help with forwarding for home assistant
-
Maybe use IPSEC or OPENVPN instead of exposing your server directly to the WAN.
-
@wgstarks said in help with forwarding for home assistant:
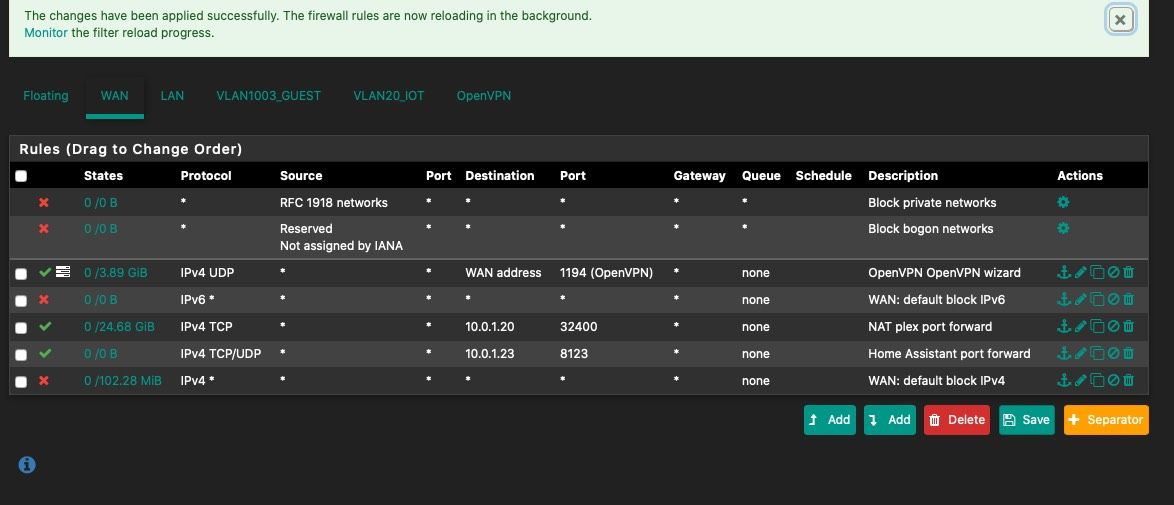
Like this?
Yes, using pfSense for DNS resolution presumed. So can access the home assistant with the same host name from within your network as well as from outside.
However, security concerns are not regarded with this recommendation. -
Is there really a security concern? I'm asking this as a legitimate question. I only have a basic layman's knowledge regarding network security but I have a very strong password set for HA and would think that it would be adequate. Maybe that's not true?
-
@tman904 said in help with forwarding for home assistant:
Maybe use IPSEC or OPENVPN instead of exposing your server directly to the WAN.
I have OpenVPN setup on my iPhone but at the time I set it up I couldn't find a way to keep it active. Maybe that has changed now (it's been a few years)?
-
Why do you think you even need to open the port? There should be zero reason for opening inbound ports to control your home smart things while outside your home.. They phone home (company servers) and you control via that connection.
I can turn on/off my lights, change the temp on the hvac, etc. without having any ports open.
If your using some home grown thing - that you need to talk to while remote, then yes vpn would be the secure way to do that.. Not opening it up to the whole internet..
-
@johnpoz said in help with forwarding for home assistant:
Why do you think you even need to open the port? There should be zero reason for opening inbound ports to control your home smart things while outside your home.. They phone home (company servers) and you control via that connection.
I can turn on/off my lights, change the temp on the hvac, etc. without having any ports open.
My iOS app fails to connect without a connection to my local network.
-
You are using this?
https://www.home-assistant.io/ -
@wgstarks said in help with forwarding for home assistant:
@johnpoz said in help with forwarding for home assistant:
Why do you think you even need to open the port? There should be zero reason for opening inbound ports to control your home smart things while outside your home.. They phone home (company servers) and you control via that connection.
I can turn on/off my lights, change the temp on the hvac, etc. without having any ports open.
My iOS app fails to connect without a connection to my local network.
Yes
-
Yeah you would want vpn then... If they server doesn't make a connection to outside services, like alexa, google, all the other 3rd brand lights and switches, and etc.. That you can use to control your devices. VPN is the way to do it securely.
https://www.home-assistant.io/docs/configuration/remote/
"Just putting a port up is not secure. "They recommend using ssl - but that still leaves it exposed.. From a security point of view you should setup vpn on your phone to your pfsense box.. Then you can access your remote assistant through the vpn.. This does not expose it to the public internet and anyone hitting that port.
