Openvpn missing option inside config.ovpn
-
I have upgraded to the latest snapshot and I saw my OpenVPN was not connecting anymore
Version 2.5.0-DEVELOPMENT (amd64) built on Sun Nov 08 13:03:56 EST 2020 FreeBSD 12.2-STABLElog was full of
Nov 9 11:10:47 openvpn 2904 Authenticate/Decrypt packet error: cipher final failed Nov 9 11:10:47 openvpn 2904 Authenticate/Decrypt packet error: cipher final failed Nov 9 11:10:36 openvpn 2904 Authenticate/Decrypt packet error: cipher final failed Nov 9 11:10:36 openvpn 2904 Authenticate/Decrypt packet error: cipher final failed Nov 9 11:10:26 openvpn 2904 Authenticate/Decrypt packet error: cipher final failed Nov 9 11:10:26 openvpn 2904 Authenticate/Decrypt packet error: cipher final failedfurther investigation lead to the OpenVPN server config missing -> cipher AES-256-CBC
I have added it to the custom option for nowhttps://redmine.pfsense.org/issues/11046
openvpn server on 2.5.0
openvpn client on 2.4.5-p1peer to peer shared key tls
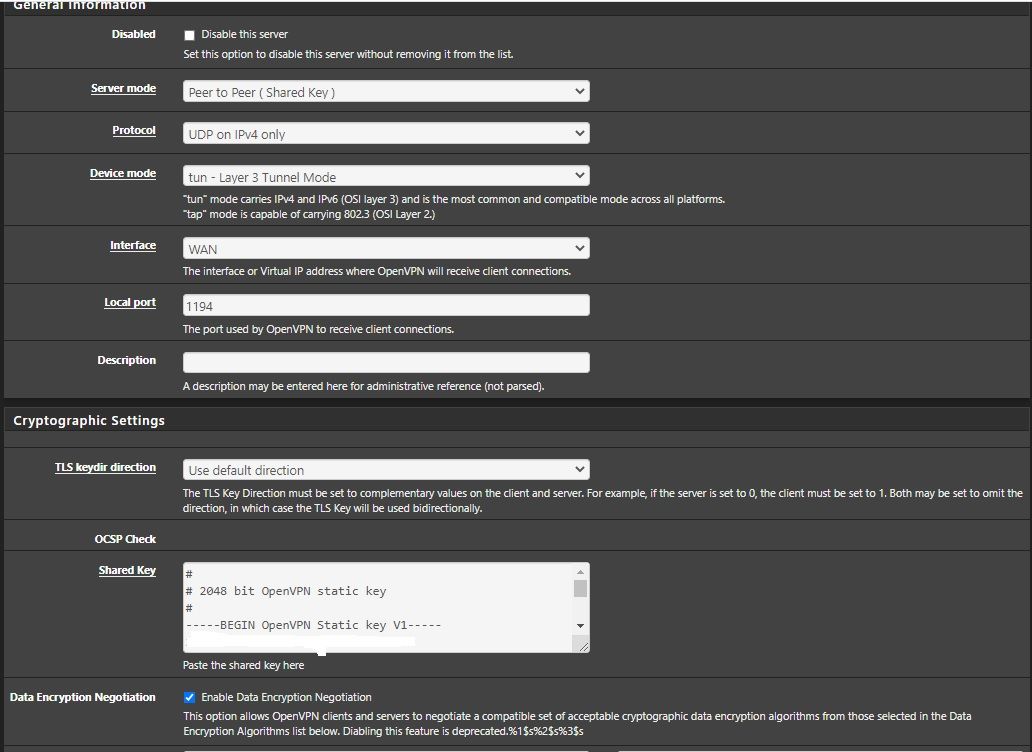
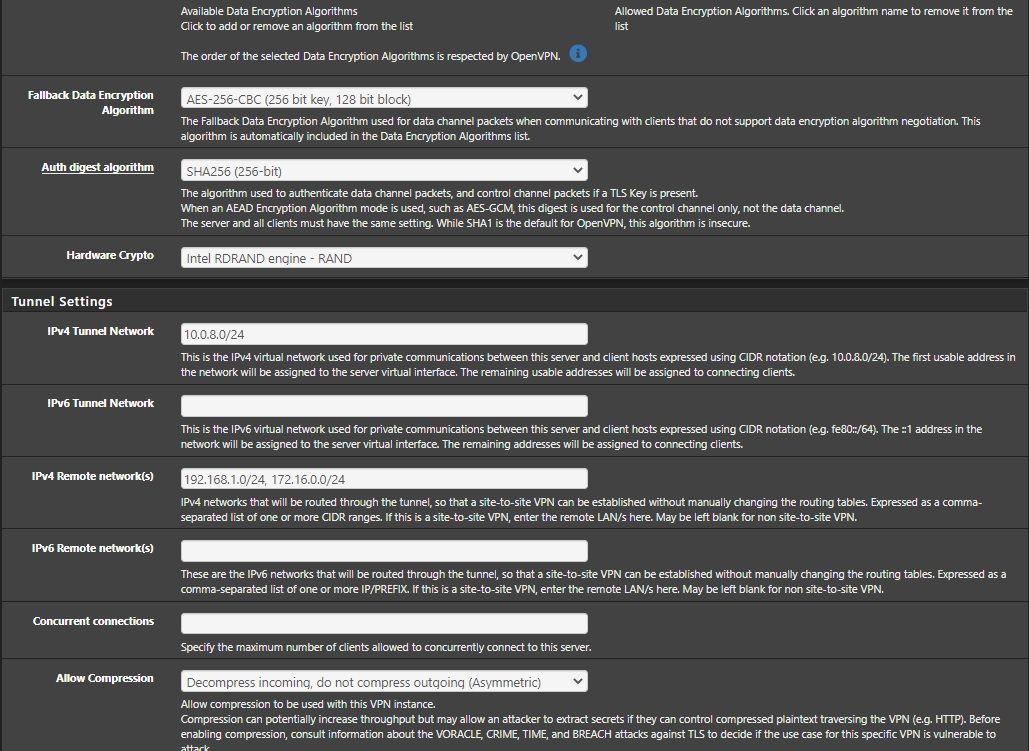
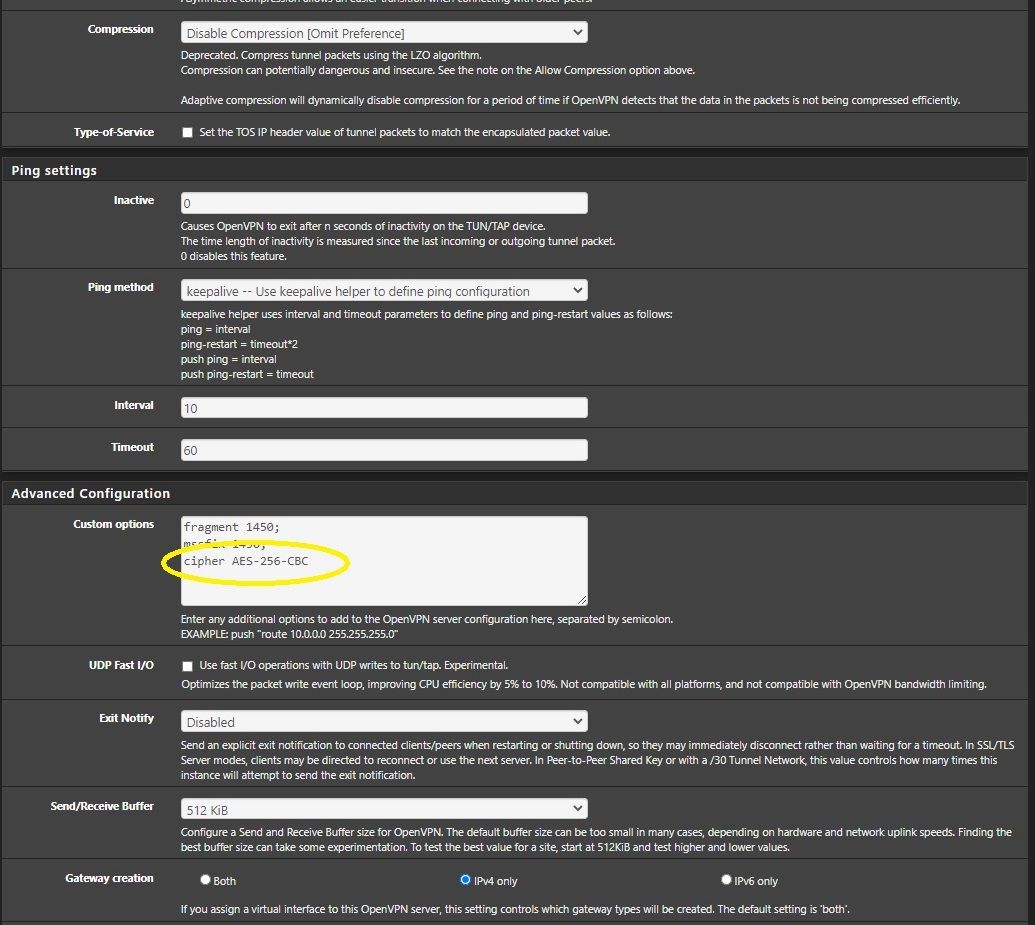
this is from the server, algorithms are the same for the client on 2.4.5-p1
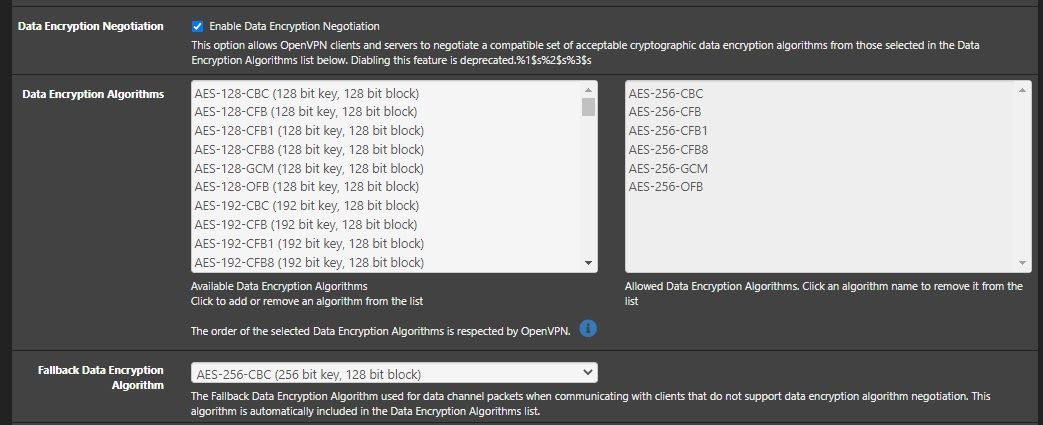
-
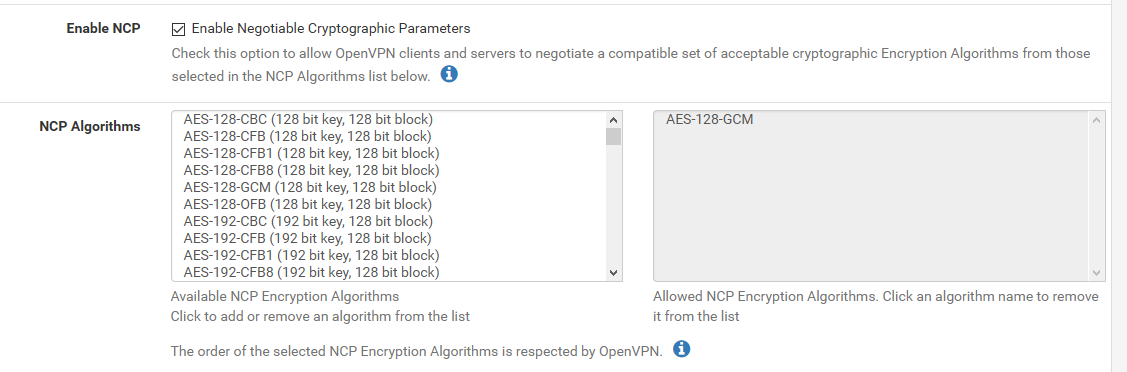
