Маршрутизация клиента OpenVPN в две сети IPSec
-
День добрый, помогите советом или ткните ссылкой.
Есть 2 офиса которые между собой объединены IPSec, и есть клиенты которые подключаются на один сервер OpenVPN (№1) которых надо запустить на оба сервера. Локально в любой из сети всё ходит нормально, а клиенты ovpn видят только сеть сервера №1, вторую сеть не видят.
Сервер №1
192.168.0.1 (/24)
255.255.255.0
сеть ovpn 192.168.192.0/24Сервер №2
192.168.1.1 (/24)
255.255.255.0В доп. настройках ovpn указано push "route 192.168.192.0 255.255.255.0"
На форме прочитал что надо указывать еще одну фазу 2 для IPSec
https://forum.netgate.com/topic/48678/openvpn-route-to-ipsec-remote-site
Но что то не получается, если указывать фазу
на 1 сервере LAN(192.168.0.0)-ovpn net (192.168.192.0)
на сервере 2 LAN(192.168.1.0)-ovpn net (192.168.192.0)
то локально пропадает доступ ко всем клиентам ovpn и в статусе IPSec во второй фазе не появляется вторая настройка, только основная.
В правилах ovpn, ipsec и lan можно всё. -
@Kowex Здр
По уму у Вас должно быть 2 фазы-2 на обоих серверах
Сервер 1
1 фаза-2 192.168.0.0/24 <-> 192.168.1.0/24
2 фаза-2 192.168.192.0/24 <-> 192.168.1.0/24На сервере 2 зеркальное отражение обеих фаз-2 сервера 1
если нет доступа к настройкам сервера-2 , то надо использовать NAT в настройках дополнительной фазы-2 сервера-1
тогда будет 2 фазы-2 на сервере-1 и 1 одна фаза-2 на сервере-2 -
@Kowex said in Маршрутизация клиента OpenVPN в две сети IPSec:
push "route 192.168.192.0 255.255.255.0"
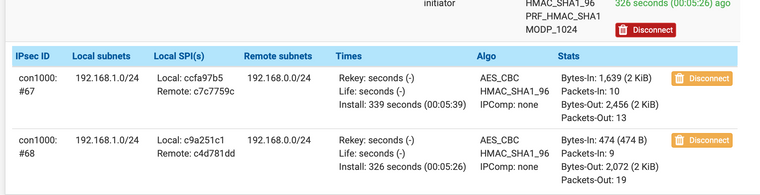
Да, не так фазу вносил, появилась в статусе 2 фазы, но странно одинаковые.
Локально всё работает, клиент так и не видит кроме сети ovpn
Сервер №1
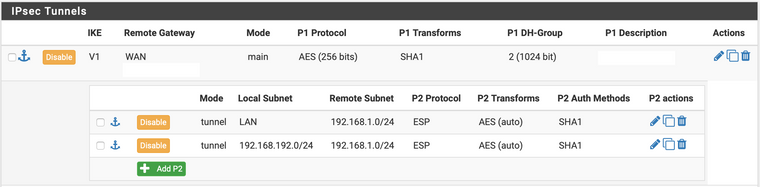
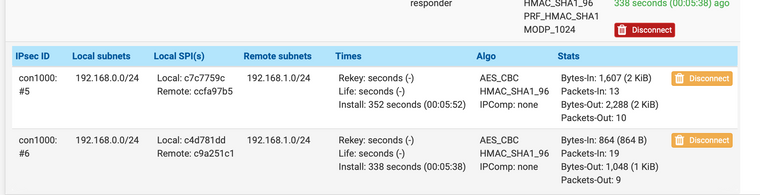
Сервер №2
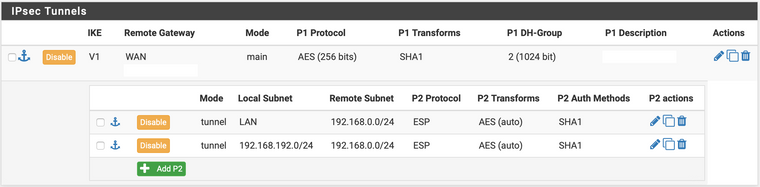
-
@Kowex
Сервер-2 , по-моему, ошибка
Должно быть
Lan -> 0.0/24
Lan -> 192.0/24а у Вас
Lan -> 0.0/24
192.0/24 -> 0.0/24 - ошибка -
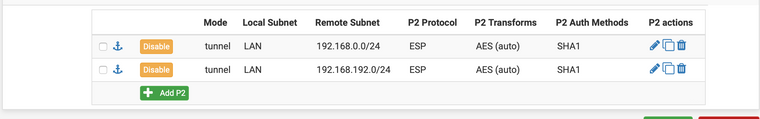
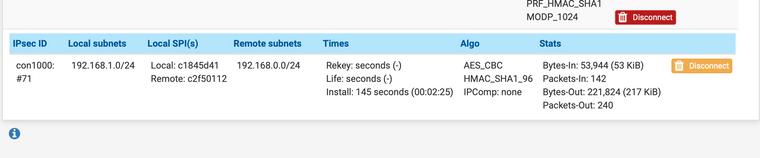
Если так делаю, то вторая фаза в фазах не запускается вообще
Сервер №2
-
@Kowex
Логи фазы-2 покажите -
May 20 22:41:39 charon 08[IKE] <con1000|29> queueing ISAKMP_DPD task May 20 22:41:39 charon 08[IKE] <con1000|29> activating new tasks May 20 22:41:39 charon 08[IKE] <con1000|29> activating ISAKMP_DPD task May 20 22:41:39 charon 08[ENC] <con1000|29> generating INFORMATIONAL_V1 request 3332412499 [ HASH N(DPD_ACK) ] May 20 22:41:39 charon 08[NET] <con1000|29> sending packet: from 1.1.1.2[500] to 1.1.1.1[500] (92 bytes) May 20 22:41:39 charon 08[IKE] <con1000|29> activating new tasks May 20 22:41:39 charon 08[IKE] <con1000|29> nothing to initiate May 20 22:41:52 charon 08[IKE] <con1000|29> sending DPD request May 20 22:41:52 charon 08[IKE] <con1000|29> queueing ISAKMP_DPD task May 20 22:41:52 charon 08[IKE] <con1000|29> activating new tasks May 20 22:41:52 charon 08[IKE] <con1000|29> activating ISAKMP_DPD task May 20 22:41:52 charon 08[ENC] <con1000|29> generating INFORMATIONAL_V1 request 748839859 [ HASH N(DPD) ] May 20 22:41:52 charon 08[NET] <con1000|29> sending packet: from 1.1.1.2[500] to 1.1.1.1[500] (92 bytes) May 20 22:41:52 charon 08[IKE] <con1000|29> activating new tasks May 20 22:41:52 charon 08[IKE] <con1000|29> nothing to initiate May 20 22:41:52 charon 08[NET] <con1000|29> received packet: from 1.1.1.1[500] to 1.1.1.2[500] (92 bytes) May 20 22:41:52 charon 08[ENC] <con1000|29> parsed INFORMATIONAL_V1 request 219244393 [ HASH N(DPD_ACK) ] May 20 22:41:52 charon 08[IKE] <con1000|29> activating new tasks May 20 22:41:52 charon 08[IKE] <con1000|29> nothing to initiate May 20 22:42:13 charon 08[NET] <con1000|29> received packet: from 1.1.1.1[500] to 1.1.1.2[500] (92 bytes) May 20 22:42:13 charon 08[ENC] <con1000|29> parsed INFORMATIONAL_V1 request 4025856574 [ HASH N(DPD) ] May 20 22:42:13 charon 08[IKE] <con1000|29> queueing ISAKMP_DPD task May 20 22:42:13 charon 08[IKE] <con1000|29> activating new tasks May 20 22:42:13 charon 08[IKE] <con1000|29> activating ISAKMP_DPD task May 20 22:42:13 charon 08[ENC] <con1000|29> generating INFORMATIONAL_V1 request 3355157915 [ HASH N(DPD_ACK) ] May 20 22:42:13 charon 08[NET] <con1000|29> sending packet: from 1.1.1.2[500] to 1.1.1.1[500] (92 bytes) May 20 22:42:13 charon 08[IKE] <con1000|29> activating new tasks May 20 22:42:13 charon 