Need help understanding VLANs and pfSense
-
@striker-pl I removed the WiFi router from the mix but it didn't resolve the issue.
Here's the new config.
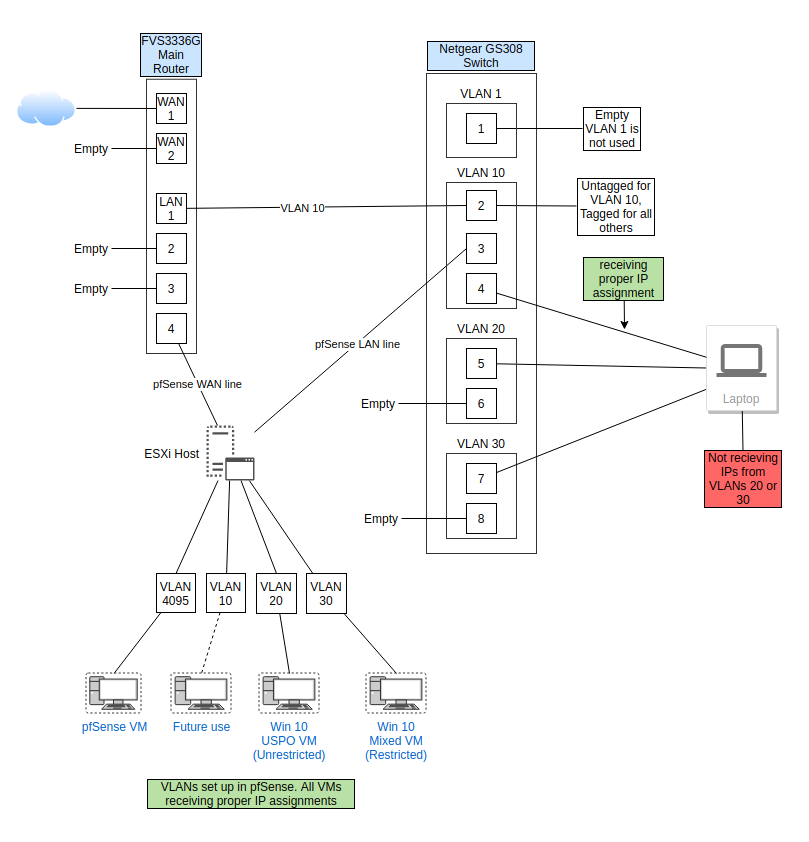
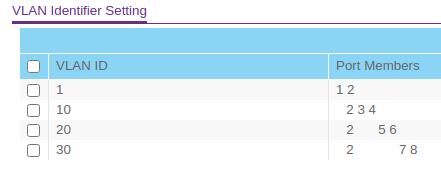
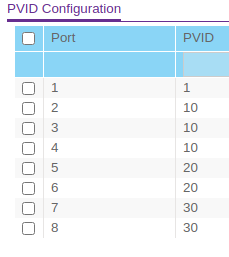
One thing I think I forgot to mention is that I still have DHCP enabled for VLAN 10 on the FVS336G. pfSense is handling DHCP for VLANs 20 and 30.
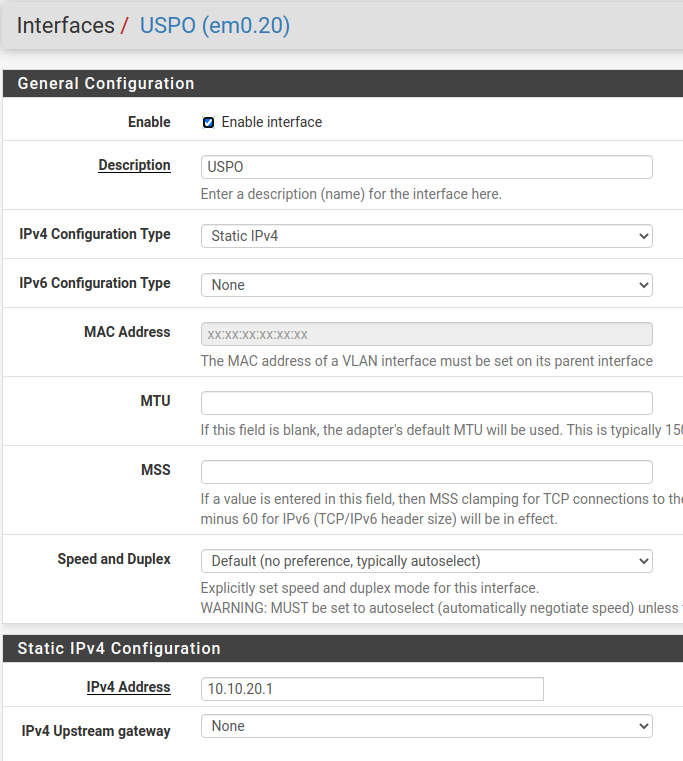
I have VLAN 10 enabled in pfSense, but have the IP config set to none and have not set up a DHCP server for this VLAN. Is that my problem? Should I disable DHCP on the router and just let pfSense handle it? I was afraid to do that, since I'm not getting VLAN info over the physical lines and that's what my laptop is connected to.
