OpenVPN clients can't ping LAN
-
I am a newbie to pfSense so please forgive me, first off. I've setup the box on Digital Ocean which provides VPC or virtual private networks for private IPs so my droplets (virtual servers) can communicate privately. I've used all default settings when I installed pfSense and I've configured the LAN network in pfSense to my private VPC network. Then, I installed the OpenVPN server on pfSense using the Wizard, created a new CA, new certificate, etc. I installed the client export package, and I can successfully connect to the VPN fine and ping both the public WAN ip and private LAN ip on the pfSense box just fine. I also added the push route in advanced settings for the OpenVPN server. I see the routes on my local machine (Ubuntu 20.04 LTS x64) when I connect to the VPN, however I CANNOT for the life of me ping any other server on the private network 10.116.0.0/20.
For reference and help in troubleshooting, here are some settings:
pfSense box: public IP on WAN / private 10.116.0.3/20 on LAN
LAN machines: private addresses in 10.116.0.0/20
pfSense OpenVPN tunnel: 192.168.0.0/20
OpenVPN server Force all ipv4 traffic through tunnel checked
OpenVPN server Adv options push "route 10.116.0.0.20";No firewall on internal LAN ip 10.116.0.2
Can ping 10.116.0.3 (pfSense LAN address) with no issues
CAN NOT ping 10.116.0.2 (another server on private LAN) or any other LAN server when connected to VPNI have been up all night, reading pfSense documentation regarding static routes, Firewall rules, etc. and I can't for the life of me figure out what's going on. I've read through tons of previous posts on this forum for OpenVPN to LAN connection issues and I just can't get this to work. I've tried Outbound NAT rules, Firewall rules from OpenVPN to LAN, firewall rules from the interface OPT1 (which the OpenVPN wizard created) to the private LAN - nothing works. I even found an article online specifically related to Digital Ocean, but it requires running their specific OpenVPN appliance and I only want to use pfSense for firewall and OpenVPN (the article is at https://mohsensy.github.io/sysadmin/2019/06/21/secure-access-to-digital-ocean-resources-using-openvpn.html). It DOES, however, mention that NAT is the best way to go with their specific VPC private networks if that helps.
I would really appreciate someone helping me, I've spent so much time trying to get this to work and I must admit I'm new to pfSense but honestly it seems like the best product to achieve my goals. Thanks in advance!
-
UPDATE: Apparently, Digital Ocean won't let external machines connect to other machines in their VPC (private network) unless there is another machine configured as a gateway. You can read all about it here: https://www.digitalocean.com/docs/networking/vpc/resources/droplet-as-gateway/. So, from what they're saying, I need my pfSense box to forward as a router (sysctl -w net.ipv4.ip_forward=1) and THEN I have to configure NAT as:
iptables -t nat -A POSTROUTING -s 10.116.0.0/20 -o <my-pfSense-public-IP> -j MASQUERADEHonestly, I have NO idea how to do this on pfSense... can someone please help?
-
The first thing I would do is move to a different subnet for your tunnel. As configured, any client whose LAN is in the 192.168.0.0/20 range is subject to routing issues.
OpenVPN server Adv options push "route 10.116.0.0.20";
Is this a typo? If not, this may be your issue. The correct command for pushing a route for 10.116.0.3/20 would be:
push "route 10.116.0.0 255.255.240.0"
However, these type of statements no longer need to be defined manually. If you add 10.116.0.0/20 to the IPv4 Local network(s) section of your config, the above command will get generated automatically.
So, from what they're saying, I need my pfSense box to forward as a router (sysctl -w net.ipv4.ip_forward=1) and THEN I have to configure NAT as:
iptables -t nat -A POSTROUTING -s 10.116.0.0/20 -o <my-pfSense-public-IP> -j MASQUERADE
PFsense has routing enabled by default and configures NAT statements for subnets assigned to LAN interfaces out of the box via Automatic Outbound NAT. So, unless you misconfigured manual outbound NAT or disabled NAT altogether, what they described for configuring a Linux distro as a gateway has already been done in PFsense.
