Appear to have two interfaces listed under firewall rules when I only have 1 openvpn configured?
-
Morning all
I think I might have an issue with my firewall and hoped you could give me some advice please?
Under firewall > Rules I appear to have 2 openvpn interfaces listed however I only have 1 openvpn instance configured and wonder if someone could help me either remove the wrong entry or advise on why I see this please?
I have attached the screen shot to show the above.
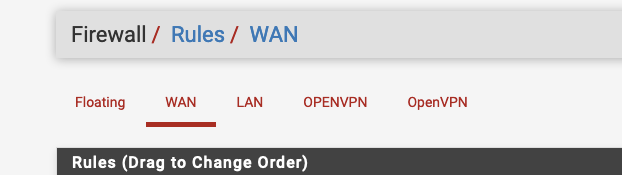
Thank you for your help with this.
Cheers
Andy
-
"OpenVPN" is an interface group covering all OpenVPN instances you're running. The tab is added by pfSense automatically as soon as you set up your first OpenVPN instance, either a server or a client.
The "OPENVPN" interface may have been assigned by yourself, I assume.
It's even not a good idea to give it such a universal name. -
AFAIK the pfSense generated interface has precedence on all OpenVPN instances.
Do not put any rules there (unless you know what you are doing) , if you want to use the "Own asigned" interfaces.
/Bingo
-
@bingo600 said in Appear to have two interfaces listed under firewall rules when I only have 1 openvpn configured?:
AFAIK the pfSense generated interface has precedence on all OpenVPN instances.
Yeah, as I said, it's an implicit interface group and rules on interface groups have generelly precedence over rules on interface tabs: https://pfsense-docs.readthedocs.io/en/latest/firewall/firewall-rule-processing-order.html
-
-
Hi
Thank you for your quick replies - Im new to pfsense hence my lack of understanding. Im really sorry but Im still confused. How do I get rid of the one I shouldnt have there?
-
If it helps there are no interfaces assigned under interface groups??
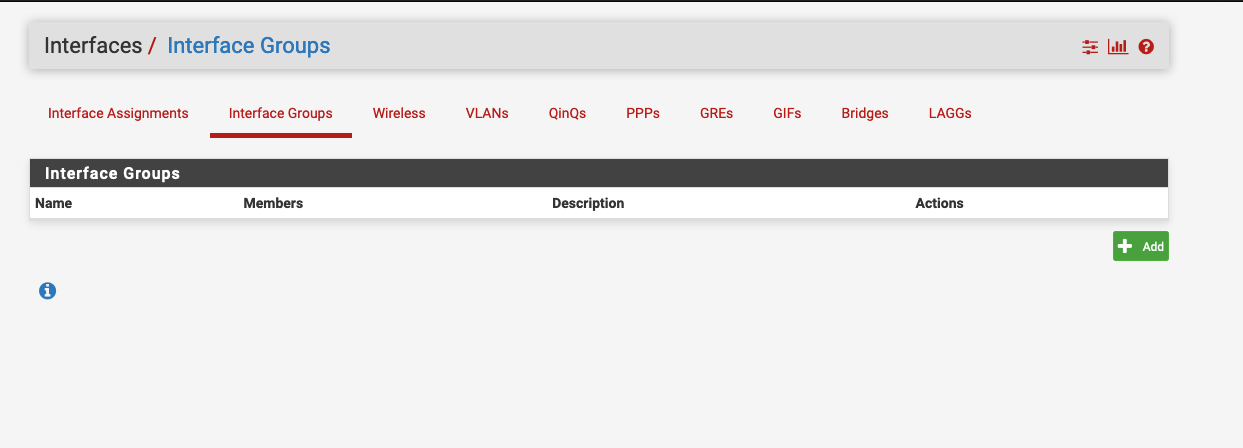
-
Easy - you leave the pfSense generated OpenVPN interface untouched.
And you rename your own named: OPENVPN interface, to something that does not resemble the pfSense generated interface-group name (that you can't get rid of)/Bingo
-
I have openvpn confirued as a client btw connecting out - I have no local Openvpn servers running on pfsense
-
@andrewglass3
Now, have you assigned "OPENVPN" manually?