08[IKE] <con1000|29> nothing to initiate May 20 22:42:23 charon 08[IKE] <con1000|29> sending DPD request May 20 22:42:23 charon 08[IKE] <con1000|29> queueing ISAKMP_DPD task May 20 22:42:23 charon 08[IKE] <con1000|29> activating new tasks May 20 22:42:23 charon 08[IKE] <con1000|29> activating ISAKMP_DPD task May 20 22:42:23 charon 08[ENC] <con1000|29> generating INFORMATIONAL_V1 request 1194493161 [ HASH N(DPD) ] May 20 22:42:23 charon 08[NET] <con1000|29> sending packet: from 1.1.1.2[500] to 1.1.1.1[500] (92 bytes) May 20 22:42:23 charon 08[IKE] <con1000|29> activating new tasks May 20 22:42:23 charon 08[IKE] <con1000|29> nothing to initiate May 20 22:42:23 charon 08[NET] <con1000|29> received packet: from 1.1.1.1[500] to 1.1.1.2[500] (92 bytes) May 20 22:42:23 charon 08[ENC] <con1000|29> parsed INFORMATIONAL_V1 request 3002549347 [ HASH N(DPD_ACK) ] May 20 22:42:23 charon 08[IKE] <con1000|29> activating new tasks May 20 22:42:23 charon 08[IKE] <con1000|29> nothing to initiate May 20 22:42:35 charon 08[NET] <con1000|29> received packet: from 1.1.1.1[500] to 1.1.1.2[500] (92 bytes) May 20 22:42:35 charon 08[ENC] <con1000|29> parsed INFORMATIONAL_V1 request 484372825 [ HASH N(DPD) ] May 20 22:42:35 charon 08[IKE] <con1000|29> queueing ISAKMP_DPD task May 20 22:42:35 charon 08[IKE] <con1000|29> activating new tasks May 20 22:42:35 charon 08[IKE] <con1000|29> activating ISAKMP_DPD task May 20 22:42:35 charon 08[ENC] <con1000|29> generating INFORMATIONAL_V1 request 30301262 [ HASH N(DPD_ACK) ] May 20 22:42:35 charon 08[NET] <con1000|29> sending packet: from 1.1.1.2[500] to 1.1.1.1[500] (92 bytes) May 20 22:42:35 charon 08[IKE] <con1000|29> activating new tasks May 20 22:42:35 charon 08[IKE] <con1000|29> nothing to initiate May 20 22:42:45 charon 11[NET] <con1000|29> received packet: from 1.1.1.1[500] to 1.1.1.2[500] (92 bytes) May 20 22:42:45 charon 11[ENC] <con1000|29> parsed INFORMATIONAL_V1 request 3214602504 [ HASH N(DPD) ] May 20 22:42:45 charon 11[IKE] <con1000|29> queueing ISAKMP_DPD task May 20 22:42:45 charon 11[IKE] <con1000|29> activating new tasks May 20 22:42:45 charon 11[IKE] <con1000|29> activating ISAKMP_DPD task May 20 22:42:45 charon 11[ENC] <con1000|29> generating INFORMATIONAL_V1 request 871769119 [ HASH N(DPD_ACK) ] May 20 22:42:45 charon 11[NET] <con1000|29> sending packet: from 1.1.1.2[500] to 1.1.1.1[500] (92 bytes) May 20 22:42:45 charon 11[IKE] <con1000|29> activating new tasks May 20 22:42:45 charon 11[IKE] <con1000|29> nothing to initiate May 20 22:42:57 charon 11[NET] <con1000|29> received packet: from 1.1.1.1[500] to 1.1.1.2[500] (92 bytes) May 20 22:42:57 charon 11[ENC] <con1000|29> parsed INFORMATIONAL_V1 request 560429149 [ HASH N(DPD) ] May 20 22:42:57 charon 11[IKE] <con1000|29> queueing ISAKMP_DPD task May 20 22:42:57 charon 11[IKE] <con1000|29> activating new tasks May 20 22:42:57 charon 11[IKE] <con1000|29> activating ISAKMP_DPD task May 20 22:42:57 charon 11[ENC] <con1000|29> generating INFORMATIONAL_V1 request 2874258477 [ HASH N(DPD_ACK) ] May 20 22:42:57 charon 11[NET] <con1000|29> sending packet: from 1.1.1.2[500] to 1.1.1.1[500] (92 bytes) May 20 22:42:57 charon 11[IKE] <con1000|29> activating new tasks May 20 22:42:57 charon 11[IKE] <con1000|29> nothing to initiate May 20 22:43:07 charon 15[NET] <con1000|29> received packet: from 1.1.1.1[500] to 1.1.1.2[500] (92 bytes) May 20 22:43:07 charon 15[ENC] <con1000|29> parsed INFORMATIONAL_V1 request 1885910885 [ HASH N(DPD) ] May 20 22:43:07 charon 15[IKE] <con1000|29> queueing ISAKMP_DPD task May 20 22:43:07 charon 15[IKE] <con1000|29> activating new tasks May 20 22:43:07 charon 15[IKE] <con1000|29> activating ISAKMP_DPD task May 20 22:43:07 charon 15[ENC] <con1000|29> generating INFORMATIONAL_V1 request 3325439433 [ HASH N(DPD_ACK) ] May 20 22:43:07 charon 15[NET] <con1000|29> sending packet: from 1.1.1.2[500] to 1.1.1.1[500] (92 bytes) May 20 22:43:07 charon 15[IKE] <con1000|29> activating new tasks May 20 22:43:07 charon 15[IKE] <con1000|29> nothing to initiate May 20 22:43:10 charon 09[CFG] vici client 799 connected May 20 22:43:10 charon 14[CFG] vici client 799 registered for: list-sa May 20 22:43:10 charon 15[CFG] vici client 799 requests: list-sas May 20 22:43:10 charon 09[CFG] vici client 799 disconnected May 20 22:43:15 charon 15[CFG] vici client 800 connected May 20 22:43:15 charon 09[CFG] vici client 800 registered