OpenVPN Split tunnelling **screenshots**
-
Here's my scenario:
I have a subscription with ExpressVPN.
Setting up as per their instruction works as it should.What i'm trying to accomplish is route specific port traffic thru VPN only, but the rest of connections thru WAN. Example: BT Transmission thru port 60000.
I can route the entire LAN thru VPN
I can route a single LAN IP thru VPN
I can't figure out how to route a single port thru VPN.Please advise.
Thanks
-
Just add a firewall rule to the to of the LAN rule set with protocol = TCP or UDP or both, source = any, dest = any, dest port = 60000, gateway = the ExpressVPN GW.
Can't find a reason, why this shouldn't work.
-
Thats what I thought too...
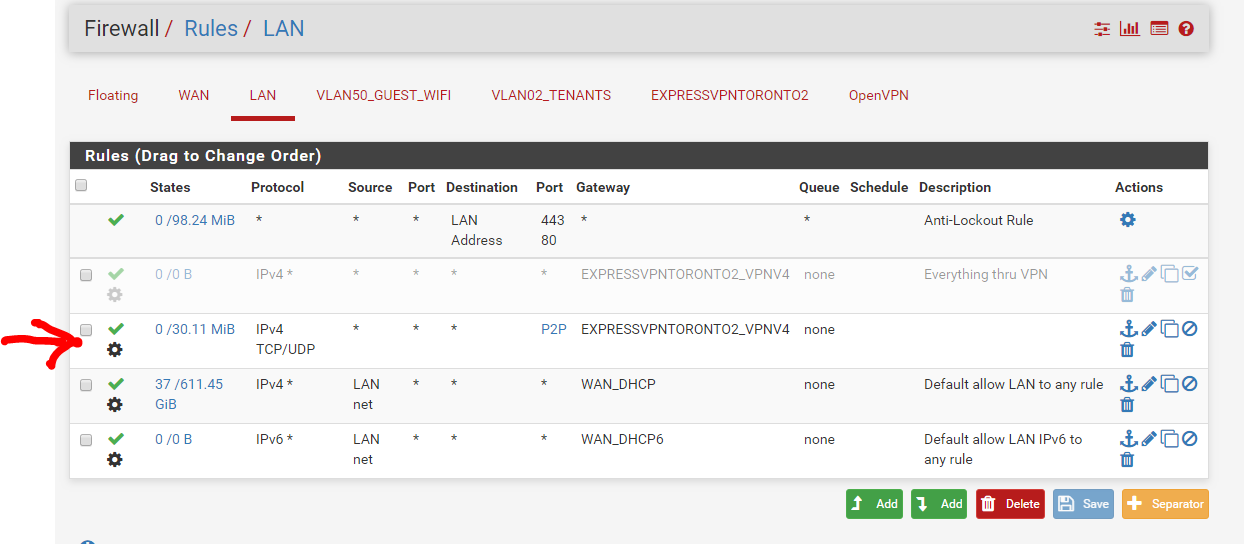
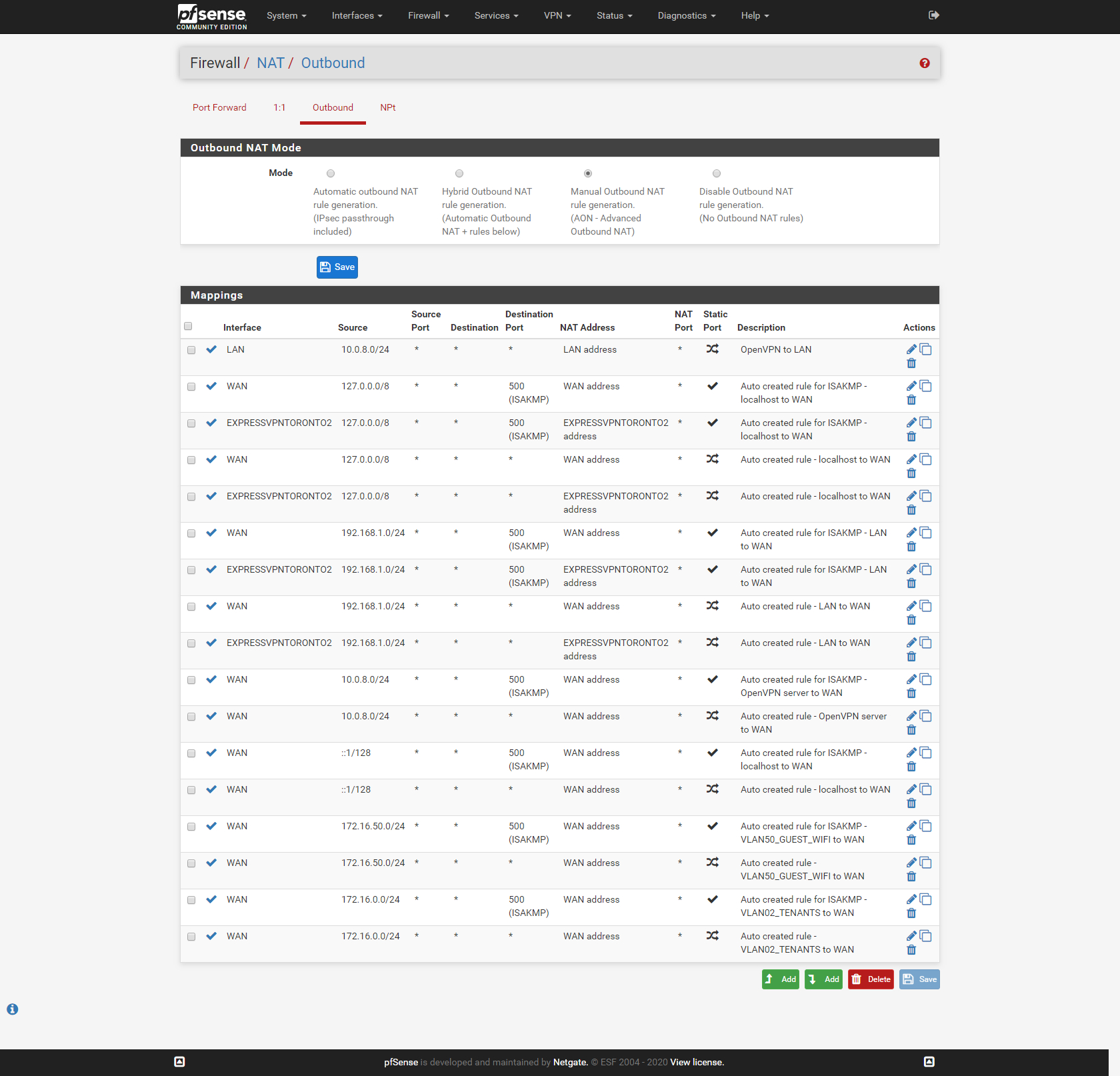
