Blocked IGMP packets flooding my logs -- IGMP snooping???
-
Hi,
I have a firewall rule set to block everything that I have not expressly allowed through my WAN interface. I'm seeing lots of IGMP packets getting blocked from Source: 99.239.247.53, which is outside of my network. The destination is 224.0.0.1, which I believe is a reserved IP range for multicast.
How are these packets able to be directed to my network if they have a destination of 224.0.0.1?
Also, don't know anything about IGMP Snooping other than it's a technique used by hackers to gain information, but is it possible this is a hacker trying to get information on my systems? I don't understand why this random IP would be sending IGMP packets directed towards my network as I do not host any public servers or services. I uploaded a snapshot from my log to show what I'm seeing...
Any thoughts on what might be happening here?
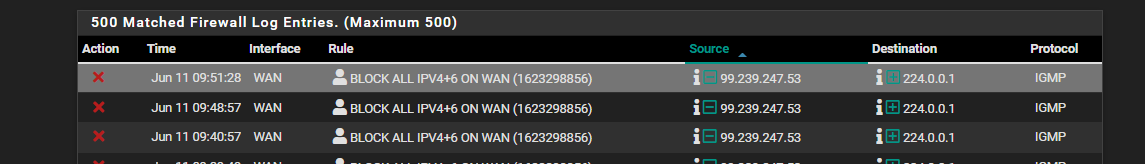
-
Aren't mDNS (multicast DNS) packets sourced from unicast address, port 53 to a few different mcast addresses? If so, and assuming your WAN interface is some kind of broadband (say cable), it's possible the something upstream is configured to allow the multicast traffic down the shared pipe so it hits your WAN.
If something local has configured your WAN to be part of that mcast group, the packets would also be routed from upstream to your WAN
Could they be nefarious? Maybe
Could they be begnin? Maybe
You could do a packet capture and try and analyze them.You could do a whois on the source IP, if it's from one of your neighbors it would probably be in a block of IPS assigned to your ISP.
My opinion, others may have a different opinion.
EDIT:
Quick look mDNS look to be sourced from port 5353 destined for 224.0.0.251. -
@spookymonkey said in Blocked IGMP packets flooding my logs -- IGMP snooping???:
I don't understand why this random IP would be sending IGMP packets directed towards
That IP is owned by
NetRange: 99.239.246.0 - 99.239.247.255 CIDR: 99.239.246.0/23 Parent: ROGERS-COM-HSD (NET-99-224-0-0-1) Customer: Rogers Cable Inc. ETOB (C02173521)Is Rogers your ISP?
What it amounts to is spam from your local ISP most likely - them not correctly filtering multicast.
If your concerned contact your ISP about it. The only way you would be able to see such traffic if your isp is sending it, or another one of their clients is sending it.
if it is filling up your logs vs interesting stuff your wanting to see, I would just stop it from being logged. Create a rule to block it and not log it above your Bock ALL rule.. BTW you understand pfsense does that out of the box anyway. There is little reason to create your own rule that logs, since that is what the default deny rule does anyway.
-
That's definitely someone on your subnet? What's your gateway address? I'm also on Rogers, but in Mississauga, not Etobicoke (Toronto) and don't see anything like that. My gateway is 99.246.124.1 and ends in .1, as is typical.
-
@johnpoz Thanks for the info! Yup on Rogers... Didn't realize pfsense auto blocked/logged by default so that's good to know. But I am still a tad paranoid so I think I'm going to keep them in there anyway lol...
-
@jknott gateway is 99.241.10.1 so different from yours.. ever since I installed pfsense and ditched my home router, I can barely sleep at night after seeing the traffic logs... is it normal to constantly be bombarded by external IPs on various ports??? When I research the ports they're trying to use it usually turns up a vulnerability associated to the port.... lots of them are directed at DNS port 53 , but I don't operate any public servers or services so not sure why random public IPs would be sending requests to my IP on port 53...
-
@spookymonkey said in Blocked IGMP packets flooding my logs -- IGMP snooping???:
constantly be bombarded by external IPs on various ports???
Yes the internet is a noisy place.. No different than when you had your soho router.. Your soho router wasn't just showing you it in a log..
random public IPs would be sending requests to my IP on port 53...
Prob looking for open dns resolver that they could use in a dns amplification attack.
-
BTW - I had set a sniff on my wan to look for the igmp.. And seeing it as well
10:06:37.270045 IP 10.205.128.1 > 224.0.0.1: igmp 10:08:42.277695 IP 10.205.128.1 > 224.0.0.1: igmp 10:10:47.288287 IP 10.205.128.1 > 224.0.0.1: igmp 10:12:52.297471 IP 10.205.128.1 > 224.0.0.1: igmp 10:14:57.307060 IP 10.205.128.1 > 224.0.0.1: igmp 10:17:02.317600 IP 10.205.128.1 > 224.0.0.1: igmp 10:19:07.327589 IP 10.205.128.1 > 224.0.0.1: igmp 10:21:12.336376 IP 10.205.128.1 > 224.0.0.1: igmp 10:23:17.346039 IP 10.205.128.1 > 224.0.0.1: igmp 10:25:22.356011 IP 10.205.128.1 > 224.0.0.1: igmp 10:27:27.366969 IP 10.205.128.1 > 224.0.0.1: igmp 10:29:32.376429 IP 10.205.128.1 > 224.0.0.1: igmpThat is on my WAN... but its a rfc1918 address.. But yeah coming from isp network.
-
As @johnpoz says, the internet is noisy. A lot of people don't seem to understand that; especially your broadband connection. A cable is basically a shared segment with all of your neighbors :) Some things like FiOS I think are more point to point so you don't see your neighbors traffic.
224.0.0.1 or any other multicast address isn't really targeted at you, it's basically "routed/sent to anyone that has joined the multicast group".
If it hits your WAN interface and you don't have an active membership in that group, it gets dropped by the stack at some point, even without the firewall (just basic networking as long as the interface is not in promiscuous mode).
When I first got my broadband connection I just put a throwaway device and just packet captured for a bit to see what was out there.
pfSense is built on some good technology; starting with a "default deny" stance on WAN is a simple way to avoid a lot of nastiness.
-
Also to the 53 traffic - yup seeing that as well

But see more to ssh, telnet and 21 (ftp) and the always present sql 1433.. Lots of common ports that get scanned all the time.
-
@johnpoz The only way that makes sense is ISP using that block of addresses on the "inside" of their network. It's not good sense, but a possibility.
Assuming your WAN is DHCP is it getting an address in the same space and gateway in that block too?
Looking at logs and periodic sniffing is a really good way for one to start banging heads over what should be common sense.
Edit:
antispoof on (interface) :) -
@mer said in Blocked IGMP packets flooding my logs -- IGMP snooping???:
he only way that makes sense is ISP using that block of addresses on the "inside" of their network.
Yeah for sure - its just isp noise.. you should of seen the flood of dhcp traffic use to see before they cleaned that up..
Its noise - nothing more, nothing less. I sure don't log it. I only log common udp ports and SYN tcp traffic.
-
@johnpoz Broadband to the home is teaching people not in the industry all kinds of new things. Easy to get too worked up over something that is the equivalent of "I'd like to talk about your car's extended warranty" phone call.
But it also useful to show someone "why" you lock things down. Took a while for my wife to understand, but it's fun listening to her call out others on "That's dumb, why would you do that". -
@mer said in Blocked IGMP packets flooding my logs -- IGMP snooping???:
equivalent of "I'd like to talk about your car's extended warranty" phone call.
Hey I have gotten like 3 or 4 of those in a day sometimes - ticks me off. More so that they are getting ripped off with whatever data they are buying. I have not had to worry about a warranty or extended warranty in year and years. Since I only lease going on 10 years. They getting ripped off for data on who might be interested in a warranty that is for sure..
I hit a point in my life where I had my last car for 13 years.. And said F this, I want to drive new - and a lease kind of forces my hand to get a new one every 3 years. But those get annoying - more so then some noise on my wan ;) Lately they have switched to sexy time woman voice - heheh
The other noise on your wan sort of calls is the that your SS card has been used fraudulently..
Not sure why the phone companies don't crack down on those to be honest.. But hey they getting paid for the call for sure.. Even if only a fraction of penny per call, 100 million of those add up ;)
-
@spookymonkey said in Blocked IGMP packets flooding my logs -- IGMP snooping???:
gateway is 99.241.10.1 so different from yours
I expected that. My point was to show it wasn't the gateway, which means it could be from another customer. If your subnet mask is /23, as mine is, then that address is not within your subnet, which is strange as multicasts are generally not passed through routers. Some traffic is normally visible on the WAN, but what you're describing doesn't sound normal. Perhaps you should call support and tell them what you see.
I can ping that address, but traceroute dies after 6 hops. The last hop I recognize is the Rogers office on Bloor at Jarvis and the last hop appears to be a Rogers management router, but nothing to indicate location. Rogers Etobicoke office is on Greensboro Dr., near Kipling & 401.
Do you see anything funny on IPv6? Also, Rogers has IPTV but that's usually carried on IPv6.
-
@johnpoz okay good to know the IGMP stuff is likely just noise... but I don't think the other stuff that's being directed at my IP is just noise though, this is just in a space of a few minutes
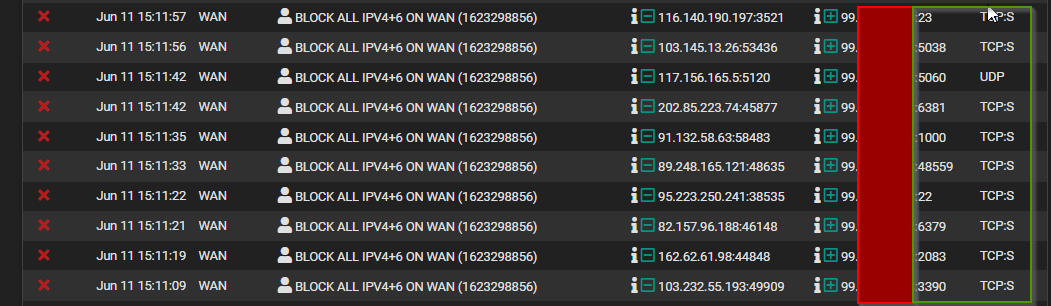
-
@spookymonkey /etc/services has mapping of port to service.
23 is telnet, 22 ssh, 5060 is a standard SIP port,
Potentially malicious, "script kiddies". It may not really be "directed" at you, more likely directed at "oh, there's an IP lets see what ports are open".But that is the beauty of the default deny rule on WAN.
-
@mer cool good to know about /etc/services .. I just setup a home lab recently to start studying for oscp so got lots of learning to do with linux :).. if these are botnets/script kiddies just running through tons of different scans/attacks on virtually all IPs (not just mine) at all minutes of the day then the internet is pretty [expletive] up lol...
-
@spookymonkey said in Blocked IGMP packets flooding my logs -- IGMP snooping???:
then the internet is pretty [expletive] up lol...
Yes, Yes it is.
Biggest thing is ask questions. Lots of knowledge here, lots in different forums.
Lots of really good PF references around (OpenBSD mailing lists) that in general talk about good/proper network security.For me, the biggest things are:
Start at default deny I personally like default deny on all interfaces (except lo), not just WAN, but others have different opinion which is fine.
Know what is on your network
Know what you want to allowNetwork security, I believe "no dumb questions" so asking is never a bad thing.
Edit:
Oh, make sure you have some Windows machines on your home network and grab the traffic to see how chatty they are. -
@mer Thanks! I have a managed switch that I just setup with 802.1q VLANs and have each VLAN along with the physical LAN interface set to
block all IPV6
allow IPV4 http/https/ntp/dns
deny all IPV4*
with a couple exceptions for my wife's VPN for work so hopefully I didn't miss anything with this setup :SI have a win10 machine I just got up and running in my proxmox box yesterday and have already noticed weird stuff getting blocked from pfBlockerNG and other random outbound traffic blocked in my firewall rules... I plan to eventually get a flip phone and ditch all the big tech garbage, but don't know how feasible that will be at this point!!!! Eventually when I learn about packet capturing/analysis, I'm sure I'll have much more to complain about...