for: list-sa May 20 22:43:15 charon 09[CFG] vici client 800 requests: list-sas May 20 22:43:15 charon 15[CFG] vici client 800 disconnected May 20 22:43:19 charon 15[IKE] <con1000|29> sending DPD request May 20 22:43:19 charon 15[IKE] <con1000|29> queueing ISAKMP_DPD task May 20 22:43:19 charon 15[IKE] <con1000|29> activating new tasks May 20 22:43:19 charon 15[IKE] <con1000|29> activating ISAKMP_DPD task May 20 22:43:19 charon 15[ENC] <con1000|29> generating INFORMATIONAL_V1 request 258169317 [ HASH N(DPD) ] May 20 22:43:19 charon 15[NET] <con1000|29> sending packet: from 1.1.1.2[500] to 1.1.1.1[500] (92 bytes) May 20 22:43:19 charon 15[IKE] <con1000|29> activating new tasks May 20 22:43:19 charon 15[IKE] <con1000|29> nothing to initiate May 20 22:43:19 charon 15[NET] <con1000|29> received packet: from 1.1.1.1[500] to 1.1.1.2[500] (92 bytes) May 20 22:43:19 charon 15[ENC] <con1000|29> parsed INFORMATIONAL_V1 request 1271110288 [ HASH N(DPD_ACK) ] May 20 22:43:19 charon 15[IKE] <con1000|29> activating new tasks May 20 22:43:19 charon 15[IKE] <con1000|29> nothing to initiate May 20 22:43:20 charon 13[CFG] vici client 801 connected May 20 22:43:20 charon 13[CFG] vici client 801 registered for: list-sa May 20 22:43:20 charon 15[CFG] vici client 801 requests: list-sas May 20 22:43:20 charon 10[CFG] vici client 801 disconnected -
@Kowex
Это немного не то
Это просто обмен DPD пакетами
Нужен журнал установления соединения .... и нужно увидеть , в чем ошибка -
@Konstanti не пинайте, а где он?
-
@Kowex
Это тот же журнал , кусок которого Вы показали
только немного раньше .... когда устанавливается соединение -
May 20 22:58:37 charon 15[CFG] vici client 809 connected May 20 22:58:37 charon 10[CFG] vici client 809 registered for: list-sa May 20 22:58:37 charon 10[CFG] vici client 809 requests: list-sas May 20 22:58:37 charon 10[CFG] vici client 809 disconnected May 20 22:58:41 charon 14[CFG] rereading secrets May 20 22:58:41 charon 14[CFG] loading secrets from '/var/etc/ipsec/ipsec.secrets' May 20 22:58:41 charon 14[CFG] loaded IKE secret for %any 1.1.1.1 May 20 22:58:41 charon 14[CFG] rereading ca certificates from '/usr/local/etc/ipsec.d/cacerts' May 20 22:58:41 charon 14[CFG] rereading aa certificates from '/usr/local/etc/ipsec.d/aacerts' May 20 22:58:41 charon 14[CFG] rereading ocsp signer certificates from '/usr/local/etc/ipsec.d/ocspcerts' May 20 22:58:41 charon 14[CFG] rereading attribute certificates from '/usr/local/etc/ipsec.d/acerts' May 20 22:58:41 charon 14[CFG] rereading crls from '/usr/local/etc/ipsec.d/crls' May 20 22:58:41 charon 07[CFG] received stroke: unroute 'bypasslan' May 20 22:58:41 ipsec_starter 54100 shunt policy 'bypasslan' uninstalled May 20 22:58:41 charon 14[CFG] received stroke: delete connection 'bypasslan' May 20 22:58:41 charon 14[CFG] deleted connection 'bypasslan' May 20 22:58:41 charon 08[CFG] received stroke: unroute 'con1000' May 20 22:58:41 charon 08[CHD] CHILD_SA con1000{72} state change: ROUTED => DESTROYING May 20 22:58:41 ipsec_starter 54100 trap policy 'con1000' unrouted May 20 22:58:41 charon 14[CFG] received stroke: delete connection 'con1000' May 20 22:58:41 charon 14[CFG] deleted connection 'con1000' May 20 22:58:41 charon 08[CFG] received stroke: unroute 'con1001' May 20 22:58:41 charon 08[CHD] CHILD_SA con1001{73} state change: ROUTED => DESTROYING May 20 22:58:41 ipsec_starter 54100 trap policy 'con1001' unrouted May 20 22:58:41 charon 14[CFG] received stroke: delete connection 'con1001' May 20 22:58:41 charon 14[CFG] deleted connection 'con1001' May 20 22:58:41 charon 08[CFG] received stroke: add connection 'bypasslan' May 20 22:58:41 charon 08[CFG] conn bypasslan May 20 22:58:41 charon 08[CFG] left=%any May 20 22:58:41 charon 08[CFG] leftsubnet=192.168.1.0/24 May 20 22:58:41 charon 08[CFG] right=%any May 20 22:58:41 charon 08[CFG] rightsubnet=192.168.1.0/24 May 20 22:58:41 charon 08[CFG] dpddelay=30 May 20 22:58:41 charon 08[CFG] dpdtimeout=150 May 20 22:58:41 charon 08[CFG] sha256_96=no May 20 22:58:41 charon 08[CFG] mediation=no May 20 22:58:41 charon 08[CFG] added configuration 'bypasslan' May 20 22:58:41 charon 14[CFG] received stroke: route 'bypasslan' May 20 22:58:41 ipsec_starter 54100 'bypasslan' shunt PASS policy installed May 20 22:58:41 charon 09[CFG] received stroke: add connection 'con1000' May 20 22:58:41 charon 09[CFG] conn con1000 May 