There are situations where an explicit interface for on OpenVPN instance is needed.The interface group "OpenVPN" is implicitly added by pfSense, as mentioned above, and cannot be removed.
-
@andrewglass3 said in Appear to have two interfaces listed under firewall rules when I only have 1 openvpn configured?:
I have openvpn confirued as a client btw connecting out - I have no local Openvpn servers running on pfsense
If you do policy routing, you will need the manually assigned interface. If you want to route the whole upstream traffic over the VPN it's not needed.
-
@viragomann said in Appear to have two interfaces listed under firewall rules when I only have 1 openvpn configured?:
There are situations where an explicit interface for on OpenVPN instance is needed.
I'm always using explicit interfaces, both on L2L and RoadWarrior
I think it makes it easier to do specific rules for the setup./Bingo
-
So under Status/Interfaces I can see this:
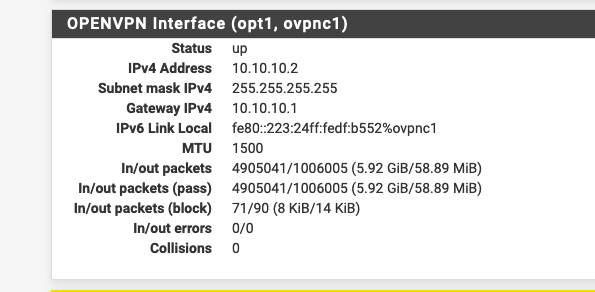
Under Interfaces / Interface Assignments I see this:
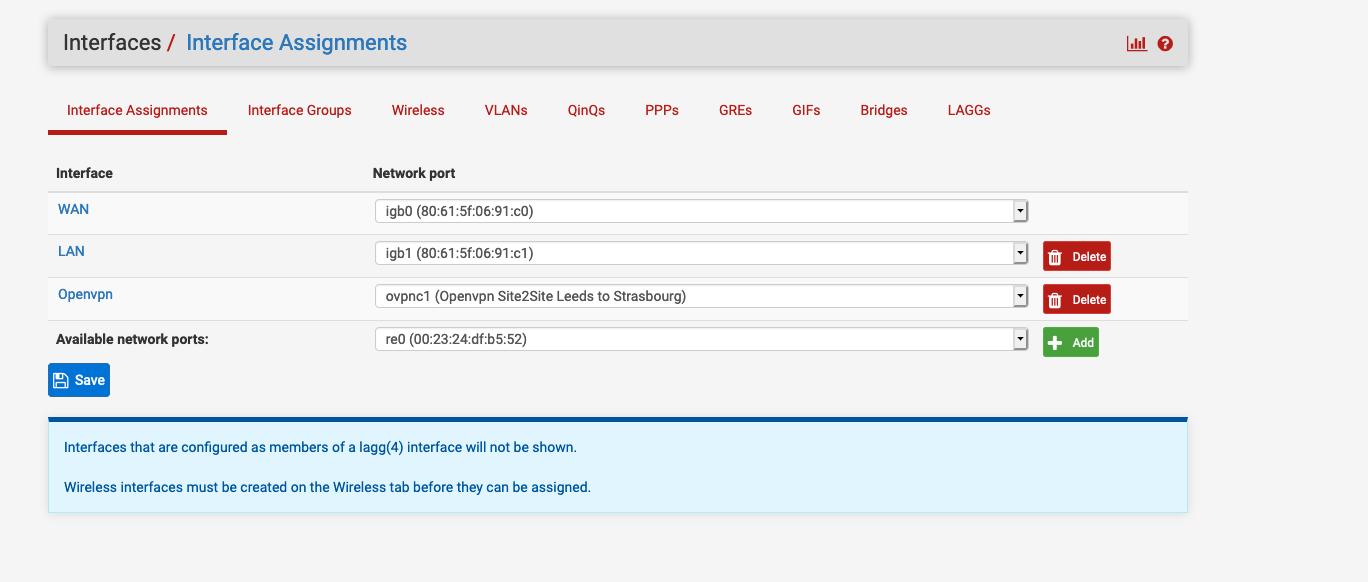
If I click on the Openvpn name on the list to the left of the drop down boxes I see this:
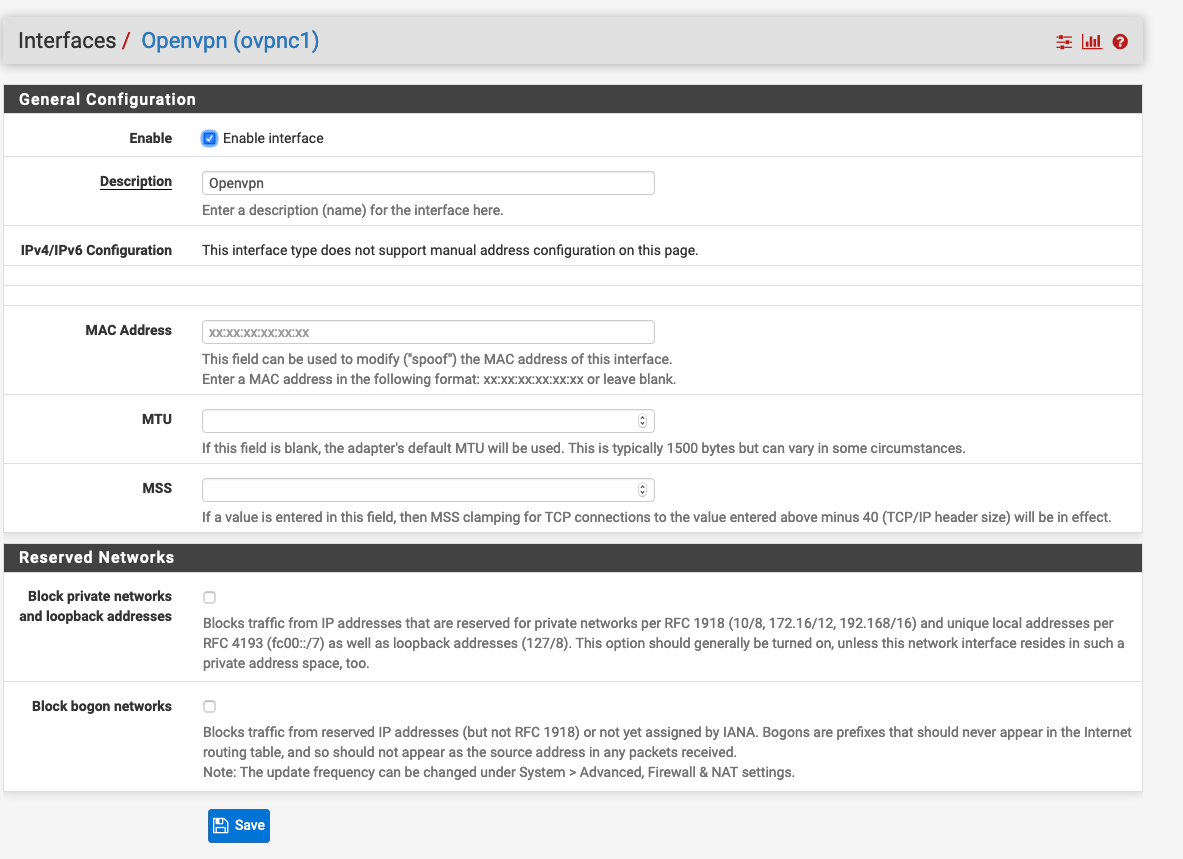
Are you saying that pfsense will implicitly name an interface tab under firewall rules as seen here in the VPN section as a general interface firewall tab for all listed clients under it?
I wonder if that other one, OPENVPN is from another vpn tunnel that I connected to try and outbound nat specific vlan traffic down it. but then deleted as my system went very slow and laggy..hmm
Sorry for the ramblings - like I say this is new to me - very different to my edgerouter 4 Ive moved over from.
Cheers
Andy
-
@andrewglass3 said in Appear to have two interfaces listed under firewall rules when I only have 1 openvpn configured?:
I wonder if that other one,
No. On the firewall rule page all interfaces are shown in upper case, while the OpenVPN interface group is in upper / lower case.
It's recommended to change the name of the OPENVPN, you have assigned manually, to avoid confusion.
