OpenVPN site to site - Only traffic from pfsense boxes work
-
Hi guys;
Im new in this community. I have some background in networking technology but I'm new into this pfsense world.
I have a problem with the OpenVPN setup, maybe you can help me out.
The case is, I have 2 pfsense boxes one in each office.
Pfsense1 is the root office, with the OpenVPN site to site server.
This box is configured as follows:- WAN ADDRESS with access to internet
- LAN: 10.0.111.0/24
- OpenVPN server peer to peer
tunnel net: 10.0.18.0/24
remote net: 10.0.50.0/24
On the other side, I have another box with the same version of PFsense, and acts as client. The configuration is as follows:
- WAN ADDRESS with access to internet
- LAN: 10.0.50.0/24
- OpenVPN client
tunnel net: 10.0.18.0/24
remote net: 10.0.111.0/24
The problem is, the PFsense boxes can ping each other to their LAN addresses (10.0.111.1 and 10.0.50.1), but when I trying to ping from a LAN computer of one side (10.0.111.10) to a LAN computer of the other side (10.0.50.10 or even the pfsense box) there is no connectivity.
I have the following rules in place in the firewall:
Pfsense1
OpenVPN: allow all
WAN: OpenVPN port open
LAN: allow allPfsense2:
OpenVPN: allow all
LAN: allow all
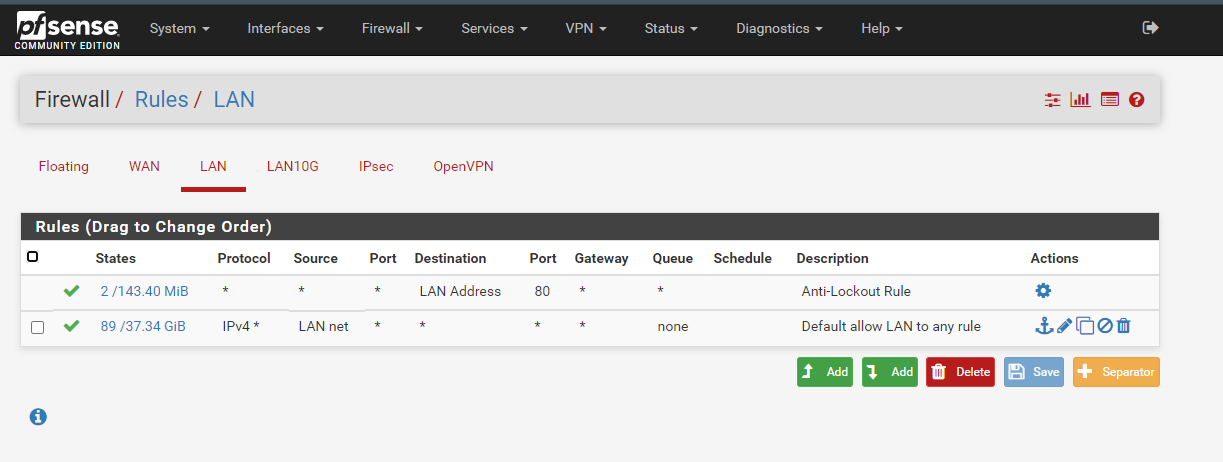
If I go to states; I can see the TPC traffic as SYNC_SENT but no connectivity at all
Am I missing something?
Thank you for your advice!!
EDIT:
Added screenshot from the box2 (10.0.50.1) ping to the box 1 LAN address (10.0.111.1)
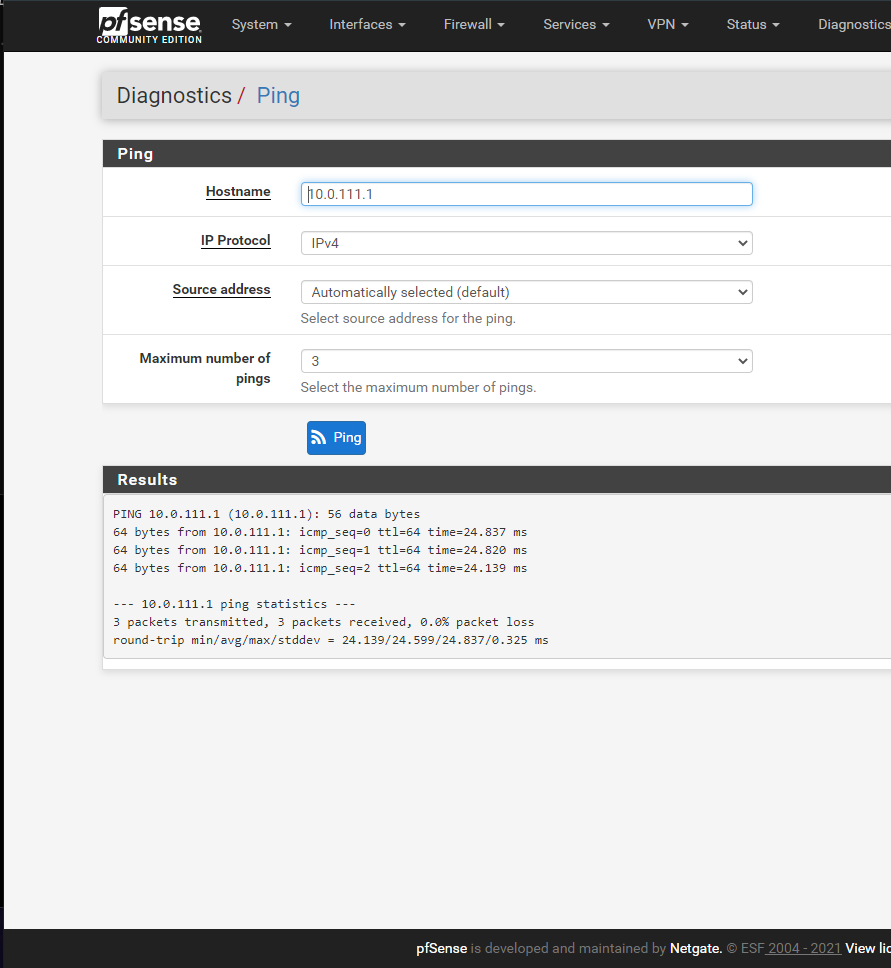
If I select source address as LAN, the ping does not go through:
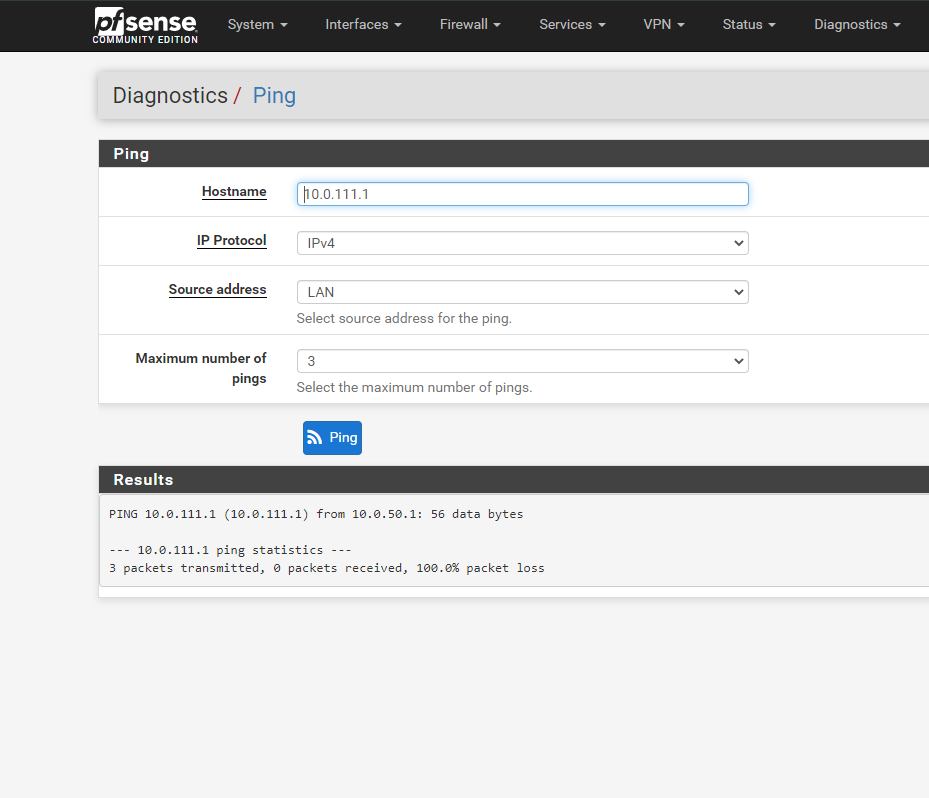
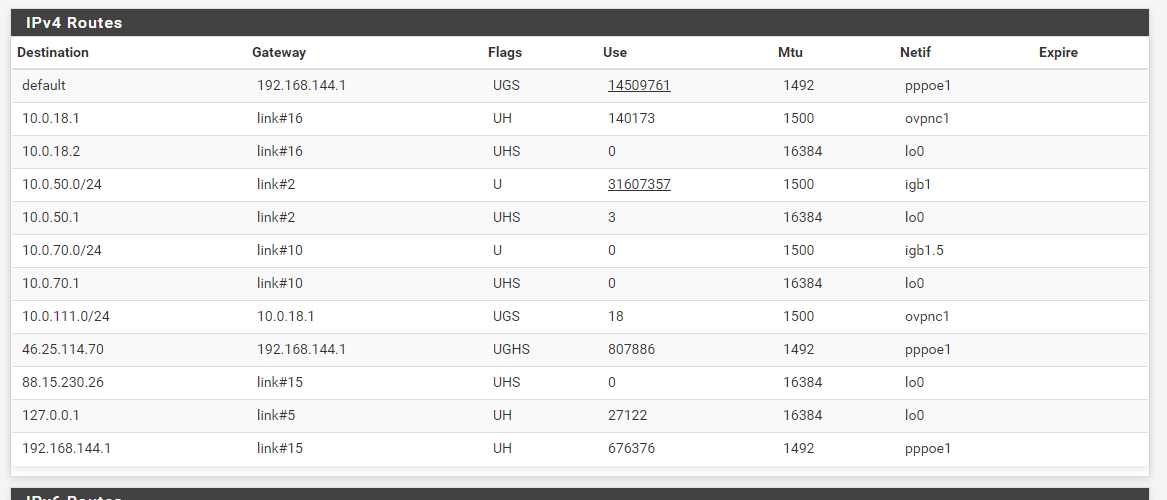
Seems like this LAN - OVPN Client routing is not working, but in the routing tables I see all ok:
-
Something wrong here?
@iago-op said in OpenVPN site to site - Only traffic from pfsense boxes work:
Pfsense1 is the root office, with the OpenVPN site to site server.
This box is configured as follows:WAN ADDRESS with access to internet
LAN: 10.0.111.0/24
OpenVPN server peer to peer