20 22:58:41 charon 09[CFG] left=1.1.1.2 May 20 22:58:41 charon 09[CFG] leftsubnet=192.168.1.0/24 May 20 22:58:41 charon 09[CFG] leftauth=psk May 20 22:58:41 charon 09[CFG] leftid=1.1.1.2 May 20 22:58:41 charon 09[CFG] right=office.domen.ru May 20 22:58:41 charon 09[CFG] rightsubnet=192.168.0.0/24 May 20 22:58:41 charon 09[CFG] rightauth=psk May 20 22:58:41 charon 09[CFG] rightid=1.1.1.1 May 20 22:58:41 charon 09[CFG] ike=aes256-sha1-modp1024! May 20 22:58:41 charon 09[CFG] esp=aes256-sha1,aes192-sha1,aes128-sha1! May 20 22:58:41 charon 09[CFG] dpddelay=10 May 20 22:58:41 charon 09[CFG] dpdtimeout=60 May 20 22:58:41 charon 09[CFG] dpdaction=3 May 20 22:58:41 charon 09[CFG] sha256_96=no May 20 22:58:41 charon 09[CFG] mediation=no May 20 22:58:41 charon 09[CFG] keyexchange=ikev1 May 20 22:58:41 charon 09[CFG] added configuration 'con1000' May 20 22:58:41 charon 08[CFG] received stroke: route 'con1000' May 20 22:58:41 charon 08[CFG] configured proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ May 20 22:58:41 charon 08[CHD] CHILD_SA con1000{74} state change: CREATED => ROUTED May 20 22:58:41 ipsec_starter 54100 'con1000' routed May 20 22:58:41 charon 09[CFG] received stroke: add connection 'con1001' May 20 22:58:41 charon 09[CFG] conn con1001 May 20 22:58:41 charon 09[CFG] left=1.1.1.2 May 20 22:58:41 charon 09[CFG] leftsubnet=192.168.1.0/24 May 20 22:58:41 charon 09[CFG] leftauth=psk May 20 22:58:41 charon 09[CFG] leftid=1.1.1.2 May 20 22:58:41 charon 09[CFG] right=office.domen.ru May 20 22:58:41 charon 09[CFG] rightsubnet=192.168.192.0/24 May 20 22:58:41 charon 09[CFG] rightauth=psk May 20 22:58:41 charon 09[CFG] rightid=1.1.1.1 May 20 22:58:41 charon 09[CFG] ike=aes256-sha1-modp1024! May 20 22:58:41 charon 09[CFG] esp=aes256-sha1,aes192-sha1,aes128-sha1! May 20 22:58:41 charon 09[CFG] dpddelay=10 May 20 22:58:41 charon 09[CFG] dpdtimeout=60 May 20 22:58:41 charon 09[CFG] dpdaction=3 May 20 22:58:41 charon 09[CFG] sha256_96=no May 20 22:58:41 charon 09[CFG] mediation=no May 20 22:58:41 charon 09[CFG] keyexchange=ikev1 May 20 22:58:41 charon 09[CFG] added child to existing configuration 'con1000' May 20 22:58:41 charon 08[CFG] received stroke: route 'con1001' May 20 22:58:41 charon 08[CFG] configured proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ May 20 22:58:41 charon 08[CHD] CHILD_SA con1001{75} state change: CREATED => ROUTED May 20 22:58:41 ipsec_starter 54100 'con1001' routed May 20 22:58:43 charon 15[CFG] vici client 810 connected May 20 22:58:43 charon 15[CFG] vici client 810 registered for: list-sa May 20 22:58:43 charon 12[CFG] vici client 810 requests: list-sas May 20 22:58:43 charon 15[CFG] vici client 810 disconnected May 20 22:58:44 charon 15[IKE] <con1000|29> sending DPD request May 20 22:58:44 charon 15[IKE] <con1000|29> queueing ISAKMP_DPD task May 20 22:58:44 charon 15[IKE] <con1000|29> activating new tasks May 20 22:58:44 charon 15[IKE] <con1000|29> activating ISAKMP_DPD task May 20 22:58:44 charon 15[ENC] <con1000|29> generating INFORMATIONAL_V1 request 3985228861 [ HASH N(DPD) ] May 20 22:58:44 charon 15[NET] <con1000|29> sending packet: from 1.1.1.2[500] to 1.1.1.1[500] (92 bytes) May 20 22:58:44 charon 15[IKE] <con1000|29> activating new tasks May 20 22:58:44 charon 15[IKE] <con1000|29> nothing to initiate May 20 22:58:44 charon 15[NET] <con1000|29> received packet: from 1.1.1.1[500] to 1.1.1.2[500] (92 bytes) May 20 22:58:44 charon 15[ENC] <con1000|29> parsed INFORMATIONAL_V1 request 3367427594 [ HASH N(DPD_ACK) ] May 20 22:58:44 charon 15[IKE] <con1000|29> activating new tasks May 20 22:58:44 charon 15[IKE] <con1000|29> nothing to initiate May 20 22:58:46 charon 11[CFG] vici client 811 connected May 20 22:58:46 charon 15[CFG] vici client 811 registered for: list-sa May 20 22:58:46 charon 11[CFG] vici client 811 requests: list-sas May 20 22:58:46 charon 11[CFG] vici client 811 disconnected May 20 22:58:54 charon 11[IKE] <con1000|29> sending DPD request May 20 22:58:54 charon 11[IKE] <con1000|29> queueing ISAKMP_DPD task May 20 22:58:54 charon 11[IKE] <con1000|29> activating new tasks May 20 22:58:54 charon 11[IKE] <con1000|29> activating ISAKMP_DPD task May 20 22:58:54 charon 11[ENC] <con1000|29> generating INFORMATIONAL_V1 request 923050361 [ HASH N(DPD) ] May 20 22:58:54 charon 11[NET] <con1000|29> sending packet: from 1.1.1.2[500] to 1.1.1.1[500] (92 