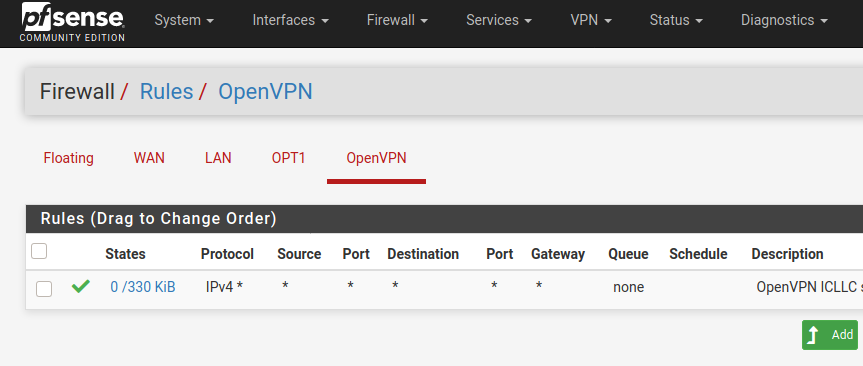
Unless you have client connections to a VPN service, the only thing on the OpenVPN tab should be an any/any rule
Remove any Outbound NAT rules you created for troubleshooting and switch back to Automatic Outbound NAT if you haven't already.
Post your config (/var/etc/openvpn)
-
@marvosa Yes, the Adv Options push "route.." was a typo, it was supposed to be:
push "route 10.116.0.0 255.255.240.0";As far as the local network, did you mean adding 10.116.0.0/20 or 10.116.0.3/20 as you stated above?
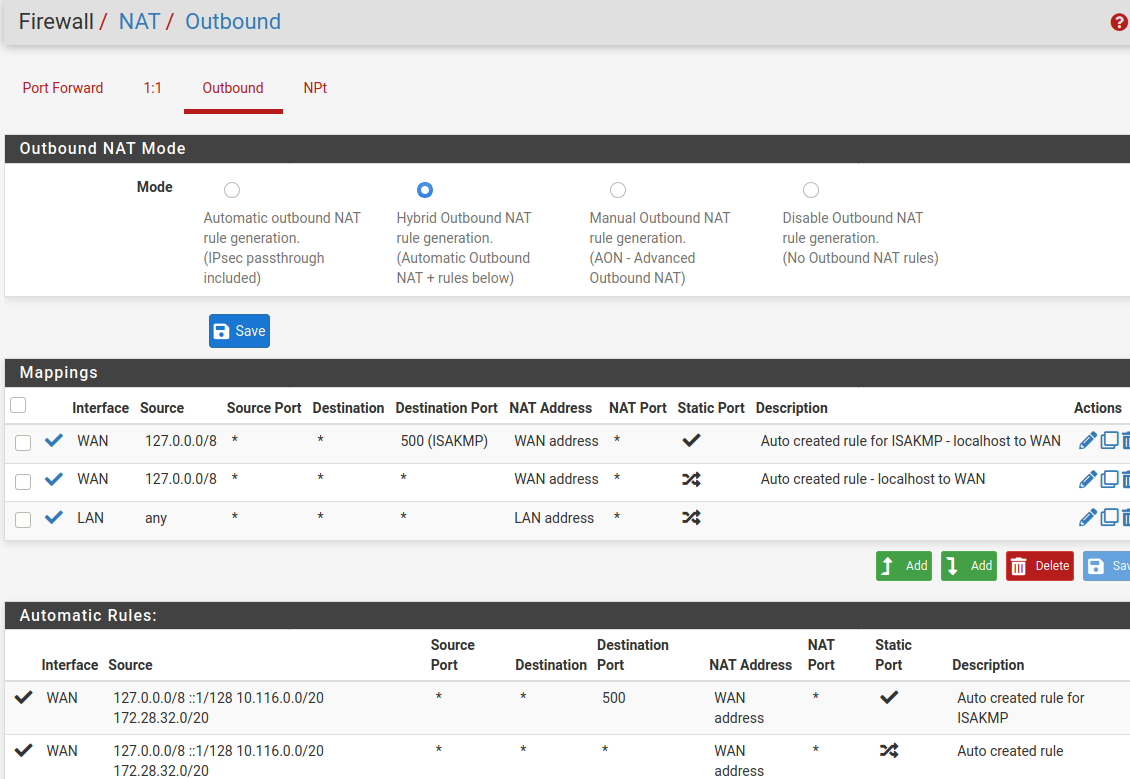
I just checked the OpenVPN tab in Firewall, there is only an any/any rule. I checked outbound NAT, it's automatic. Here is the /var/etc/openvpn/server1/config.ovpn:
[2.5.0-RELEASE][root@srdp.icllc.cc]/root: cat /var/etc/openvpn/server1/config.ovpn dev ovpns1 verb 1 dev-type tun dev-node /dev/tun1 writepid /var/run/openvpn_server1.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown client-connect /usr/local/sbin/openvpn.attributes.sh client-disconnect /usr/local/sbin/openvpn.attributes.sh local 161.xx.x.x tls-server server 192.168.0.0 255.255.240.0 client-config-dir /var/etc/openvpn/server1/csc username-as-common-name plugin /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so /usr/local/sbin/ovpn_auth_verify_async user TG9jYWwgRGF0YxxxxxU= false server1 1194 tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'xxx.xxx.xxx' 1" lport 1194 management /var/etc/openvpn/server1/sock unix max-clients 10 push "dhcp-option DNS 67.207.67.2" push "dhcp-option DNS 67.207.67.3" push "redirect-gateway def1" capath /var/etc/openvpn/server1/ca cert /var/etc/openvpn/server1/cert key /var/etc/openvpn/server1/key dh /etc/dh-parameters.2048 tls-auth /var/etc/openvpn/server1/tls-auth 0 ncp-disable cipher AES-256-CBC allow-compression no persist-remote-ip float topology subnet push "route 10.116.0.0 255.255.240.0"The auto NAT Outbound rules are:
WAN 127.0.0.0/8 ::1/128 10.116.0.0/20 192.168.0.0/20 * * 500 WAN address * Auto created rule for ISAKMP
WAN 127.0.0.0/8 ::1/128 10.116.0.0/20 192.168.0.0/20 * * * WAN address * Auto created rule
Thanks for your quick response. I don't know if this is Digital Ocean or something I did. -
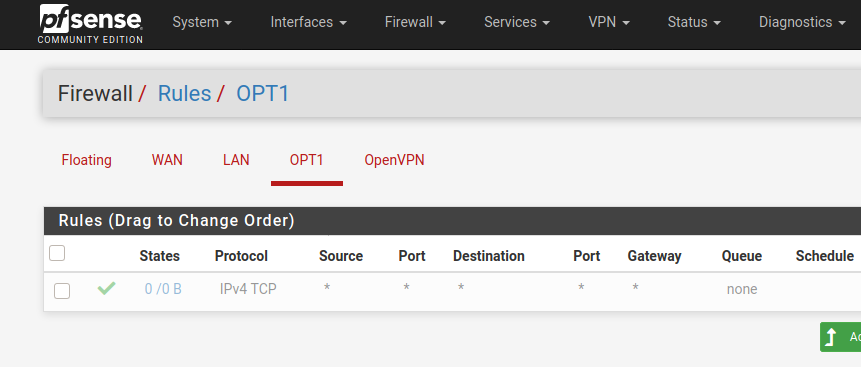
@marvosa Also, here are the Firewall rules for the two interfaces...
