Issues using DNSBL and IP to block domains
-
I am trying to block DoH and DoT on my network. I use DoT on my DNS resolver, and I want to prevent DoH (and DoT) circumvention by clients. I have blocked port 853 for DoT. For DoH, I have a list of domains in DNSBL that is currently working. (all LAN port 53 traffic is forwarded to DNS resolver too)
However, this doesn't prevent a hard coded DoH request to, for example, 8.8.8.8:443 (dns.google). So I would like to also block port 443, 8443, 853, to the resolved IP addresses of my DoT domain list.
I have configured a new IP block feed and added advanced rules to only block the ports to these domains. However when the list of domains is added and the pfblocker is updated. All of these domains are resolved to the pfblocker VIP, presumably because they are already on the DNSBL.
Is it possible to adjust pfblocker to be able to resolve this list of domains? And not use itself for resolution?
-
If I remembered correctly, you'll need to adjust your browser as well.
-
Hi thanks for the reply. I'm not sure what you mean. What in the browser would affect this?
-
This might lead you there: https://forum.netgate.com/topic/146884/suggestion-disable-default-doh-in-firefox
-
Thanks, I know how to disable DoH in firefox. I am concerned about clients that I cannot control or modify. Do you have any suggestions related to my initial question? The issue I have asked about is related to pfsense only. Not any clients.
-
@Risfold said in Issues using DNSBL and IP to block domains:
Thanks, I know how to disable DoH in firefox. I am concerned about clients that I cannot control or modify. Do you have any suggestions related to my initial question? The issue I have asked about is related to pfsense only. Not any clients.
Pretty much the entire point of DoH is to prevent third parties from intercepting, reading or modifying DNS lookups (and in this case, sounds like from the client's point of view your network is a "third party"). So that leads to DoH being somewhere between hard and impossible to block.
Here is a recent SANS Institute whitepaper on the issues with network monitoring caused by DoT and DoH: https://www.sans.org/reading-room/whitepapers/dns/needle-haystack-detecting-dns-https-usage-39160.
And here is another little tidbit of information to keep you up at night ...
 : https://www.zdnet.com/article/first-ever-malware-strain-spotted-abusing-new-doh-dns-over-https-protocol/.
: https://www.zdnet.com/article/first-ever-malware-strain-spotted-abusing-new-doh-dns-over-https-protocol/.So life for network security admins is not going to be getting any easier ...
-
Hi thank you for the reply. Yeah agreed, it is difficult to block. I am mostly looking to block the lowest common denominator on my home network. Do you have any suggestions on how to have pfblocker block the IP of a domain that is already blocked by DNSBL?
-
@Risfold said in Issues using DNSBL and IP to block domains:
Hi thank you for the reply. Yeah agreed, it is difficult to block. I am mostly looking to block the lowest common denominator on my home network. Do you have any suggestions on how to have pfblocker block the IP of a domain that is already blocked by DNSBL?
Well, I'm not a pfBlocker user (I am actually the Snort and Suricata package developer and use Snort on my personal system), but from what I understand you can configure pfBlocker to create aliases which you can then use in firewall rules. So set up pfBlocker to create aliases and then you should be able to have pfBlocker download the DNSBL IP list and stuff the contents into an alias. You would then manually create a rule that used that alias as the source of IPs to block.
-
IP address of domains is constantly changing...
-
@NollipfSense said in Issues using DNSBL and IP to block domains:
IP address of domains is constantly changing...
Yeah, but doesn't pfBlocker periodically update its lists? Nothing will keep up if the IPs change like every few minutes, but if it is days, then perhaps pfBlocker daily list updates can keep up ?? pfBlocker would update the IPs in the alias from the list.
Another possibility is using a URL alias table and loading an updated list from a URL periodically. This would require more work on the part of the admin to manually create an update process.
-
@bmeeks said in Issues using DNSBL and IP to block domains:
This would require more work on the part of the admin to manually create an update process.
That's why I mentioned the changing IP. I am learning more and more that network administration even for small home network is a bit* h.
-
@NollipfSense said in Issues using DNSBL and IP to block domains:
That's why I mentioned the changing IP. I am learning more and more that network administration even for small home network is a bit* h.
