OpenVPN client can ping but not access server on LAN
-
Hi All,
I have a OpenVPN server on pfSense 2.4.5-RELEASE-p1 with a tunnel of 192.168.10.0/24 that goes to a local network 192.168.2.0/24 (OPT1) & 192.168.1.0/24 (LAN).
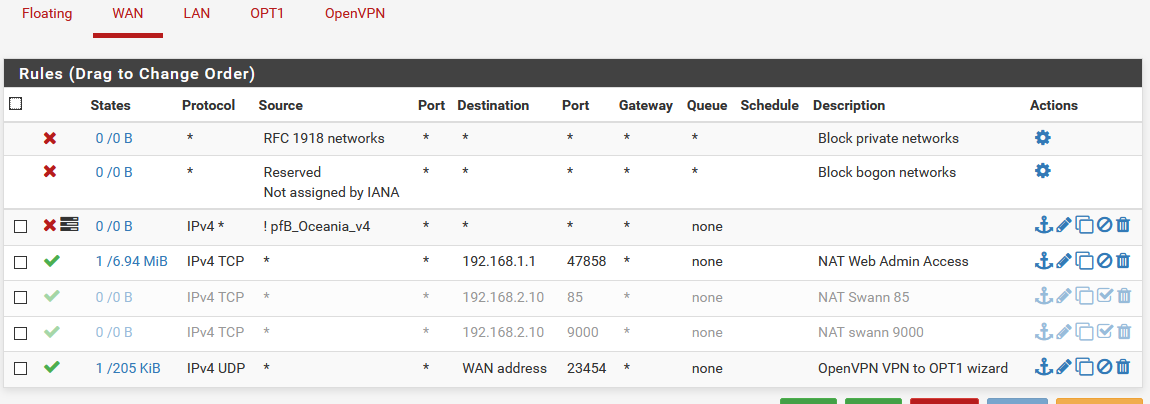
I have a security system I'm trying to access at 192.168.2.10 via it's web interface but are unable to. Once I connect I can see the route in the clients route table to 192.168.2.0/24 via the gateway 192.168.10.1. I can also ping the security system from the client. When I try go to 192.168.2.10:85 in the web browser it just hangs.
If I open up the firewall and port forward ports 85 and 9000 from the WAN to the security system I have no issues.
The same thing goes for the pfSense web GUI from the client, via port forward, no issues. Via the VPN, it just times out, even though I can ping pfSense on 192.168.1.1.
The goal is to isolate the security system on it's own LAN without a gateway as I don't trust the security systems firmware to be secure enough for direct external access.
The VPN was setup using the wizard.
Thanks for taking the time to read,
Andy. -
I did a packet capture on pfSense for 192.168.0.0/16 on port 85, this is what I got.
The Client is 192.168.10.2, and the security system is 192.168.2.10.
11:10:52.215258 IP (tos 0x0, ttl 128, id 30654, offset 0, flags [DF], proto TCP (6), length 40)
192.168.10.2.53680 > 192.168.2.10.85: Flags [R.], cksum 0x4bfd (correct), seq 2501817268, ack 3038185094, win 0, length 0
11:10:52.215334 IP (tos 0x0, ttl 128, id 30655, offset 0, flags [DF], proto TCP (6), length 52)
192.168.10.2.53697 > 192.168.2.10.85: Flags [S], cksum 0xc1b5 (correct), seq 3351086733, win 65535, options [mss 1360,nop,wscale 8,nop,nop,sackOK], length 0
11:10:52.216080 IP (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 52)
192.168.2.10.85 > 192.168.10.2.53697: Flags [S.], cksum 0x6e52 (correct), seq 1476298976, ack 3351086734, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
11:10:52.333288 IP (tos 0x0, ttl 128, id 30656, offset 0, flags [DF], proto TCP (6), length 40)
192.168.10.2.53697 > 192.168.2.10.85: Flags [.], cksum 0x1d35 (correct), seq 1, ack 1, win 1024, length 0
11:10:52.337620 IP (tos 0x0, ttl 128, id 30657, offset 0, flags [DF], proto TCP (6), length 323)
192.168.10.2.53697 > 192.168.2.10.85: Flags [P.], cksum 0x702a (correct), seq 1:284, ack 1, win 1024, length 283
11:10:52.338301 IP (tos 0x0, ttl 63, id 14540, offset 0, flags [DF], proto TCP (6), length 40)
192.168.2.10.85 > 192.168.10.2.53697: Flags [.], cksum 0x1f2d (correct), seq 1, ack 284, win 237, length 0
11:10:52.338772 IP (tos 0x0, ttl 63, id 14541, offset 0, flags [DF], proto TCP (6), length 148)
192.168.2.10.85 > 192.168.10.2.53697: Flags [P.], cksum 0xfb00 (correct), seq 1:109, ack 284, win 237, length 108
