How to distribute connections between two wan-ip interfaces
-
Dear,
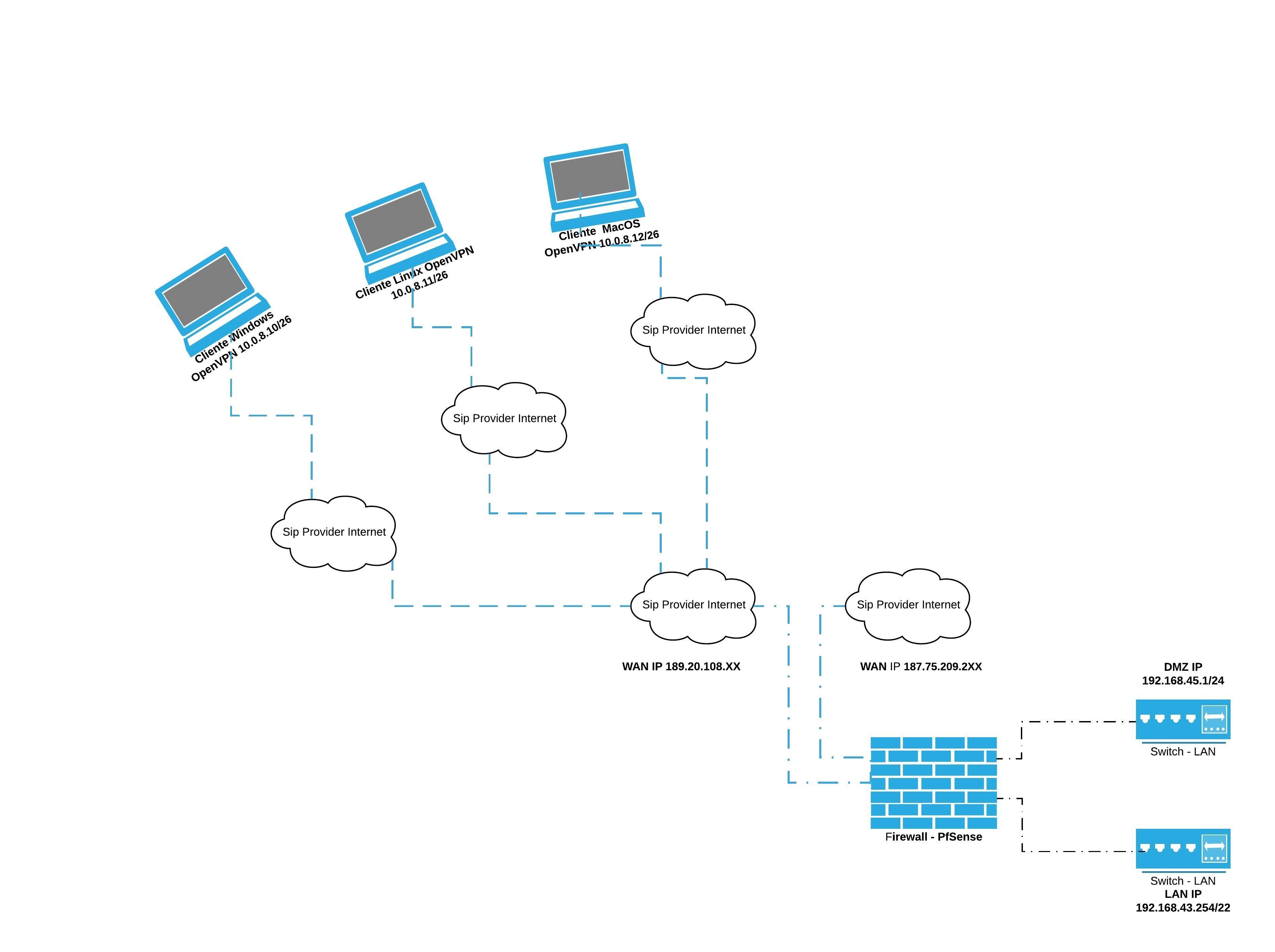
Please help me with the sizing of my OpenVPN server. I'm using pfsense 2.4.4-RELEASE-p3 (amd64), as shown in the diagram below, two wan-ip connections, the 189.20.108 Internet interface. xx 10 MB full duplex and the second wan-ip interface 187.75.209.2xx is a 100 MB PPOE connection. My demand for remote connections has increased a lot, so it is creating bottlenecks in the dedicated link for remote connections via OpenVPN. Help me with the configuration and distribution of these demands between the two links.
I'm reading the documentation on Use Multiple Servers, but I don't know if that's the path I should take.
https://docs.netgate.com/pfsense/en/latest/vpn/scaling.html#scaling-openvpnUse Multiple Servers OpenVPN is not multi-threaded so any single instance of OpenVPN is limited to using a single CPU. If a router has fast cores and not too many users, that may be OK, but it does not scale well. A workaround for this is to split users onto multiple servers. There are various means to reach this goal, including (but not limited to): Multiple servers on different WANs or ports, each with unique tunnel networks but otherwise identical settings (Same CA structure, encryption, etc). Administrators could choose to manually configure pools of clients to connect to specific servers, but that does not scale well. Clients may connect to any server configured in this manner so long as their settings line up properly. Multiple servers can be listed in a single client configuration with additional remote statements. Add remote-random to the client configuration so that clients will pick a random server when starting, which avoids overloading whichever server is listed first. Servers could be run on multiple WANs to overcome single-circuit throughput limits. Multiple servers with completely unique settings (Different CA structure, different clients, etc) More secure but more difficult to manage. Clients must use different configurations to reach each server, no automated/built-in way to pick between them unless a specific client supports that function. Good for isolating separate security levels (e.g. remote workers, remote administrators, vendors). -
https://www.netgate.com/resources/videos/advanced-openvpn-on-pfsense-24.html
Multi-WAN Tactics starting at ~40:08... but the whole hangout is worth watching.
-Rico
-
Gentlemen,
Please, can anyone help with this demand, I need to apply the concept of multi-wan-ip on my OpeVPN server, currently I already have two links, they are published in my DNS.Example:
vpn.company.com.br -> 189.20.108.xx
vpn2.company.com.br -> 187.75.209.2xxBelow is an example of conf.OVPN
dev tun persist-tun persist-key cipher AES-256-CBC ncp-disable auth SHA1 tls-client client resolv-retry infinite remote vpn.company.com.br 1194 udp verify-x509-name "OpenVPN-Server" name auth-user-pass remote-cert-tls server remote vpn2.company.com.br 1194 udp keepalive 4 15 <ca>best regards,
Wesley Santos -
https://openvpn.net/community-resources/reference-manual-for-openvpn-2-4/ says :
If –remote is unspecified, OpenVPN will listen for packets from any IP address, but will not act on those packets unless they pass all authentication tests. This requirement for authentication is binding on all potential peers, even those from known and supposedly trusted IP addresses (it is very easy to forge a source IP address on a UDP packet).So - it's a question of setting :
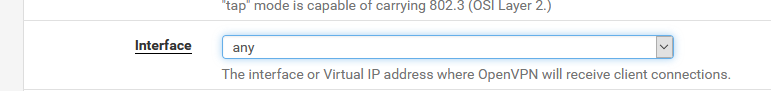
Didn't know that this was possible.
Don't know much more. -
@Gertjan
it is possible to use listening on all interfaces on the OpenVPN server, as shown in the image below.
the problem that is occurring is the overload on a single link, all clients connect only on wan1-IP, which responds at the URL "vpn. company.com.br", if wan1-IP is not responding, therefore, all customers always connect to the wan1-IP interface as the primary.I am looking for a solution that can balance customer traffic between the wan1-ip and wan2-ip interfaces.
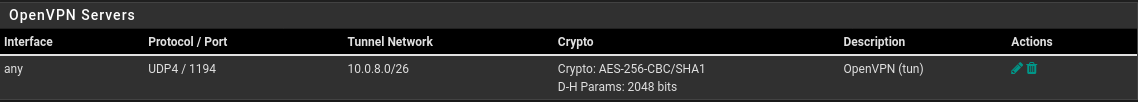
-
Unusual. The typical method is to bind to loopback and create port-forwards on the WAN interfaces.
I think remote-random is the config option your are looking for. -
@dotdash said in How to distribute connections between two wan-ip interfaces:
I think remote-random is the config option your are looking for.
Yes, I was told to use the random remote control in the configuration option, but I don't know where to start and I can't even find material to use as a reference.
-
@wesleylc1 said in How to distribute connections between two wan-ip interfaces:
I can't even find material
I advise to to stop using the "one script-solution-for-all-needs".
Because :
Your setup is unusual. And thus less know, less documented, less tested. You're probably the first mentioning it on this forum.
On the other hand, the doc was mentioned ones already - let's do it twice now : you use OpenVPN ? then read the OpenVPN manual : https://openvpn.net/community-resources/reference-manual-for-openvpn-2-4/ - the remote-random is explained over there. Google will add in another thousand or so references. That's what you have. Up to you to decide if it's is enough to implement.
For more better support is of course available at the OpenVPN support channels.
Do not break the rule : keep it simple.@wesleylc1 said in How to distribute connections between two wan-ip interfaces:
but I don't know where to start
So, you are in this plane, in the cockpit to be precise. And you want to fly it. And you're not type rated. Do what works best : learn. You can even test and try, something that isn't really possible with planes.
-
@Gertjan said in How to distribute connections between two wan-ip interfaces:
I advise to to stop using the "one script-solution-for-all-needs".
Thank you for your replies.
I didn't understand "one script-solution-for-all-needs". -
@wesleylc1 said in How to distribute connections between two wan-ip interfaces:
Yes, I was told to use the random remote control in the configuration option, but I don't know where to start and I can't even find material to use as a reference.
I think you just add it in the advanced configuration options when you roll the client (it's the EXAMPLE option...)
Per my understanding, it basically scrambles the server list when the client starts. Not ideal, but better than nothing. -
@wesleylc1 said in How to distribute connections between two wan-ip interfaces:
"one script-solution-for-all-needs".
Ad @dotdash above : use a OpenVPN settings file for each the WAN connections. Use 2 separate OpenVPN servers processes.
-
@Gertjan said in [How to distribute connections between two wan-ip interfaces]
Ad @dotdash above : use a OpenVPN settings file for each the WAN connections. Use 2 separate OpenVPN servers processes.
I would actually advise him to follow the 'port forward method' of multi-WAN described in the book. Perhaps if the loads were very high, it might make sense to have separate processes. I've never heard of binding to all interfaces before this thread, and it seems a bit sloppy...
https://docs.netgate.com/pfsense/en/latest/book/openvpn/openvpn-and-multi-wan.html -
@dotdash
I don't know if I understood your answer very well.
But I'm already using the advanced configuration options with a list of URLs (vpn.company.com.br / vpn2.company.com.br), but, by default, I always connect to (vpn.company.com.br) that way connections are never balanced. -
@Gertjan
I think I understand your suggestion, because of COVID-19, I already have many clients connected remotely to the office and I believe that if I use this configuration option with 2 OpenVPN servers, these clients may have connection problems. -
I thought I was clear, but I'll be more specific-
Add the line
remote-random
to the client openvpn config file.
This can be included in the installer by adding it to the advanced configuration options on the client export page. -
@dotdash
My problem is not in the CPU usage of my server, this load is very low, despite having 40 clients connected simultaneously to the OpenVPN server. I believe that this port forwarding solution should be an option.last pid: 77788; load averages: 0.18, 0.11, 0.11 up 70+15:28:24 11:26:10 77 processes: 1 running, 68 sleeping, 8 zombie CPU: 0.5% user, 0.0% nice, 0.5% system, 0.1% interrupt, 98.9% idle Mem: 64M Active, 204M Inact, 678M Wired, 176K Buf, 2984M Free ARC: 217M Total, 42M MFU, 165M MRU, 331K Anon, 1059K Header, 9024K Other 96M Compressed, 204M Uncompressed, 2.14:1 Ratio Swap: 2048M Total, 2048M Free PID USERNAME THR PRI NICE SIZE RES STATE C TIME WCPU COMMAND 30696 root 1 20 0 16356K 13684K select 1 16:17 2.02% openvpn 52568 root 1 21 0 97764K 36552K accept 1 0:28 0.60% php-fpm 425 root 1 20 0 99812K 38836K accept 2 0:35 0.31% php-fpm 99249 www 1 20 0 20692K 15620K kqread 1 2:09 0.16% haproxy 58210 root 1 20 0 6404K 2632K select 3 113:32 0.14% syslogd -
@dotdash
As shown in the image below?
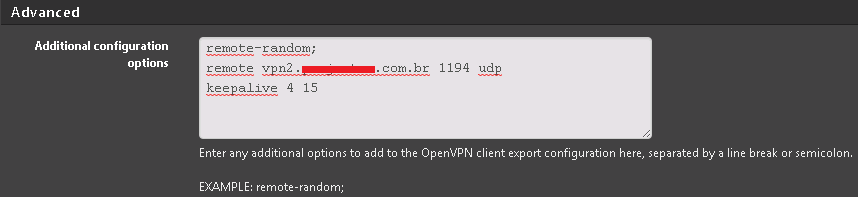
-
Yes, that looks correct.
-
@dotdash said in How to distribute connections between two wan-ip interfaces:
Yes, that looks correct.
My doubts are ..
After using this parameter, it is necessary to update the config.OVPN of all clients that are already configured on their computers.What if, after using this parameter, load balancing is done between the wan1-ip / wan2-ip interfaces, which listen to the URLs (vpn.company.com.br / vpn2.company.com.br)?
-
Hmm I never tried with (Open)VPN and maybe it's kind of shoddy....you could also round robin your DNS (target IPs).
-Rico