-
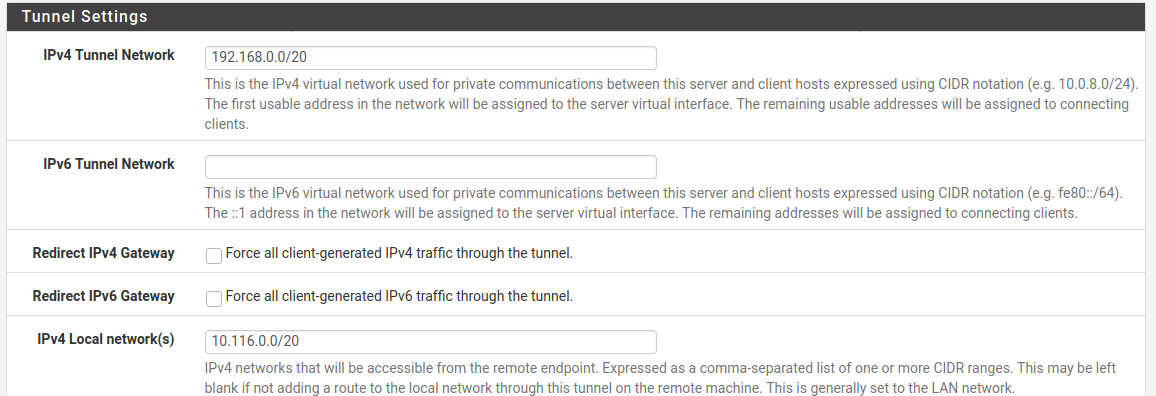
@marvosa Sorry, I wanted to add one more thing... There is an option to forward all IPv4 traffic, and I have it checked, but only when I unchecked it I get the Local Lan, and I have it as shown...
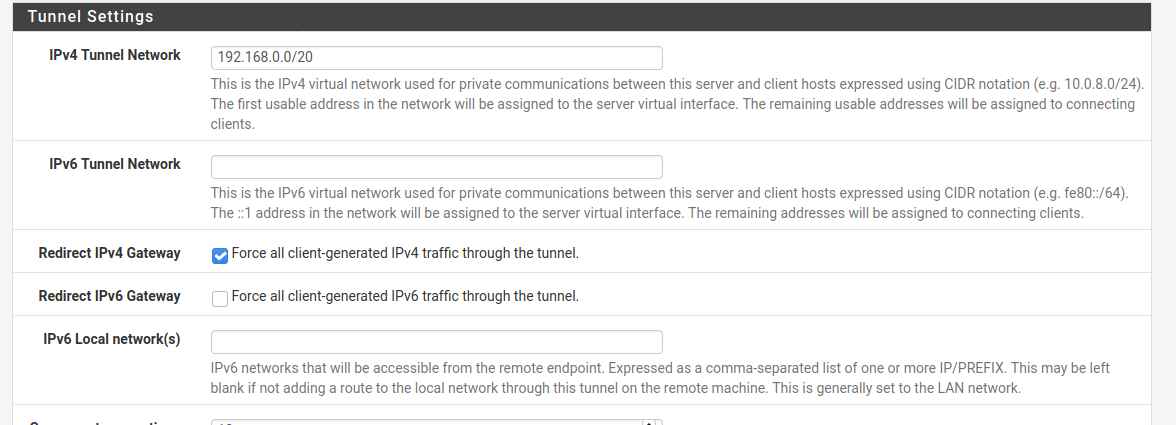
And with unchecked, I've tried as well, nothing happens different on my Ubuntu 20.04 OpenVPN client when I change it...
-
@marvosa Finally, here's the article from Digital Ocean on how to connect to their private "VPC" network via another server on their network...
https://www.digitalocean.com/docs/networking/vpc/resources/droplet-as-gateway/ -
@marvosa Also, you said 192.168.0.0/20 is subject to routing issues, would 172.16.0.0/20 be a better range for the OpenVPN server tunnel network? And, if so, should I re-create the VPN server or just update the existing one with that tunnel network?
