Limit access between remote locations and local clients?
-
Hi,
I have a situation in which I have a large number of remote hosts that I want to connect to a single VPN server. The remote hosts are unrelated and should not be able to interact with each other.
I also have various users that should be able to access only one specific remote host.
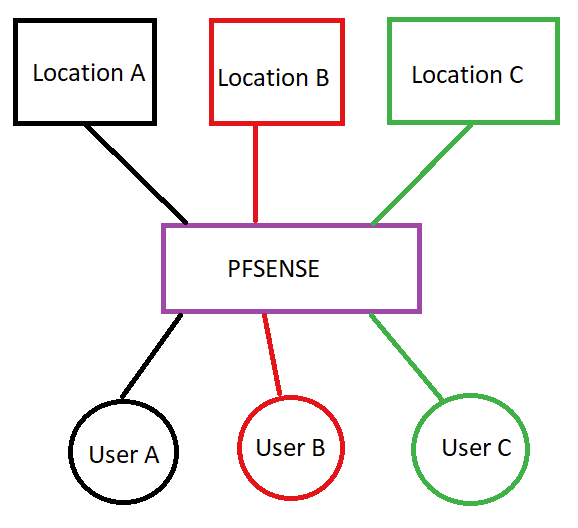
Excuse my poor paint skills. User A should only be able to connect to Location A etc. I know how to setup VPN servers with pfsense but I'm not sure how I can achieve the above in a practical manner.
For example due to firewalling etc. I would like each remote location to be able to connect on port 1194 but if I do that I don't see how I can separate where users can connect to because it will all be the same VPN server inside pfsense.
I can see how it can work with creating a separate VPN server for each location but that does not seem manageable to me given I can have 100+ locations.
Goal:
- Limit user access to specified remote locations
- Allow users to access local lan behind remote network
- Keep things somewhat manageable
How should I go about this or should I be looking at something other than pfsense?
-
You need to hand out the same ip address to each user when they connect via OVPN then create firewall rules for each user to define what they can access.
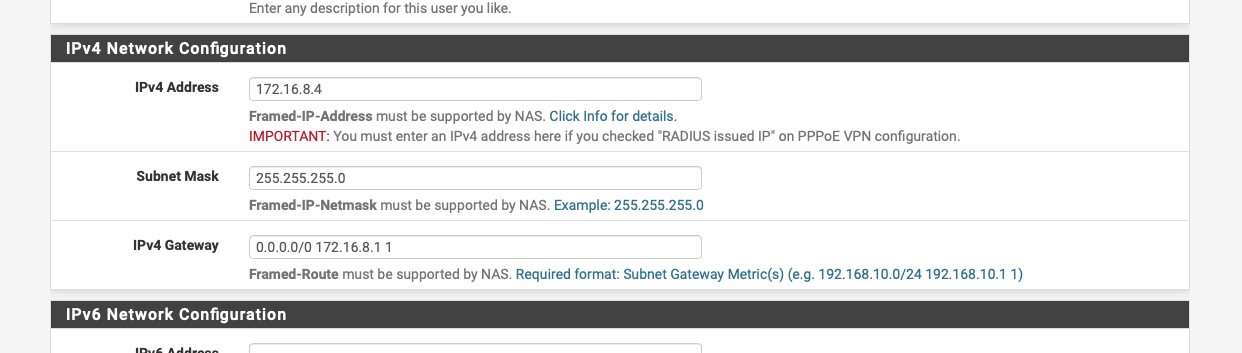
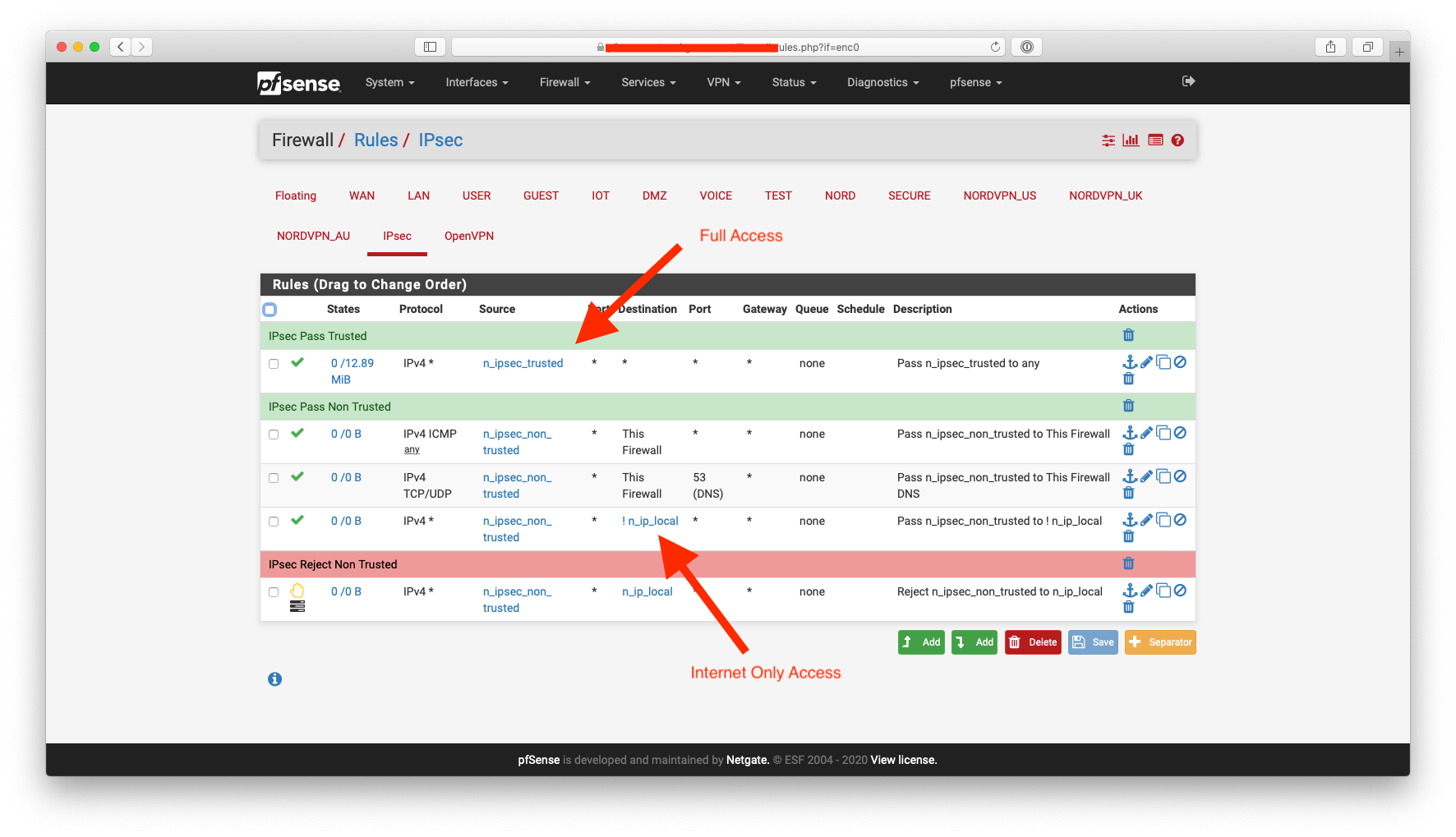