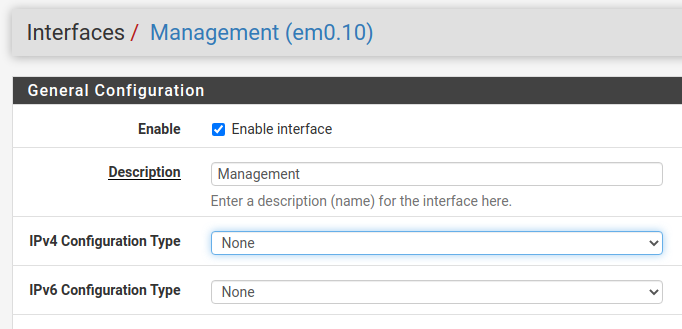
-
@troybdex you should be able to use whatever DHCP server you want on each VLAN.
Do you have an IPv4 address setup for VLAN20 or VLAN30 in your interface management screen?
I see that you don't have one setup for VLAN10.
-
-
@troybdex and the IPv4 Address is set to /24 right?
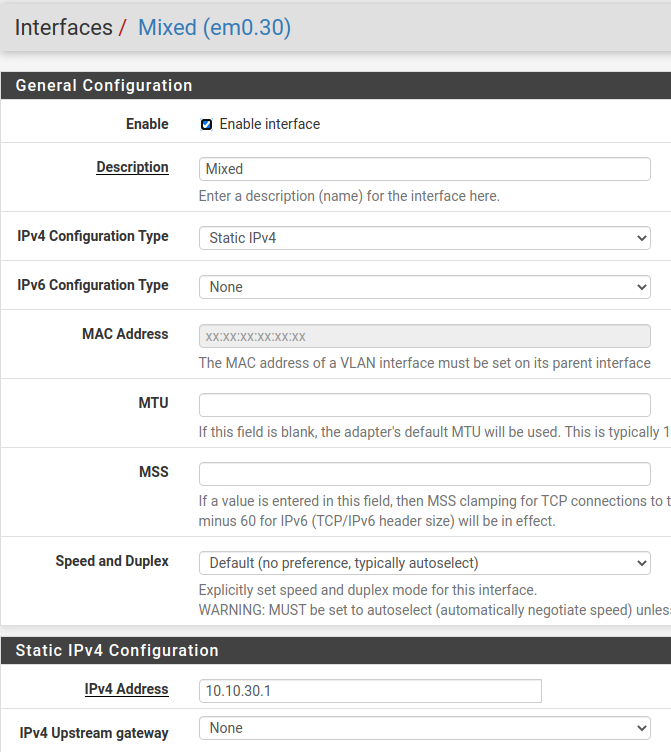
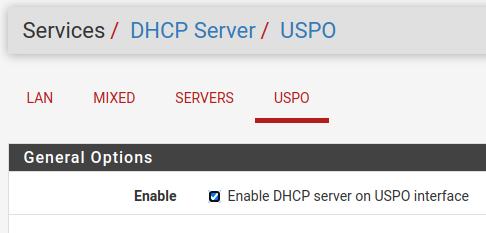
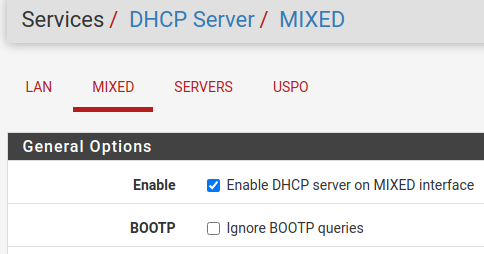
Just to confirm, your DHCP servers are Enabled on VLAN20 and VLAN30? You can configure them, but there is a separate Enable checkbox that needs to be set as well.
-
@striker-pl yep. Both have a check in the "Enable DHCP server on MIXED interface" box. I am getting addresses from both on my VMs. I have these VLAN's set up on my router, but they are disabled.
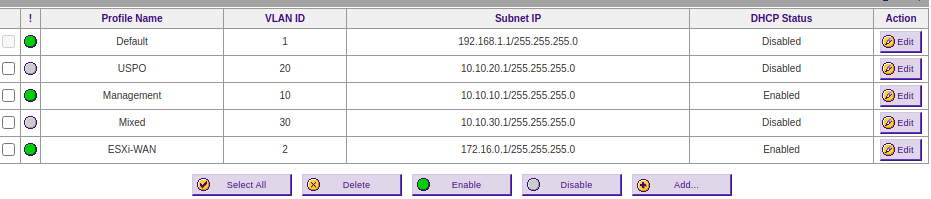
-
-
So you understand when you have tags going into esxi, if you don't set 4095 on the vswitch - the tags will be removed.
If you don't want esxi messing with tags you need to set 4095 on any vswitch the vlan tags will cross.
You have that set but what about those other vlans you have on esxi? How do you have that connected into pfsense to route? Your esxi breakout doesn't show any detail on how you have your pfsense vm setup tied to what vswitches in esxi, which is connected how exactly to your physical network.
And looks like you have the same IPs setup on you router, that you have as pfsense IP.. 10.10.20.1, 10.10.30.1 for example? You can not do that on the same L2.. Or your going to have dupe IP issues..
To honest I have no idea what your wanting to accomplish here.. If your going to have 2 routers. and pfsense is going to be downstream of your other router. Then they would be connected with a transit, and that upstream router wouldn't have settings for any of those vlans - only routes via the transit to get to them via pfsense.
-
@johnpoz Thanks for the reply. Yes, I understand that.
Here is my ESXi config. This has not been modified since my original post. You can ignore VLAN 40 as it is not in use at the moment. VLAN 10 is also not in use, but when I had a vm tied to it, it got the proper IP address. All other VMs are receiving an IP address in their respective VLAN range.
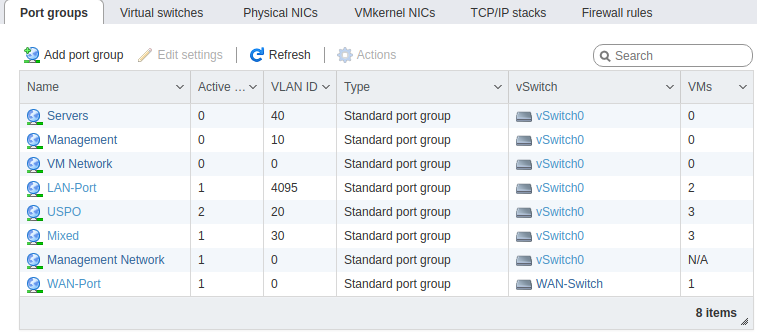
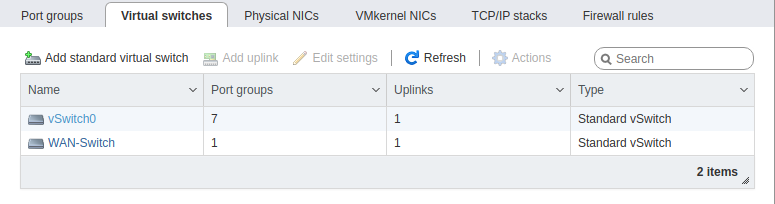
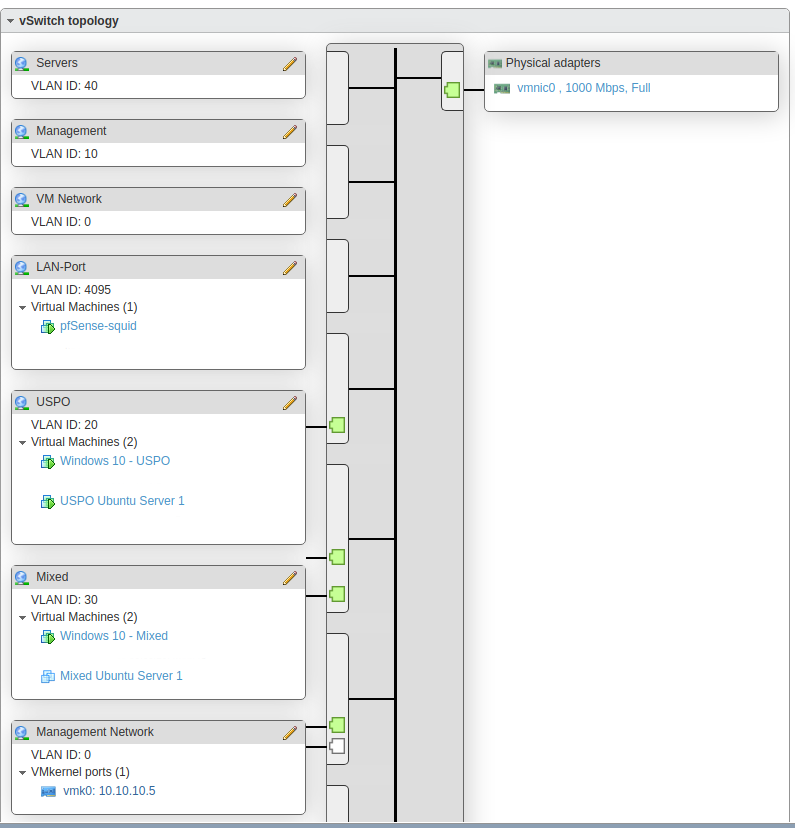
Could this issue with the configuration on my physical laptop? I am running Ubuntu Mate 20.04. Is there anything I need to configure on there before this will work. I don't have a physical Win 10 Eval box, but can build one for testing if need be.
-
And that makes no sense at all.. Pfsense is not going to be able to route any of those..
-
@johnpoz As I stated in my previous post, VLANs 20 and 30 are configured on the router but are disabled. The pictures verify this.