-
@jacobisreal said in OpenVPN clients can't ping LAN:
Can ping 10.116.0.3 (pfSense LAN address) with no issues
CAN NOT ping 10.116.0.2 (another server on private LAN) or any other LAN server when connected to VPNIs the default gateway set correctly on the remote server to 10.116.0.3?
Do a simply test with Diagnostic > Ping.
Ping the server with default options. Should get replies. Then try again with source = OpenVPN@jacobisreal said in OpenVPN clients can't ping LAN:
Also, you said 192.168.0.0/20 is subject to routing issues, would 172.16.0.0/20 be a better range for the OpenVPN server tunnel network?
A /20 provides 4k IPs. Do you really need these? I assume, the VPN is only for your admin purposes, so you can go better with a /28.
192.168.0.0 is in generally verey common, 172.16.0.0 as well. If you have multiple clients better use something like 172.28.47.0/24. -
@viragomann Pinging with default to the LAN 10.116.0.2:
PING 10.116.0.2 (10.116.0.2): 56 data bytes 64 bytes from 10.116.0.2: icmp_seq=0 ttl=64 time=2.567 ms 64 bytes from 10.116.0.2: icmp_seq=1 ttl=64 time=0.558 ms 64 bytes from 10.116.0.2: icmp_seq=2 ttl=64 time=0.630 ms --- 10.116.0.2 ping statistics --- 3 packets transmitted, 3 packets received, 0.0% packet loss round-trip min/avg/max/stddev = 0.558/1.252/2.567/0.931 msPinging from OpenVPN to 10.116.0.2:
PING 10.116.0.2 (10.116.0.2) from 192.168.0.1: 56 data bytes --- 10.116.0.2 ping statistics --- 3 packets transmitted, 0 packets received, 100.0% packet lossI do have multiple clients, this is for a non-profit project where I need to grant access to the 10.116.0.0/20 network from the OpenVPN which is publicly addressed and open on the WAN. I could change the OpenVPN tunnel address to what you suggest, no problem. But no matter what I do, I can't reach the internal LAN from OpenVPN.
Thanks for your input, let me know what you think. I do not need 4k addresses, but I might need a couple hundred... I won't make any changes until I hear back. Did you review the link about Digital Ocean requiring a "gateway" machine to access their network? -
@jacobisreal
If you really need a /20 use something like 172.28.32.0/20. Ensure that you enter the network address here.Yeah, the VPN tunnel network has nothing to do with the access.
So ensure that the gateway is set correctly on the destination server and that it doesn't block the access by its own firewall. -
As far as the local network, did you mean adding 10.116.0.0/20 or 10.116.0.3/20 as you stated above?>
Yes, my apologies, 10.116.0.3/20 was a typo, I meant 10.116.0.0/20. I made the correction on my post.
On OPT1, you'll want to change the protocol to any.
Also, you said 192.168.0.0/20 is subject to routing issues, would 172.16.0.0/20 be a better range for the OpenVPN server tunnel network?
In a routed tunnel, all subnets have to be unique and 192.168.0.0/20 covers a series of common ranges for SOHO routers. This means any client whose LAN within 192.168.0.1 - 192.168.15.254 will have routing issues when trying to reach your LAN. So, you'll want to change it to something completely uncommon like @viragomann suggested. And a /20 is entirely too wide unless you really do have 4000+ clients. Trim it to fit your client base.
I would verify the mask and gateway on 10.116.0.2 are what you're expecting. Is it using PFsense as the gateway? (i.e. the IP assigned to the LAN interface). Also, for grins and giggles, I would re-verify the mask on your LAN adapter.