I use an ipsec vpn and freeradius with framed-ip addresses to give me ( TRUSTED ) full access to my network and the internet when i’m connected and internet only access based on the router location to my friends( NON_TRUSTED ).
Freeradius Framed-IP:-
IPsec Firewall Rules:-
-
Thanks for the reply. I'm not sure I follow though. If the source IP is going to be the same for every user, how can I prevent a user from connecting to a location they shouldn't be able to connect to?
-
The IP they are given is tied into their login details, sorry I should have said unique

"andy-ipad" Cleartext-Password := "xxxxxxxxxx", Simultaneous-Use := "1", Expiration := "Apr 11 2027", NAS-Identifier == strongSwan Framed-IP-Address = 172.16.8.2, Framed-IP-Netmask = 255.255.255.0, Framed-Route = "0.0.0.0/0 172.16.8.1 1" "andy-ipad-pro" Cleartext-Password := "xxxxxxxxxx", Simultaneous-Use := "1", Expiration := "Apr 11 2027", NAS-Identifier == strongSwan Framed-IP-Address = 172.16.8.3, Framed-IP-Netmask = 255.255.255.0, Framed-Route = "0.0.0.0/0 172.16.8.1 1" "andy-iphone" Cleartext-Password := "xxxxxxxxxx", Simultaneous-Use := "1", Expiration := "Apr 11 2027", NAS-Identifier == strongSwan Framed-IP-Address = 172.16.8.4, Framed-IP-Netmask = 255.255.255.0, Framed-Route = "0.0.0.0/0 172.16.8.1 1"https://forum.netgate.com/topic/115795/guide-ikev2-ipsec-per-user-firewall-rule-settings-with-freeradius
-
Are the clients connected via the LAN or over a OVPN connection, the wording in the orignal post isn't that clear?