You have enable negotiation set.. Did you snip out where you select which ones are enabled to be selected?
-
i was still uploading img

-
Im talking about the server - that section whre you select the algo is missing?
-
the screenshot are all from the server,
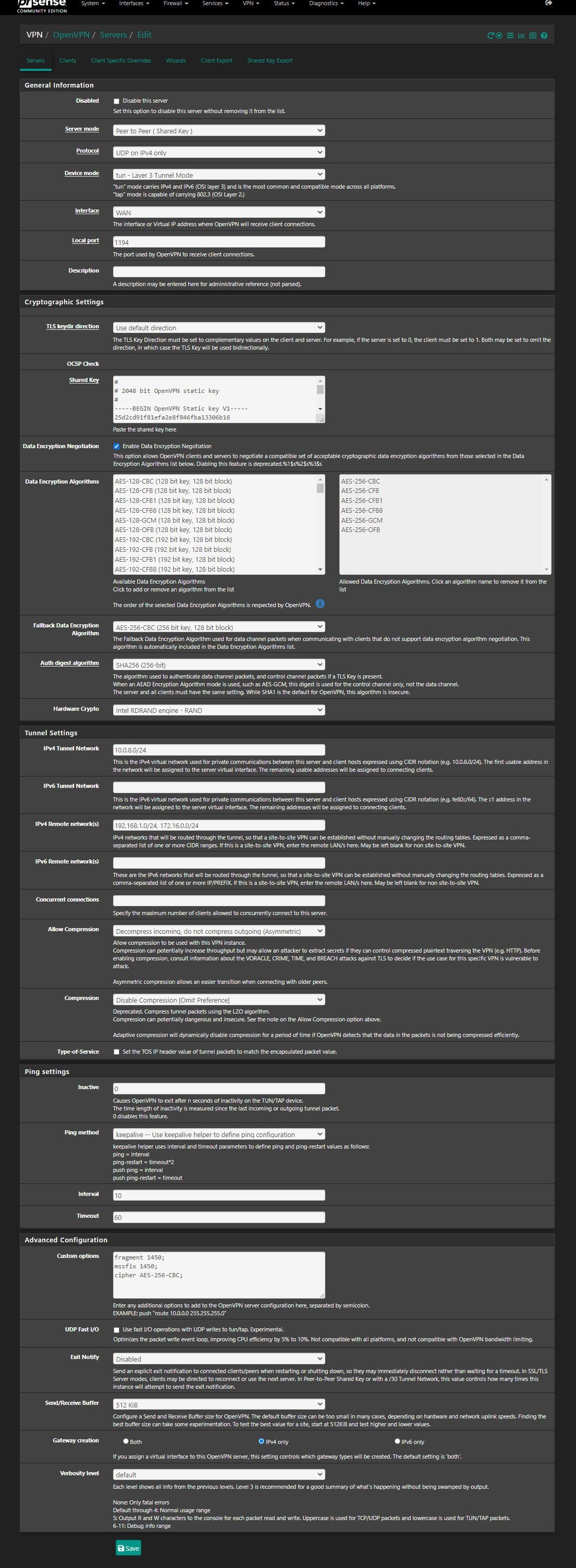
the resulting config file is as follow[2.5.0-DEVELOPMENT][root@pfSense.kiokoman.home]/etc/inc: cat /var/etc/openvpn/server1/config.ovpn dev ovpns1 verb 1 dev-type tun dev-node /dev/tun1 writepid /var/run/openvpn_server1.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown local xxx.xxx.xxx.xxx engine rdrand ifconfig 10.0.8.1 10.0.8.2 lport 1194 management /var/etc/openvpn/server1/sock unix route 192.168.1.0 255.255.255.0 route 172.16.0.0 255.255.255.0 secret /var/etc/openvpn/server1/secret allow-compression asym sndbuf 524288 rcvbuf 524288 fragment 1450 mssfix 1450 cipher AES-256-CBCcheck the latest screenshot i have added after you wrote
-
Where in your config is your ncp ciphers?
ncp-ciphers AES-128-GCM:AES-192-GCM:AES-256-GCM:AES-128-CBC:AES-192-CBC:AES-256-CBC -
@johnpoz
that's the point
-
So your saying that option is missing to set in the gui in 2.5?
Oh your drawing all snipped up - I use faststone which has an autoscroller for taking long screens.
-
