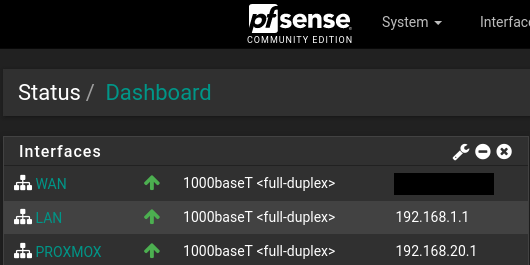
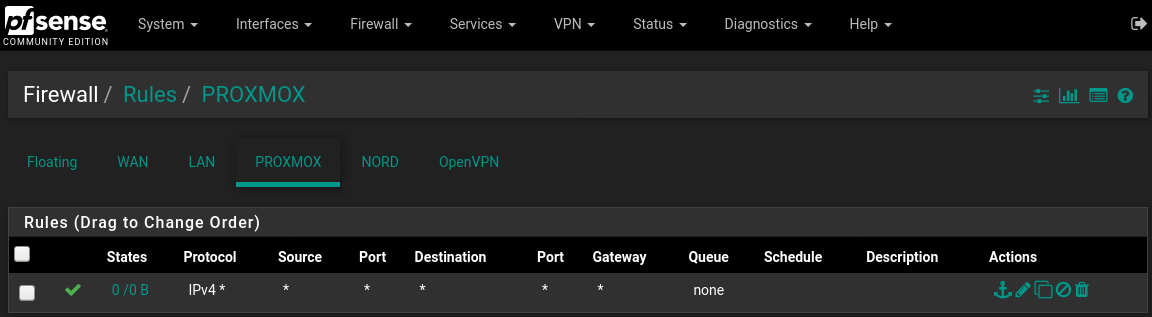
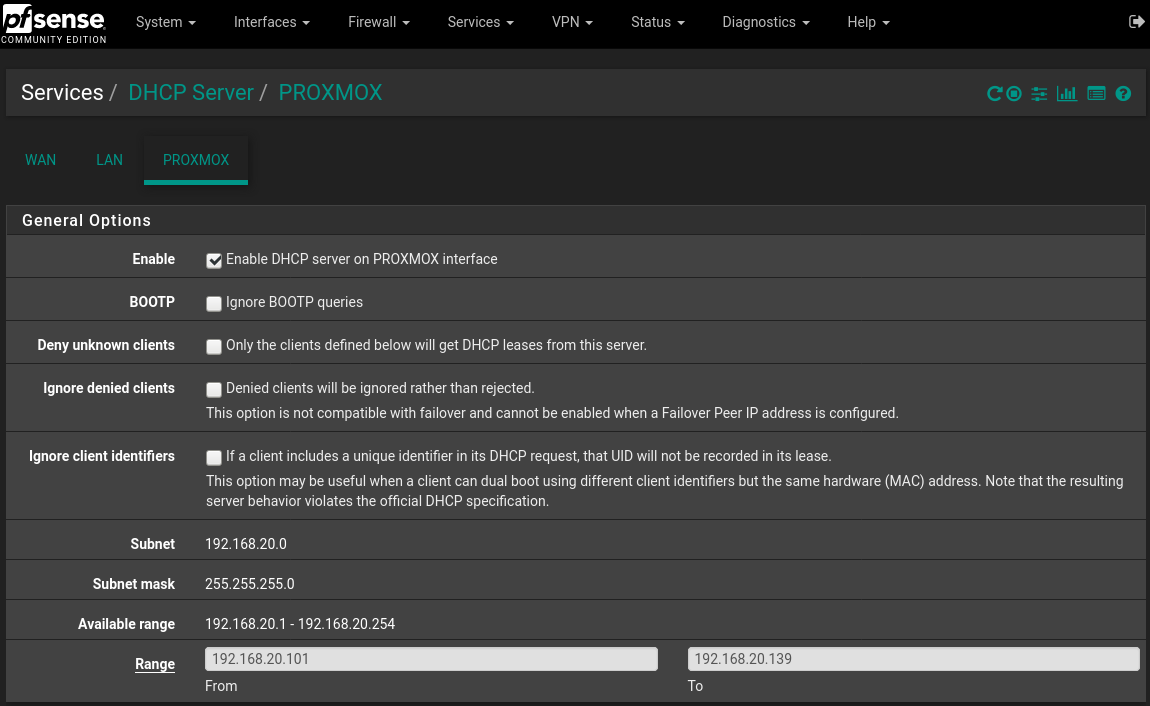
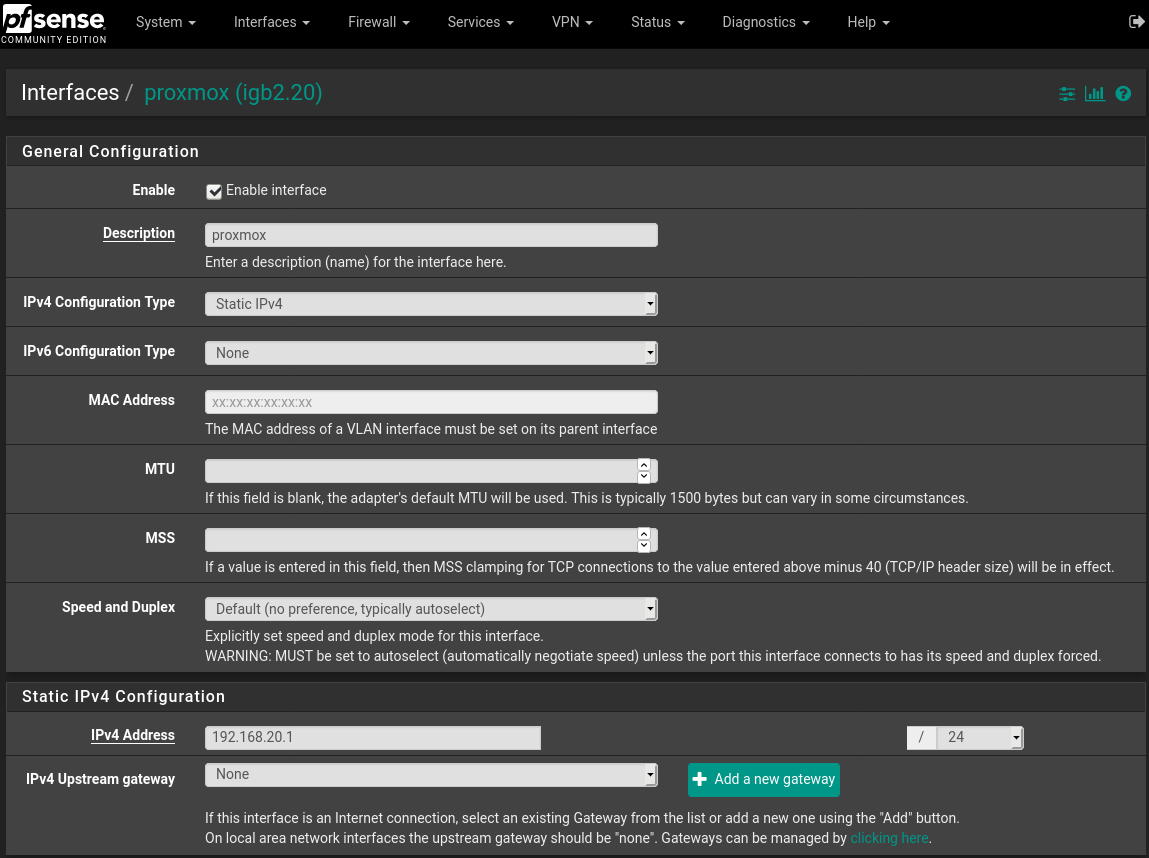
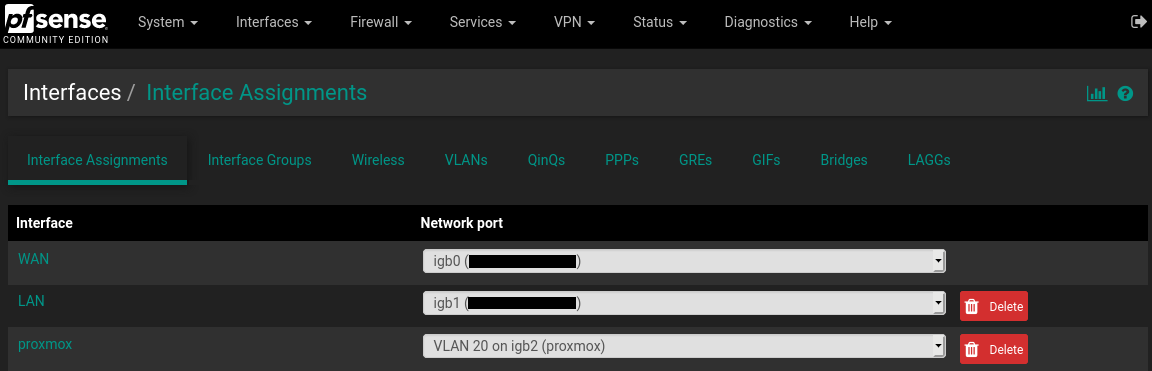
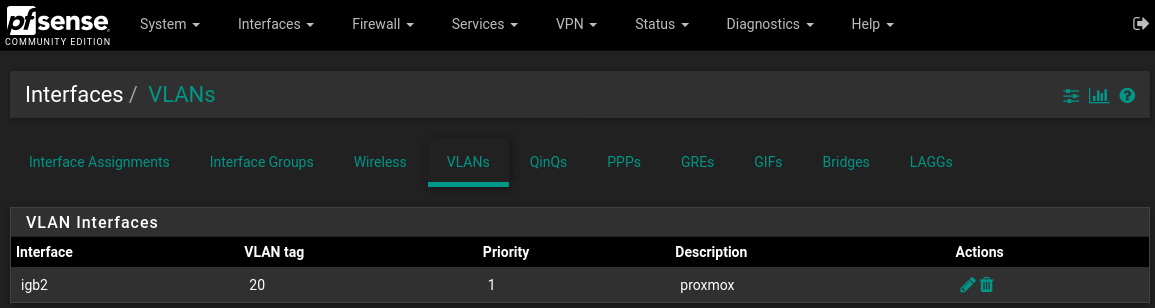
Spent 3 days trying to implement simple VLAN, help please, picture and details inside.
-
Just curious -- are you using wireshark for the sniffing?
-
Doesn't matter where/what you sniff with - you can always just load it into wireshark..
I don't think the gui in pfsense allows for the tcpdump -e flag to see the tags... But you can just do it via tcpdump on pfsense and write the capture to a file.. Then load that file in wireshark, etc.
-
Perhaps a question for a different thread -- however is it true the xn driver used for the paravirtualization in FreeBSD does not support 802.1q tagging? Any reason for this?
-
That is prob better in its own thread - sounds unlikely to me.. I have never ran across a driver that can not do tags..