-
@viragomann I've temporarily disabled the firewall on the LAN server 10.116.0.2 and there is no gateway defined on it because Digital Ocean doesn't require a gateway for VPC networks. It's an Ubuntu 20.04 server, here's the netplan:
/etc/netplan$ cat 50-cloud-init.yaml # This file is generated from information provided by the datasource. Changes # to it will not persist across an instance reboot. To disable cloud-init's # network configuration capabilities, write a file # /etc/cloud/cloud.cfg.d/99-disable-network-config.cfg with the following: # network: {config: disabled} network: version: 2 ethernets: eth0: addresses: - 142.xxx.xxx.xxx/20 - 10.10.0.10/16 gateway4: 142.x.x.x match: macaddress: 5a:xx:xx:xx:xx:xx nameservers: addresses: - 67.207.67.3 - 67.207.67.2 search: [] set-name: eth0 eth1: addresses: - 10.116.0.2/20 match: macaddress: xx:xx:xx:xx:xx:xx nameservers: addresses: - 67.207.67.3 - 67.207.67.2 search: [] set-name: eth1The server I'm trying to reach also has a public internet address, but it's the VPC private address of 10.116.0.2/20 that I'm trying to reach from the OpenVPN server on pfSense that has a LAN address of 10.116.0.3/20. There's no gateway to define.
-
I've temporarily disabled the firewall on the LAN server 10.116.0.2 and there is no gateway defined on it because Digital Ocean doesn't require a gateway for VPC networks. It's an Ubuntu 20.04 server, here's the netplan:>
There's your issue. In order for 10.116.0.2 to reach a network outside of it's LAN subnet (e.g. the OpenVPN tunnel network), there has to be a default gateway set. Configure the gateway to the PFsense LAN IP.
Any device you want to reach over OpenVPN will need PFsense as its gateway.
-
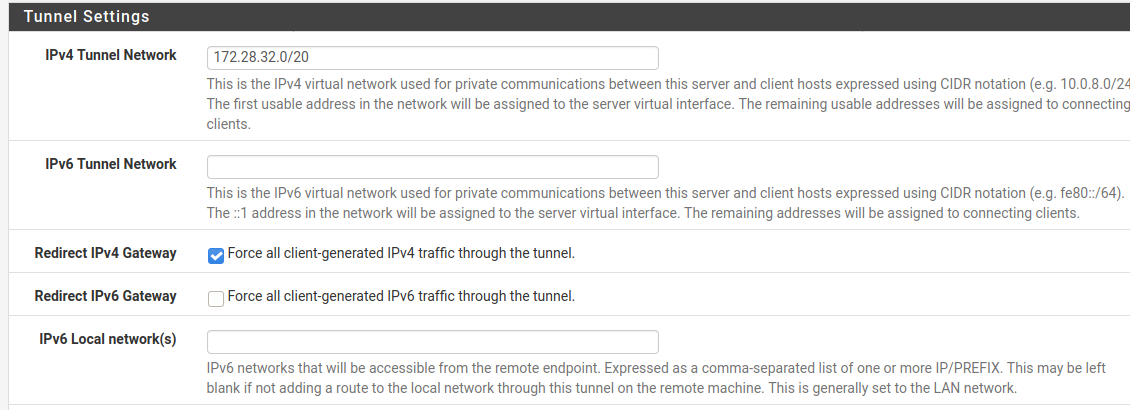
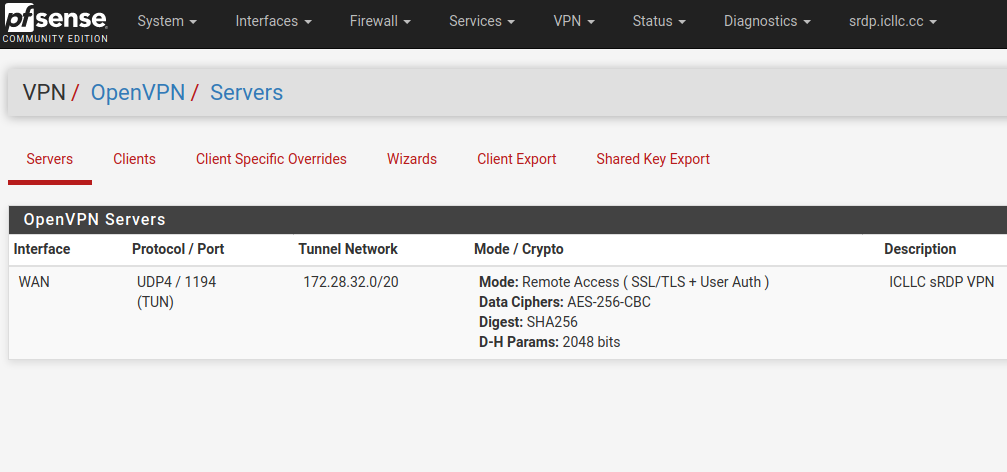
@marvosa Updated OpenVPN tunnel as you suggested.