I believe the OP is asking about this for his home network. Blocking DoT or DoH in a home network is not really something I would concern myself with. If you have an army of IoT devices, then maybe segregate them on a restricted VLAN by themselves. Some of them are useless without Internet connectivity, though, so you probably need to let them have Internet access even if on a restricted VLAN.
You can very quickly get "too complicated" in a home network if you try to solve or plan for every cyber security potential issue. You can find yourself with a highly secure network that is, for all intents and purposes, non-functional in terms of what you built it for. In other words, most of the stuff you want to access no longer works as it should ...
 .
.Just take reasonable precautions, keep your software updated with security fixes and live a normal peaceful life with a happy wife! Remember, if your wife can't reliably get to Netflix, Amazon Prime Video and Pinterest over the home network, then your life as a network admin will suck! ...

-
@bmeeks said in Issues using DNSBL and IP to block domains:
You can very quickly get "too complicated" in a home network if you try to solve or plan for every cyber security potential issue. You can find yourself with a highly secure network that is, for all intents and purposes, non-functional in terms of what you built it for. In other words, most of the stuff you want to access no longer works as it should ... .
Just take reasonable precautions, keep your software updated with security fixes and live a normal peaceful life with a happy wife! Remember, if your wife can't reliably get to Netflix, Amazon Prime Video and Pinterest over the home network, then your life as a network admin will suck! ...Had to laugh aloud, I recently added Shodan and DOH, lots of sites got broken and still working on Skype as that's how household communicates with other distant family members.

-
I definitely am the type to over complicate my home network. Mostly for fun
 . Yes pfblocker can use aliases and that is what it uses when a feed is created. My issue is that I currently have a list of domains that pfblocker will fetch the IPs for. And I want those IPs blocked on specific ports. However when pfblocker returns the IPs it only lists the VIP used for DNSBL because they are listed there as well. Do you have any thoughts on how to have pfblocker retreive these IPs?
. Yes pfblocker can use aliases and that is what it uses when a feed is created. My issue is that I currently have a list of domains that pfblocker will fetch the IPs for. And I want those IPs blocked on specific ports. However when pfblocker returns the IPs it only lists the VIP used for DNSBL because they are listed there as well. Do you have any thoughts on how to have pfblocker retreive these IPs? -
I have been thinking disabling DNS resolver responding on the local host might work, but I'm not sure if that will work or what else it will effect.
-
@Risfold said in Issues using DNSBL and IP to block domains:
I have been thinking disabling DNS resolver responding on the local host might work, but I'm not sure if that will work or what else it will effect.
Well that didn't work. Got the error below. Plus then my resolver wouldn't use the DoH I have setup.
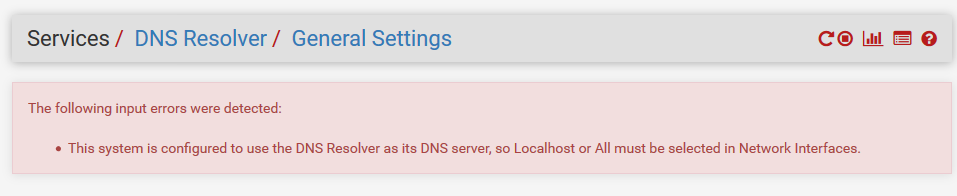
-
@BBcan177 Do you have any suggestions? I would very much appreciate any help you can offer.
-
You will need the resolver for DNSBL to work. I am not familiar with the internal details of how pfBlockerNG works. The developer and I have exchanged ideas in the past, but I mostly concentrate on the IDS/IPS packages (Snort and Suricata).
-
@bmeeks said in Issues using DNSBL and IP to block domains:
You will need the resolver for DNSBL to work. I am not familiar with the internal details of how pfBlockerNG works. The developer and I have exchanged ideas in the past, but I mostly concentrate on the IDS/IPS packages (Snort and Suricata).
Thanks for your contributions to pfsense! I actually am upgrading to beefier pfsense hardware soon and I plan on looking into those. I am currently on an APU board and from what I hear that doesn't quite cut it for those.
-
Some more info here:
https://www.reddit.com/r/pfBlockerNG/comments/d3p1gf/doh_server_blocklist/