tunnel net: 10.0.18.0/24
remote net: 10.0.50.0/24On the other side, I have another box with the same version of PFsense, and acts as client. The configuration is as follows:
WAN ADDRESS with access to internet
LAN: 10.0.111.0/24
OpenVPN client
tunnel net: 10.0.18.0/24
remote net: 10.0.111.0/24 -
@viragomann sure man
the pfsense2 box is 10.0.50.0/24 sorry and thanks for the help!
-
@iago-op
Are both pfSense boxes the default gateway in the respective LAN?If so check the firewall on the destination device. By default it is blocking access from out of its own subnet.
-
@viragomann
Yeah@viragomann said in OpenVPN site to site - Only traffic from pfsense boxes work:
@iago-op
Are both pfSense boxes the default gateway in the respective LAN?If so check the firewall on the destination device. By default it is blocking access from out of its own subnet.
Yeah there is only 1 WAN per pfsense box and each pc have the Pfsense box as the gateway (10.0.111.1 and 10.0.50.1 respectively)
As far as the LAN firewall, I have an allow all rule on each Pfsense LAN. this should be enough right?
-
@iago-op
The point is if the destination device itself is allowing the access from the remote network.You can easily check this with pfSense. On the pfSense next to the device go to Diagnostic > Ping, enter its IP at host and try to ping. Should succeed.
Then change the source to OpenVPN and try again. Does this succeed as well? -
@viragomann said in OpenVPN site to site - Only traffic from pfsense boxes work:
@iago-op
The point is if the destination device itself is allowing the access from the remote network.You can easily check this with pfSense. On the pfSense next to the device go to Diagnostic > Ping, enter its IP at host and try to ping. Should succeed.
Then change the source to OpenVPN and try again. Does this succeed as well?Thanks for your tip, but I've already checked that.
If I ping using either default, or OpenVPNclient the ping goes through
If I ping using LAN, it does not. The same as if I use a computer into the local LAN to do the end to end ping.
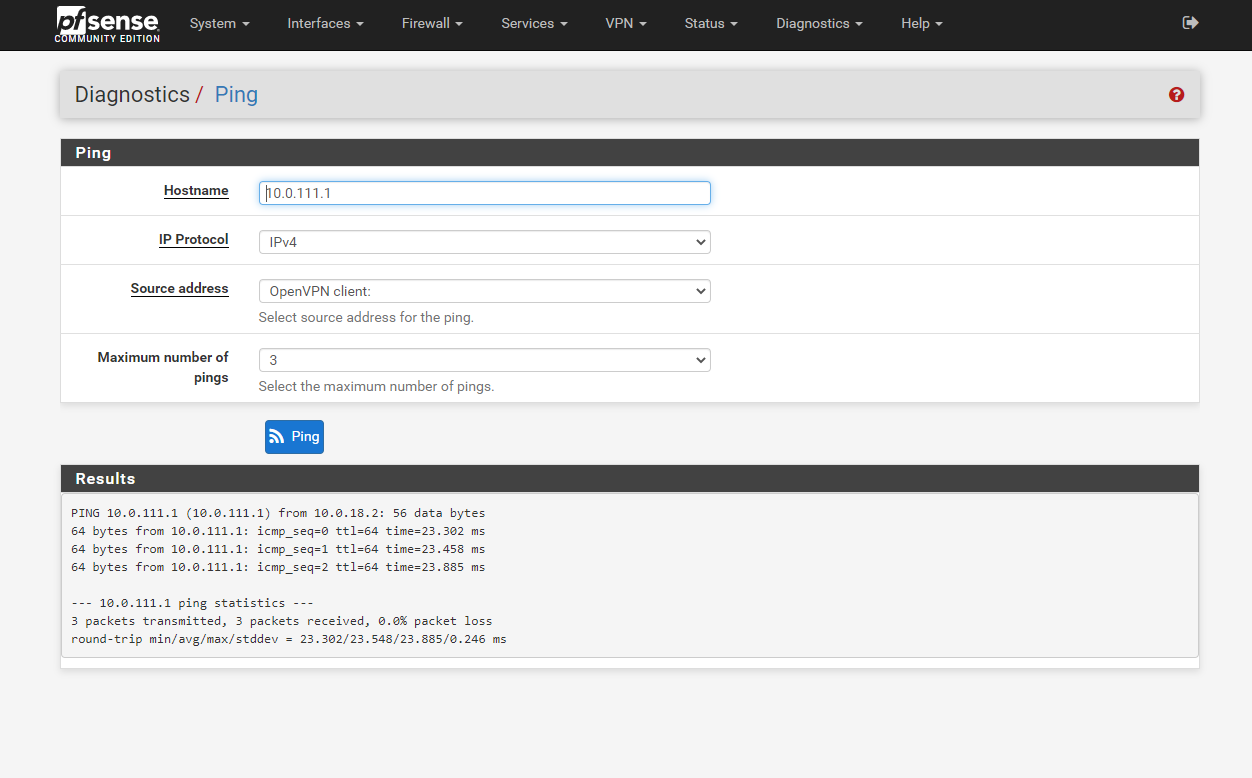
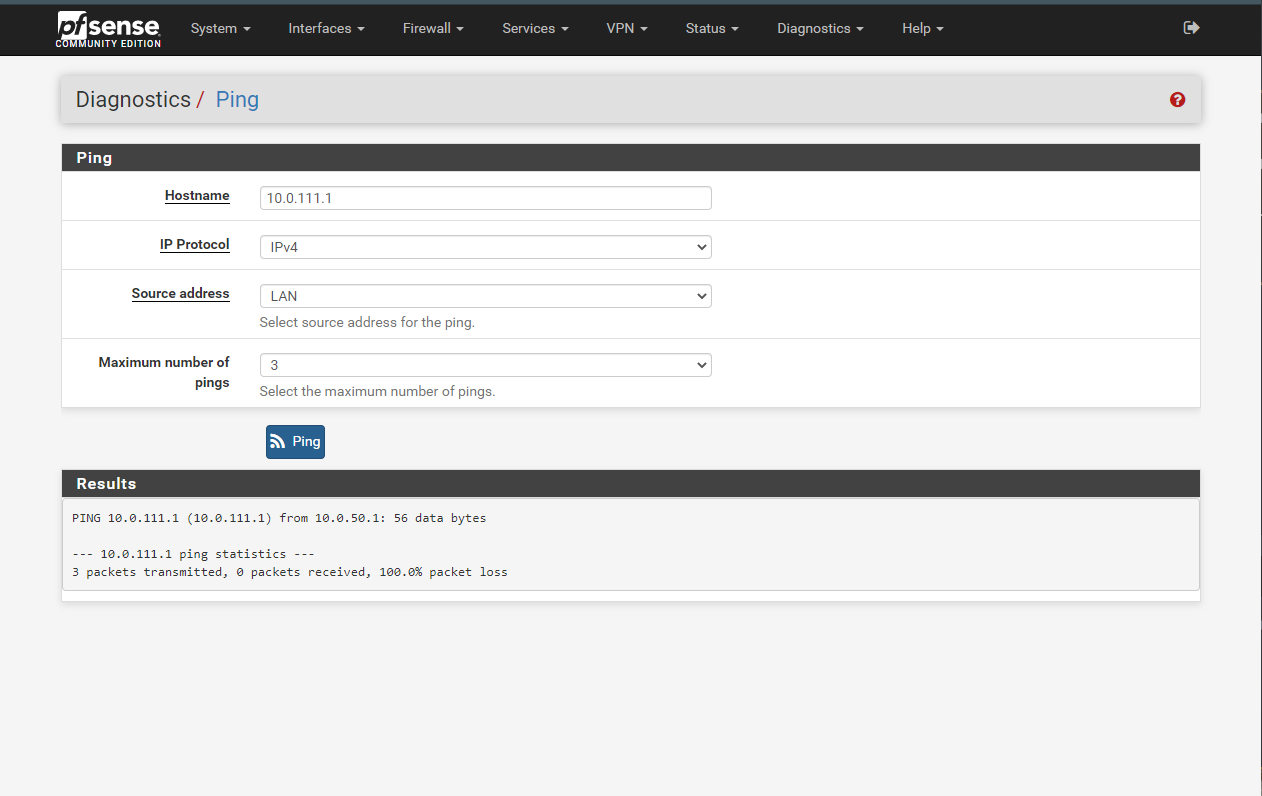
I also did another test. Try to open a webpage from my local computer (10.0.50.10) in a remote end machine webserver (10.0.111.200) while I debug with the pTop utility:
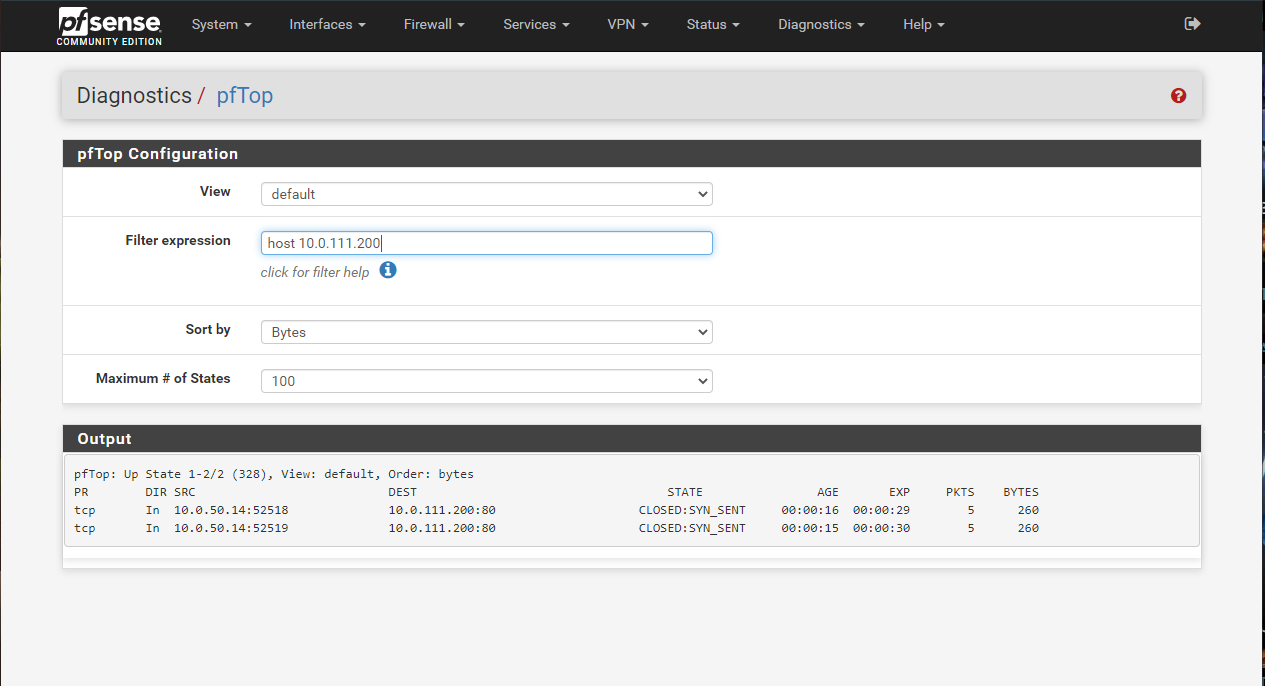
-
@iago-op said in OpenVPN site to site - Only traffic from pfsense boxes work:
If I ping using either default, or OpenVPNclient the ping goes through
If I ping using LAN, it does not. The same as if I use a computer into the local LAN to do the end to end ping.I asked to do that on the pfSense box next to the destination device, not on the remote box and not pinging the one of the pfSense boxes themself. You did already mention above that this is working.
So go on the server and ping any device in it LAN 10.0.111.0/24. -
@viragomann said in OpenVPN site to site - Only traffic from pfsense boxes work:
@iago-op said in OpenVPN site to site - Only traffic from pfsense boxes work:
If I ping using either default, or OpenVPNclient the ping goes through
If I ping using LAN, it does not. The same as if I use a computer into the local LAN to do the end to end ping.I asked to do that on the pfSense box next to the destination device, not on the remote box and not pinging the one of the pfSense boxes themself. You did already mention above that this is working.
So go on the server and ping any device in it LAN 10.0.111.0/24.Yep, the scenario is:
ClientsLAN1 -10.0.111.0/24- Pfsense1(server) [ OPENVPN ] Pfsense2 --10.0.50.0/24- ClientsLAN2
Everything between Pfsense1(server) and LAN2 works ok (pfsense and clients)
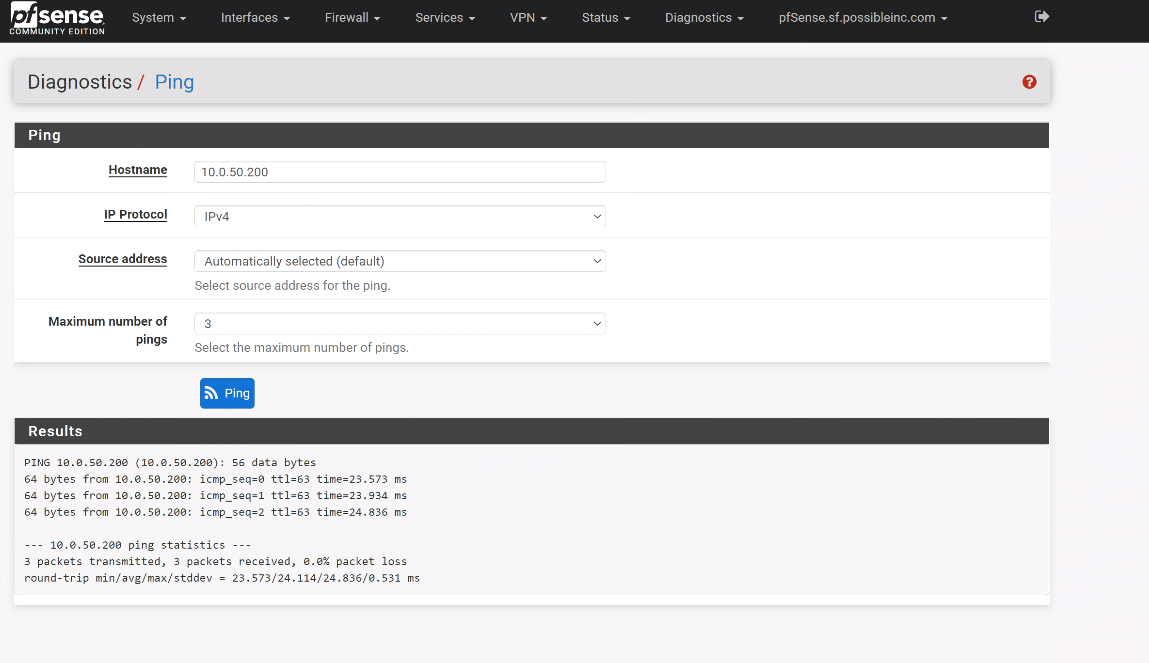
The same, everything between pfsense2 and LAN1 work ok.