-
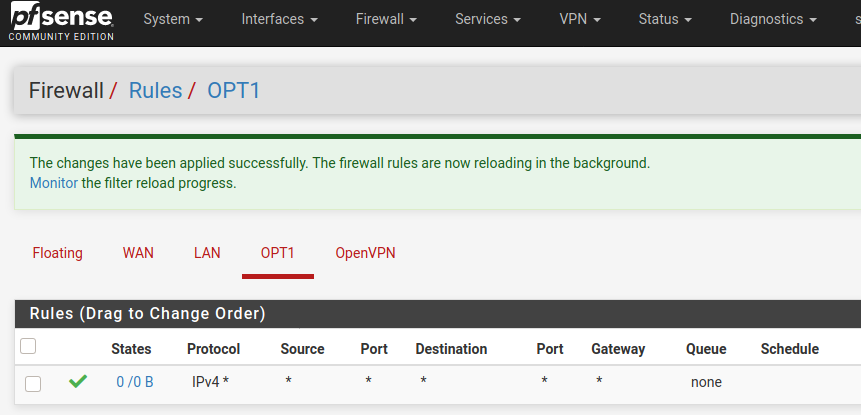
@marvosa Updated OPT1 protocol to any:
-
@marvosa said in OpenVPN clients can't ping LAN:
I've temporarily disabled the firewall on the LAN server 10.116.0.2 and there is no gateway defined on it because Digital Ocean doesn't require a gateway for VPC networks. It's an Ubuntu 20.04 server, here's the netplan:>
There's your issue. In order for 10.116.0.2 to reach a network outside of it's LAN subnet (e.g. the OpenVPN tunnel network), there has to be a default gateway set. Configure the gateway to the PFsense LAN IP.
Any device you want to reach over OpenVPN will need PFsense as its gateway.
I can't set the gateway on that server - it's a private VPC (virtual network) inside Digital Ocean's network. The address 10.116.0.2 is the address they assigned the box on the private VPC on their side. I've read several articles that state I need a NAT rule to access that box - here's the post I read:
https://mohsensy.github.io/sysadmin/2019/06/21/secure-access-to-digital-ocean-resources-using-openvpn.html
And:
https://forum.netgate.com/topic/63243/openvpn-server-openvpn-client-and-nat/2?_=1614660188717Digital Ocean support docs state that there must be iptables rules, but pfSense doesn't use iptables - see:
https://www.digitalocean.com/docs/networking/vpc/resources/droplet-as-gateway/ -
Can you guys please take a look at their documentation? Here's the link:
https://www.digitalocean.com/docs/networking/vpc/resources/droplet-as-gateway/
It doesn't make any sense to me... If pfSense already is configured out-of-the-box to forward, and NAT rules are automatic, then this should just work. I'm pretty smart, I've tried all kinds of configurations, re-imaged the box and tried again all night. There has to be some kind of NAT I'm missing per their documentation. Ahh! :) Thank you for all your help, friends!
-
@jacobisreal
So you can only go with masquerading. However, I'd not recommend that for multiple VPN users.To activate it, go to Firewall > NAT > Outbound. If it is still in automatic mode, switch to hybrid and save that.
Add a new rule:
interface: LAN
protocol: any
sourec: any
destination: any
Translation: interface addressDirty, but may work.
-
@viragomann Like this: