Test Request: UPnP Fix for Multiple Consoles playing the same game / static port outbound NAT
-
There has been some progress by the
miniupnpdproject on support for pf to handle rules like the Linux "masquerade" style. This may help improve how multiple consoles behave when playing the same game, or even to allow single consoles to work without setting up static port outbound NAT rules, provided the game/client sets up UPnP entries for the ports it needs.We have compiled a test version of miniupnpd for pfSense 2.5.0 snapshots containing the in-development code which can be used to test if this helps in your environment. [Note: This version will not work on 2.4.5, do not attempt to use it there]
The package to download, and instructions on how to use it, are at https://redmine.pfsense.org/issues/7727#note-43
Please post feedback and discussion here on the forum and not on the Redmine issue.
-
Hey there!
Thanks again everyone! But weirdly, it doesn't appear to be working correctly for me for some reason, as one console can still get on the game (diablo 3) with the same configuration (Static outbound ports, uPnP ACL, NAT reflection, etc) but any other console cannot join the lobby... I noticed some IPv6 stuff in the logs, so I disabled IPv6 from the WAN interface as I don't use it anyways.
Now I get this in the logs:
@Jun 2 06:33:11 miniupnpd 26938 no HTTP IPv6 address, disabling IPv6 Jun 2 06:33:11 miniupnpd 26938 Listening for NAT-PMP/PCP traffic on port 5351 Jun 2 06:33:11 miniupnpd 26938 PCPSendUnsolicitedAnnounce() IPv6 sendto(): Bad file descriptor Jun 2 06:40:05 miniupnpd 26938 ioctl(s, SIOCGIFADDR, ...): Can't assign requested address Jun 2 06:40:05 miniupnpd 26938 ioctl(s, SIOCGIFADDR, ...): Can't assign requested address Jun 2 06:40:05 miniupnpd 26938 Failed to get IP for interface pppoe0 Jun 2 06:40:05 miniupnpd 26938 SendNATPMPPublicAddressChangeNotification: cannot get public IP address, stopping Jun 2 06:40:05 miniupnpd 26938 PCPSendUnsolicitedAnnounce() sendto(): No route to host Jun 2 06:40:05 miniupnpd 26938 PCPSendUnsolicitedAnnounce() IPv6 sendto(): Bad file descriptor Jun 2 06:40:11 miniupnpd 26938 SendNATPMPPublicAddressChangeNotification: sendto(s_udp=10, port=5351): No route to host Jun 2 06:40:11 miniupnpd 26938 PCPSendUnsolicitedAnnounce() sendto(): No route to host Jun 2 06:40:11 miniupnpd 26938 PCPSendUnsolicitedAnnounce() IPv6 sendto(): Bad file descriptor@(I feel obligated to say I did restart the service and the whole pfsense install after the patch, still no luck)
Seeing this version of miniupnpd creates the equivalent outbound NAT rule, maybe I need to disable the manual outbound NAT rules I've already got in place for this to be properly tested?Oh! and the following commands give no output unfortunantly: "pfctl -a miniupnpd -s rules" either does "pfctl -a miniupnpd -s nat"....
I also see no miniupnp rules/requests appear in the logs either under: Status > UPnP & NAT-PMP for me :(Any other commands I can try on SSH or the command prompt /GUI to troubleshoot this some more for you guys?
Thanks! -
To make sure you're checking the right way for the rules, see what shows up in
pfSsh.php playback pfanchordrill.Granted I don't have IPv6 on my WAN, but I am not seeing anything like those errors. It may be specific to PPPoE, though.
-
i have pppoe the service start
i have only this on my log
i don't have any console to try, i can test later with something elseJun 3 17:44:00 miniupnpd 54810 Listening for NAT-PMP/PCP traffic on port 5351
Jun 3 17:44:00 miniupnpd 54810 setsockopt(udp, IPV6_RECVPKTINFO): Invalid argument
Jun 3 17:44:00 miniupnpd 54810 HTTP IPv6 address given to control points : [2001:470:26:5dc::1]
Jun 3 17:44:00 miniupnpd 54810 HTTP listening on port 2189 -
@jimp said in Test Request: UPnP Fix for Multiple Consoles playing the same game / static port outbound NAT:
pfSsh.php playback pfanchordrill
Ahhhhh! Thank you for that command and break-down.
I see the results now, but the contents are still blank/empty as seen below:miniupnpd rules/nat contents:Now I currently do have each xbox on it's own static IP and static port Outbound NAT setup. I did read in your first post that it could likely allow single consoles to work without setting up static port outbound NAT rules, but I have multiple, should I be testing this updated miniupnpd version with those static port Outbbound NAT rules disabled or keep them enabled for the multiple consoles in this example?
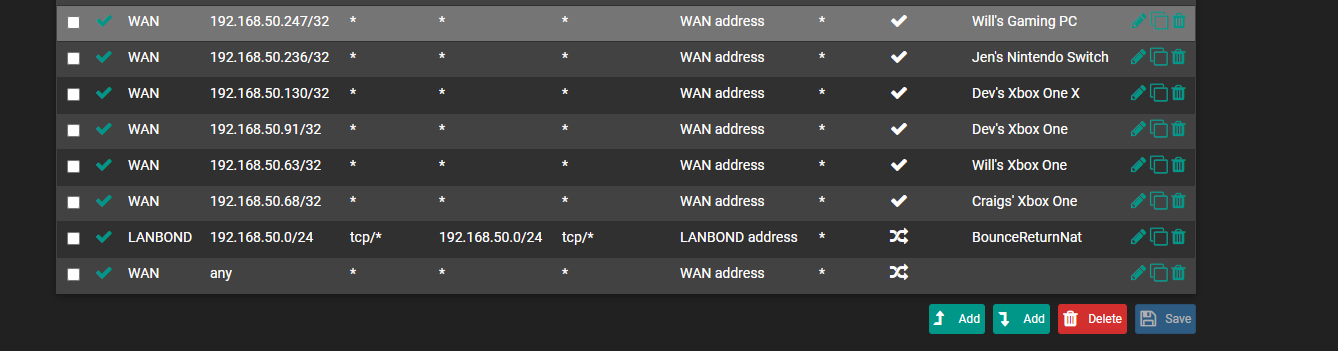
I am no expert in this by any means, but do have an environment where this can be tested as much as needed.
Simply let me know what you need, and I will provide! (logs, config files, etc) to help troubleshoot this.Also just to mention, I did have IPv6 on WAN, but disabled it to stop the IPv6 related errors in miniupnpd which seems to have somewhat worked as it does this now:
miniupnpd 26938 no HTTP IPv6 address, disabling IPv6But I still get the following with IPv6 disabled on all interfaces:
Jun 2 06:33:11 miniupnpd 26938 Listening for NAT-PMP/PCP traffic on port 5351 Jun 2 06:33:11 miniupnpd 26938 PCPSendUnsolicitedAnnounce() IPv6 sendto(): Bad file descriptor Jun 2 06:40:05 miniupnpd 26938 ioctl(s, SIOCGIFADDR, ...): Can't assign requested address Jun 2 06:40:05 miniupnpd 26938 ioctl(s, SIOCGIFADDR, ...): Can't assign requested address Jun 2 06:40:05 miniupnpd 26938 Failed to get IP for interface pppoe0 Jun 2 06:40:05 miniupnpd 26938 SendNATPMPPublicAddressChangeNotification: cannot get public IP address, stopping Jun 2 06:40:05 miniupnpd 26938 PCPSendUnsolicitedAnnounce() sendto(): No route to hostThanks
-
Whether or not it helps is contingent upon the game (and/or console) managing the ports it uses with UPnP. Some do, some do not.
-
I was able to get everything working following this guide: https://forum.netgate.com/topic/144291/howto-multiples-xbox-play-together-without-upnp-dmz
I only have 2 xboxs that usually conflict using the same games even though we have 5 in the house. I was unable to get any progress with this miniupnpd version though unfortunately.
This seemed to solve the issue for those 2 consoles as found here: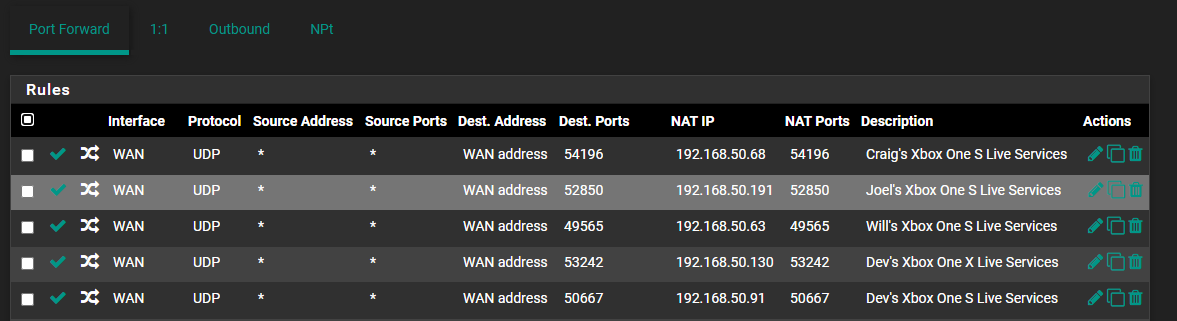
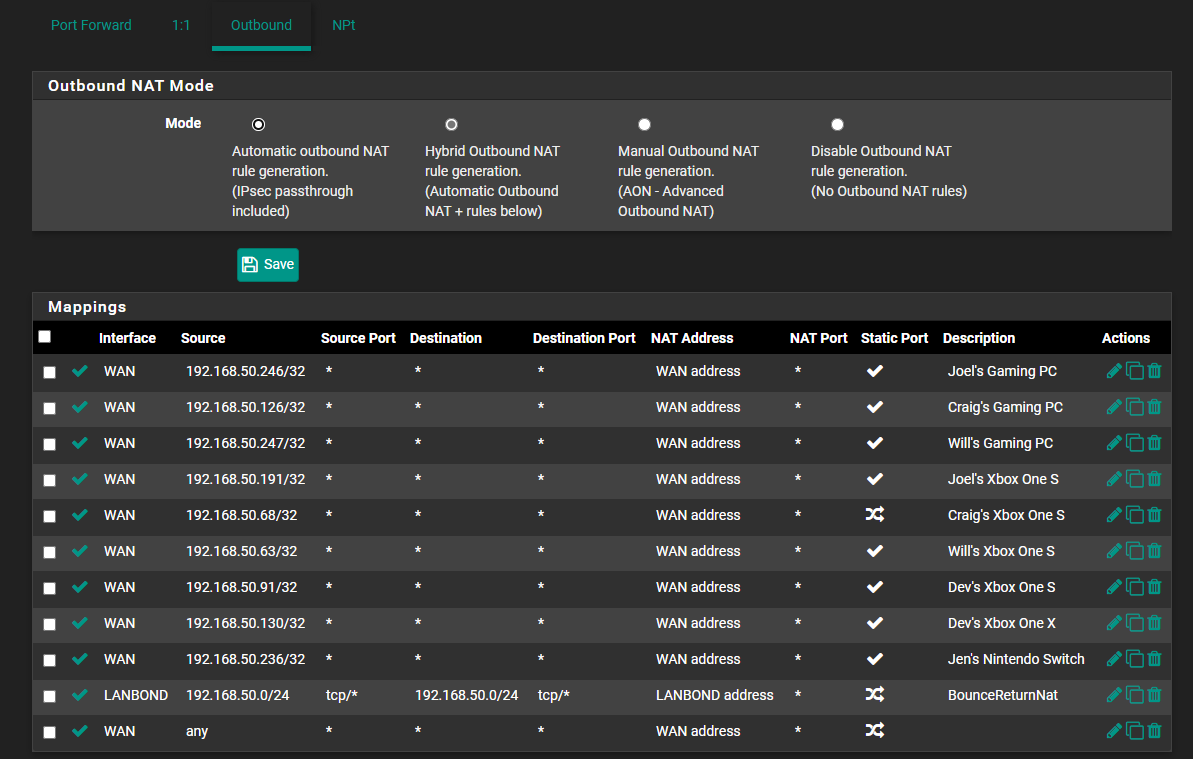
-
OK, this thread is just for feedback about the test version of miniupnpd, but it's a good data point to know that it didn't help your situation. I'd expect the static method to be unchanged since this is only a change to how UPnP forms its rules. If the consoles are doing static/custom ports and not UPnP then this won't help.
-
Fair enough, I am still willing to test this with other games and consoles, but the errors mentioned above seemed to cause this version of miniupnpd to shutdown.
I did notice some extra changes in Github, would these make a difference if compiled for testing?Thanks again Jim :)
-
Not yet, we'd have to build a new version with the new changes manually patched in like we did before. Time is short at the moment so unlikely to happen any time in the next few days.
-
No worries at all Jim :) Take your time. I at least have a static config that works for the 2 conflicting consoles for now.
I will keep watch for any updates or requests for testing in the future. -
I tested this with two PS4's.
The network test on a PS4 is set to a constant port of 9308. Hence, running the PS4's network test on the first console gives NAT Type 2, and running the same test on the second console gives NAT Type Failed (sometimes NAT Type 3). Running the game Destiny 2, I can see ports being opened in UPnP in the GUI, with and without the patch.
Here is the command output without the patch:
[2.5.0-DEVELOPMENT][admin@gw.ruhex.net]/root: pfSsh.php playback pfanchordrill ipsec rules/nat contents: miniupnpd rules/nat contents: rdr quick on igb0 inet proto udp from any to any port = 9308 keep state label "10.0.5.40:9308 to 9308 (UDP)" rtable 0 -> 10.0.5.40 port 9308 # First PS4 network test rdr quick on igb0 inet proto udp from any to any port = 3074 keep state label "DemonwarePortMapping" rtable 0 -> 10.0.5.40 port 3074 rdr quick on igb0 inet proto udp from any to any port = 3075 keep state label "DemonwarePortMapping" rtable 0 -> 10.0.5.43 port 3075 rdr quick on igb0 inet proto udp from any to any port = 22389 keep state label "DemonwarePortMapping" rtable 0 -> 10.0.5.40 port 22389 rdr quick on igb0 inet proto udp from any to any port = 14626 keep state label "DemonwarePortMapping" rtable 0 -> 10.0.5.43 port 14626 pass in quick on igb0 inet proto udp from any to 10.0.5.40 port = 9308 flags S/SA keep state label "10.0.5.40:9308 to 9308 (UDP)" rtable 0 pass in quick on igb0 inet proto udp from any to 10.0.5.40 port = 3074 flags S/SA keep state label "DemonwarePortMapping" rtable 0 pass in quick on igb0 inet proto udp from any to 10.0.5.43 port = 3075 flags S/SA keep state label "DemonwarePortMapping" rtable 0 pass in quick on igb0 inet proto udp from any to 10.0.5.40 port = 22389 flags S/SA keep state label "DemonwarePortMapping" rtable 0 pass in quick on igb0 inet proto udp from any to 10.0.5.43 port = 14626 flags S/SA keep state label "DemonwarePortMapping" rtable 0 natearly rules/nat contents: natrules rules/nat contents: openvpn rules/nat contents: tftp-proxy rules/nat contents: userrules rules/nat contents:Same tests/game with the patch:
[2.5.0-DEVELOPMENT][admin@gw.ruhex.net]/root: pfSsh.php playback pfanchordrill ipsec rules/nat contents: miniupnpd rules/nat contents: nat quick on igb0 inet proto udp from 10.0.5.40 port = 9308 to any keep state label "10.0.5.40:9308 to 9308 (UDP)" rtable 0 -> x.x.x.x port 9308 nat quick on igb0 inet proto udp from 10.0.5.40 port = 22388 to any keep state label "DemonwarePortMapping" rtable 0 -> x.x.x.x port 22388 nat quick on igb0 inet proto udp from 10.0.5.43 port = 3076 to any keep state label "DemonwarePortMapping" rtable 0 -> x.x.x.x port 3076 nat quick on igb0 inet proto udp from 10.0.5.43 port = 14625 to any keep state label "DemonwarePortMapping" rtable 0 -> x.x.x.x port 14625 nat quick on igb0 inet proto udp from 10.0.5.40 port = 3075 to any keep state label "DemonwarePortMapping" rtable 0 -> x.x.x.x port 3075 rdr quick on igb0 inet proto udp from any to any port = 9308 keep state label "10.0.5.40:9308 to 9308 (UDP)" rtable 0 -> 10.0.5.40 port 9308 rdr quick on igb0 inet proto udp from any to any port = 22388 keep state label "DemonwarePortMapping" rtable 0 -> 10.0.5.40 port 22388 rdr quick on igb0 inet proto udp from any to any port = 3076 keep state label "DemonwarePortMapping" rtable 0 -> 10.0.5.43 port 3076 rdr quick on igb0 inet proto udp from any to any port = 14625 keep state label "DemonwarePortMapping" rtable 0 -> 10.0.5.43 port 14625 rdr quick on igb0 inet proto udp from any to any port = 3075 keep state label "DemonwarePortMapping" rtable 0 -> 10.0.5.40 port 3075 pass in quick on igb0 inet proto udp from any to 10.0.5.40 port = 9308 flags S/SA keep state label "10.0.5.40:9308 to 9308 (UDP)" rtable 0 pass in quick on igb0 inet proto udp from any to 10.0.5.40 port = 22388 flags S/SA keep state label "DemonwarePortMapping" rtable 0 pass in quick on igb0 inet proto udp from any to 10.0.5.43 port = 3076 flags S/SA keep state label "DemonwarePortMapping" rtable 0 pass in quick on igb0 inet proto udp from any to 10.0.5.43 port = 14625 flags S/SA keep state label "DemonwarePortMapping" rtable 0 pass in quick on igb0 inet proto udp from any to 10.0.5.40 port = 3075 flags S/SA keep state label "DemonwarePortMapping" rtable 0 natearly rules/nat contents: natrules rules/nat contents: openvpn rules/nat contents: tftp-proxy rules/nat contents: userrules rules/nat contents:I'm not certain if this is an improvement given that I no longer have the game I could reproduce the issue with 100% of the time (Ghost Recon Wildlands). I do see that additonal NAT rules are added however, and I'd assume that these are an improvement, though @jimp would have to say if that's true or not.
-
So if am reading this correctly through the various posts I see two issues, uPNP isnt working at all and more than one console or system attempting to play the same game or service can fail if they need to use the same port on the firewall? I just installed pfSense this weekend and immediately started running into issues with our Nintendo Switch, Amazon tablet etc.
Can someone smarter than myself help me understand how this works with consumer grade firewalls like eero, netgear, comcast, etc...without issue but pfSense chokes on it? This isn't a knock on pfSense by any means as the increase level of visibility and control and plethora of additional features is worth the extra steps provided they work as I am looking to invest in the 7100 model router/firewall but I am just having hard time wrapping my head around an issue thats apparently been around for at least three years and still isnt fully functional. I have read that other routers apparently can be affected by the NAT traversal issue but on my old router I could use two Nintendo Switch's on the same network and same game without NAT issues.
I would love to help test but with the flack I am receiving from my kids I will be forced to put back the other router for now.
Regards
-
There are plenty of topics covering those questions already, this thread is only for testing this fix.
-
This post is deleted! -
So I'm willing to upgrade to 2.5.0 image to test. My only concern is if I switch to the new image will I be able to get back to a stable version without having to wait for a new version? For instance can I go to 2.5.0 and then downgrade back to 2.4.5_1?
-
@vMAC said in Test Request: UPnP Fix for Multiple Consoles playing the same game / static port outbound NAT:
So I'm willing to upgrade to 2.5.0 image to test. My only concern is if I switch to the new image will I be able to get back to a stable version without having to wait for a new version? For instance can I go to 2.5.0 and then downgrade back to 2.4.5_1?
There is no downgrade procedure. Take a config backup first and keep an installer handy for 2.4.5-p1. If something goes wrong on 2.5.0, reinstall 2.4.5-p1 and restore the 2.4.x backup.
-
We have added the 2.2.0-RC1 version of miniupnpd to the repository for pfSense 2.5.0 and so it should be included in snapshots shortly, later today or tomorrow, for additional (and easier) testing.
-
I updated my 5100 from the web UI this morning (from the latest stable official release to the latest devel release.)
I can confirm that, with the correct NAT rules, I seem to be able to get multiple consoles online successfully using UPNP. My household has 3 switches, 2 XBox Ones and 2 PS4s, and I was able to get them all connected simultaneously with suitable NAT levels and no error reports.
I can provide more detailed information to @jimp if necessary.
I'll be doing some more testing later today to make sure I haven't missed anything, but so far so good.
Andrew
-
That's good news!
@andrew_r said in Test Request: UPnP Fix for Multiple Consoles playing the same game / static port outbound NAT:
with the correct NAT rules
Do you mean the correct NAT rules generated automatically by UPnP, or did you have manual rules setup for those consoles?