bytes) May 20 22:58:54 charon 11[IKE] <con1000|29> activating new tasks May 20 22:58:54 charon 11[IKE] <con1000|29> nothing to initiate May 20 22:58:54 charon 10[NET] <con1000|29> received packet: from 1.1.1.1[500] to 1.1.1.2[500] (92 bytes) May 20 22:58:54 charon 10[ENC] <con1000|29> parsed INFORMATIONAL_V1 request 3973572512 [ HASH N(DPD) ] May 20 22:58:54 charon 10[IKE] <con1000|29> queueing ISAKMP_DPD task May 20 22:58:54 charon 10[IKE] <con1000|29> activating new tasks May 20 22:58:54 charon 10[IKE] <con1000|29> activating ISAKMP_DPD task May 20 22:58:54 charon 10[ENC] <con1000|29> generating INFORMATIONAL_V1 request 1379165606 [ HASH N(DPD_ACK) ] May 20 22:58:54 charon 10[NET] <con1000|29> sending packet: from 1.1.1.2[500] to 1.1.1.1[500] (92 bytes) May 20 22:58:54 charon 10[IKE] <con1000|29> activating new tasks May 20 22:58:54 charon 10[IKE] <con1000|29> nothing to initiate May 20 22:58:54 charon 10[NET] <con1000|29> received packet: from 1.1.1.1[500] to 1.1.1.2[500] (92 bytes) May 20 22:58:54 charon 10[ENC] <con1000|29> parsed INFORMATIONAL_V1 request 1704107891 [ HASH N(DPD_ACK) ] May 20 22:58:54 charon 10[IKE] <con1000|29> activating new tasks May 20 22:58:54 charon 10[IKE] <con1000|29> nothing to initiate May 20 22:59:06 charon 10[NET] <con1000|29> received packet: from 1.1.1.1[500] to 1.1.1.2[500] (92 bytes) May 20 22:59:06 charon 10[ENC] <con1000|29> parsed INFORMATIONAL_V1 request 1403021559 [ HASH N(DPD) ] May 20 22:59:06 charon 10[IKE] <con1000|29> queueing ISAKMP_DPD task May 20 22:59:06 charon 10[IKE] <con1000|29> activating new tasks May 20 22:59:06 charon 10[IKE] <con1000|29> activating ISAKMP_DPD task May 20 22:59:06 charon 10[ENC] <con1000|29> generating INFORMATIONAL_V1 request 1202476669 [ HASH N(DPD_ACK) ] May 20 22:59:06 charon 10[NET] <con1000|29> sending packet: from 1.1.1.2[500] to 1.1.1.1[500] (92 bytes) May 20 22:59:06 charon 10[IKE] <con1000|29> activating new tasks May 20 22:59:06 charon 10[IKE] <con1000|29> nothing to initiate -
@Kowex
Ради интереса
Покажите вывод команды "ipsec statusall" из консолии что можно увидеть в
/Status/IPsec/SPDs -
Status of IKE charon daemon (strongSwan 5.8.2, FreeBSD 11.3-STABLE, amd64): uptime: 50 minutes, since May 20 22:19:26 2020 worker threads: 11 of 16 idle, 5/0/0/0 working, job queue: 0/0/0/0, scheduled: 3 loaded plugins: charon unbound aes des blowfish rc2 sha2 sha1 md4 md5 random nonce x509 revocation constraints pubkey pkcs1 pkcs7 pkcs8 pkcs12 pgp dnskey sshkey ipseckey pem openssl fips-prf curve25519 xcbc cmac hmac drbg curl attr kernel-pfkey kernel-pfroute resolve socket-default stroke vici updown eap-identity eap-sim eap-md5 eap-mschapv2 eap-dynamic eap-radius eap-tls eap-ttls eap-peap xauth-generic xauth-eap xauth-pam whitelist addrblock counters Listening IP addresses: 192.168.0.254 1.1.1.1 192.168.192.1 Connections: bypasslan: %any...%any IKEv1/2 bypasslan: local: uses public key authentication bypasslan: remote: uses public key authentication bypasslan: child: 192.168.0.0/24|/0 === 192.168.0.0/24|/0 PASS con1000: 1.1.1.1...shop.domen.ru IKEv1, dpddelay=10s con1000: local: [1.1.1.1] uses pre-shared key authentication con1000: remote: [1.1.1.2] uses pre-shared key authentication con1000: child: 192.168.0.0/24|/0 === 192.168.1.0/24|/0 TUNNEL, dpdaction=restart con1001: child: 192.168.192.0/24|/0 === 192.168.1.0/24|/0 TUNNEL, dpdaction=restart Shunted Connections: bypasslan: 192.168.0.0/24|/0 === 192.168.0.0/24|/0 PASS Routed Connections: con1001{9}: ROUTED, TUNNEL, reqid 5 con1001{9}: 192.168.192.0/24|/0 === 192.168.1.0/24|/0 con1000{8}: ROUTED, TUNNEL, reqid 3 con1000{8}: 192.168.0.0/24|/0 === 192.168.1.0/24|/0 Security Associations (1 up, 0 connecting): con1000[4]: ESTABLISHED 33 minutes ago, 1.1.1.1[1.1.1.1]...1.1.1.2[1.1.1.2] con1000[4]: IKEv1 SPIs: 41e4c753c5391f47_i* ffa36a079875b43d_r, rekeying disabled con1000[4]: IKE proposal: AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 con1000{7}: INSTALLED, TUNNEL, reqid 3, ESP SPIs: c2f50112_i c1845d41_o con1000{7}: AES_CBC_256/HMAC_SHA1_96, 2741944 bytes_i (3232 pkts, 18s ago), 868272 bytes_o (2176 pkts, 18s ago), rekeying disabled con1000{7}: 192.168.0.0/24|/0 === 192.168.1.0/24|/0 -
@Kowex
Попробуйте не перезапустить , а остановить IPSEC и запустить заново
И покажите журнал установления соединения -