Here's some more screenshots. Please advise on what i'm doing wrong.
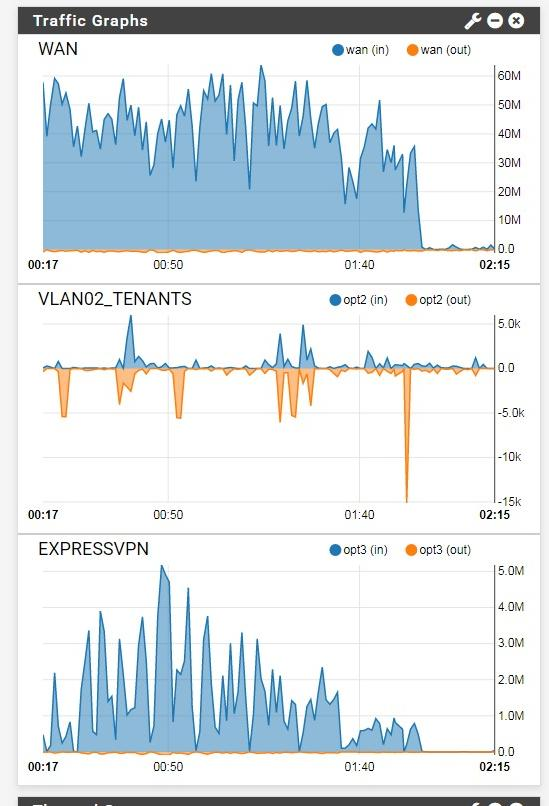
From this, you can sort of see that the WAN graph doesn't match the ExpressVPN graph.. (i tested by downloading)
-
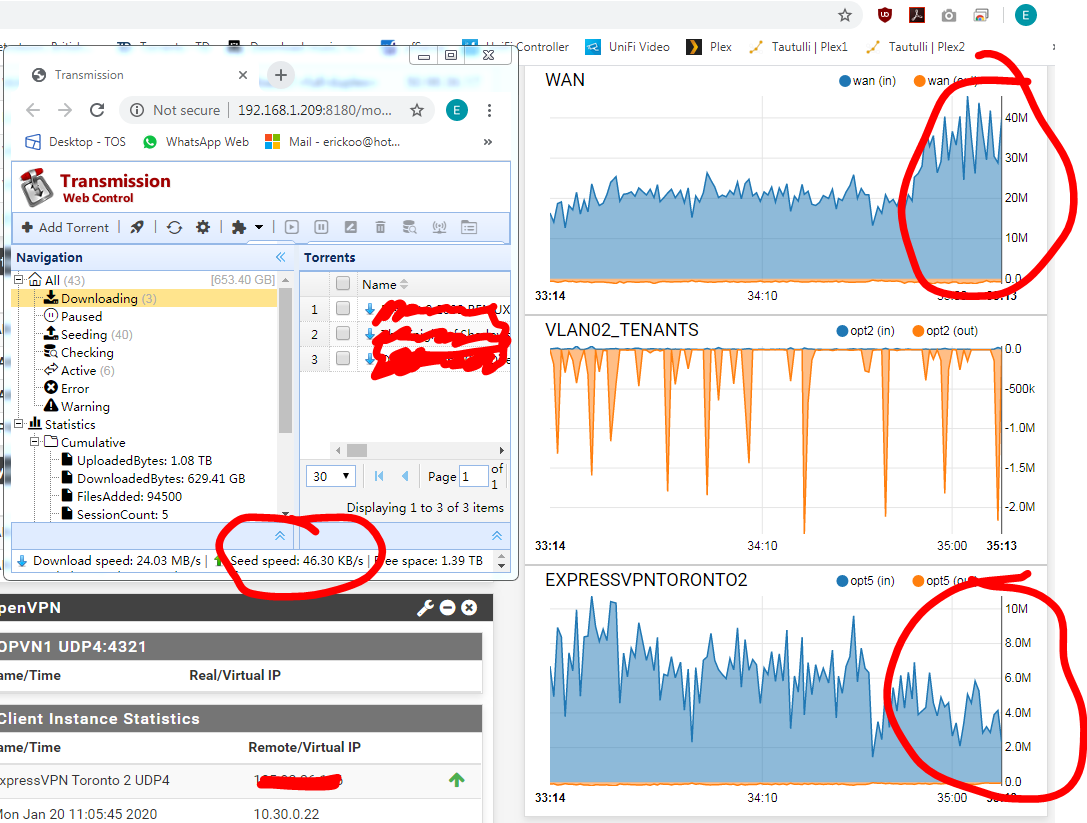
it seemed like its kind of working, but not sure as the private tracker website is still reporting my WAN IP, but not the VPN IP
Any ideas?
-
Not sure why you think p2p would be 1 port... You understand that the other people in the swarm are going to be pretty much on any port they want to be on... So you talking to that IP in the swarm could be any destination..
if you want your p2p box to talk out your vpn... Then policy route it based upon your devices source IP..
-
@johnpoz said in OpenVPN Split tunnelling **screenshots**:
Not sure why you think p2p would be 1 port... You understand that the other people in the swarm are going to be pretty much on any port they want to be on... So you talking to that IP in the swarm could be any destination..
if you want your p2p box to talk out your vpn... Then policy route it based upon your devices source IP..
Maybe this? my p2p box is actually a Terra-Master NAS.If I policy route based on the devices IP, then all the services on the NAS would route thru VPN, which is what i dont' want to do.
I guess what i'm trying to acomplish is to mask all P2P traffic, but not anything else. uTorrent had a SOCKS5 option but Transmission doesn't seem like it does, I don't think ExpressVPN has SOCKS5 support.
