MS activated DoH at the operating system level, in this "great" 20H2 release...?!
-
Just for the sake of the test we installed the new Win10 release (20H2 clean install) and ...
The pfBlockerNG is currently unable to do anything at this point...! and / or :-) ?
a blocked target on a Win10 1909 machine, for example (msftncsi.com or o.ss2.us):
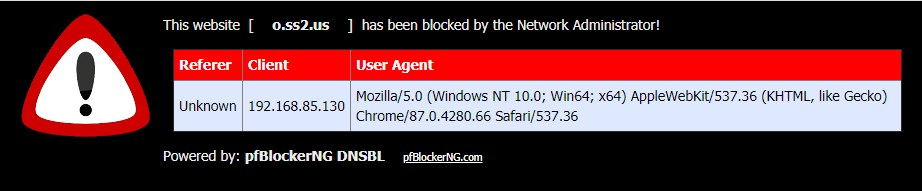
or

the same on a 20H2 windows machine:
or
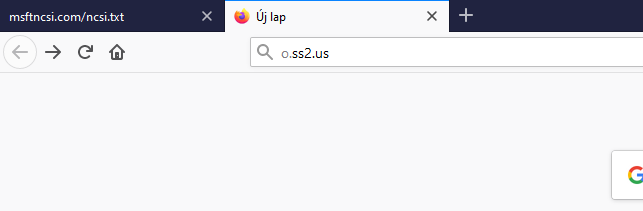
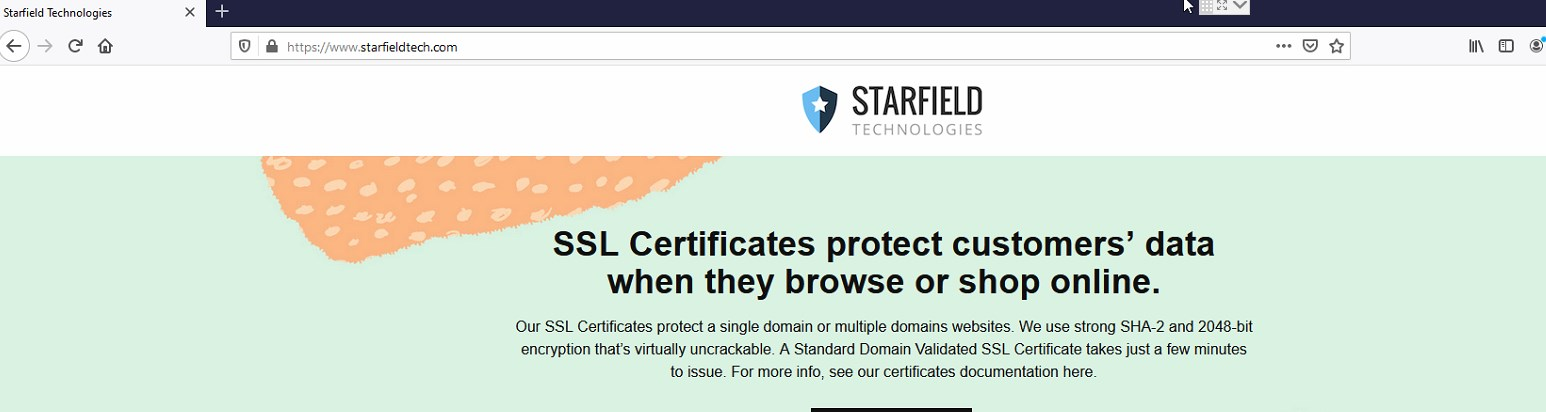
o.ss2.us = redirect to https://www.starfieldtech.com/

the network settings are exactly the same on the two computers (except IPs RFC1918, :-)):
PC config via DHCP - pfSense DNS - pfBlockerNG
one more fact:
msftconnecttest.com, bypass pfBlockerNG here: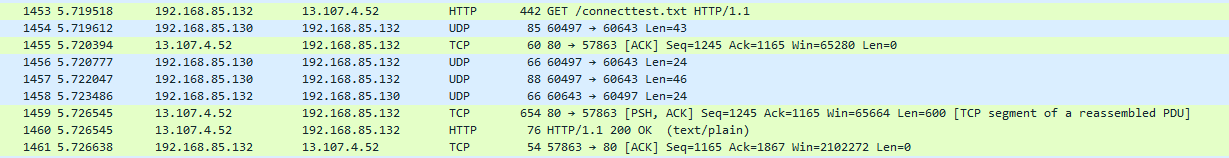


-
Where did they do this at the OS level.. Your testing in a browser - browsers like to enable doh sure... But I don't recall any mention of doh being enabled at the os level?
I'm running 20h2
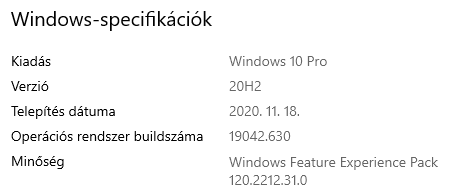
Microsoft Windows [Version 10.0.19042.630]And OS is still using my local dns..
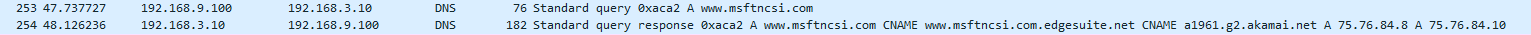
I flushed my local dns.. ipconfig /flushdns - and then dig a simple ping
ping www.msftncsi.com Pinging a1961.g2.akamai.net [75.76.84.8] with 32 bytes of data: Reply from 75.76.84.8: bytes=32 time=20ms TTL=54 Reply from 75.76.84.8: bytes=32 time=19ms TTL=54You can see from sniff it asked my local dns
-
@johnpoz said in MS activated DoH at the operating system level, in this "great" 20H2 release...?!:
Where did they do this at the OS level.
https://www.windowslatest.com/2020/05/14/windows-10-is-getting-dns-over-https-doh-support/
and
there is only one bare Firefox on the test machine, with this:
about:config
network.trr.mode 5+++edit:
BTW:
this is a couple of hours of a really fresh installation with an image downloaded from our MS VLSCnot constantly updated, starting from 1909, for example
-
For it to work on the OS you would have to point to specific doh dns..
While you can enable it - from here for example
https://lifehacker.com/how-to-turn-on-dns-over-https-for-all-apps-in-windows-1-1843544589Where did they state it would be the default configuration?? See my edit above where I did a simple ping so the OS would resolve and where it got its answer from, etc. via sniff on the box.
edit: Also from my understanding the reg entry would have to be there.

-
@johnpoz said in MS activated DoH at the operating system level, in this "great" 20H2 release...?!:
edit: Also from my understanding the reg entry would have to be there.
I know this post....no entry I have already checked
 - already as I meant "2"
- already as I meant "2"but:
I understand that, but did you see Wireshark?
MS connecttest is disabled everywhere on the network, but on this one machine, pfBlockerNG is bypassed
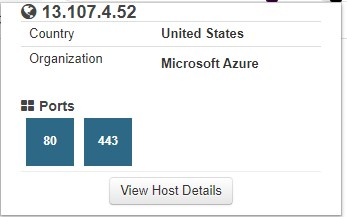
(since connecttest runs on an external web server of its own)in addition, it uses a new MS IP (for me new): 13.107.4.52 - instead of this 131.107.255.255
where does it get DNS from?++edit:
and
-
Well that IP reports back with a footprintdns name - So I would assume its some tracking IP for something..
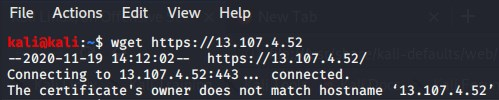
wget https://13.107.4.52 --2020-11-19 12:12:43-- https://13.107.4.52/ Connecting to 13.107.4.52:443... connected. ERROR: certificate common name ‘*.clo.footprintdns.com’ doesn't match requested host name ‘13.107.4.52’.If you hit it up using a name that matches you get back some sort of canary something?
root@NewUC:/home/user# cat index.html <?xml version="1.0" encoding="utf-8"?> <canaryresponse xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" currenttime="2020-11-19T18:13:35.6198632Z"> <instanceset> <instance isresponder="true"> <datacenter>fra</datacenter> <cluster>fra21prdapp03</cluster> <canary>fra21prdapp03-canary</canary> <canaryservicetype>IPv6</canaryservicetype> <fd>0</fd> <ud>0</ud> <instanceid>b5d731fa4a1d487b9c36124ac47d3ae1</instanceid> <dip>10.0.0.83</dip> <canaryversion>1.0.5.751</canaryversion> </instance> </instanceset>I can tell you one thing - the day windows defaults to doh, will be the day I wipe my windows machine and go pure linux..
-
@johnpoz said in MS activated DoH at the operating system level, in this "great" 20H2 release...?!:
If you hit it up using a name that matches you get back some sort of canary something?
Nope..
The WS *.pcap basically shows port 80, hmmmm
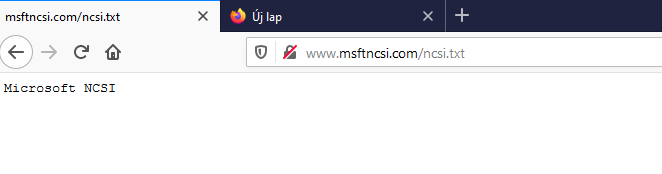
the way it works http - http://www.msftconnecttest.com/connecttest.txt
or
http://www.msftncsi.com/ncsi.txttherefore I am completely lost...it can be inside in advance...
but as you can see it downloads the connecttest.txt file
200 OKand pfBlockerNG is bypassed!
13.107.4.52...- <h2>Our services aren't available right now</h2><p>We're working to restore all services as soon as possible. Please check back soon.</p>08Lu2XwAAAADuj8s0xzLNRqgGp76wBEbWTElTMDFFREdFMDMxNQBFZGdl
@johnpoz "I can tell you one thing - the day windows defaults to doh, will be the day I wipe my windows machine and go pure linux.."
I’m already half on Linux, precisely because of such bullshit :)
++edit:
https://www.shodan.io/host/13.107.4.52
-
@DaddyGo said in MS activated DoH at the operating system level, in this "great" 20H2 release...?!:
it uses a new MS IP (for me new): 13.107.4.52 - instead of this 131.107.255.255
where does it get DNS from?Well that's the one I get:
dig www.msftconnecttest.com @8.8.4.4; <<>> DiG 9.16.5 <<>> www.msftconnecttest.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 34855
;; flags: qr rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 1;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;www.msftconnecttest.com. IN A;; ANSWER SECTION:
www.msftconnecttest.com. 3542 IN CNAME v4ncsi.msedge.net.
v4ncsi.msedge.net. 18 IN CNAME ncsi.4-c-0003.c-msedge.net.
ncsi.4-c-0003.c-msedge.net. 10 IN CNAME 4-c-0003.c-msedge.net.
4-c-0003.c-msedge.net. 56 IN A 13.107.4.52 -
you can try to use DoH feeds in pfBlockerNG,
see https://redmine.pfsense.org/issues/10969also https://raw.githubusercontent.com/oneoffdallas/dohservers/master/list.txt
and (all public DNS servers):
https://public-dns.info/nameservers.txt -
@viktor_g said in MS activated DoH at the operating system level, in this "great" 20H2 release...?!:
you can try to use DoH feeds in pfBlockerNG,
thanks for the advice, but we’ve been past that for a long time

https://forum.netgate.com/topic/157500/blocking-dns-over-https-seems-the-only-way-is-to-fire-a-shotgun-at-it/30
https://public-dns.info/nameservers.txt
https://raw.githubusercontent.com/Sekhan/TheGreatWall/master/TheGreatWall_ipv4or but it has not been available for some time....
https://heuristicsecurity.com/dohservers.txtUNBOUND Custom:
server:
local-zone: "use-application-dns.net" always_nxdomain
local-zone: "cloudflare-dns.com" static+++edit:
it is a long-established system, only a certain test PC has this condition, which is win10 20H2
+++edit:
yesterday, I downloaded (fresh - crunchy
 ) this "image" from our own MS VLSC account...
) this "image" from our own MS VLSC account...true this is an account which is attached to MS Insider program, but the image was not marked as beta
-
@teamits said in MS activated DoH at the operating system level, in this "great" 20H2 release...?!:
Well that's the one I get:
Yes, there's the IP 13.107.4.52
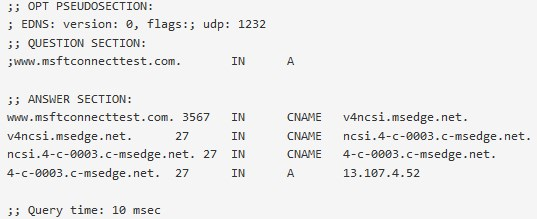
but, the IP according to the win registry...131.107.255.255
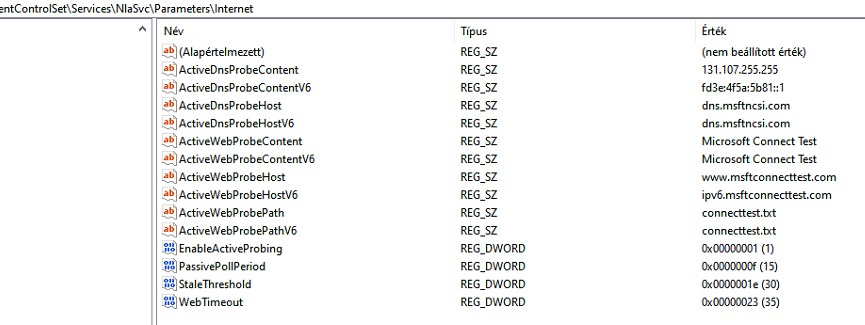
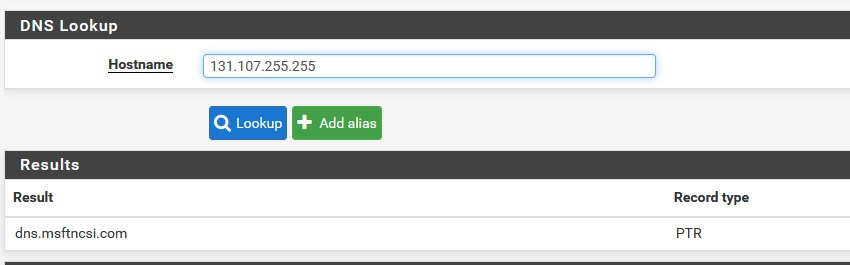
pfBlockerNG (from Win10 1909 PC):
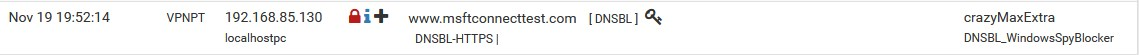
on the new PC (20H2), the request does not pass through pfBlockerNG, directly download the connecttest.txt from this IP 13.107.4.52
+++edit:
So the situation is changing, when I go back to 1909 and 2004 everything works as expected....
(everything is the same in the network environment, everything....)The pfBlockerNG works great!!!
who wants to test this "image 20H2" I'd love to upload it somewhere...
(DropBox, MEGA, etc)thoughts,
-when on an older "win" installation (what you have), you keep moving up with versions 1803, 1909, 2004, etc.
(the behavior is not the same as a clean installation)-I have now done a clean installation with 20H2 from a VLSC image and I'm not a fool and/or beginer, there are trivial problems here...
in the post I not only presented the MS connect test, there is another domain that behaves this way...
see this: o.ss2.usI haven't tested any more steps....
(what I know is that I get the same in a VM environment) -
+++edit:
So the situation is changing, when I go back to 1909 and 2004 everything works as expected....
(everything is the same in the network environment, everything....)The pfBlockerNG works great!!!
who wants to test this "image 20H2" I'd love to upload it somewhere...
(DropBox, MEGA, etc)thoughts,
-when on an older "win" installation (what you have), you keep moving up with versions 1803, 1909, 2004, etc.
(the behavior is not the same as a clean installation)-I have now done a clean installation with 20H2 from a VLSC image and I'm not a fool and/or beginer, there are trivial problems here...
in the post I not only presented the MS connect test, there is another domain that behaves this way...
see this: o.ss2.usI haven't tested any more steps....
(what I know is that I get the same in a VM environment** -
Not saying you haven't found something odd. But I don't agree with your wording. That its at the os level.
To me - the os level would mean that all dns queries would be using doh. For all you know this is some "app" or service on the OS using doh to check for xyz..
I am using 20h2, and agree it wasn't clean.. It was from a 2004 clean install. My system would not update to 2004.. Stupid info about your system is not ready - yet no info on exactly what was keeping it from updating.
So I ended up doing a clean install to 2004, but then it updated to 20h2..
My 20h2 system is doing normal dns to msftncsi

I see no queries to ss2.us at all..
So while you have found something doing doh, I would be hesitant to say the OS dns client is doing it.. It clearly is not doing it for all queries..
My take on the ss2.us - its something to do with certs.. And is tied to https://www.starfieldtech.com/
-
@johnpoz said in MS activated DoH at the operating system level, in this "great" 20H2 release...?!:
Not saying you haven't found something odd. But I don't agree with your wording. That its at the os level.
Yes sir, but :-)
I agree with you in a super way...
please try this "image" even on a VM... or other way
if you think, I'll upload it for you somewhere...I feel myself completely stupid about that...
-
@johnpoz said in MS activated DoH at the operating system level, in this "great" 20H2 release...?!:
My 20h2 system is doing normal dns to msftncsi
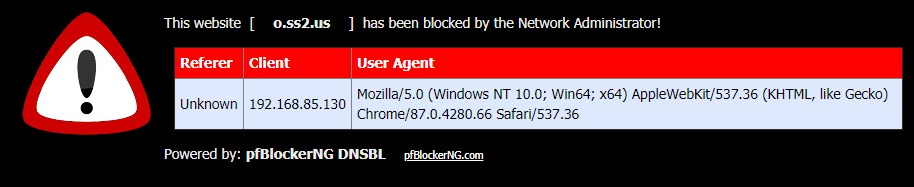
--- o.s22.us
I'll show you again,
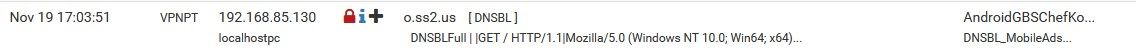
this domain is blocked by us..., o.ss2.us via DNSBL feedWin1909:
test PC on clean 20H2:
network setup:
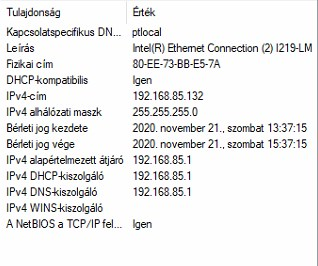
pfSense IP is: 192.168.85.1
igen = yes
DHCP kiszolgáló = DHCP server(sorry for the hungarian OS language)
more over:
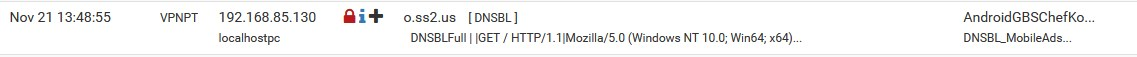
192.168.85.130 on Win1909
no entry from 192.168.85.132 on win 20H2
-
You would prob get better help on some MS forum.. While this I guess could be related to pfblocker.. If said device doesn't ask pfblocker for dns, that is not pfsense or pfblocker that keeps the client from doing that.
Why said client doesn't use your assigned dns, would be up to the client.. No matter what you hand it via dhcp.
I wouldn't block that mfsft site for sure.. That is a well known domain in how windows check if it has internet, etc. Blocking it could for sure kick in other methods of the OS trying to see if it has any sort of internet connectivity..
-
@johnpoz said in MS activated DoH at the operating system level, in this "great" 20H2 release...?!:
You would prob get better help on some MS forum..
you're just kidding me now, aren't you?

@johnpoz "I wouldn't block that mfsft site for sure.."
it's just a matter of taste

so as I wrote above we run an external connecttest server, this is not an MS denial...it was just enough of the voyeur or something...
not really a pfSense or pfBlockerNG theme (issue), yet ... you are right (let's say it's a simple statement)but it will be....?!
I knew that, you will be the first to respond to my post, knowing your DoH hate...
(we are rowing in the same boat)do not think that, the future will not come
you cannot delay it, by denying it...+++edit:
I would willingly to give you this "image 20H2 VLSC" if you think, try it on a VM, you don't have to activate it for a few days and you'll see what the future holds I say kindly

-
it would be a much more expedient test, if the leaderboard poster also tried what I am talking about... or anyone else who is willing...
@johnpoz don't get me wrong I seriously respect you


one more time...
I did not share this to seek for advice, just I reported a fact...
(it will affect, everyone in the community)so the defensive behavior is unnecessary in this case...
this is not a pfSense theme yet, but it will be...(maybe the Wireshark isn't lying??!!)
so I’m not going to comment on that anymore, because the stiff rejection isn’t good...who is brave ask me for a "image 201H2" in PM
-
It really wouldn't surprise me if you aren't seeing the start of microsoft following what the other's have already done.
It seem's like everytime I update edge on a machine at the shop I have to go through the setting's and disable a bunch of crap and they advertise that edge is secure what a joke.
-
@DaddyGo said in MS activated DoH at the operating system level, in this "great" 20H2 release...?!:
this is not a pfSense theme yet, but it will be...
Not trying to be defensive, but no this will never be a pfsense anything.. What some OS does, be it linux, be it windows, be it beos or bsd, mac osx, etc. etc..
The only way this would have anything to do with pfsense would be if freebsd decided to only allow for doh, etc.. ;)