In the end I will have a physical and virtual network that pass the same VLAN tags. I need VLANing to work with my routers, switches, physical desktops and servers and virtual desktops and servers.
-
Yeah - well what you have there isn't going to do that.
What do you want to route between your vlans? Doesn't matter if they are on virtual, physical or both..
You still need something to route between them - is that going to be your upstream router, or pfsense.. If its pfsense it has to have an interface in that L2.. Are you trying to send traffic back out to physical just to come back in another physical via your 4095 vswitch? So that pfsense can see the tags?
What you have there is via the technical term - a MESS ;)
-
@johnpoz said in Need help understanding VLANs and pfSense:
What you have there is via the technical term - a MESS ;)
Yeah, it's a hot mess. The problem is, I have no clue what I'm doing and I have 4 more months to do it. Thankfully, management is patient with me, as they know even less than I do.
Are you trying to send traffic back out to physical just to come back in another physical via your 4095 vswitch? So that pfsense can see the tags?
To be honest, because my networking skills are non-existent, I don't know.
We're a small office, with three local employees, myself included, and six remote. Currently, there is no centralized network management. Everything is done on the local computer or server. It's my job to transition the network to one that is centrally managed and that is secure.
The company recently - before I was hired - set up two ESXi hosts and migrated some of their physical servers to them. One host is for USPO and one for Mixed. The USPO network is for our government work that can only be accessed by US citizens. The Mixed network is for everyone else. Mixed cannot see USPO computers, applications, etc. but USPO is allowed to see everything. Right now, all of the network segmentation is handled on the routers, using separate subnets but not using VLANs. The boss would like USPO and Mixed each on their own isolated VLAN. The company also has four or five additional servers that will eventually be virtualized. However, a few physical servers will remain indefinitely and those must also be on the VLANs. Then, of course, there are the physical desktops and laptops we use to access all of these systems, which also need to be on their respective VLANs.