-
That is YOUR port!!!! That has zero to do with what port I am running my p2p client on that shares with you...
Which would be your dest port when you talk to me...
-
In that case, is there a way of isolate this service thru VPN, but everything else thru WAN? all on the same box.
-
No not really.. Since you have no idea what ports a remote p2p box (member of the swarm) might run on - could be 80, could be 443, etc. etc. Only way is to isolate the client that will be doing your p2p to the vpn is to understand the destination port(s) or do the routing via the source IP (your client).
Your p2p client could be a vm with its own IP, your p2p client could be application bound to specific source IP - which in that case then you can filter that traffic to only use the vpn.
To be honest, I really don't get why anyone these days runs p2p clients on their own connections. Just run it on a box somewhere else.. And just move the files you want back and forth to your network... Let the remote box in some dc on a 10g connection do the "sharing".. Much better solution if you ask me.
Many of the swarm members prob going to be in the same DC.. Huge bandwidth, very low latency for exchanging the "linux iso images" ;) Your isp only sees you moving encrypted data between your ip and some IP X... These boxes with large amounts of storage and fast connections can be had for less than the cost of a netflix subscription... You only move the files back and forth when its convenient to you, at the full speed of your pipe.. You don't use up any of your limited upload "sharing" etc. etc.. It really makes zero sense to me to run p2p via your main connection - how much does that vpn cost you per month? When you could just use that for some seed box in p2p friendly country.. But hey you have fun! ;)
How about sharing said remote box with some buddies that are also fans of sharing linux isos at high speed ;)
-
I am also interested in this option, so rather than create a new thread I'll ask about a possible solution here. While I agree @johnpoz 's case for a remote P2P box may make sense for many users, I still think the OP has a valid question that wasn't answered. Let's say you have a truly high-speed connection to your home, both up and down.
Is it possible (this may be a Windows question as well) to assign an OpenVPN connection to one's VPN provider to a VLAN, and then make this VLAN a second network connection in Windows, alongside the network card LAN already in place? Most P2P software supports binding to a specific network connection. Details of implementation for less-than-expert pfSense users would be helpful.
-
Yes you can policy route a source IP, already went over this... What you can not do is policy route destinations you have no idea about... What are the destination IPs, what are the ports - you have no idea what ports will be used by the other p2p nodes you will be talking to. And your not going to use the same source port, so you can not even policy route on the source port.
But sure if you want to take an be it a standalone box, your application bound to a vip on your box.. A vm with its own IP, etc and then policy route that out your vpn service that is just clickity clickity sort of setup.
You don't need to create vlan or anything... Say your IP on your windows machine is 192.168.1.100, add a second IP - again very simple to do, say 192.168.1.101, then bind your p2p client to this .101 IP, now any traffic from .101 you policy route out your vpn connection you setup on pfsense.
-
I'm a believer that the simplest implementation is to be preferred. Not sure a VM is necessary, given the application in question can prefer a particular network connection.
How would one set up a VPN/VLAN to appear as a second network connection in Windows?
-
You DON"T need to do that!!! But if you run the vpn software on your machine directly it will automatically be another interface that you can bind your p2p client too.
As to setting up a vlan along with your normal connection. You would need a nic that supports multiple vlans on it.. windows doesn't make that easy like linux does.. Off the top the head I don't think in say normal windows 10 with direct support from the nic driver you can actually just create a vlan sub interface...
But again you do not need to, just add a secondary IP to your interface...
Here..
Ethernet adapter Local: Connection-specific DNS Suffix . : Description . . . . . . . . . . . : Realtek PCIe GbE Family Controller Physical Address. . . . . . . . . : 00-13-3B-2F-67-62 DHCP Enabled. . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes IPv4 Address. . . . . . . . . . . : 192.168.9.100(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 192.168.9.253 DNS Servers . . . . . . . . . . . : 192.168.3.10 NetBIOS over Tcpip. . . . . . . . : EnabledNow I added a secondary IP..