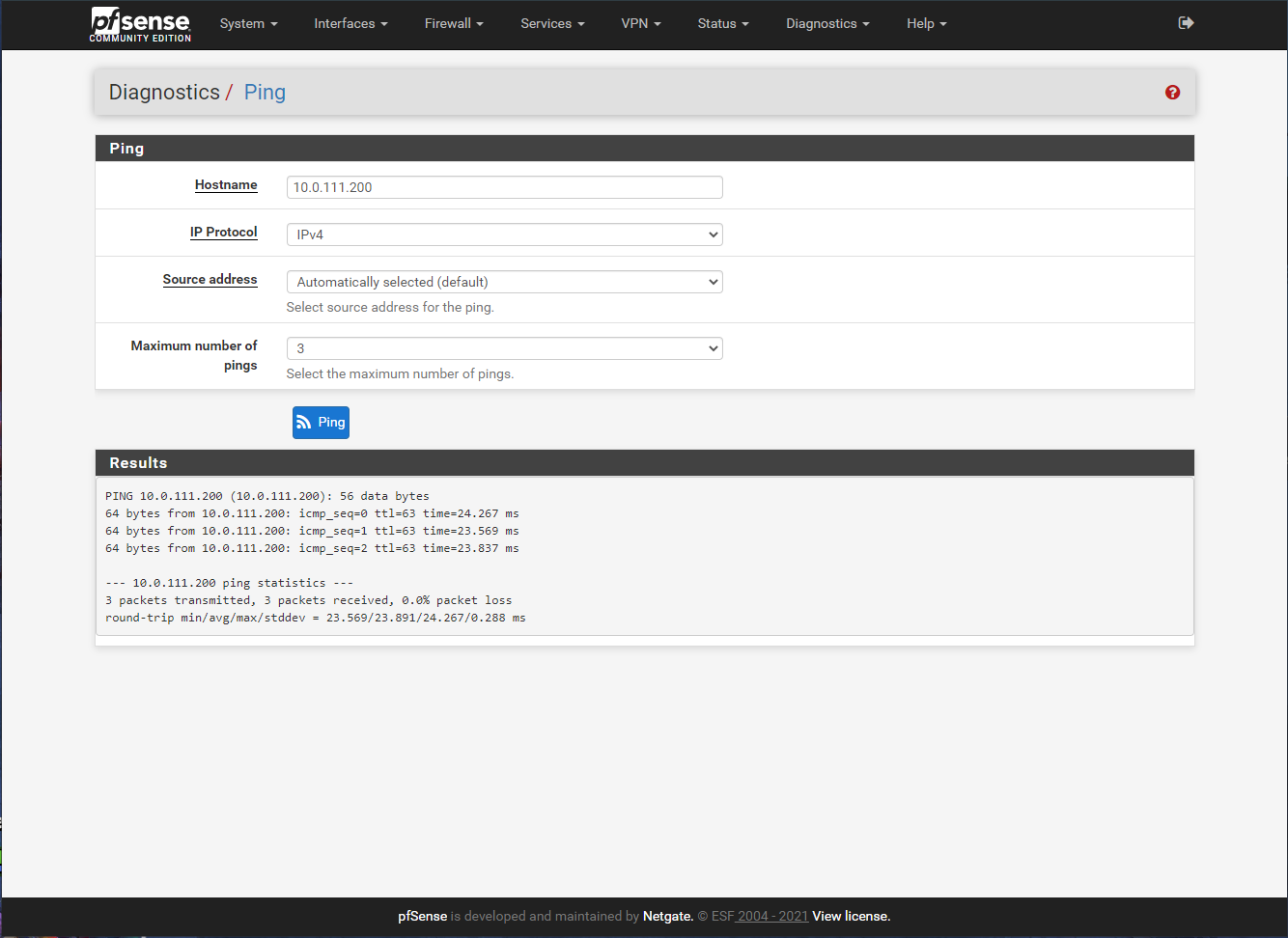
The problem is when I try LANCLIENTS1 to LANCLIENTS2
Is weird, could be a bug in pfsense? Should I miss some rules ? -
@iago-op
Fine now you're showing pings on both site with default settings. Still no use. -
@viragomann said in OpenVPN site to site - Only traffic from pfsense boxes work:
@iago-op
Fine now you're showing pings on both site with default settings. Still no use.@viragomann said in OpenVPN site to site - Only traffic from pfsense boxes work:
I asked to do that on the pfSense box next to the destination device, not on the remote box and not pinging the one of the pfSense boxes themself. You did already mention above that this is working.
So go on the server and ping any device in it LAN 10.0.111.0/24.On the server, I can ping the LAN devices without problems
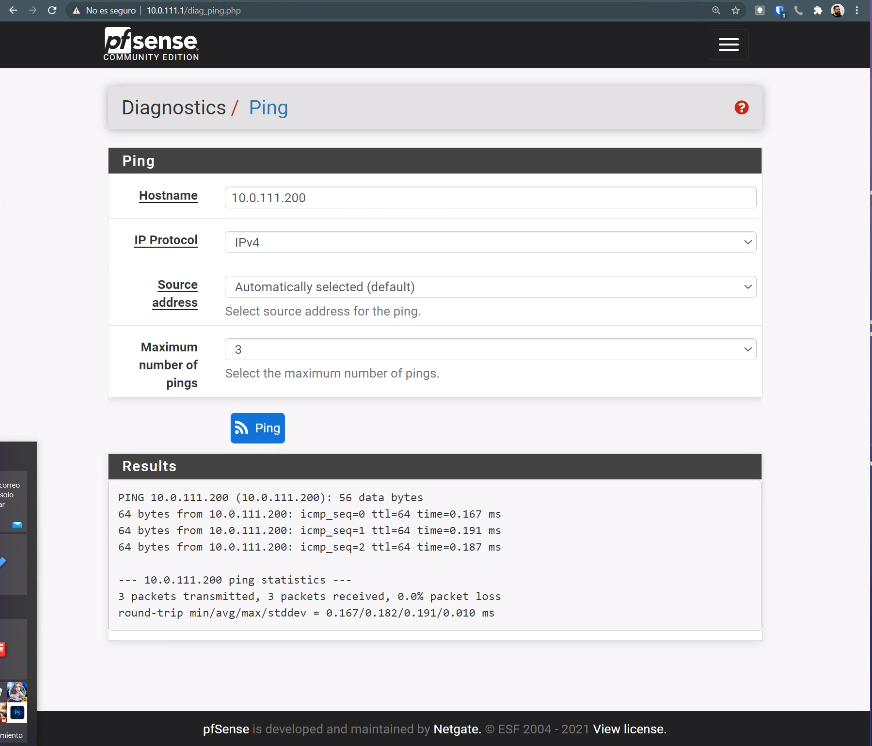
Thanks for you help mate
-
@iago-op said in OpenVPN site to site - Only traffic from pfsense boxes work:
On the server, I can ping the LAN devices without problems
Dude! I'm not in doubt of that. Mentioned above. But what do you get here if you simple change the source to OpenVPN???
-
@viragomann said in OpenVPN site to site - Only traffic from pfsense boxes work:
@iago-op said in OpenVPN site to site - Only traffic from pfsense boxes work:
On the server, I can ping the LAN devices without problems
Dude! I'm not in doubt of that. Mentioned above. But what do you get here if you simple change the source to OpenVPN???
It also works
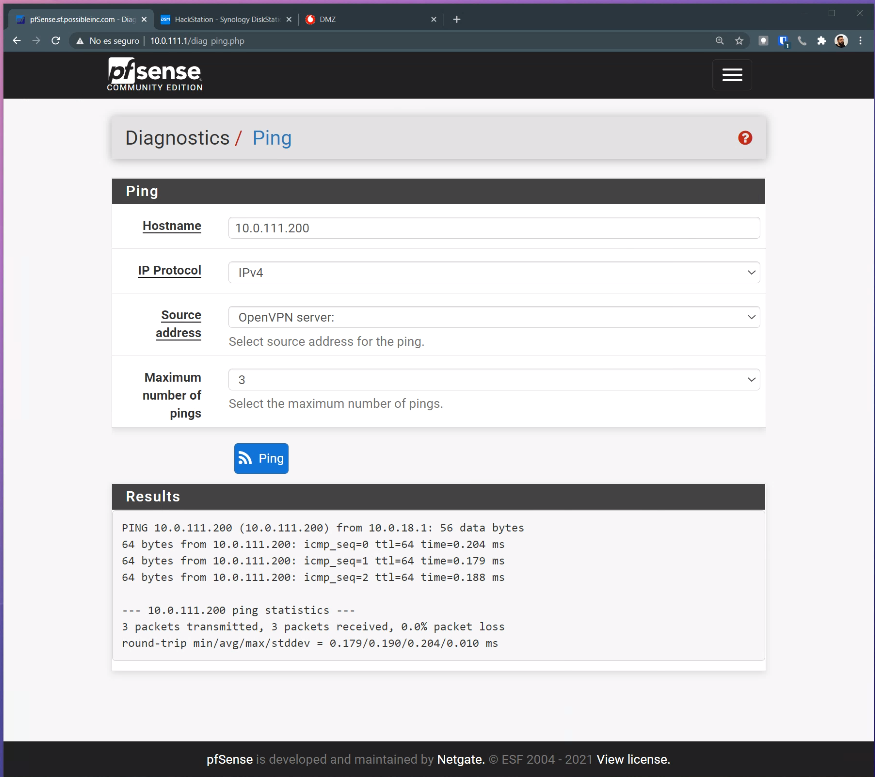
In the server side, I can ping from openVPN to CLientLAN1 without problems.
On the client side, the same, pings between OpenVPN interface/lan and the ClientsLAN2 work fine.
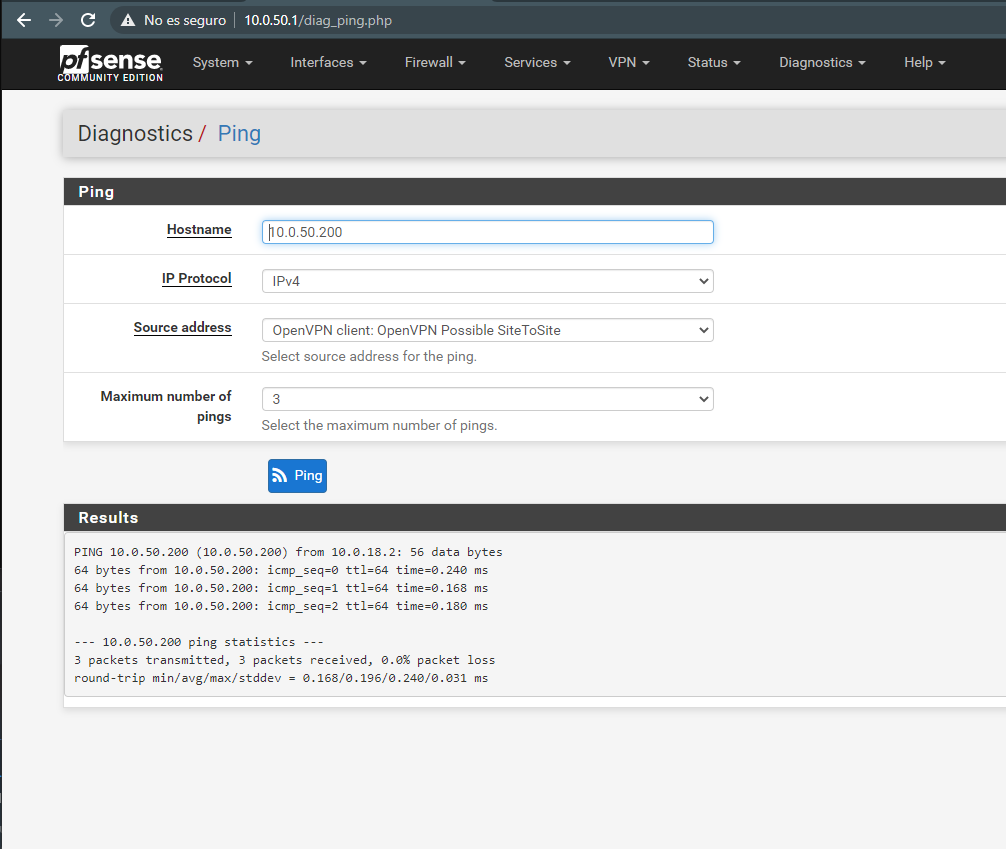
It just only fails on the LAN1 to LAN2 communications :S it's weird right?
-
@iago-op
Well. So the device is not blocking the access.
So let's take a look into the routing tables of both pfSense boxes. -
@viragomann said in OpenVPN site to site - Only traffic from pfsense boxes work:
@iago-op
Well. So the device is not blocking the access.
So let's take a look into the routing tables of both pfSense boxes.Client:
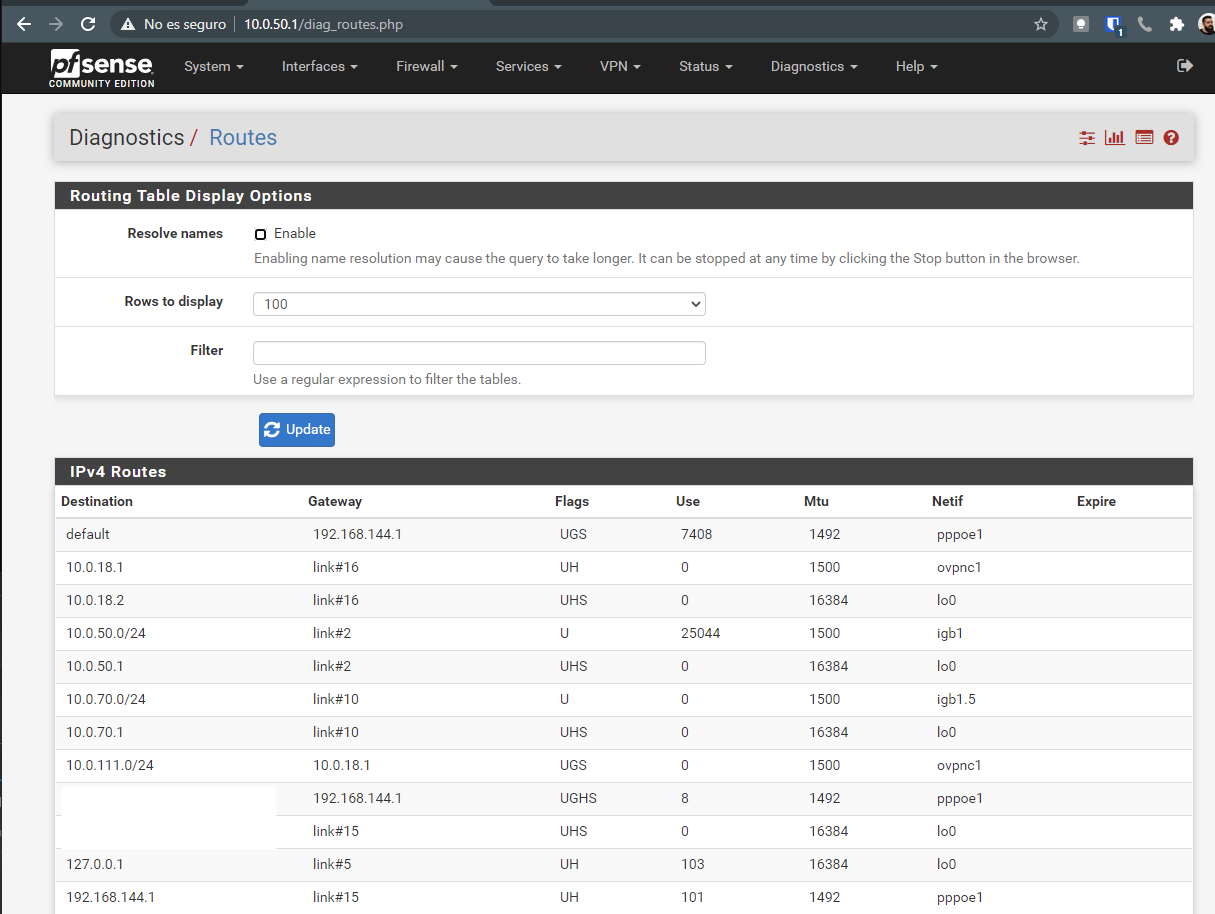
I can see the route 10.0.111.0/24 going through 10.0.18.1 which is the OpenVPN interfaceOn the server side:
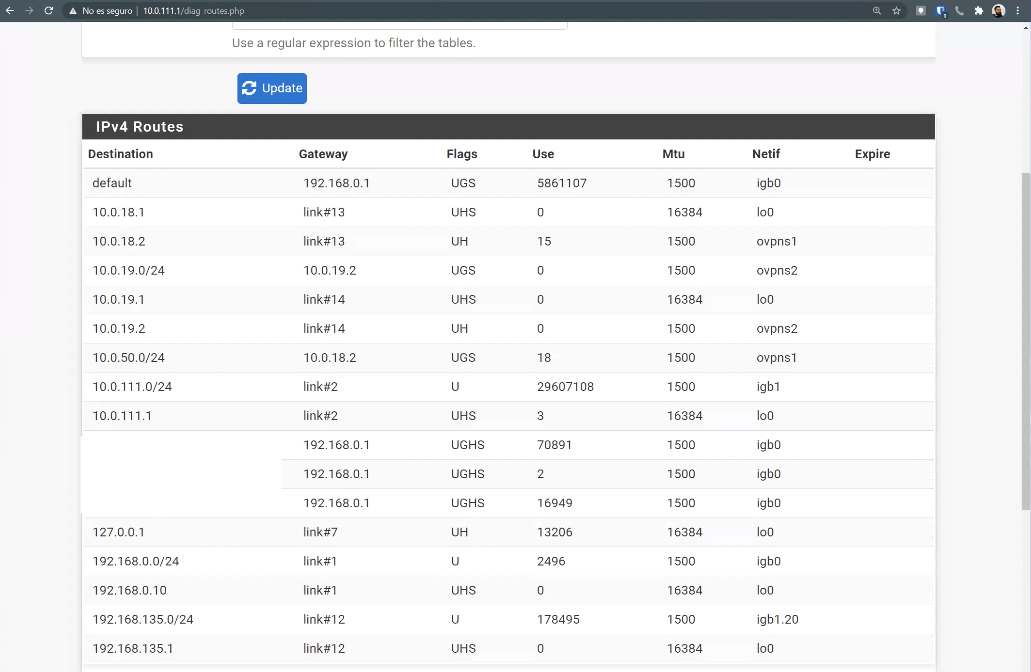
I also see the correct routes:
10.0.50.0/24 by 10.0.18.2(I also have in here a server2 which i creted trying to solving this problem with a new server, but I I'm not using it right now)
Thanks !!
-
@iago-op
Seems to be well.Static public IPs should better be hidden when you post a screenshot in the web. The PPPoE may change, but I don't know of the other one.
Interestingly the client show no use of the route. Maybe if you try a connection from the clients LAN.
Yes, absolutely weird.
We had already issues with VPNs that won't work while all seems fine. After pulling it down and start from scratch it mostly worked.You may try more investigations with the packet capture tool, but I cannot think of any further reason.
Only one thing are the firewall rules on OpenVPN interface. You didn't post a screenshot. So consider for pinging you have to allow ICMP or any protocol. If you have only TCP, ping will not work.
-
@viragomann said in OpenVPN site to site - Only traffic from pfsense boxes work:
@iago-op
Seems to be well.Static public IPs should better be hidden when you post a screenshot in the web. The PPPoE may change, but I don't know of the other one.
