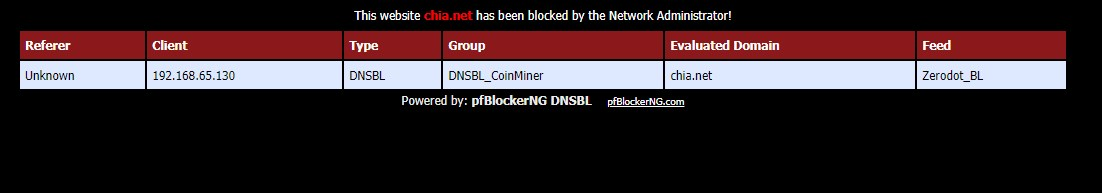
help to unblock chia
-
Trying to access chia.net from either firefox or chrome on any platform and keep getting
I have tried disabling ERR_CONNECTION_REFUSED
I have tried disabling the protection in both chrome and firefox.I can't see anything in the logs of either pfBlockerNG or suricata
If i take my mobile off wifi it is reachable. So it is definitely from my network. -
@gwaitsi said in help to unblock chia:
Trying to access chia.net
Hi,
Dangerous waters...hihihihi, - it will certainly block

+++edit:
try this first...
-
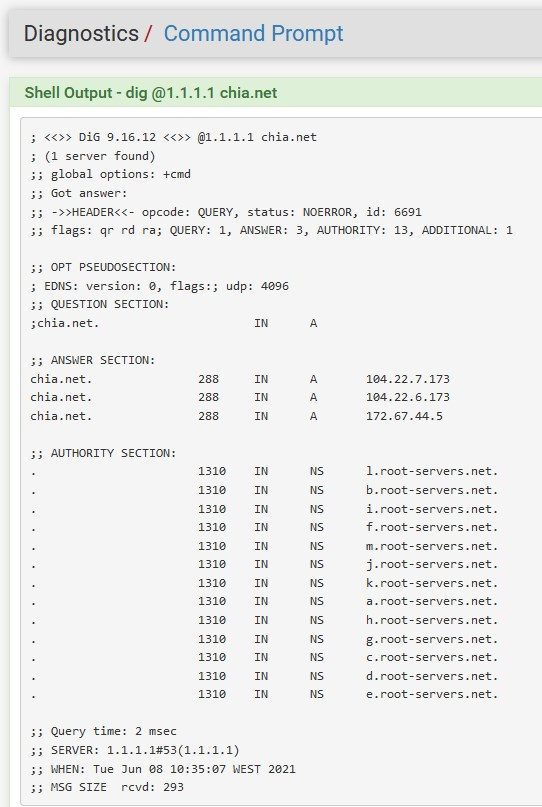
@daddygo i can traceroute and dig from clients and pfsense no problems. it is http/s that is being blocked for some reason
Even with the ubuntut tor browser, i am getting server 503 unless i turn off both pfblockerng and suricata.
if I disable pfblockerng and suricata and reboot, i still get blocked by normal browsers, but the tor browser does not block
-
@gwaitsi said in help to unblock chia:
it is http/s that is being blocked for some reason
what about your ISP? (or transit network)
from our system (behind pfSense) from another client without coinminer DNSBL...
(from Hungary)
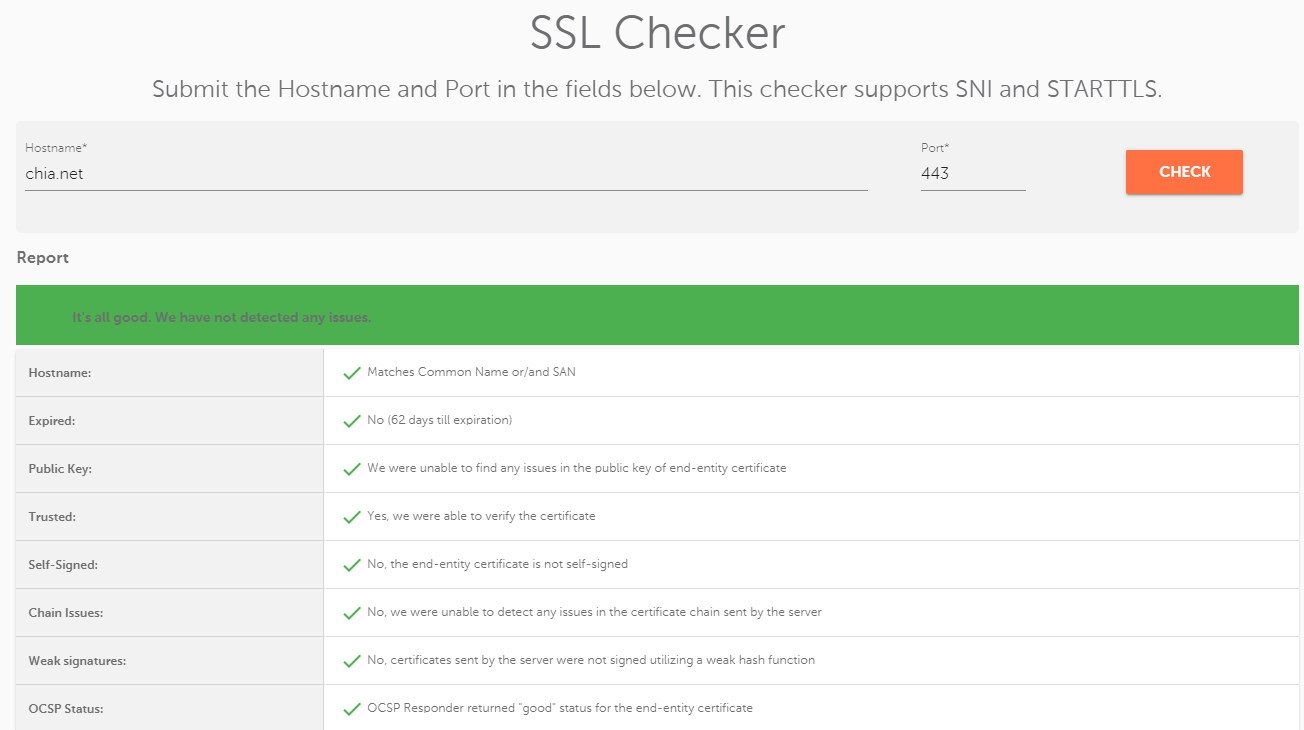
++++edit:
from Portugal w/o DNSBL also...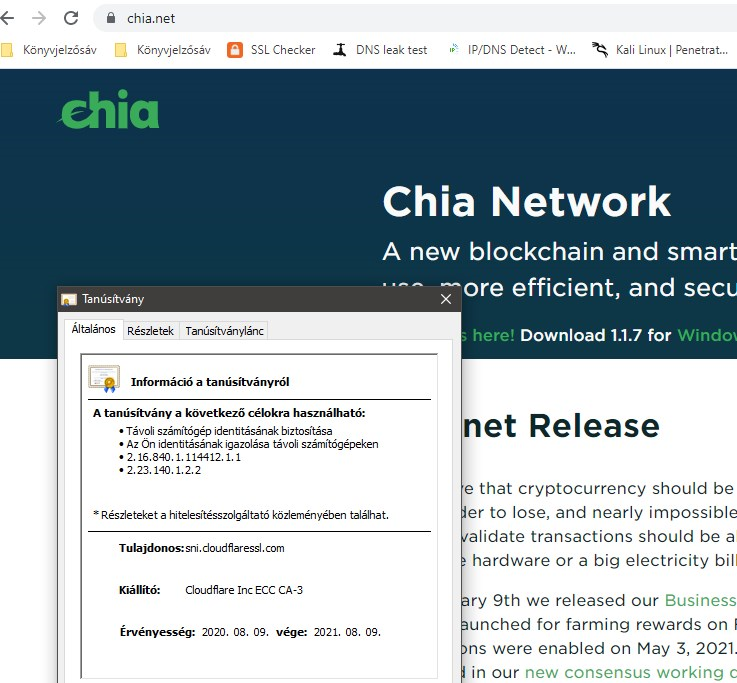
-
I figured out, on firefox, had to enable DNS over HTTPS to make it work.
Can't seem to find the same setting in chromium.But why is it so?
-
@gwaitsi said in help to unblock chia:
I figured out, on firefox, had to enable DNS over HTTPS to make it work.
Bad, bad, bad....

https://forum.netgate.com/topic/157500/blocking-dns-over-https-seems-the-only-way-is-to-fire-a-shotgun-at-it/29
Our and NGFW's great enemy, the DoH - then why use pfBlockerNG...????
by the way, here:
FireFox:
about:config
network.trr.mode 5UNBOUND Custom:
server:
local-zone: "use-application-dns.net" always_nxdomain
local-zone: "cloudflare-dns.com" staticChrome:
chrome://flags/#dns-over-https
+++++++++++edit:
I will fight with the DoH, as long as I live!
(so, since you can connect via DoH, this makes it clear that your pfSense setting is filtering out the page)
-
@daddygo said in help to unblock chia:
(so, since you can connect via DoH, this makes it clear that your pfSense setting is filtering out the page)
Can't be. I disabled pfblockerng and suricata and rebooted.
It was still blocked, until i stumbled on the dns over ssl on firefox.My unbound is fowarding to 1.1.1.2. could it be;
1.1.1.2 blocks chia.net
dns over ssl is forwarding to 1.1.1.1 and that it why it is working ? -
@gwaitsi said in help to unblock chia:
1.1.1.2 blocks chia.net
Hey Bro,
 , you have given yourself the answer...
, you have given yourself the answer...1.1.1.2 DNS prefiltered by CF
+++edit:
push the stuff to 1.1.1.1 / 1.0.01 with 853 (DoT)+++edit2:
by the way, IPS/IDS (Suricata / Snort) does nothing to do with a regular (normal) HTTPS, pfBlockerNG-devel does not touch them if you do not filter with lists
-
- i have dual wan and had 1.1.1.3 / 1.0.0.3 in the general settings to each wan.
- i have unbound setup with 853 forwarding.
- i have dns redirected to local host
how can i make a DNS exception a specific machine/s to 1.1.1.1, but should be reusable, rather than hard coded e.g.
is there a way to do this forward for a specific VLAN and/or IPserver: # forward-zone: # name: "." # forward-ssl-upstream: yes # forward-addr: 1.1.1.1@853 # forward-addr: 1.0.0.1@853 -
@gwaitsi said in help to unblock chia:
how can i make a DNS exception a specific machine/s to 1.1.1.1
Hmmmm, Okay
you complicate it well,.... instead of using pfBlockerNG-devel + well thought out lists
1.1.1.3 / 1.0.0.3 also performs malware and adult content filtering
I for one like to tell myself what I want to access/view and have the control in my hands and not CloudFlare's
this would be my first approach, but there may be a faster, better way...
set the upstream server 1.1.1.1 also, (general tab)
create a VLAN interface for 1.1.1.1 DNS client(s) only
(if you are thinking about in VLAN - good, so the network is separated)Unbound (custom):
access - control (allow - deny for subnet(s))
- forward-zone: / forward-addr
this will not work from GUI (I think...?..!), you have to edit unbound.conf
these may help:
https://calomel.org/unbound_dns.html
https://wiki.archlinux.org/title/Unbound -
Just a couple of pointers. Mixing filtered and non-filtered dns is going to be problematic.. As you have already run into it seems.
If your going to point a client to more than 1 NS for dns - you need to be sure that these NS used provide the same info. Be it filtered or non filtered.. Since you never know which NS a client might query for dns.
Bad idea to point a client to local dns and external dns - be it filtering involved or not, since external is never going to resolve your internal resources.