-
Why stress around
If u use openVpn
Do a client spec override to assign always the same ip to the client set the firewall rules and call it a day -
I think I might not have been clear in my first post.
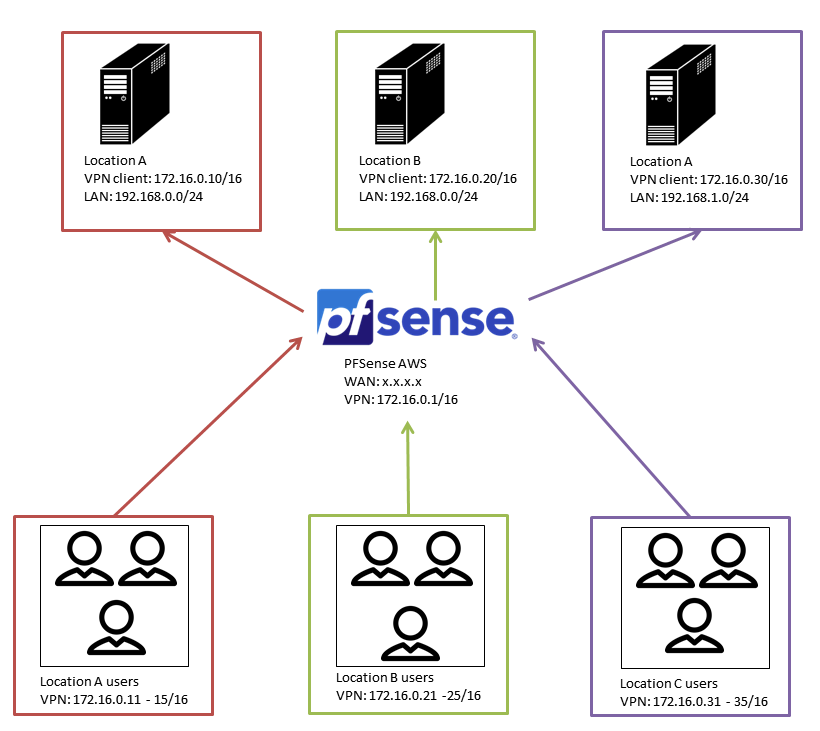
Goals
- One VPN server
- Multiple locations connecting to the server
- Remote location users can connect to the LAN of the respective location
- No connectivity between different locations and users (users belonging to the same location ideally shouldn't be able to communicate with each other either)
- I will have several hundred locations so preferably things have to be kept somewhat manageable.
- Every location should only use to VPN for allow users access to the LAN. All outgoing traffic (unrelated to the VPN) should not pass over the VPN.
So far I've set up the VPN server with two users. Location_A and Location_A_User. On Location_A_User I'm also pushing the route for Location A's local LAN. For testing I've also enabled "allow traffic between clients". Nothing else.
Both users can connect to the server and Location_A_User can connect to Location_A's VPN IP but the user cannot connect to Location_A's LAN. If I do a traceroute I see the traffic destined for the Location's LAN going to the VPN server's IP but nothing from there on.
I'm also worried about how manageable things will be when I have 100+ locations.
I tried looking for some documentation or examples for the kind of setup I want to do but was unable to find anything. All the documentation is either only server client or site to site.
-
@DutchSamurai said in Limit access between remote locations and local clients?:
Location's LAN going to the VPN server's IP but nothing from there on.
so what do u use ?
openVpn or IpSec ?How does Location A-users connect to PfsAWS (dial in eg user from location A opens a VPN tunnel) or is the a pfs box @ locationA-users that connects a tunnel to pfsAWs or another device (router / firewall) that connects to pfsAWS.
of course the same information needed for Location-A how does this network connect to pfsAWs
a wild guess is that you are tryin to set up a site to site vpn
and gettin lost a) in routing the tunnel-net back and b) in the firewall rules regarding the VPN tunneli really dont get it cuz if u r not usin site2site vpn
and u use openVPN Do a client spec override to assign always the same ip
to the client (Location-A-users) set the firewall rules and call it a day -
@DutchSamurai said in Limit access between remote locations and local clients?:
I will have several hundred locations so preferably things have to be kept somewhat manageable.
do u mean 100 locations protected by a Firewall
or
100 users opening a VPN connection (road warrior style) to get a tunnel / connection to their locationif done some crazy stuff in the last months regarding remote workers
but 100 boxes .... oh yeah that really sounds fun ! -
@noplan I'm using openvpn for the moment as that is what I'm most familiar with (though that isn't saying much in my case).
For the moment my test setup looks like this:
- pfsense runs on AWS
- Location A is a Windows box in, well, location A.