-
@johnpoz said in help with forwarding for home assistant:
Yeah you would want vpn then... If they server doesn't make a connection to outside services, like alexa, google, all the other 3rd brand lights and switches, and etc.. That you can use to control your devices. VPN is the way to do it securely.
They do have a paid service for this but I would rather connect manually (turn the vpn on/off) and save the money if I can't find anyway to keep the vpn active.
-
Well the vpn could be set to always be active.. But turning on and off is just a single click.. On your phone
-
@johnpoz said in help with forwarding for home assistant:
They recommend using ssl - but that still leaves it exposed.. From a security point of view you should setup vpn on your phone to your pfsense box.. Then you can access your remote assistant through the vpn.. This does not expose it to the public internet and anyone hitting that port.
Right now I have ssl (lets encrypt). I have OpenVPN installed on my iPhone but it tends to disconnect when changing networks and won't connect at all when I'm connected to my local network. I see that the OpenVPN app now has functionality to try and re-connect but I'm not sure what those continuous re-connection attempts will do to my battery life and network performance.
-
You don't need it while your on your local network... Just turn it on when your away "and" you want to do something with your home assistant. Its a click to turn it on.
Do what it is you want to do and then disconnect it - click.
I would not suggest you open your home assistant to the public net - it is not secure be it your using https or not..
Here is some info about how often this port is scanned..
https://www.dshield.org/port.html?port=8123
https://www.speedguide.net/port.php?port=8123 -
Can you do what you want with homebridge?
https://homebridge.io/
I can control devices when i’m away from home with out any sort of port forwarding, i run it on a Raspberry Pi 3 and it talks to my Apple TV homekit hub.
-
^ exactly.. There really should be no reason to port forward for home automation sort stuff.. Not sure exactly how OP is setup and what gear..
If you have to open a port to public internet - its not a secure..
-
@NogBadTheBad said in help with forwarding for home assistant:
Can you do what you want with homebridge?
https://homebridge.io/
I can control devices when i’m away from home with out any sort of port forwarding, i run it on a Raspberry Pi 3 and it talks to my Apple TV homekit hub.
For some reason HomeKit doesn’t show any of my insteon sensors. Only the switches. Regardless, I really don’t want to go through the headache of re-creating all of my automations again.
-
The home assistant iOS app relies on anytime access to the server on my local network for some of its services. I’m going to try the OpenVPN option and see how well that works.
-
Let us know how it goes for you.
-
So even their website recommends vpn or ssh (poor mans vpn) ;)
https://www.home-assistant.io/docs/configuration/securing/
"To expose your instance to the internet, use a VPN, or an SSH tunnel."While sure https is more secure than http.. Your still just exposing the service to the public which is bad. A vpn or ssh provides for a secure method to auth to even make an a connection, before exposing the service interface to anyone.
VPN or even ssh can require very secure auth methods, and then keeping all traffic passed between the authed user and the service secure inside an encrypted tunnel.
If my user base was more tech savy, I would require all my friends and family to use vpn to access my plex. Sadly that is not possible - so had to make compromises to a secure setup to allow them to use in a easy fashion. I tried locking it down to only their known IPs - but this proved to be too difficult for many of them. So best I could do was lock down the ips to only the locations they are coming from. Currently the US. Changing the port from the common port. And actively monitoring any access. Any time a new IP access my plex I am notified, and can check with that account - hey are you traveling why am I seeing a connection from different state than your normally from..
But since something like home control/automation remote access should really only be accessed by you, or maybe a house mate or too.. Locking that down to vpn access is a very viable solution. And simple enough to setup via just app on any phone, tablet, laptop - remote access devices. Not like you need a TV to access home assistant server.
From a security point of view I can not stress enough the importance of not allowing such access to just any public IP..
With something like plex, at least the worse thing that could happen is someone deleted all my media. But even if they compromised that system. They would be limited to that service, and not have any access to anything else in my network.
-
I suppose exposing an encrypted service to the Internet is better than just using a plain HTTP/HTTPS server though. I think the most important factor is if this server will be kept updated/patched and monitored. That all depends on if the vendor ever pushes out any updates though.
They always do that right.
 lol
lol