Be it you resolve, or forward or use doh or dot when you forward. You need to make sure that any possible dns a client can query can and does return what your interested in. Filtered or not filtered, local or external. That being a pc on your network, or pfsense doing dns for your clients. If you list multiple ns that pfsense can forward to - you need to make sure where you forward will be able to resolve the same stuff filtered or not, etc.
Also if your going to forward, dnssec should not be enabled.. dnssec is a feature of a resolver. if you want dnssec to be used - then forward to dns that support this and it will use dnssec when it resolves. Forwarding somewhere is either going to do dnssec already, or not - you asking for it doesn't provide anything other than wasted dns queries.
-
@johnpoz i think you misunderstood.
- DNS is NAT forwarded to my pfsense box.
- unbound is forwarded to 1.1.1.3
My question is, can I tell unbound to use a different dns server, for queries from a specific VLAN.
In other words,
DNS 1.1.1.3 -> VLAN (LAN, IOT, MEDIA) - default
DNS 1.1.1.1 -> VLAN (ADMIN)i.e. using forward zone, view filters, or something
p.s. i don't have DNSSEC on pfsense enabled. i was referring to the setting within firefox, which i turned off once i validated it was the cloudfare DNS that was filtering the site.
-
@daddygo i don't use pfblocker for the dns filtering because would take too much time. especially when cloudflare will do all the work. which is could for the family environment i have. p.s. thanks for the help in getting to the root cause. i will look up these resources
-
@gwaitsi said in help to unblock chia:
i don't use pfblocker for the dns filtering because would take too much time.
perhaps, I saw you write that you use

it's the best solution(! in my reading) , setting up the new version takes 5 minutes with lots of predefined listsI understand that children......hmmmm
but, the CF (1.1.1.3) may let you pass on content that you regret afterwardsit's safe if you're in control
BTW:
@johnpoz "Mixing filtered and non-filtered dns is going to be problematic."
nope, John did not misunderstand you and is right in what he wrote
+++edit: (for pfBlockerNG)
https://www.vikash.nl/setup-pfblockerng-python-mode-with-pfsense/ -
@daddygo I looked at the article, made some tweaks to match and set the default dns to 1.1.1.1
On my J1900 it is a challenge.
With only shallalist and a 512mb temp in memory, I am at 64% of 8Gb.I probably need to optimize the lists. Interestingly,
xxx - brings me the banner like you first posted
xhamster - brings me SSL_ERROR_INTERNAL_ERROR_ALERTis there a recommendation on feeds to use for good family protection
thanks again for the support guys.
-
@gwaitsi said in help to unblock chia:
On my J1900 it is a challenge.
this "iron" is more than enough for your target... (home privacy and security)...
we have several endpoint pfSense installations (https://www.pcengines.ch/apu4d4.htm) that can handle large DNSBL lists with 4G RAM, just don't overload your "box" with unnecessary heavy apps (Squid for home, IPS for home, thousands of OpenVPN tunnels)
my answer to the question of the list, it all depends on what you want to achieve, there can be very different goals
(f.e.: I have at least 10 variations for lists, the first is always to keep the bad guys out, the second is to keep the individual goals)for XXX, I would suggest the following, just off the top of my head, which was in my collection:
(but there are many other good lists for this purpose)https://raw.githubusercontent.com/Clefspeare13/pornhosts/master/0.0.0.0/hosts
https://raw.githubusercontent.com/chadmayfield/my-pihole-blocklists/master/lists/pi_blocklist_porn_all.list@gwaitsi "xhamster - brings me SSL_ERROR_INTERNAL_ERROR_ALERT"
(I see everyone is into the good stuff)just do the right things: - Diagnostics / States / Reset States

-
Where is chia.net being filtered by 1.1.1.3??
$ dig @1.1.1.1 chia.net +short 104.22.7.173 172.67.44.5 104.22.6.173 $ dig @1.1.1.3 chia.net +short 104.22.7.173 104.22.6.173 172.67.44.5 Now other stuff is filtered.. $ dig @1.1.1.3 www.youporn.com +short 0.0.0.0 -
@johnpoz said in help to unblock chia:
chia.net being filtered by 1.1.1.3
Yup, that's right, it wasn't checked...