In the end, I need to have that segmentation and to have all of it work with Active Directory. Eventually, I need to throw a VPN and a DMZ into the mix. I figured I would start with the perimeter firewall first and work my way back from there. Since pfSense can also be a router, I figured I would run DHCP from pfSense rather than having to configure each and every physical router, switch and host. I realize that some router/switch configuration may be necessary.
So, basically, all traffic, regardless of location or whether it is physical or virtual, needs to transit a VLAN. As to how that is accomplished...that's why I'm here. I'm open to any ideas, better solutions and/or advice.
Please note that the setup I have shared is on a test network that is isolated from our production network, so I have a lot of room for play.
If its pfsense it has to have an interface in that L2
I'm not entirely sure what you mean but all of my VLANs are assigned to the LAN port in pfSense.
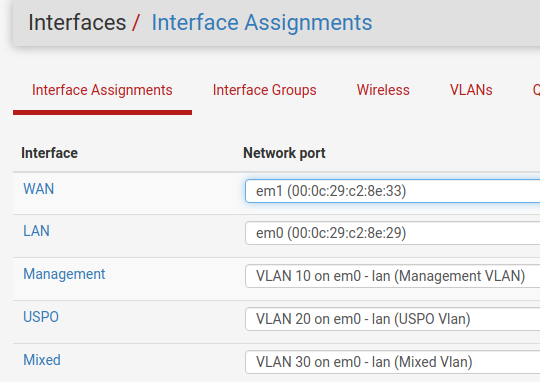
-
@johnpoz is this something that is possible?
-
@troybdex I was in a similar boat. Check this link out: https://nguvu.org/
It did help me achieve something close to what you want (not exact though), but going through you get few tips about VLANS, separation, and rules. He also has examples of couple switches and how he set up the tagging on them. Note, that in his configuration, pfSense was managing all.I got the external switch to work with those. That said, I am stuck in a different problem (in my post), where I would like to have different ports on the SG3100 to have different VLAN groups using pfSense switch configuration.
-
@smik67 Thank you so much! I will definitely read through those articles. Sorry about your problem. I hope you can figure it out.
Troy
-
@troybdex said in Need help understanding VLANs and pfSense:
@johnpoz is this something that is possible?
What your wanting to do run pfsense on virtual is quite easy, and yes you can have your vlans on both virtual or physical and both, etc.. None of it is overly complicated.
But you do need to understand how tagging works, and how your VM host does it, and how your switches do it. And you need to understand what your trying to accomplish.
I am not sure from what you have provide exactly what your trying to accomplish. If you want to route on pfsense via virtual machine - sure that is fine. is it going to be a downstream router? Your edge router with something else downstream, the only router? And if your going to have more than 1 router, then you need to understand how to connect these routers together with a transit network. And how to route between the two routers.
And you need to understand if you want your vm host to actually handle all the tags or if you want pfsense to do it - or if you want to do a combination where pfsense sees some tags, and other times your VM host does it..
If you do not understand any of this - then yeah its going to be a steep learning curve.. If you want pfsense to see tags and handle the vlans, then with esxi you have to set 4095 as the vlan ID on the port group or vswitch.. Then how you tie that to your switching setup and how you tag or don't tag for your different switch ports. And which physical port in the vm host is tied to which vswitch and or port groups..
The simpler solution would be to just do all the vlans in esxi, and let it handle the tags - and then just create virtual interfaces on pfsense tied to each port group that is in each vlan. The connect those port groups to the correct physical ports in your switching infrastructure.
-
@johnpoz Lucy! You got a lot a readin' to do.
Anyway, thanks for the help. I'll take it all into consideration as I venture onward.
-
Happy to help, I ran pfsense on esxi for many years.. I currently do not have esxi setup here, or any access where I could post screenshots on how it can be done, etc.
But happy to answer questions..
The biggest issues I see new users with multiple routers having is not understanding why they run into problems when they try and have hosts on what ends up being their transit network.
And new users to esxi not understanding how it works with tags, or doesn't work ;)
But when it comes down to it - tag is a tag is a tag.. But tags are only need when you want to carry more than 1 vlan over the same wire.