Suricata Inline IPS blocks LAN
-
What version of the Suricata package are you running? The current version is 6.0.3_3.
Can you be more specific than "crashes the LAN when some traffic hits the interface"?
- Crashes how specifically? Does pfSense itself crash or hang?
- Does the LAN interface stop passing all traffic?
- Does this happen if any type of traffic passes through the interface, or just some specifiy type of traffic (only ICMP, only UDP, only TCP, etc.)?
- Is this problem caused only when specific rules trigger? If so, what are those rules (check the ALERTS tab).
- What messages, if any, are printed in the pfSense system log?
- Have you checked the
suricata.logfile for the LAN interface to see what is logged in there (access this under the LOGS VIEW tab).
-
@bmeeks said in Suricata Inline IPS blocks LAN:
What version of the Suricata package are you running? The current version is 6.0.3_3.
Can you be more specific than "crashes the LAN when some traffic hits the interface"?
- Crashes how specifically? Does pfSense itself crash or hang?
- Does the LAN interface stop passing all traffic?
- Does this happen if any type of traffic passes through the interface, or just some specifiy type of traffic (only ICMP, only UDP, only TCP, etc.)?
- Is this problem caused only when specific rules trigger? If so, what are those rules (check the ALERTS tab).
- What messages, if any, are printed in the pfSense system log?
- Have you checked the
suricata.logfile for the LAN interface to see what is logged in there (access this under the LOGS VIEW tab).
hi
thanks for the reply
it is the latest suricata, yes
sorry about the bad description, it crashes as in it stops all traffic on the lan interface, including to the pfsense.
no rules trigger, i've even disabled all the downloaded categories
no messages, nothing in suricata.log or system log
something that i tested with is downloading a big 2gb ubuntu torrent. it starts downloading, gets to high speed (my net limit is 500mb/s) then at an arbitrary interval ranging from 2 s to 1min the interface stops responding
thanks -
@cobrax2 said in Suricata Inline IPS blocks LAN:
it is the latest suricata, yes
sorry about the bad description, it crashes as in it stops all traffic on the lan interface, including to the pfsense.
no rules trigger, i've even disabled all the downloaded categories
no messages, nothing in suricata.log or system log
something that i tested with is downloading a big 2gb ubuntu torrent. it starts downloading, gets to high speed (my net limit is 500mb/s) then at an arbitrary interval ranging from 2 s to 1min the interface stops respondingThat sounds an awful lot like the old flow manager "stuck thread" bug, but the patch for that is included with the latest pfSense Suricata binary (or at least it is supposed to be included).
If you can get access to the console when the LAN interface hang occurs, execute this series of commands for me:
ps -ax | grep suricataThe above command will print out the process IDs (PID) of all running Suricata processes. Find the PID of the Suricata instance that is on your LAN and then run this command replacing <pid> with the PID of the Suricata instance on your LAN interface:
procstat -t <pid>I would like to see the full output of that last command. I'm looking to see if any threads are showing as kernel-locked.
Another thing you can try is to run the LAN interface in "workers" threading mode instead of "autofp". That setting can be changed on the INTERFACE SETTINGS tab.
Of course if you have removed Suricata and installed Snort, the above steps cannot be performed.
Another helpful piece of info would be the full
suricata.logfile from the interface. Some useful info is logged there during startup of the Suricata instance. -
I also found a few Google references to that Mellanox driver and weird issues with hangs and other problems. That driver may be a problem even though you say it identifies as an "em" driver.
If the flow manager hang bug patch was truly not present in the current Suricata binary build on pfSense, I would expect to be seeing a flood of messages here as that bug always showed itself after only a few minutes of "up time".
