Mail servers imap behind pfsense not reachable
-
Hi,
My mail servers IMAP is not reachable outside of my network.
I can access the mail server in my LAN network.I already created firewall and NAT rules, the ports are open but the IMAP server is not reachable.
NAT:
WAN TCP * * WAN address 143 (IMAP) 192.168.1.200 143 (IMAP) IMAPFirewall rule WAN:
IPv4 TCP * * 192.168.1.200 143 (IMAP) * none NAT IMAPFirewall rule LAN:
IPv4 TCP LAN net * * 143 (IMAP) * none IMAP Rule -
So your Clients connect to the server without SSL encryption? Are you sure?
Possibly the server itself blocks the access from outside its subnet. Check its firewall.
The firewall rule on LAN allows only outbound connection. It is useless for incoming traffic.
-
Clients connect via STARTTLS on port 143.
I do not have any firewall rules on the mail server itself... -
Do you have other port forwarding to internal services behind pfSense which are accessible from the internet for reference?
-
Yes I have http and https services, they work..
WAN TCP * * WAN address 443 (HTTPS) 192.168.1.155 443 (HTTPS) HTTPS ServerWAN TCP * * WAN address 80 (HTTP) 192.168.1.155 80 (HTTP) HTTP Server
-
Anyway, ensure that requests on port 143 arrive on your WAN interface. You may use the Packet Capture tool for investigating.
-
@daan said in Mail servers imap behind pfsense not reachable:
I already created firewall and NAT rules, the ports are open but the IMAP server is not reachable.
NAT:
WAN TCP * * WAN address 143 (IMAP) 192.168.1.200 143 (IMAP) IMAP
Firewall rule WAN:
IPv4 TCP * * 192.168.1.200 143 (IMAP) * none NAT IMAP
Firewall rule LAN:
IPv4 TCP LAN net * * 143 (IMAP) * none IMAP RuleYou have only a LAN and a WAN interface ?
Then you don't need to create a LAN firewall rule.
And just a (one) NAT rule (this action will create a firewall rule, which is, look carefully, linked to the NAT rule - you shoiuld NOT create a WAN firewall rule).HTTPS and HTTP works ? IMAP on port 143 is exactly the same rule, only the port number changes (and your LAN IMAP mail server is on another LAN device)
Btw : 99 % of all web traffic is https now, so you can ditch the http (port 80). The same thing goes for IMAP, do not force people - including yourself - to use 143 = mail goes in clear over the net. NAT port 993 TCP, and, because they are free, easy to set up, use certs that everybody trusts.
Same thing for POP => POPS using port 995 TCP - "110" is dead these days.edit : and forgot the mention the classic one : did you also "NAT" the upstream 'ISP' router ?
Less classic, but it has been seen : your ISP permits a '143' access ?
As @viragomann : launch a packet capture on WAN and you have your answer in a second or two. -
Yes currently I only have a WAN and LAN.
My 143 port is running on STARTTLS, clear text is not allowed.My ISP allows it, because with my previous router (not a pfsense router) it worked fine. Never had any problems.
I just tried to capture packets, I think something is wrong I get TCP Retransmission in Wireshark. I do not know what it means, I want and am currently learning networking..
-
@daan said in Mail servers imap behind pfsense not reachable:
wrong I get TCP Retransmission in Wireshark
You pre selected
Port 143
Protocom TCP
Interface : WAN
right ?You will probably find the same traffic on the LAN side which implies that pfSense :: the NAT rule, is working correcly.
Your IMAP server on LAN accepts connection from the LAN network, not connection from 'else where' like the Internet. Check this.
-
Yes I did
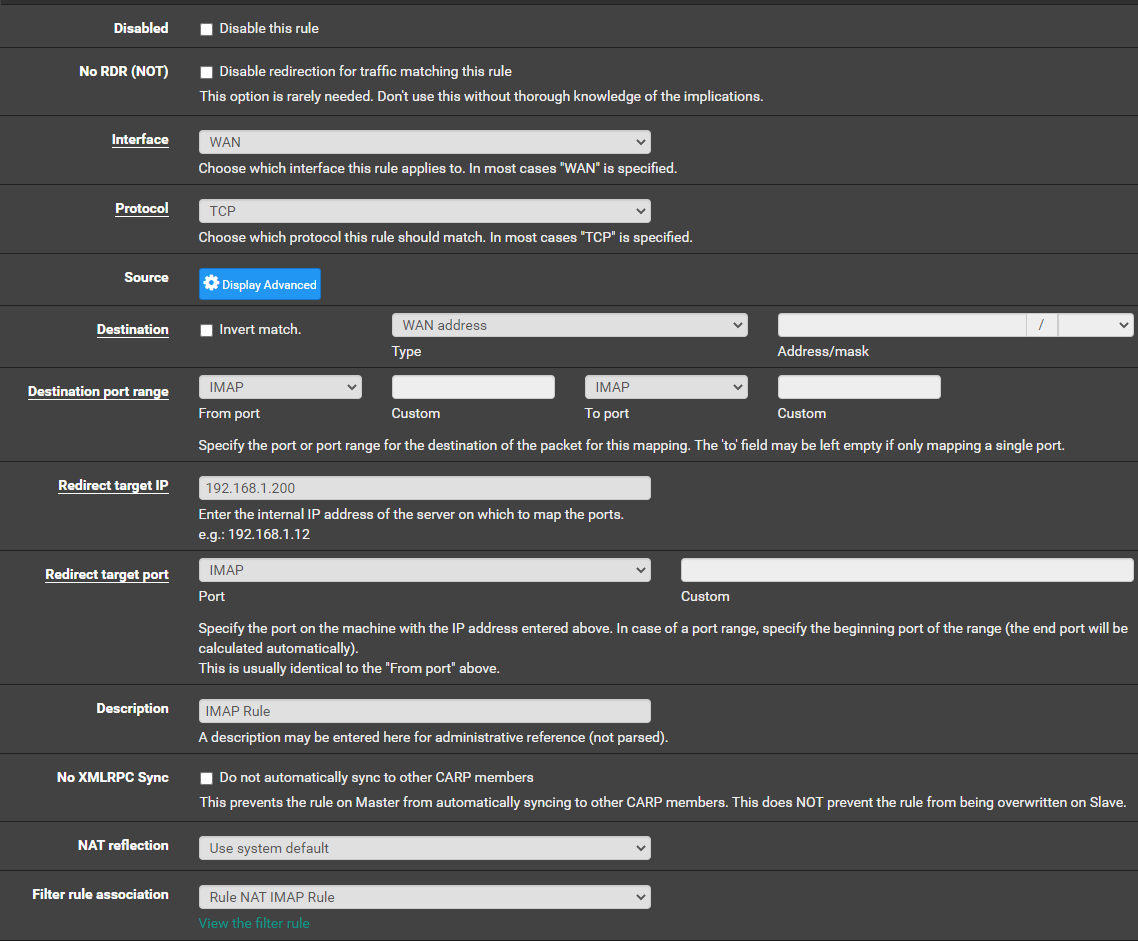
-
Do a packet capture on your LAN port while someone tries to connect from outside and see if the traffic shows up there or not.
-
This is what I get, 192.168.1.118 is my pc.
12:44:52.525535 IP 192.168.1.118.39414 > MY.IP.00.00.143: tcp 0The capture is full with these packets, no incoming packets found..
-
@daan said in Mail servers imap behind pfsense not reachable:
This is what I get, 192.168.1.118 is my pc.
12:44:52.525535 IP 192.168.1.118.39414 > MY.IP.00.00.143: tcp 0Where Exactly are you sniffing for that? Sure isn't your wan of pfsens showing traffic getting to it.. Since the source is rfc1918, doesn't go over the internet.
Step 1 in troubleshooting port forwarding is VALIDATION that traffic gets to wan of pfsense, pfsense can not forward something it never sees..
Then validate it sends it on by sniffing on lan side of pfsense.. Here is example
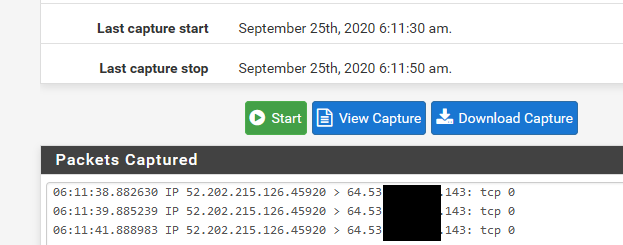
That is my wan... Here is sniff on lan side, showing sending to IP on inside.. And my machine sending back a RST
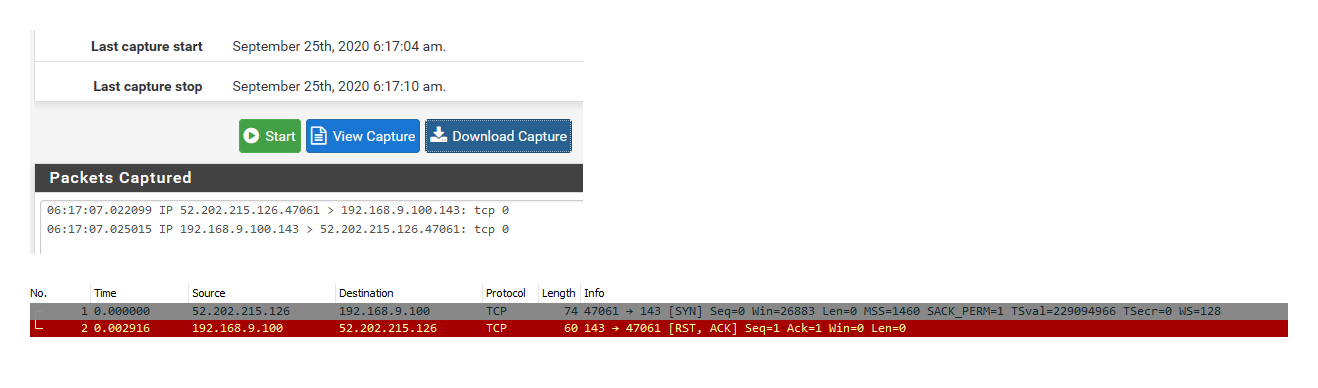
After I setup a port forward.
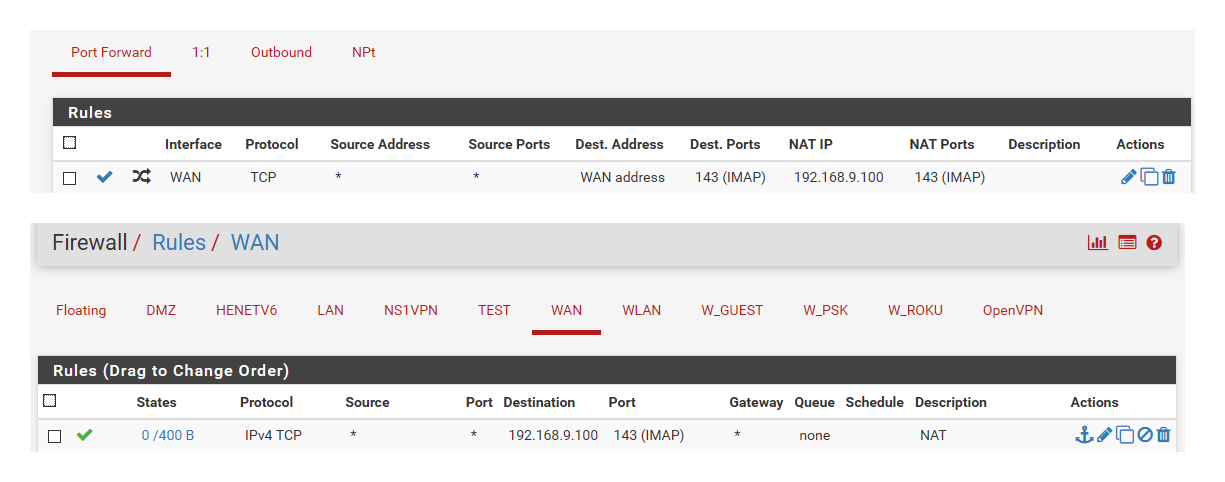
Everything you need to troubleshoot port forwarding is here
https://docs.netgate.com/pfsense/en/latest/troubleshooting/nat.htmljust use can you see me . org to send traffic from the outside.
-
When I check for open LAN ports on 192.168.1.200 (My mail server IP, running in docker) I get the expected output.
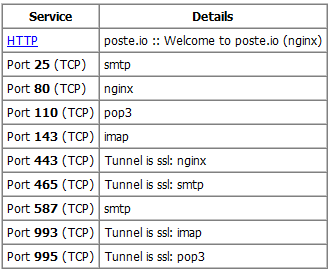
When I check for open ports on " https://www.yougetsignal.com/tools/open-ports/ " the imap and smtp ports are all reachable.
And there is another weird thing, I have my mail setup on my phone. I do get notifications from my email app when I get a new mail (The title and part of the message is readable in the notification), but when I open the app the email is not there and it throws a IMAP connection error..
-
Dude I can not help you if you can not provide the simple info that would take you 10 seconds to provide.
Do a sniff on pfsense wan... Not go to can you see me . org.. put in 143 - do you see the packets on pfsense? If so,
Then sniff on the lan side and repeat the process.. If you see traffic going to your imap server rfc1918 IP.. Then pfsense has done its job.. .Whatever other issues you might be having nothing to do with the simple act of forwarding a port.
I just hit the IP you used to connect to the forum and it is answers via 143
Escape character is '^]'. * OK [CAPABILITY IMAP4rev1 SASL-IR LOGIN-REFERRALS ID ENABLE IDLE XLIST LITERAL+ STARTTLS LOGINDISABLED] Dovecot (Debian) ready. -
Yes I know, when I do a packet capture on my WAN. I get an empty log

I know that the IMAP responds but I can't reach it with a E-Mail client
-
Well then you not sniffing on the right interface, or the correct port?
Are you using PPPoE for your connection?
Or maybe there is something in front of your device answering for these ports? If what your saying is pfsense never sees the traffic. Then you have something in front of pfsense answering?
If your not seeing loads of traffic when you sniff on your wan... Then your sniffing on the wrong interface or you have something wrong with your packet capture.. Do a simple tcpdump from pfsense console.
-
I used these settings
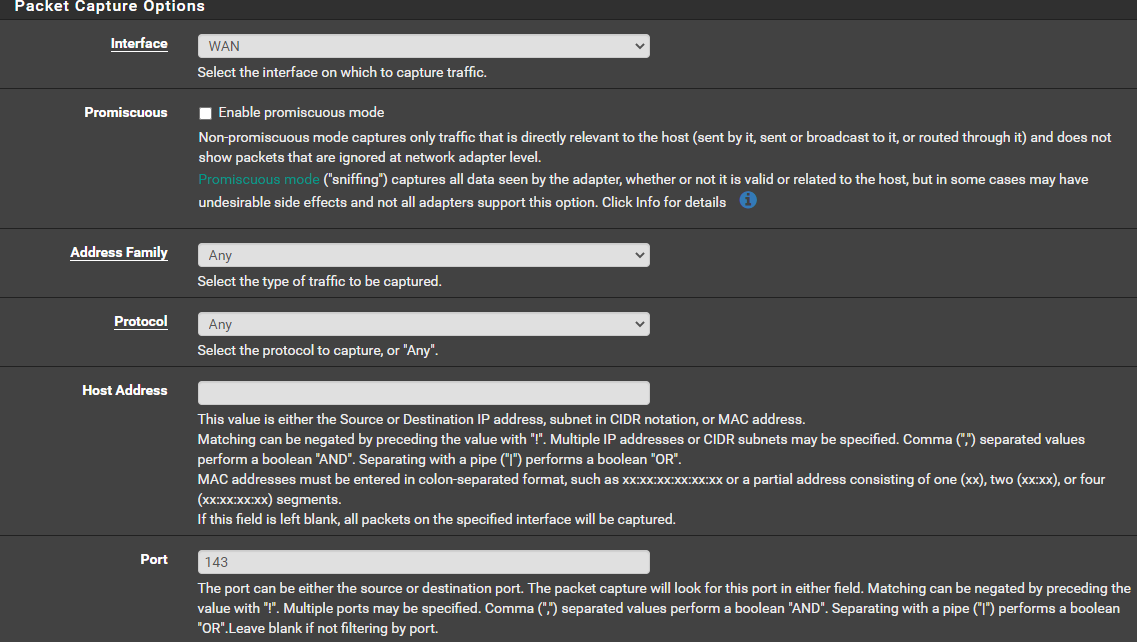
Pfsense is hooked up straight to my ISP modem, my LAN interface goes to a layer 2 cisco switch, the mail server is attached to the switch
-
Well do it without 143, do you see lots of traffic?
If you see lots of normal traffic, and nothing on 143 - then something in front of pfsense is answering for 143..
-
When I do not specify a port I see loads of traffic, HTTPS traffic