it is available in the GUI but not saved inside the config
-
I get ya now - hmmm... I don't currently have 2.5 to fire up..
For clarity besides saying lastest, you should always list the exact version your using even if saying latest.. That goes for anything firmware, software, etc.. You might want to add that.. Lets see if I can fire up a 2.5 snap to test with.
-
@kiokoman said in Openvpn missing option inside config.ovpn:
Version 2.5.0-DEVELOPMENT (amd64)
built on Sun Nov 08 13:03:56 EST 2020
FreeBSD 12.2-STABLEfaststone:

-
There you go, much better ;) just 1 picture. heheh
I looked I had purged the 2.5 vm I was playing with - have to reset it up to try and duplicate..
-
Ok - VM is up, I can try and duplicate.. But your not on the "latest"
Nov 9 build is out..
-
-
Ok - your setup as shared key.. So yeah ncp would be disabled anyway.
Do you really have a shared key setup? That was working before.. I can fire up another 2.5 vm..
-
Maybe it's an update to OpenVPN 2.5? I checked the changelog/release log a while ago and there were quite a few changes to NCP etc.?
-
Well having a bit of problem setting up my lab..
Tried to add some vlans to my 2 vms, so could route those networks over the shared key vpn.. And both are crashing with this..
-
it was working without any problem before the upgrade to the latest snapshot

Already being worked on: #10919
https://redmine.pfsense.org/issues/10919 -
Yep, as I thought, that's one of the new 2.5-series changes to handling ciphers and now "defaulting" to use ciphers alternative/additional to ncp-ciphers (that are to be renamed) etc. I saw quite a few small changes to config files that way. And I'm still not sure why the hell I should provide multiple ciphers via NCP or with ciphers: (now), if I control the server and roll out the clients. Just define a good working set like AES-256-GCM, SHA256, ECDH only with secp384r1 and be done with it. Bit annoying but once the UI will deal with it - not that much of my problem anymore. ;)
-
This should be all good now. It'll be in snapshots later today, or you can gitsync from a snapshot with the problem to pick up the fix.
It primarily affected shared key instances. When I was testing on Friday before I committed the changes that broke it, I was primarily focused on SSL/TLS configurations and didn't spot that shared key would have ended up with nothing.
Though also from the looks of it, the Data Ciphers (formerly known as NCP ciphers) may not have been working with shared key even before this.
But it should be all good now on 2.5.0.