-
@bmeeks
i reinstalled suricata so i could debug the problem
the "workers" setting was already set
suricata.log:30/11/2021 -- 19:43:09 - <Notice> -- This is Suricata version 6.0.3 RELEASE running in SYSTEM mode 30/11/2021 -- 19:43:09 - <Info> -- CPUs/cores online: 2 30/11/2021 -- 19:43:09 - <Info> -- HTTP memcap: 67108864 30/11/2021 -- 19:43:09 - <Info> -- Netmap: Setting IPS mode 30/11/2021 -- 19:43:09 - <Info> -- fast output device (regular) initialized: alerts.log 30/11/2021 -- 19:43:09 - <Info> -- http-log output device (regular) initialized: http.log 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_uri 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_uri 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_raw_uri 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_raw_uri 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_request_line 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_client_body 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_response_line 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_header 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_header 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_header_names 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_header_names 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_accept 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_accept 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_accept_enc 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_accept_enc 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_accept_lang 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_accept_lang 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_referer 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_referer 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_connection 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_connection 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_content_len 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_content_len 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_content_len 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_content_len 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_content_type 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_content_type 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_content_type 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_content_type 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http.server 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http.server 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http.location 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http.location 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_protocol 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_protocol 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_start 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_start 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_raw_header 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_raw_header 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_method 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_method 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_cookie 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_cookie 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_cookie 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_cookie 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.name 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.name 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.name 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.name 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.name 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.name 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.name 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.name 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.name 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.name 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.name 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.magic 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.magic 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.magic 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.magic 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.magic 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.magic 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.magic 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.magic 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.magic 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.magic 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file.magic 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_user_agent 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_user_agent 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_host 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_raw_host 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_raw_host 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_stat_msg 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_stat_code 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http_stat_code 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http2_header_name 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http2_header_name 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http2_header 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for http2_header 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for dns_query 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for dnp3_data 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for dnp3_data 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for tls.sni 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for tls.cert_issuer 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for tls.cert_subject 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for tls.cert_serial 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for tls.cert_fingerprint 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for tls.certs 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for ja3.hash 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for ja3.string 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for ja3s.hash 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for ja3s.string 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for dce_stub_data 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for dce_stub_data 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for dce_stub_data 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for dce_stub_data 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for smb_named_pipe 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for smb_share 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for ssh.proto 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for ssh.proto 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for