11:10:52.693167 IP (tos 0x0, ttl 63, id 14542, offset 0, flags [DF], proto TCP (6), length 910)
192.168.2.10.85 > 192.168.10.2.53697: Flags [P.], cksum 0x0941 (correct), seq 109:979, ack 284, win 237, length 870
11:10:53.048076 IP (tos 0x0, ttl 63, id 14543, offset 0, flags [DF], proto TCP (6), length 1018)
192.168.2.10.85 > 192.168.10.2.53697: Flags [P.], cksum 0xe588 (correct), seq 1:979, ack 284, win 237, length 978
11:10:53.758153 IP (tos 0x0, ttl 63, id 14544, offset 0, flags [DF], proto TCP (6), length 1018)
192.168.2.10.85 > 192.168.10.2.53697: Flags [P.], cksum 0xe588 (correct), seq 1:979, ack 284, win 237, length 978
11:10:55.176161 IP (tos 0x0, ttl 63, id 14545, offset 0, flags [DF], proto TCP (6), length 1018)
192.168.2.10.85 > 192.168.10.2.53697: Flags [P.], cksum 0xe588 (correct), seq 1:979, ack 284, win 237, length 978
11:10:58.016196 IP (tos 0x0, ttl 63, id 14546, offset 0, flags [DF], proto TCP (6), length 1018)
192.168.2.10.85 > 192.168.10.2.53697: Flags [P.], cksum 0xe588 (correct), seq 1:979, ack 284, win 237, length 978 -
@Andy142 said in OpenVPN client can ping but not access server on LAN:
The goal is to isolate the security system on it's own LAN without a gateway
If you want to talk to a system without a gateway from a remote network, then you would need to do a source nat (outbound nat in pfsense on its interface connected to the device)
So for example I talk to this 192.168.0.101 IP from my vpn, and device on that IP has no gateway set..
The outbound (source nat) makes it looks to that device like the traffic came from pfsense IP on that vlan.

sniff via the vpn interface - you can see my remote client from 10.0.200.2 is sending to 192.168.9.101
06:33:39.977012 IP 10.0.200.2 > 192.168.9.101: ICMP echo request, id 13601, seq 0, length 64 06:33:39.977322 IP 192.168.9.101 > 10.0.200.2: ICMP echo reply, id 13601, seq 0, length 64 06:33:40.872795 IP 10.0.200.2 > 192.168.9.101: ICMP echo request, id 13601, seq 1, length 64 06:33:40.873109 IP 192.168.9.101 > 10.0.200.2: ICMP echo reply, id 13601, seq 1, length 64But if I sniff on the lan interface while doing the same ping test, it looks like traffic coming from pfsense lan interface 192.168.9.253
06:37:30.483321 IP 192.168.9.253 > 192.168.9.101: ICMP echo request, id 11550, seq 0, length 64 06:37:30.483568 IP 192.168.9.101 > 192.168.9.253: ICMP echo reply, id 11550, seq 0, length 64 06:37:31.374898 IP 192.168.9.253 > 192.168.9.101: ICMP echo request, id 11550, seq 1, length 64 06:37:31.375172 IP 192.168.9.101 > 192.168.9.253: ICMP echo reply, id 11550, seq 1, length 64 -
I may be off with my terminology so to clarify, the OPT1 network has only the security system on it and I don't want it to have internet access.