-
Thanks I'll open a different thread
-
But that is really not a hardware driver - specific vm driver.. So you never know what they might not include, etc.
-
@kevdog said in Spent 3 days trying to implement simple VLAN, help please, picture and details inside.:
Just curious -- are you using wireshark for the sniffing?
Yes, I use Wireshark frequently.
-
Interesting discussion here - I know at one point a couple years ago I also read (or heard somewhere) that one shouldn't mix tagged an untagged (native) traffic on the same interface. I realize that it can be done, but I am trying to figure out why it might be a bad idea. So far all I could find was this old article from 2009:
https://www.networkworld.com/article/2234512/cisco-subnet-tagging-the-native-vlan.html
What do you guys think - is this a problem to be concerned about? Thanks in advance for your insight, I really appreciate it.
-
I read the article you referenced however I'm not sure its exactly relative to your questions. When you're saying interface -- are you talking about switch ports? Usually trunk ports for example contained an untagged and tagged traffic. When you create VLANs within pfSense you are essentially mixing native or untagged traffic with tagged traffic.
-
@tman222 said in Spent 3 days trying to implement simple VLAN, help please, picture and details inside.:
Interesting discussion here - I know at one point a couple years ago I also read (or heard somewhere) that one shouldn't mix tagged an untagged (native) traffic on the same interface. I realize that it can be done, but I am trying to figure out why it might be a bad idea. So far all I could find was this old article from 2009:
https://www.networkworld.com/article/2234512/cisco-subnet-tagging-the-native-vlan.html
What do you guys think - is this a problem to be concerned about? Thanks in advance for your insight, I really appreciate it.