192.168.1.0/24 192.168.0.0/24 ◄ Inbound ESP 1.1.1.2 -> 1.1.1.1 192.168.1.0/24 192.168.192.0/24 ◄ Inbound ESP 1.1.1.2 -> 1.1.1.1 192.168.0.0/24 192.168.1.0/24 ► Outbound ESP 1.1.1.1 -> 1.1.1.2 192.168.192.0/24 192.168.1.0/24 ► Outbound ESP 1.1.1.1 -> 1.1.1.2 -
May 20 23:25:38 ipsec_starter 4358 Starting strongSwan 5.8.2 IPsec [starter]... May 20 23:25:38 charon 00[DMN] Starting IKE charon daemon (strongSwan 5.8.2, FreeBSD 11.3-STABLE, amd64) May 20 23:25:38 charon 00[KNL] unable to set UDP_ENCAP: Invalid argument May 20 23:25:38 charon 00[NET] enabling UDP decapsulation for IPv6 on port 4500 failed May 20 23:25:38 charon 00[CFG] loading unbound resolver config from '/etc/resolv.conf' May 20 23:25:38 charon 00[CFG] loading unbound trust anchors from '/usr/local/etc/ipsec.d/dnssec.keys' May 20 23:25:38 charon 00[CFG] ipseckey plugin is disabled May 20 23:25:38 charon 00[CFG] loading ca certificates from '/usr/local/etc/ipsec.d/cacerts' May 20 23:25:38 charon 00[CFG] loading aa certificates from '/usr/local/etc/ipsec.d/aacerts' May 20 23:25:38 charon 00[CFG] loading ocsp signer certificates from '/usr/local/etc/ipsec.d/ocspcerts' May 20 23:25:38 charon 00[CFG] loading attribute certificates from '/usr/local/etc/ipsec.d/acerts' May 20 23:25:38 charon 00[CFG] loading crls from '/usr/local/etc/ipsec.d/crls' May 20 23:25:38 charon 00[CFG] loading secrets from '/var/etc/ipsec/ipsec.secrets' May 20 23:25:38 charon 00[CFG] loaded IKE secret for %any 1.1.1.2 May 20 23:25:38 charon 00[CFG] loaded IKE secret for 1 May 20 23:25:38 charon 00[CFG] opening triplet file /usr/local/etc/ipsec.d/triplets.dat failed: No such file or directory May 20 23:25:38 charon 00[CFG] loaded 0 RADIUS server configurations May 20 23:25:38 charon 00[LIB] loaded plugins: charon unbound aes des blowfish rc2 sha2 sha1 md4 md5 random nonce x509 revocation constraints pubkey pkcs1 pkcs7 pkcs8 pkcs12 pgp dnskey sshkey ipseckey pem openssl fips-prf curve25519 xcbc cmac hmac drbg curl attr kernel-pfkey kernel-pfroute resolve socket-default stroke vici updown eap-identity eap-sim eap-md5 eap-mschapv2 eap-dynamic eap-radius eap-tls eap-ttls eap-peap xauth-generic xauth-eap xauth-pam whitelist addrblock counters May 20 23:25:38 charon 00[JOB] spawning 16 worker threads May 20 23:25:38 ipsec_starter 4787 charon (4926) started after 20 ms May 20 23:25:38 charon 16[CFG] received stroke: add connection 'bypasslan' May 20 23:25:38 charon 16[CFG] conn bypasslan May 20 23:25:38 charon 16[CFG] left=%any May 20 23:25:38 charon 16[CFG] leftsubnet=192.168.0.0/24 May 20 23:25:38 charon 16[CFG] right=%any May 20 23:25:38 charon 16[CFG] rightsubnet=192.168.0.0/24 May 20 23:25:38 charon 16[CFG] dpddelay=30 May 20 23:25:38 charon 16[CFG] dpdtimeout=150 May 20 23:25:38 charon 16[CFG] sha256_96=no May 20 23:25:38 charon 16[CFG] mediation=no May 20 23:25:38 charon 16[CFG] added configuration 'bypasslan' May 20 23:25:38 charon 13[CFG] received stroke: route 'bypasslan' May 20 23:25:38 ipsec_starter 4787 'bypasslan' shunt PASS policy installed May 20 23:25:38 charon 16[CFG] received stroke: add connection 'con1000' May 20 23:25:38 charon 16[CFG] conn con1000 May 20 23:25:38 charon 16[CFG] left=1.1.1.1 May 20 23:25:38 charon 16[CFG] leftsubnet=192.168.0.0/24 May 20 23:25:38 charon 16[CFG] leftauth=psk May 20 23:25:38 charon 16[CFG] leftid=1.1.1.1 May 20 23:25:38 charon 16[CFG] right=shop.domen.ru May 20 23:25:38 charon 16[CFG] rightsubnet=192.168.1.0/24 May 20 23:25:38 charon 16[CFG] rightauth=psk May 20 23:25:38 charon 16[CFG] rightid=1.1.1.2 May 20 23:25:38 charon 16[CFG] ike=aes256-sha1-modp1024! May 20 23:25:38 charon 16[CFG] esp=aes256-sha1,aes192-sha1,aes128-sha1! May 20 23:25:38 charon 16[CFG] dpddelay=10 May 20 23:25:38 charon 16[CFG] dpdtimeout=60 May 20 23:25:38 charon 16[CFG] dpdaction=3 May 20 23:25:38 charon 16[CFG] sha256_96=no May 20 23:25:38 charon 16[CFG] mediation=no May 20 23:25:38 charon 16[CFG] keyexchange=ikev1 May 20 23:25:38 charon 16[CFG] added configuration 'con1000' May 20 23:25:38 charon 13[CFG] received stroke: route 'con1000' May 20 23:25:38 charon 13[CFG] configured proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ May 20 23:25:38 charon 13[CHD] CHILD_SA con1000{1} state change: CREATED => ROUTED May 20 23:25:38 ipsec_starter 4787 'con1000' routed May 20 23:25:38 charon 16[CFG] received stroke: add connection 'con1001' May 20 23:25:38 charon 16[CFG] conn con1001 May 20 23:25:38 charon 16[CFG] left=1.1.1.1 May 20 23:25:38 charon 16[CFG] leftsubnet=192.168.192.0/24 May 20 23:25:38 charon 16[CFG] leftauth=psk May 20 23:25:38 charon 16[CFG] leftid=1.1.1.1 May 20 23:25:38 charon 16[CFG] right=shop.domen.ru May 20 23:25:38 charon 16[CFG] rightsubnet=192.168.1.0/24 May 20 23:25:38 charon 16[CFG] rightauth=psk May 20 23:25:38 charon 16[CFG] rightid=1.1.1.2 May 20 23:25:38 charon 16[CFG] ike=aes256-sha1-modp1024! May 20 23:25:38 charon 16[CFG] esp=aes256-sha1,aes192-sha1,aes128-sha1! May 20 23:25:38 charon 16[CFG] dpddelay=10 May 20 23:25:38 charon 16[CFG] dpdtimeout=60 May 20 23:25:38 charon 16[CFG] dpdaction=3 May 20 23:25:38 charon 16[CFG] sha256_96=no May 20 23:25:38 charon 16[CFG] mediation=no May 20 23:25:38 charon 16[CFG] keyexchange=ikev1 May 20 23:25:38 charon 16[CFG] added child to existing configuration 'con1000' May 20 23:25:38 charon 13[CFG] received stroke: route 'con1001' May 20 23:25:38 charon 13[CFG] configured proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ May 20 23:25:38 charon 13[CHD] CHILD_SA con1001{2} state change: CREATED => ROUTED May 20 23:25:38 ipsec_starter 4787 'con1001' routed May 20 23:25:38 charon 15[KNL] creating acquire job for policy 1.1.1.1/32|/0 === 1.1.1.2/32|/0 with reqid {1} May 20 23:25:38 charon 16[IKE] <con1000|1> queueing ISAKMP_VENDOR task May 20 23:25:38 charon 16[IKE] <con1000|1> queueing ISAKMP_CERT_PRE task May 20 23:25:38 charon 16[IKE] <con1000|1> queueing MAIN_MODE task May 20 23:25:38 charon 16[IKE] <con1000|1> queueing ISAKMP_CERT_POST task May 20 23:25:38 charon 16[IKE] <con1000|1> queueing ISAKMP_NATD task May 20 23:25:38 charon 16[IKE] <con1000|1> queueing QUICK_MODE task May 20 23:25:38 charon 16[IKE] <con1000|1> activating new tasks May 20 23:25:38 charon 16[IKE] <con1000|1> activating ISAKMP_VENDOR task May 20 23:25:38 charon 16[IKE] <con1000|1> activating ISAKMP_CERT_PRE task May 20 23:25:38 charon 16[IKE] <con1000|1> activating MAIN_MODE task May 20 23:25:38 charon 16[IKE] <con1000|1> activating ISAKMP_CERT_POST task May 20 23:25:38 charon 16[IKE] <con1000|1> activating ISAKMP_NATD task May 20 23:25:38 charon 16[IKE] <con1000|1> sending XAuth vendor ID May 20 23:25:38 charon 16[IKE] <con1000|1> sending DPD vendor ID May 20 23:25:38 charon 16[IKE] <con1000|1> sending FRAGMENTATION vendor ID May 20 23:25:38 charon 16[IKE] <con1000|1> sending NAT-T (RFC 3947) vendor ID May 20 23:25:38 charon 16[IKE] <con1000|1> sending draft-ietf-ipsec-nat-t-ike-02\n vendor ID May 20 23:25:38 charon 16[IKE] <con1000|1> initiating Main Mode IKE_SA con1000[1] to 1.1.1.2 May 20 23:25:38 charon 16[IKE] <con1000|1> IKE_SA con1000[1] state change: CREATED => CONNECTING May 20 23:25:38 charon 16[CFG] <con1000|1> configured proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 May 20 23:25:38 charon 16[ENC] <con1000|1> generating ID_PROT request 0 [ SA V V V V V ] May 20 23:25:38 charon 16[NET] <con1000|1> sending packet: from 1.1.1.1[500] to 1.1.1.2[500] (180 bytes) May 20 23:25:38 charon 16[NET] <con1000|1> received packet: from 1.1.1.2[500] to 1.1.1.1[500] (160 bytes) May 20 23:25:38 charon 16[ENC] <con1000|1> parsed ID_PROT response 0 [ SA V V V V ] May 20 23:25:38 charon 16[IKE] <con1000|1> received XAuth vendor ID May 20 23:25:38 charon 16[IKE] <con1000|1> received DPD vendor ID May 20 23:25:38 charon 16[IKE] <con1000|1> received FRAGMENTATION vendor ID May 20 23:25:38 charon 16[IKE] <con1000|1> received NAT-T (RFC 3947) vendor ID May 20 23:25:38 charon 16[CFG] <con1000|1> selecting proposal: May 20 23:25:38 charon 16[CFG] <con1000|1> proposal matches May 20 23:25:38 charon 16[CFG] <con1000|1> received proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 May 20 23:25:38 charon 16[CFG] <con1000|1> configured proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 May 20 23:25:38 charon 16[CFG] <con1000|1> selected proposal: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 May 20 23:25:38 charon 16[IKE] <con1000|1> reinitiating already active tasks May 20 23:25:38 charon 16[IKE] <con1000|1> ISAKMP_VENDOR task May 20 23:25:38 charon 16[IKE] <con1000|1> MAIN_MODE task May 20 23:25:38 charon 16[ENC] <con1000|1> generating ID_PROT request 0 [ KE No NAT-D NAT-D ] May 20 23:25:38 charon 16[NET] <con1000|1> sending packet: from 1.1.1.1[500] to 1.1.1.2[500] (244 bytes) May 20 23:25:38 charon 16[NET] <con1000|1> received packet: from 1.1.1.2[500] to 1.1.1.1[500] (244 bytes) May 20 23:25:38 charon 16[ENC] <con1000|1> parsed ID_PROT response 0 [ KE No NAT-D NAT-D ] May 20 23:25:38 charon 16[IKE] <con1000|1> reinitiating already active tasks May 20 23:25:38 charon 16[IKE] <con1000|1> ISAKMP_VENDOR task May 20 23:25:38 charon 16[IKE] <con1000|1> MAIN_MODE task May 20 23:25:38 charon 16[ENC] <con1000|1> generating ID_PROT request 0 [ ID HASH N(INITIAL_CONTACT) ] May 20 23:25:38 charon 16[NET] <con1000|1> sending packet: from 1.1.1.1[500] to 1.1.1.2[500] (108 bytes) May 20 23:25:38 charon 16[NET] <con1000|1> received packet: from 1.1.1.2[500] to 1.1.1.1[500] (76 bytes) May 20 23:25:38 charon 16[ENC] <con1000|1> parsed ID_PROT response 0 [ ID HASH ] May 20 23:25:38 charon 16[IKE] <con1000|1> IKE_SA con1000[1] established between 1.1.1.1[1.1.1.1]...1.1.1.2[1.1.1.2] May 20 23:25:38 charon 16[IKE] <con1000|1> IKE_SA con1000[1] state change: CONNECTING => ESTABLISHED May 20 23:25:38 charon 16[IKE] <con1000|1> activating new tasks May 20 23:25:38 charon 16[IKE] <con1000|1> activating QUICK_MODE task May 20 23:25:38 charon 16[CFG] <con1000|1> configured proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ May 20 23:25:38 charon 16[CFG] <con1000|1> configured proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ May 20 23:25:38 charon 16[CFG] <con1000|1> proposing traffic selectors for us: May 20 23:25:38 charon 16[CFG] <con1000|1> 192.168.0.0/24|/0 May 20 23:25:38 charon 16[CFG] <con1000|1> proposing traffic selectors for other: May 20 23:25:38 charon 16[CFG] <con1000|1> 192.168.1.0/24|/0 May 20 23:25:38 charon 16[ENC] <con1000|1> generating QUICK_MODE request 2775791088 [ HASH SA No ID ID ] May 20 23:25:38 charon 16[NET] <con1000|1> sending packet: from 1.1.1.1[500] to 1.1.1.2[500] (220 bytes) May 20 23:25:38 charon 16[NET] <con1000|1> received packet: from 1.1.1.2[500] to 1.1.1.1[500] (188 bytes) May 20 23:25:38 charon 16[ENC] <con1000|1> parsed QUICK_MODE response 2775791088 [ HASH SA No ID ID ] May 20 23:25:38 charon 16[CFG] <con1000|1> selecting proposal: May 20 23:25:38 charon 16[CFG] <con1000|1> proposal matches May 20 23:25:38 charon 16[CFG] <con1000|1> received proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ May 20 23:25:38 charon 16[CFG] <con1000|1> configured proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ May 20 23:25:38 charon 16[CFG] <con1000|1> selected proposal: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ May 20 23:25:38 charon 16[IKE] <con1000|1> received 28800s lifetime, configured 0s May 20 23:25:38 charon 16[CHD] <con1000|1> CHILD_SA con1000{3} state change: CREATED => INSTALLING May 20 23:25:38 charon 16[CHD] <con1000|1> using AES_CBC for encryption May 20 23:25:38 charon 16[CHD] <con1000|1> using HMAC_SHA1_96 for integrity May 20 23:25:38 charon 16[CHD] <con1000|1> adding inbound ESP SA May 20 23:25:38 charon 16[CHD] <con1000|1> SPI 0xcf0cb126, src 1.1.1.2 dst 1.1.1.1 May 20 23:25:38 charon 16[CHD] <con1000|1> adding outbound ESP SA May 20 23:25:38 charon 16[CHD] <con1000|1> SPI 0xc32a300a, src 1.1.1.1 dst 1.1.1.2 May 20 23:25:38 charon 16[IKE] <con1000|1> CHILD_SA con1000{3} established with SPIs cf0cb126_i c32a300a_o and TS 192.168.0.0/24|/0 === 192.168.1.0/24|/0 May 20 23:25:38 charon 16[CHD] <con1000|1> CHILD_SA con1000{3} state change: INSTALLING => INSTALLED May 20 23:25:38 charon 16[IKE] <con1000|1> reinitiating already active tasks May 20 23:25:38 charon 16[IKE] <con1000|1> QUICK_MODE task May 20 23:25:38 charon 16[ENC] <con1000|1> generating QUICK_MODE request 2775791088 [ HASH ] May 20 23:25:38 charon 16[NET] <con1000|1> sending packet: from 1.1.1.1[500] to 1.1.1.2[500] (60 bytes) May 20 23:25:38 charon 16[IKE] <con1000|1> activating new tasks May 20 23:25:38 charon 16[IKE] <con1000|1> nothing to initiate May 20 23:25:43 charon 10[CFG] vici client 1 connected May 20 23:25:43 charon 09[CFG] vici client 1 registered for: list-sa May 20 23:25:43 charon 08[CFG] vici client 1 requests: list-sas May 20 23:25:43 charon 09[CFG] vici client 1 disconnected -
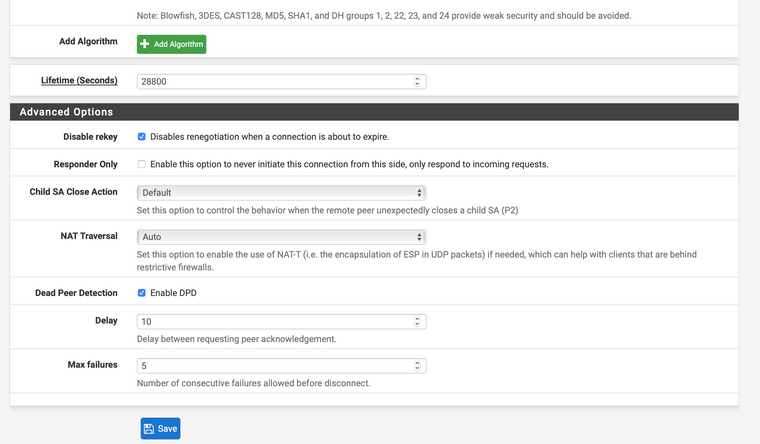
@Kowex В настройках фазы 1 есть опция
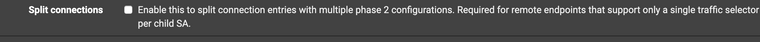
Попробуйте ее отметить с обеих сторон и посмотреть результат
-
@Konstanti странно, но у меня в фазе 1 нет такого параметра.
-
@Kowex В самом низу , Advanced options
-
@Konstanti да я уже понял что там должно быть.