won't work. Is it a typo?
-
@bmeeks said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
@DINU said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
Pls find below my network connected :

In your drawing, two devices have the same IP address. Virtual Machine #3 (DHCP and Sec DNS) is shown as having IP 192.168.30.11, but so is the Windows 10 Laptop machine shown hanging off the external switch. That won't work. Is it a typo?
it is typo error Windows 10 Laptop is 192.168.30.111
-
@DINU said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
@bmeeks said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
@DINU said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
Pls find below my network connected :

In your drawing, two devices have the same IP address. Virtual Machine #3 (DHCP and Sec DNS) is shown as having IP 192.168.30.11, but so is the Windows 10 Laptop machine shown hanging off the external switch. That won't work. Is it a typo?
it is typo error Windows 10 Laptop is 192.168.30.111
I just noticed another issue that hopefully is also a typo. You have the Asus router shown with IP 192.168.30.100, but you are also showing that same IP address apparently assigned to the eth1 interface on the VM Physical Host. That can't be correct.
And the external switch you are showing, is it a dumb switch or a managed switch? If managed, are any VLANs defined in it and is at least one trunk port configured?
And which hypervisor are you using? Is it ESXi, Hyper-V or something else?
-
@bmeeks said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
I just noticed another issue that hopefully is also a typo. You have the Asus router shown with IP 192.168.30.100, but you are also showing that same IP address apparently assigned to the eth1 interface on the VM Physical Host. That can't be correct.
YEs that is also typo error eth1 is 192.168.30.150
And the external switch you are showing, is it a dumb switch or a managed switch? If managed, are any VLANs defined in it and is at least one trunk port configured?
It is managed no Vlans or trunk port configured. When I am trying to use same subnet in the LAN, internet is not working in External devices.. then no use of using VLAN hereAnd which hypervisor are you using? Is it ESXi, Hyper-V or something else?
Vmware workstation -
@johnpoz :
Thanks a ton johnpoz for your help and spending your valuable time to check the issue and provided the solution.....
Issue is resolved, I can able to access the internet from my external LAN devices through wifi and through switch as well...
(i) Issue is with pfsense in System => General Setup => DNS Server that was pointed to WAN_IP I have changed to none and added local DNS as well and it started working fine.
(ii) I have tried another way of using all interfaces to go through pfsense DNS of creating NAT port forward DNS 53 to 127.0.0.1 and solved the issue..
But (i) looks good and I have used that..
Thanks Once again !!!!
-
@DINU said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
(i) Issue is with pfsense in System => General Setup => DNS Server that was pointed to WAN_IP I have changed to none and added local DNS as well and it started working fine.
Sorry but NO... That would have zero to do with it.. You would of gotten an answer from unbound if running.. What you put in general has ZERO to do with that unless you had changed it to forwarder?
And would of had zero to do with your client talking to 8.8.8.8 for dns.. So whatever you think the problem was - it sure wasn't that..
So your now redirecting dns?? I had asked you before if you were doing such thing.. Which sure that could of cause you all kinds of grief if that was setup wrong. Which you could of validated in like 2 seconds with as simple sniff that you could actually even talk to pfsense for dns.
-
@johnpoz said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
Sorry but NO... That would have zero to do with it.. You would of gotten an answer from unbound if running.. What you put in general has ZERO to do with that unless you had changed it to forwarder?
And would of had zero to do with your client talking to 8.8.8.8 for dns.. So whatever you think the problem was - it sure wasn't that..
So your now redirecting dns?? I had asked you before if you were doing such thing.. Which sure that could of cause you all kinds of grief if that was setup wrong. Which you could of validated in like 2 seconds with as simple sniff that you could actually even talk to pfsense for dns.I went into deep dive and found the biggest culprit is SEP (Symantec Endpoint protection)....
If I enable firewall it is not allowing DNS , If i disable it is working...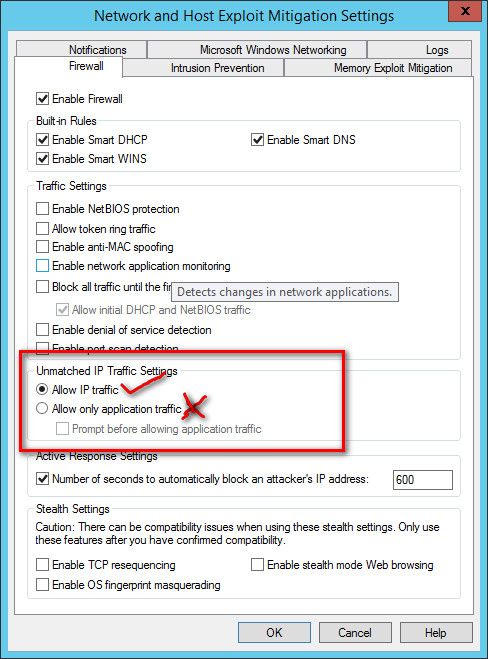
In symantec in firewall it has to "Allow IP Traffic" not "Allow only application traffic" this SEP culprit made me mad...
Thanks Again...