Interestingly the client show no use of the route. Maybe if you try a connection from the clients LAN.
Yes, absolutely weird.
We had already issues with VPNs that won't work while all seems fine. After pulling it down and start from scratch it mostly worked.You may try more investigations with the packet capture tool, but I cannot think of any further reason.
Only one thing are the firewall rules on OpenVPN interface. You didn't post a screenshot. So consider for pinging you have to allow ICMP or any protocol. If you have only TCP, ping will not work.
Yep, Thanks for the remainder of the public ips :)
the OpenVPN firewall rules are allow all for all protocols. I just make sure because of this tests specifically with ping.
There is any way to debug this kind of problems? Like a traceroute which indicates what interfaces goes through a packet?
Tank you again mate
-
@iago-op said in OpenVPN site to site - Only traffic from pfsense boxes work:
@viragomann said in OpenVPN site to site - Only traffic from pfsense boxes work:
@iago-op
Seems to be well.Static public IPs should better be hidden when you post a screenshot in the web. The PPPoE may change, but I don't know of the other one.
Interestingly the client show no use of the route. Maybe if you try a connection from the clients LAN.
Yes, absolutely weird.
We had already issues with VPNs that won't work while all seems fine. After pulling it down and start from scratch it mostly worked.You may try more investigations with the packet capture tool, but I cannot think of any further reason.
Only one thing are the firewall rules on OpenVPN interface. You didn't post a screenshot. So consider for pinging you have to allow ICMP or any protocol. If you have only TCP, ping will not work.
Yep, Thanks for the remainder of the public ips :)
the OpenVPN firewall rules are allow all for all protocols. I just make sure because of this tests specifically with ping.
There is any way to debug this kind of problems? Like a traceroute which indicates what interfaces goes through a packet?