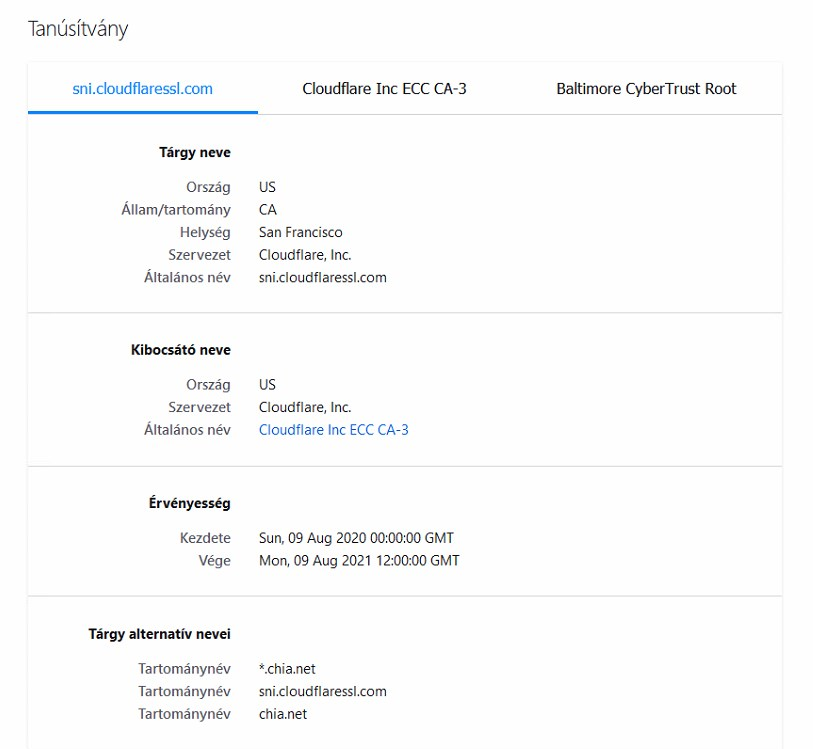
(just looked it up I also, 1.1.1.2 does not filter this site
would be strange as it uses CF cert. - they don't shoot at "house rabbits"this also shows there are other problems there
+++edit:
originally the discussion was about 1.1.1.2@gwaitsi "My unbound is fowarding to 1.1.1.2. could it be;
1.1.1.2 blocks chia.net" -
@johnpoz I rechecked it.
1.1.1.1 / 1.1.1.2 / 1.1.1.3 all resolve and can traceroute for chia.net
1.1.1.2 / 1.1.1.3 https doesn't work to chia.net (but does if it use firefox dns over ssl settings to 1.1.1.1)I have a good config. I am using 1.1.1.1 and pfblocker for the lists).
Three observations;
-
the dnsbl lists don't load on boot. Waiting to see if they load on the next scheduled cron job. * it updates on the first cron run. wouldn't it make sense to run all cron jobs on boot?
-
some results e.g. xhamster get return ssl errors rather than a pfblocker banner but the net effect is the same, the site is blocked.
-
the results are not filtered from search (I use duckduckgo). ** this was the reason from memory I went for the 1.1.1.3 to begin with
So, looks like I have come the full circle.
If I want the results to be removed from the search, I need to use cloudflare family.But then, I am stuck with not being able to access https://www.chia.net
** interestingly, with pfsense set top 1.1.1.1 i set firefox to dns over ssl with 1.1.1.3 and it works.
so, something on my pfsense is causing https://www.chia.net to break when I use either 1.1.1.2 / 1.1.1.3 as the dns. but doesn't seem to happen to anything else. -
-
@DaddyGo this gives a better result for me, because xhamster, porn etc from any browser simply returns no results and I don't have to worry about maintenance. I wonder if there is still any point to also use dnsbl as it only uses additional resources.