- User A is another Windows box located at the office (not location A).
- Both location A and user A connect as a openvpn client to pfsense AWS.
- The openvpn firewall rule is an allow all rule.
I tried pushing the route in the client override and I also tried setting it up according to this link https://www.secure-computing.net/wiki/index.php/OpenVPN/Routing. I can see the 192.168.0.0 and 10.0.0.0 routes appearing on location A and user A (both have the pfsense vpn as gateway for those two subnets) but I cannot get connectivity from for example the 192.168.0.0 subnet to the 10.0.0.0 subnet. Location A and user A can connect to each other on their VPN address.
AS for the boxes, yes, I got over a 100 (probably up to 500) remote locations that need to connect to the pfsense aws. For each location there probably are half a dozen or so remote users that need access to it. Firewall access to the remote locations is limited hence I want the remote location to initiate the connection and tunnel everything over that.
I'm still wondering how its all going to work though, as many remote locations have the same subnet and devices with the same IP. If they connect to the same OpenVPN server, how is that going to work? I also tried subnetting on the OpenVPN server so each location and its users would have a block of IP's but when I tried setting that up it wouldn't work the vpn clients couldn't connect to the openvpn gw ip anymore.
There is also little to no documentation that I can find on how to achieve something like this even though it sounds like something that should be pretty common to me.
-
@DutchSamurai So its 100 locations with pfsense boxes at the edge and users behind each pfsense?
Or is it users with openvpn client connecting directly?
You do say that connectivity is needed behind the remote networks, and that their ip's overlap.
If it was just outbound you could nat, but as you set the goal, most probably you need to renumber.
-
@netblues Its a single pfsense box acting as the hub and the remote locations and remote users are just openvpn clients connecting to the pfsense box.
Changing the remote location lan network is not possible.
The users will have to be clients but it might be possible to put a pfsense/openvpn box at the remote location if that would make things easier.
Edit: Just to be clear, the remote locations don't have any users that need to connect. The remote locations only have some devices that need to be accessible by the remote users.
The remote locations don't allow incoming connections hence the need to have the remote location initiate the VPN connection.
-
so and again why the hustle ...
if u use openVPN and your clients fire up a tunnel to the pfsAWS
its as easyuse
assign a ip to each client with CSO and set a firewall rule.
and it works.
runs fine and smooth even in crazy combinations win/mac/lin/ LDAP&AD envs
-
@DutchSamurai said in Limit access between remote locations and local clients?:
this link
outdated in 2014 !
justsaying -
@DutchSamurai said in Limit access between remote locations and local clients?:
Edit: Just to be clear, the remote locations don't have any users that need to connect. The remote locations only have some devices that need to be accessible by the remote users.
The remote locations don't allow incoming connections hence the need to have the remote location initiate the VPN connection.can u describe a use case for me
sounds like u r running a server farm somewhere seperated by ips and now you want to
enable your users to connect via openVPNARE u shure that your IP ranges are set and not changeable
whats your tunnel network, whats your DNS ?
how do u seperate the users in the tunnel network (prevent them from talkin to each other)oh this is fun ....
-
@noplan The CSO works for assigning a static IP and setting up the VPN tunnel, but it doesn't give the users access to the remote location LAN.
Use case:
All these remote locations are kind of like a small office in remote areas that aren't easily accessible. Various different parties are involved with the network at those locations hence changing the IP's of the local networks is not possible.
Each location has various devices that collect data locally but don't send any of that data. The question I often get is "why can't we connect to those devices from our office?".
Basically people want to set up a connection that a certain remote location, SSH or HTTP to the IP of their device on the remote LAN and download some data.
The remote locations don't belong to a single owner hence there is also the need to keep everything separated.
-
@DutchSamurai If they are devices and not full blown workstastasions, then are they able to run local openvpn clients? This eradicates the need for any renumbering.
If you need to know your devices by ip, then you need to assign them static private ip's.
With careful grouping, firewall rules will do the rest. -
@netblues Sorry, I wasn't clear on that part. We have a Linux box at each remote location that will initiate the VPN connection. If necessary I can also run pfsense (or anything else) on those boxes. The devices themselves cannot run openvpn.
-
thats the classic roas warrior approach you are on.
and yes carefull gouping and rule set
is this a sort of TV setup sounds like
-
@DutchSamurai If you can't renumber, then you will need a proxy, or as it called, a jump host to access the devices.
So the linux box openvpn's to central and establishes ip connectivity.Users ssh to the linux box and then ssh to the iot device.
You could run a 1to 1 nat at the linux box and assign natted ip's for your devices.
However managing this won't be easy