Tank you again mate
I think I have a clue. Revieweing the logs for each interface I found that it's using ipv6 routing in the client side. While on the client side, openVPN is configured only to use ipv4
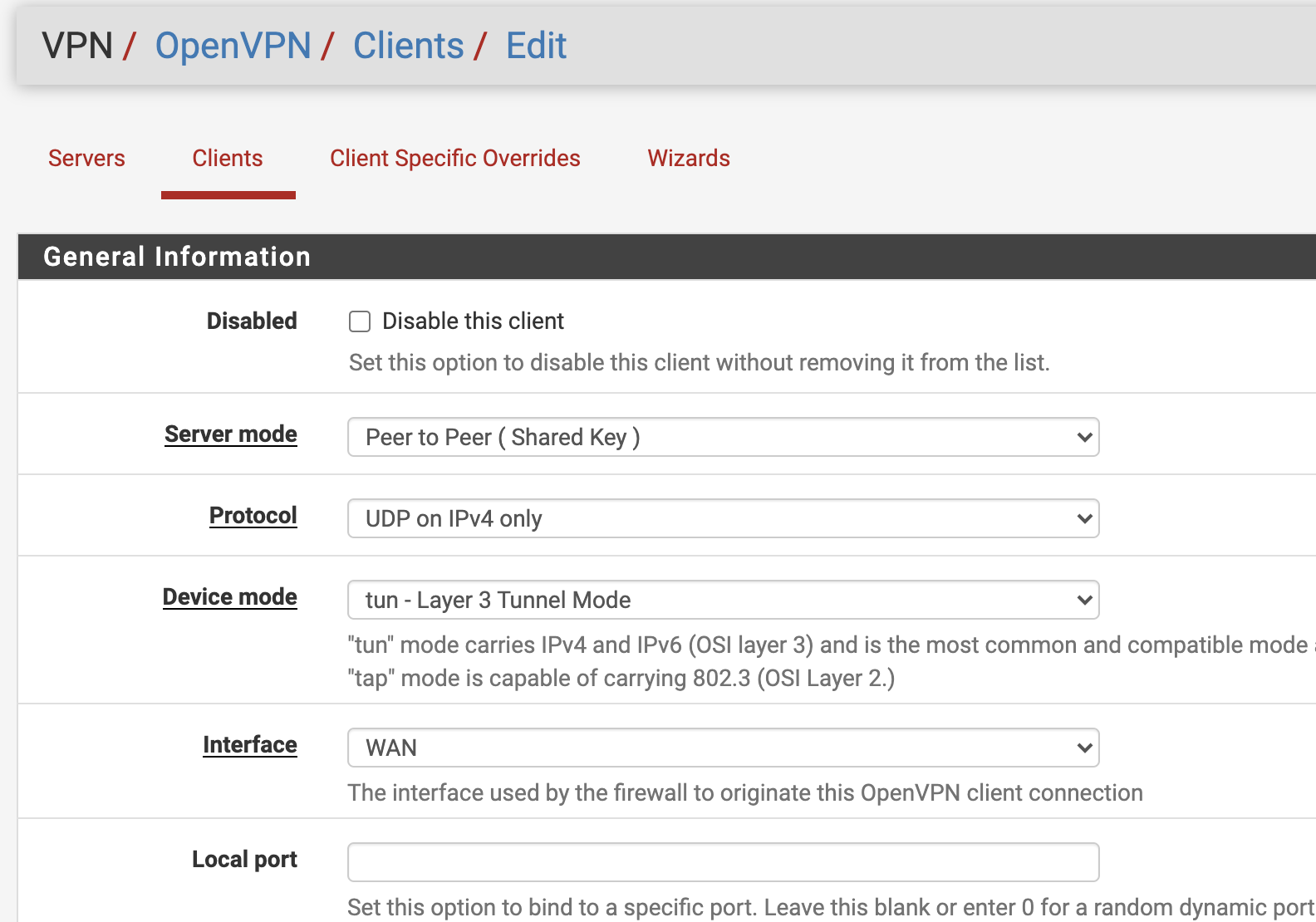
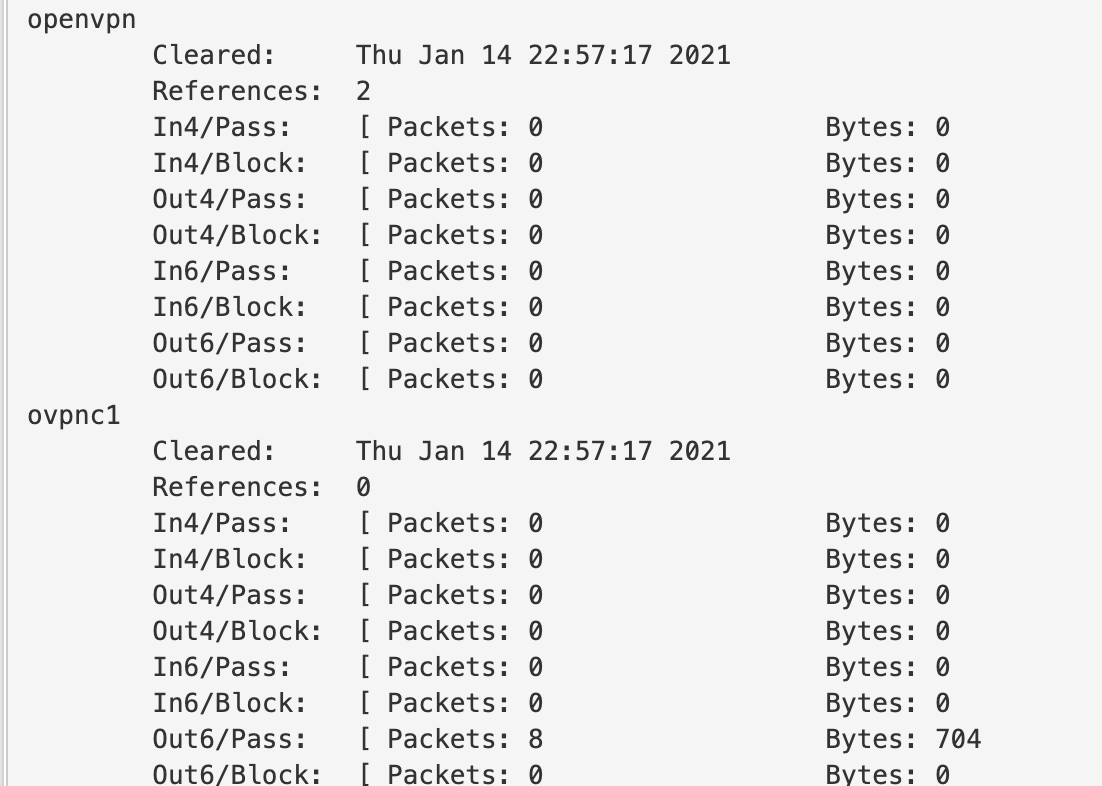
Maybe cloud be this ?
-
The routing protocol setting is at the bottom, you can check IPv4 gateway only there.
-
@viragomann said in OpenVPN site to site - Only traffic from pfsense boxes work:
The routing protocol setting is at the bottom, you can check IPv4 gateway only there.
In one side was ipv4 but in the other side was both. I changed to ipv4 only but this not fixed the problem.
as I'm expected.I keep investigating. If I do a packet capture on the openvpn interface in the client while a ping is in course, it does not register any packet.