I have setup an outbound NAT as you recommended but still no luck unfortunately.

Is the fact I can ping the device but not connect to it significant?
-
Do the simple test I did in my edit above.. Sniffing on openvpn interface I see the vpn client sending traffic
Then on the interface this device is connected to.. see the traffic get natted.
Using some mask of /16 would be saying the both your source and dest are on the same network - which they are not..
If you sniffing on the openvpn and you saw return traffic.. Then you got something else going on to why your not connecting. Pfsense sent the traffic back, which would be impossible really if the client has no gateway.. Unless you created a specific route back to pfsense opt1 interface to get to your vpn network? On that host.
This shows you saw answer back
192.168.10.2.53697 > 192.168.2.10.85: Flags [S], cksum 0xc1b5 (correct), seq 3351086733, win 65535, options [mss 1360,nop,wscale 8,nop,nop,sackOK], length 0 11:10:52.216080 IP (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 52) 192.168.2.10.85 > 192.168.10.2.53697: Flags [S.], cksum 0x6e52 (correct), seq 1476298976, ack 3351086734, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0See the Syn send [S] and then the Syn,Ack back [S.]
-
Okay that makes sense, here are my results:
For OpenVPN interface for host 192.168.10.2 (client)
11:42:52.942806 IP 192.168.10.2 > 192.168.2.10: ICMP echo request, id 1, seq 37, length 40
11:42:52.943393 IP 192.168.2.10 > 192.168.10.2: ICMP echo reply, id 1, seq 37, length 40
11:42:53.875418 IP 192.168.10.2 > 192.168.2.10: ICMP echo request, id 1, seq 38, length 40
11:42:53.876096 IP 192.168.2.10 > 192.168.10.2: ICMP echo reply, id 1, seq 38, length 40For OPT1 interface looking at Host 192.168.2.10 (security system)
11:44:29.215472 IP 192.168.10.2 > 192.168.2.10: ICMP echo request, id 1, seq 41, length 40
11:44:29.216103 IP 192.168.2.10 > 192.168.10.2: ICMP echo reply, id 1, seq 41, length 40
11:44:30.241505 IP 192.168.10.2 > 192.168.2.10: ICMP echo request, id 1, seq 42, length 40
11:44:30.242146 IP 192.168.2.10 > 192.168.10.2: ICMP echo reply, id 1, seq 42, length 40It doesn't look like the NAT is doing anything?
-
No its not..
Btu you show a response.. How would you see a response if the security system has no gateway? 192.168.10 is not on its network 192.168.2/24
Did you set a specific route on the security system for 192.168.10/24?
-
That's what has been throwing me.
There are no static routes or bridges setup. Only thing I have linking them is the "Local Network" of 192.168.2.0/24 in the OpenVPN config.
Here is the interface setup for OPT1.