Native VLAN? Given that he starts with an oxymoron, I don't know how credible he is. However, VLANs and native LAN are quite common. For example, with VoIP phones, the phone connects to the switch and a computer plugs into the back of the phone. The phone would be on a VLAN and the computer, native LAN. Same with WiFi APs, with a guest SSID. The main SSID connects to the native LAN and the guest uses a VLAN. I have also worked on a network, in a seniors residence, with native LAN for office network, VLAN for office phone, VLAN for the residents Internet and another VLAN for management. The whole point of VLANs is to provide logically separate networks over the same wire.
-
Thanks guys - maybe I can illustrate my question better with example:
Let's assume I have a pfsense router with interfaces i1 and i2 -- i1 is WAN and i2 is LAN. I also have a switch with VLAN support on which I have defined 3 VLAN's, let's call them VLAN 10, 20, and 30. Let's assume the switch's port 1 is connected to pfSense's i2 interface.
I'm contemplating the following two configurations:
-
On the switch port 1 is tagged for VLAN 10, 20, and 30, i.e. essentially becomes a trunk port. On pfSense, I setup a VLAN interfaces on interface i2 for VLAN 10, 20, and 30. There is no native LAN on i2.
-
On the switch port 1 is tagged for VLAN 10 and 20, 30 stays untagged. On pfSense I setup VLAN interfaces for 10 and 20 only on interface i2. 30 becomes the native LAN on i2.
Is there an advantage of one over the other? Is it better practice to have a native LAN per interface vs. just VLAN's?
Thanks again for your help in guiding my understanding, I really appreciate it.
-
-
Be it you mix or not... Doesn't matter in the long run... I mix, have always mixed in such a scenario... Its not an issue from a security point, and is no different than putting a bunch of tagged vlans on the interface..
You run into a scenario where where some devices do not like tags.. can not do them - until recently the unifi AP could not do tags for the management vlan.. IE the IP on the device could not be on a tagged vlan.
So in the scenario what you plug it into pfsense or switch port.. The network that the AP would get an IP on would have to be untagged. And then any other ssids you wanted in other vlans would be tagged.
The only so called security problem is you could plug a device in, and be on the network without knowing the vlan ID.. But that is just like not broadcasting your ssid, or trying set mac address filtering on your AP as some "extra" security. Its utter nonsense and provides zero extra anything other than hassle doing those things.
But what if you want to be able to do that ;) Ie running a native or untagged network I can always be sure to be able to plug say a laptop in and get an IP.. Without having to go thru the extra step of figuring out what the tag for whatever vlans might be running on that port.
When it comes to OP issue.. Since he tagged, then YES he has to set his device to understand and use that tag.. Doesn't freaking make it any more secure... JFC its his router, in his location plugged into his freaking machine ;) Its not a gawd damn DC in a dod facility ;)
Now is it common practice when you going to use an interface for vlans that you don't put an untagged on there - sure very common, many people do it that way, etc. etc. But that is when its going to be plugging into a switch.. And If I was creating an uplink from switch A to switch B, that would carry vlans.. There wouldn't be any untagged running on that uplink... But this is a bit different when your going to be plugging something directly into your router/firewall vs just connecting that port as unplink to a switch. If it just going to be an uplink to a switch - then there is no reason to run unttaged networks on it. That is not the scenario the OP was in..
In the long run doesn't matter if you or do not run an untagged network when you run vlans on the interface - as long as you understand what your doing an what your plugging into that port, etc.
-
Thanks @johnpoz - so in the example scenario I posted where I have 3 VLAN's and I'm hooking the router interface i2 up to switch port 1, a more common practice would be to use the switch port as a trunk port (i.e. everything is tagged) vs. using a mixture of tagged and untagged - did I understand that correctly? Thanks again.
-
Correct... If your sending it to switch sure just tag everything.. This common... But there is nothing saying 1 of those can't be untagged.. There is nothing wrong with it, you just need to understand what your doing.
And it sure and the F is not less secure...
Say for example was going to plug my AP into that port on the firewall.. And for its management network it has to be untagged.. How would it work if tagged everything on the port on the firewall.
Switch don't care, port don't care - it just needs to know what it tags or doesn't tag... When you put more than one vlan on a port.. Only 1 can be untagged, rest tagged, or all of them tagged... Makes no difference.. You just can not expect to run more than 1 untagged network on a port..