-
@viragomann Thanks for your help - Where would i do that? Under what section?
-
When I click on the dropdown for interfaces at the top I see this:
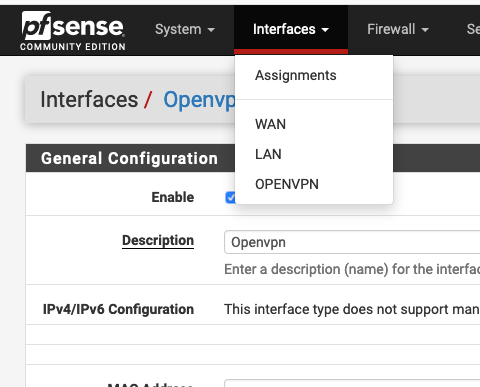
When I click on the uppercase OPENVPN in that said dropdown I see this:
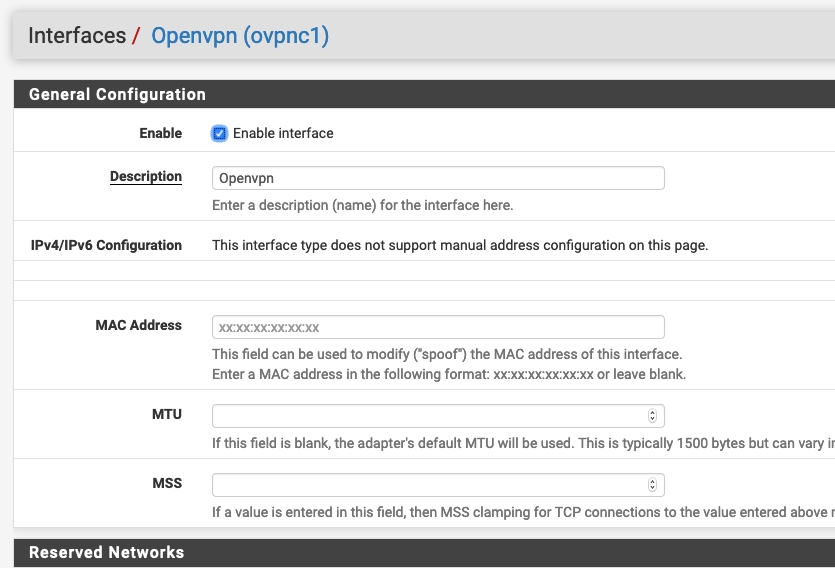
Confused lol
-
Ah got it :)
-
So what confuses me then is you can name the interface that relates to the ovpnc1 adaptor. Is this really needed as it doesnt show in any interface groups. Or would you only assign ovpnc1 to an interface name if you wanted to do policy based routing and outbound NAT?
-
@andrewglass3 said in Appear to have two interfaces listed under firewall rules when I only have 1 openvpn configured?:
So what confuses me then is you can name the interface that relates to the ovpnc1 adaptor. Is this really needed as it doesnt show in any interface groups.
The ovpnc1 is ever a part of the OpenVPN group, even if it's not displayed.
Assigning interfaces to OpenVPN instances is primarily needed for policy routing and for special routing back of response packets to a specific OpenVPN gateway (reply-to).
In your case you will have to add an outbound NAT rule for the OpenVPN instance, however, this will also work by using the OpenVPN interface group. But you have to consider that this rule bear on all OpenVPN instances after.
-
@viragomann said in Appear to have two interfaces listed under firewall rules when I only have 1 openvpn configured?:
So what confuses me then is you can name the interface that relates to the ovpnc1 adaptor. Is this really needed as it doesnt show in any interface groups.
Because it is NOT a manually added interface group but an automatically generated Group Tab - same as if you create an IPSec tunnel or dial-in connection, a IPSec Tab will show up that is an interface group over all IPSec connections you have.
You can manually add interfaces to interface groups -> those will show up as separate tabs with the defined name as well - and will be listed under interface groups as you manually added them. "IPsec" and "OpenVPN" (watch the upper/lowercase) are automatically created interface groups that will pop into existence as soon as one interface of their type is in created and in use. :)
For all other details check out the link @viragomann gave you and read up on interface groups and handling :)