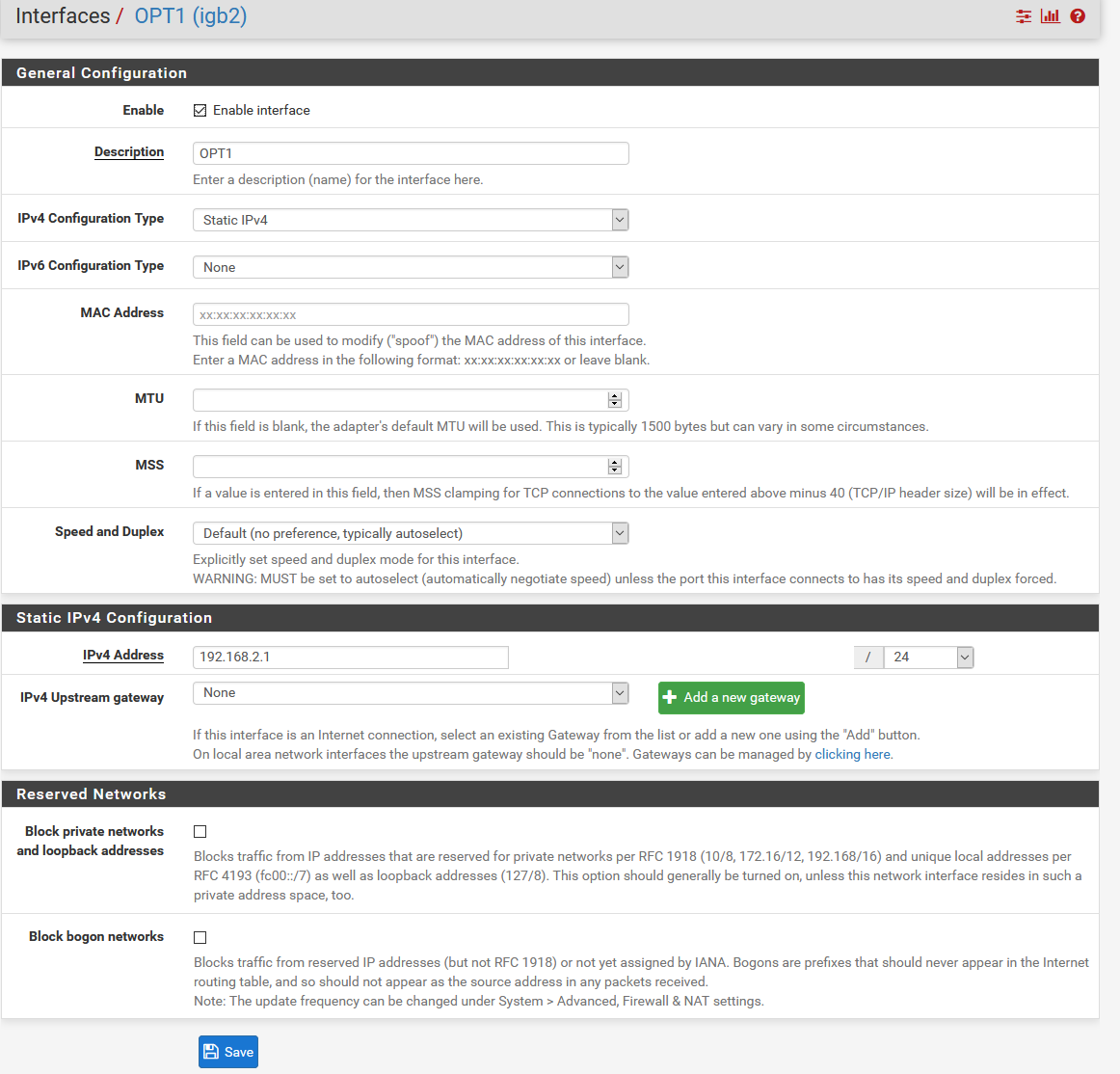
-
@Andy142 , Can I see a screenshot of your Mappings?
Go to Firewall > NAT > Outbound -
Sure thing, here you go.
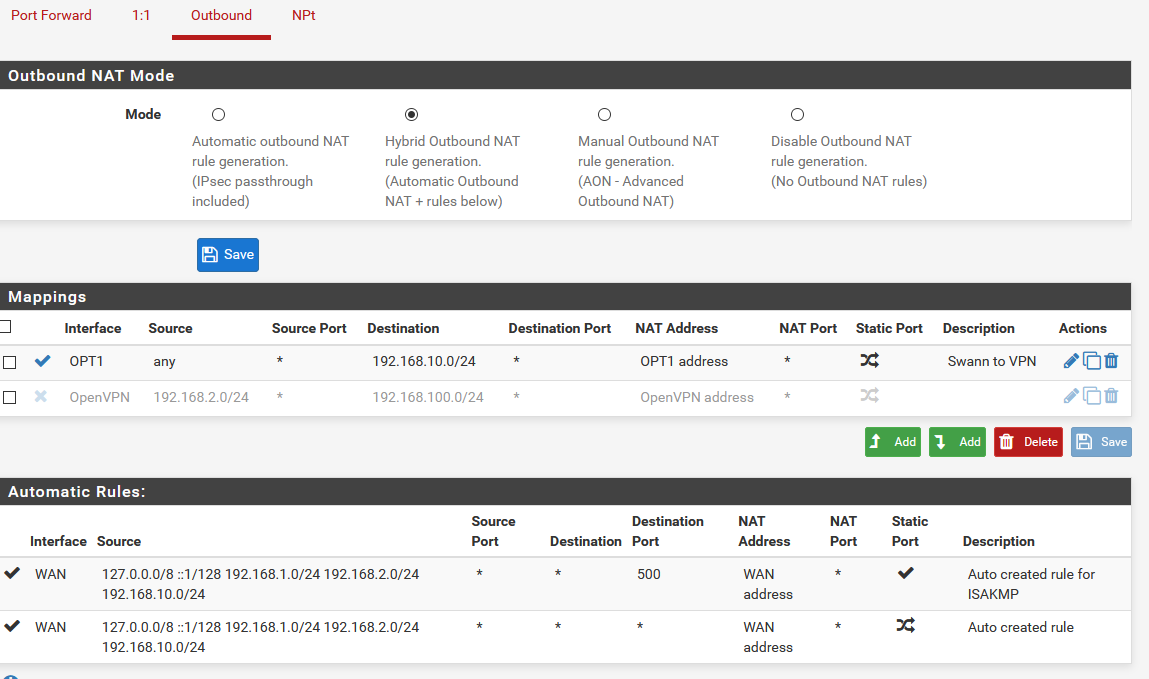
-
@Andy142 , Do you how to make Aliases?
-
@AKEGEC Not really... Sorry
-
Your dest is wrong in that outbound nat.. your vpn client is coming from 192.168.10 right, and he is talking to your security device on 192.168.2.x right?
So your outbound nat dest would be the 192.168.2 network.. not 192.168.10
The point of the outbound nat to talk to a device on a 192.168.2 network that has no gateway on the device, is to make the traffic look like its coming from its own network 192.168.2..
The destination is the opt1 network.. 192.168.2
client 192.168.10.2 --- vpn ---192.168.10.1 (pfsense) 192.168.2.1 --- 192.168.2.x
So you want to nat this 192.168.10 traffic to look like it came from 192.168.2.1, so 2.x knows how to talk back to it without a gateway..
-
Go to Firewall > Aliases > +Add
Name: Private OPT1 or bla bla bla
Type: Network(s)
Network or FQDN: 192.168.10.2-192.168.10.254
If your OPT1 IP interface is 192.168.10.1, you must excluded your OPT1 interface ip address.
Press Add Network button -
I regijied the outbound, here are the results
On the OpenVPN Interface
12:40:36.930315 IP 192.168.10.2 > 192.168.2.10: ICMP echo request, id 1, seq 69, length 40
12:40:36.931039 IP 192.168.2.10 > 192.168.10.2: ICMP echo reply, id 1, seq 69, length 40The OPT1 interface
12:42:01.418506 IP 192.168.2.1 > 192.168.2.10: ICMP echo request, id 50048, seq 73, length 40
12:42:01.419125 IP 192.168.2.10 > 192.168.2.1: ICMP echo reply, id 50048, seq 73, length 40Looks like it's replying to the default gateway now at least.
-
Yup that looks good..
You should be able to talk to that device now on anything not just icmp
To that device any traffic coming from your vpn will just look like its coming from pfsense 2.1, which is on its own network and it can talk to.
This should also circumvent any device firewalls that would prevent talking to some service from a different network.
-
@AKEGEC What do I put in the second box that comes up after pressing "Add network"? Or did you mean "save"?
-
Have no idea why he wants you to create an alias, there is no need for one in such a setup.
-
@johnpoz Still not getting a response from the security system....
-
Well do you sniff test again.. Do you see traffic going to your security system looking like its coming from 2.1, do you see a response - does the response go back to yoru vpn client?
If you see traffic going back over the vpn to your vpn client - its not a pfsense issue.