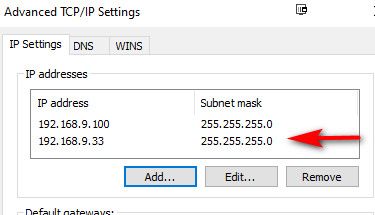
Ethernet adapter Local: Connection-specific DNS Suffix . : Description . . . . . . . . . . . : Realtek PCIe GbE Family Controller Physical Address. . . . . . . . . : 00-13-3B-2F-67-62 DHCP Enabled. . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes IPv4 Address. . . . . . . . . . . : 192.168.9.100(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0 IPv4 Address. . . . . . . . . . . : 192.168.9.33(Tentative) Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 192.168.9.253 DNS Servers . . . . . . . . . . . : 192.168.3.10 NetBIOS over Tcpip. . . . . . . . : EnabledHere is pfsense pinging that IP..
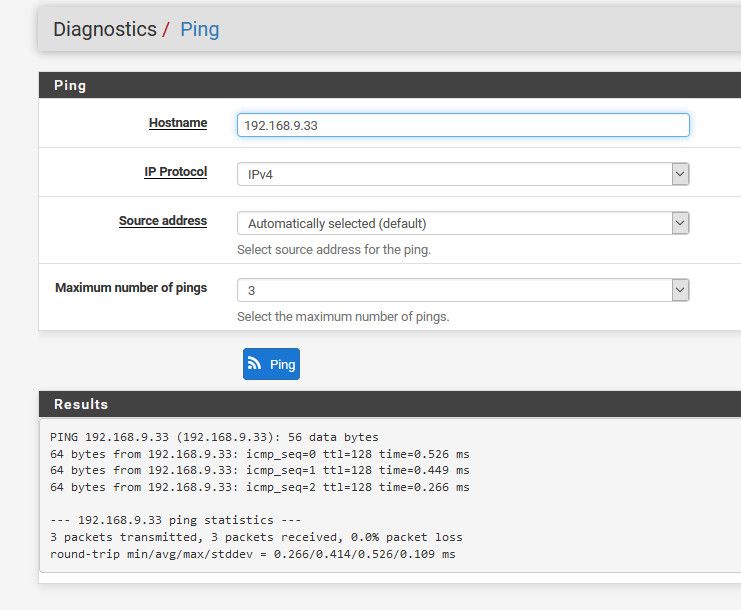
Now just bind your p2p app to that 2nd IP, and policy route it - clickity clickity!
-
Thanks, that was helpful!
-
Is there an IPv6 version of the above? I know where to find the network configuration in Windows, but wanting to do things correctly, there may be more to it than just typing in an IPv6 and changing the last 4 digits. The IPv6 the windows box gets now comes from prefix delegation from Comcast. Can I set up pfSense to hand out a second address to this machine? I'm getting "temporary" IPv6 addresses, but I doubt I want to use those as I believe they can change over time.
Thanks again for the help.
-
Your vpn supports IPv6? Unlikely..
-
@johnpoz said in OpenVPN Split tunnelling **screenshots**:
Your vpn supports IPv6? Unlikely..
Well, that wasn't an answer to the question at hand. I can choose a provider, some do support it, and as I've been working with pfsense I have found reasons to support IPv6.
-
How exactly are you going to route traffic out your vpn that support IPv6 from a client behind pfsense? On a different IPv6 address. You would have to NAT the ipv6 for that to work. The setup makes no sense..
If want to do it with ipv6, then you would run the vpn client on the client - you wouldn't be policy routing traffic out a vpn connected to pfsense.
-
@johnpoz said in OpenVPN Split tunnelling **screenshots**:
How exactly are you going to route traffic out your vpn that support IPv6 from a client behind pfsense? On a different IPv6 address. You would have to NAT the ipv6 for that to work. The setup makes no sense..
By binding the application requiring VPN to the 2nd network connection associated with an additional IPv6 address on the PC. pfSense would route traffic from that address to the VPN. Couldn't this be a firewall rule, not NAT? Agreed NAT and IPv6 don't make sense.
If want to do it with ipv6, then you would run the vpn client on the client - you wouldn't be policy routing traffic out a vpn connected to pfsense.
I don't want to run the VPN client on the server PC, I'm already doing that and it has several drawbacks, the main one is the VPN becomes the network connection for everything and screws with WAN server access.
-
For IPv6 vpn to work on pfsense, you would have to NAT to it... The vpn connection is not going to route your local IPv6 space..