ssh_software 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for ssh_software 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for ssh.hassh 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for ssh.hassh.server 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for ssh.hassh.string 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for ssh.hassh.server.string 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file_data 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file_data 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file_data 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file_data 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file_data 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for file_data 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for krb5_cname 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for krb5_sname 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for sip.method 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for sip.uri 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for sip.protocol 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for sip.protocol 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for sip.method 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for sip.stat_msg 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for sip.request_line 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for sip.response_line 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for rfb.name 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for snmp.community 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for snmp.community 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for mqtt.connect.clientid 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for mqtt.connect.username 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for mqtt.connect.password 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for mqtt.connect.willtopic 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for mqtt.connect.willmessage 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for mqtt.publish.topic 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for mqtt.publish.message 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for mqtt.subscribe.topic 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for mqtt.unsubscribe.topic 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for icmpv4.hdr 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for tcp.hdr 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for udp.hdr 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for icmpv6.hdr 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for ipv4.hdr 30/11/2021 -- 19:43:09 - <Perf> -- using shared mpm ctx' for ipv6.hdr 30/11/2021 -- 19:43:10 - <Info> -- Rule with ID 2026440 is bidirectional, but source and destination are the same, treating the rule as unidirectional 30/11/2021 -- 19:43:12 - <Error> -- [ERRCODE: SC_ERR_OPENING_RULE_FILE(41)] - opening hash file /usr/local/etc/suricata/suricata_16921_em1/rules/fileextraction-chksum.list: No such file or directory 30/11/2021 -- 19:43:12 - <Error> -- [ERRCODE: SC_ERR_INVALID_SIGNATURE(39)] - error parsing signature "drop http any any -> any any (msg:"Black list checksum match and extract MD5"; filemd5:fileextraction-chksum.list; filestore; sid:28; rev:1;)" from file /usr/local/etc/suricata/suricata_16921_em1/rules/suricata.rules at line 14321 30/11/2021 -- 19:43:12 - <Error> -- [ERRCODE: SC_ERR_OPENING_RULE_FILE(41)] - opening hash file /usr/local/etc/suricata/suricata_16921_em1/rules/fileextraction-chksum.list: No such file or directory 30/11/2021 -- 19:43:12 - <Error> -- [ERRCODE: SC_ERR_INVALID_SIGNATURE(39)] - error parsing signature "drop http any any -> any any (msg:"Black list checksum match and extract SHA1"; filesha1:fileextraction-chksum.list; filestore; sid:29; rev:1;)" from file /usr/local/etc/suricata/suricata_16921_em1/rules/suricata.rules at line 14322 30/11/2021 -- 19:43:12 - <Error> -- [ERRCODE: SC_ERR_OPENING_RULE_FILE(41)] - opening hash file /usr/local/etc/suricata/suricata_16921_em1/rules/fileextraction-chksum.list: No such file or directory 30/11/2021 -- 19:43:12 - <Error> -- [ERRCODE: SC_ERR_INVALID_SIGNATURE(39)] - error parsing signature "drop http any any -> any any (msg:"Black list checksum match and extract SHA256"; filesha256:fileextraction-chksum.list; filestore; sid:30; rev:1;)" from file /usr/local/etc/suricata/suricata_16921_em1/rules/suricata.rules at line 14323 30/11/2021 -- 19:43:12 - <Info> -- 2 rule files processed. 14587 rules successfully loaded, 3 rules failed 30/11/2021 -- 19:43:12 - <Info> -- Threshold config parsed: 0 rule(s) found 30/11/2021 -- 19:43:12 - <Perf> -- using shared mpm ctx' for tcp-packet 30/11/2021 -- 19:43:12 - <Perf> -- using shared mpm ctx' for tcp-stream 30/11/2021 -- 19:43:12 - <Perf> -- using shared mpm ctx' for udp-packet 30/11/2021 -- 19:43:12 - <Perf> -- using shared mpm ctx' for other-ip 30/11/2021 -- 19:43:12 - <Info> -- 14587 signatures processed. 31 are IP-only rules, 3208 are inspecting packet payload, 11147 inspect application layer, 110 are decoder event only 30/11/2021 -- 19:43:12 - <Warning> -- [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.ButterflyJoin' is checked but not set. Checked in 2011296 and 0 other sigs 30/11/2021 -- 19:43:12 - <Warning> -- [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.Netwire.HB.1' is checked but not set. Checked in 2018282 and 0 other sigs 30/11/2021 -- 19:43:12 - <Warning> -- [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.GenericPhish_Adobe' is checked but not set. Checked in 2023048 and 0 other sigs 30/11/2021 -- 19:43:12 - <Warning> -- [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'ET.gadu.loginsent' is checked but not set. Checked in 2008299 and 0 other sigs 30/11/2021 -- 19:43:12 - <Warning> -- [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'et.http.PK' is checked but not set. Checked in 2019835 and 1 other sigs 30/11/2021 -- 19:43:12 - <Warning> -- [ERRCODE: SC_WARN_FLOWBIT(306)] - flowbit 'FB180732_2' is checked but not set. Checked in 2024697 and 0 other sigs 30/11/2021 -- 19:43:12 - <Perf> -- TCP toserver: 41 port groups, 33 unique SGH's, 8 copies 30/11/2021 -- 19:43:12 - <Perf> -- TCP toclient: 21 port groups, 20 unique SGH's, 1 copies 30/11/2021 -- 19:43:12 - <Perf> -- UDP toserver: 41 port groups, 25 unique SGH's, 16 copies 30/11/2021 -- 19:43:12 - <Perf> -- UDP toclient: 12 port groups, 7 unique SGH's, 5 copies 30/11/2021 -- 19:43:12 - <Perf> -- OTHER toserver: 254 proto groups, 3 unique SGH's, 251 copies 30/11/2021 -- 19:43:12 - <Perf> -- OTHER toclient: 254 proto groups, 0 unique SGH's, 254 copies 30/11/2021 -- 19:43:17 - <Perf> -- Unique rule groups: 88 30/11/2021 -- 19:43:17 - <Perf> -- Builtin MPM "toserver TCP packet": 28 30/11/2021 -- 19:43:17 - <Perf> -- Builtin MPM "toclient TCP packet": 15 30/11/2021 -- 19:43:17 - <Perf> -- Builtin MPM "toserver TCP stream": 29 30/11/2021 -- 19:43:17 - <Perf> -- Builtin MPM "toclient TCP stream": 18 30/11/2021 -- 19:43:17 - <Perf> -- Builtin MPM "toserver UDP packet": 24 30/11/2021 -- 19:43:17 - <Perf> -- Builtin MPM "toclient UDP packet": 6 30/11/2021 -- 19:43:17 - <Perf> -- Builtin MPM "other IP packet": 2 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_uri (http)": 7 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_uri (http2)": 7 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_raw_uri (http)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_raw_uri (http2)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_request_line (http)": 2 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_client_body (http)": 7 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient http_response_line (http)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_header (http)": 9 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient http_header (http)": 9 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_header_names (http)": 3 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient http_header_names (http)": 3 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_accept (http)": 2 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_accept (http2)": 2 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_accept_enc (http)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_accept_enc (http2)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_accept_lang (http)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_accept_lang (http2)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_referer (http)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_referer (http2)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_connection (http)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_connection (http2)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_content_len (http)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_content_len (http2)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient http_content_len (http)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient http_content_len (http2)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_content_type (http)": 2 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_content_type (http2)": 2 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient http_content_type (http)": 2 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient http_content_type (http2)": 2 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient http.server (http)": 2 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient http.server (http2)": 2 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient http.location (http)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient http.location (http2)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_start (http)": 4 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient http_start (http)": 4 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_raw_header (http)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient http_raw_header (http)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_method (http)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_method (http2)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_cookie (http)": 3 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient http_cookie (http)": 3 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_cookie (http2)": 3 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient http_cookie (http2)": 3 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_user_agent (http)": 6 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_user_agent (http2)": 6 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_host (http)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_host (http)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_raw_host (http)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver http_raw_host (http2)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient http_stat_code (http)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient http_stat_code (http2)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver dns_query (dns)": 2 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver dns_query (dns)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver tls.sni (tls)": 2 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver tls.sni (tls)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient tls.cert_issuer (tls)": 2 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient tls.cert_subject (tls)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient tls.cert_serial (tls)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient tls.cert_fingerprint (tls)": 1 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver ssh.proto (ssh)": 2 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient ssh.proto (ssh)": 2 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver file_data (smtp)": 7 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient file_data (http)": 7 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver file_data (smb)": 7 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient file_data (smb)": 7 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toserver file_data (http2)": 7 30/11/2021 -- 19:43:17 - <Perf> -- AppLayer MPM "toclient file_data (http2)": 7 30/11/2021 -- 19:43:24 - <Perf> -- Using 1 threads for interface em1 30/11/2021 -- 19:43:24 - <Info> -- Going to use 1 thread(s) for device em1 30/11/2021 -- 19:43:24 - <Info> -- devname [fd: 6] netmap:em1/R em1 opened 30/11/2021 -- 19:43:24 - <Info> -- devname [fd: 7] netmap:em1^/T em1^ opened 30/11/2021 -- 19:43:24 - <Perf> -- Using 1 threads for interface em1^ 30/11/2021 -- 19:43:24 - <Info> -- Going to use 1 thread(s) for device em1^ 30/11/2021 -- 19:43:24 - <Info> -- devname [fd: 8] netmap:em1^/R em1^ opened 30/11/2021 -- 19:43:24 - <Info> -- devname [fd: 9] netmap:em1/T em1 opened 30/11/2021 -- 19:43:24 - <Notice> -- all 2 packet processing threads, 2 management threads initialized, engine started.dmesg | grep Ethernet: this is how i thought the driver is Mellanox. maybe it means something else?
em1: Ethernet address: 00:15:17:7b:6d:cb mlx5en: Mellanox Ethernet driver 3.5.2 (September 2019) em0: Ethernet address: 00:15:17:7b:6d:ca em1: Ethernet address: 00:15:17:7b:6d:cb mlx5en: Mellanox Ethernet driver 3.5.2 (September 2019) em0: Ethernet address: 00:15:17:7b:6d:ca em1: Ethernet address: 00:15:17:7b:6d:cbShell Output - ps -ax | grep suricata
47538 - Ss 0:39.83 /usr/local/bin/suricata --netmap -D -c /usr/local/etc/suricata/suricata_16921_em1/suricata.yaml --pidfile /var/run/suricata_em116921.pid -vv
71349 - S 0:00.00 sh -c ps -ax | grep suricata 2>&1
71739 - S 0:00.00 grep suricataprocstat
PID TID COMM TDNAME CPU PRI STATE WCHAN 47538 100574 suricata - -1 120 sleep nanslp 47538 100646 suricata W#01-em1 -1 120 sleep select 47538 100653 suricata W#01-em1^ -1 120 sleep select 47538 100654 suricata FM#01 -1 121 sleep nanslp 47538 100655 suricata FR#01 -1 120 sleep nanslpthank you very much!
-
Are you running on bare metal or within a VM? Curious that Suricata is only opening a single thread for I/O. That indicates your NIC is exposing only a single queue. That would be expected in a virtual machine using an emulated adaptor, but is a bit unusual for bare metal. Most bare metal NICs have at least two queues, and many expose four.
Also, what rules package are running that is generating the missing MD5 checksum list? That error should not be happening, and the fact it is getting logged means those rules are doing nothing for you.
-
@bmeeks
yes, it is installed on pc directly
the nic is a Intel(R) PRO/1000 PT dual port, installed in the vga pcie slot, as it is a bit longer than the standard pcie slot. does this matter?
the mb is an asus prime, cpu intel celeron G5905, 8GB ram
i will deactivate all the rules again, so it won't generate that error anymore
edit:
hmm i was using et rules, but the errors stays after deactivating them all.
the builtin rules are the ones generating errors. i mean files.rules, httpevents.rules, etc
thanks -
@cobrax2 said in Suricata Inline IPS blocks LAN:
@bmeeks
yes, it is installed on pc directly
the nic is a Intel(R) PRO/1000 PT dual port, installed in the vga pcie slot, as it is a bit longer than the standard pcie slot. does this matter?
the mb is an asus prime, cpu intel celeron G5905, 8GB ram
i will deactivate all the rules again, so it won't generate that error anymore
thanksThat NIC is a plain-vanilla older Intel card. It should not be using the Mellanox driver. Not sure where that boot message is coming from. But that Mellanox driver has been included in pfSense since 2.4.5 or perhaps even earlier.
I don't believe those errors are related to your hang condition, but they indicate something is not configured 100% correctly. The message indicates you have a rule referencing a list of MD5 checksums, but the file containing that list is not in the referenced location -- hence the logged error and the failure of the rule to load properly.
-
@bmeeks
hmm i was using et rules, but the errors stays after deactivating them all.
the builtin rules are the ones generating errors. i mean files.rules, httpevents.rules, etc -
@bmeeks said in Suricata Inline IPS blocks LAN:
@cobrax2 said in Suricata Inline IPS blocks LAN:
@bmeeks
yes, it is installed on pc directly
the nic is a Intel(R) PRO/1000 PT dual port, installed in the vga pcie slot, as it is a bit longer than the standard pcie slot. does this matter?
the mb is an asus prime, cpu intel celeron G5905, 8GB ram
i will deactivate all the rules again, so it won't generate that error anymore
thanksThat NIC is a plain-vanilla older Intel card. It should not be using the Mellanox driver. Not sure where that boot message is coming from. But that Mellanox driver has been included in pfSense since 2.4.5 or perhaps even earlier.
maybe that mellanox doesnt relate to the nic?
did i use the right command to check?
thanks -
@cobrax2 said in Suricata Inline IPS blocks LAN:
@bmeeks
hmm i was using et rules, but the errors stays after deactivating them all.
the builtin rules are the ones generating errors. i mean files.rules, httpevents.rules, etcNo, I think you are mistaken there. Those built-in rules should not be referencing any md5 checksums. I have ET-Open and all the built-in rules enabled in my test VMs, and I don't get that error message. Have you created any custom rules by chance? Or have you specified a custom URL for downloading rules packages?
-
@cobrax2 said in Suricata Inline IPS blocks LAN:
@bmeeks said in Suricata Inline IPS blocks LAN:
@cobrax2 said in Suricata Inline IPS blocks LAN:
@bmeeks
yes, it is installed on pc directly
the nic is a Intel(R) PRO/1000 PT dual port, installed in the vga pcie slot, as it is a bit longer than the standard pcie slot. does this matter?
the mb is an asus prime, cpu intel celeron G5905, 8GB ram
i will deactivate all the rules again, so it won't generate that error anymore
thanksThat NIC is a plain-vanilla older Intel card. It should not be using the Mellanox driver. Not sure where that boot message is coming from. But that Mellanox driver has been included in pfSense since 2.4.5 or perhaps even earlier.
maybe that mellanox doesnt relate to the nic?
did i use the right command to check?
thanksRunning this command will list all the active PCI devices:
pciconf -lv -
@bmeeks
look what i mean:

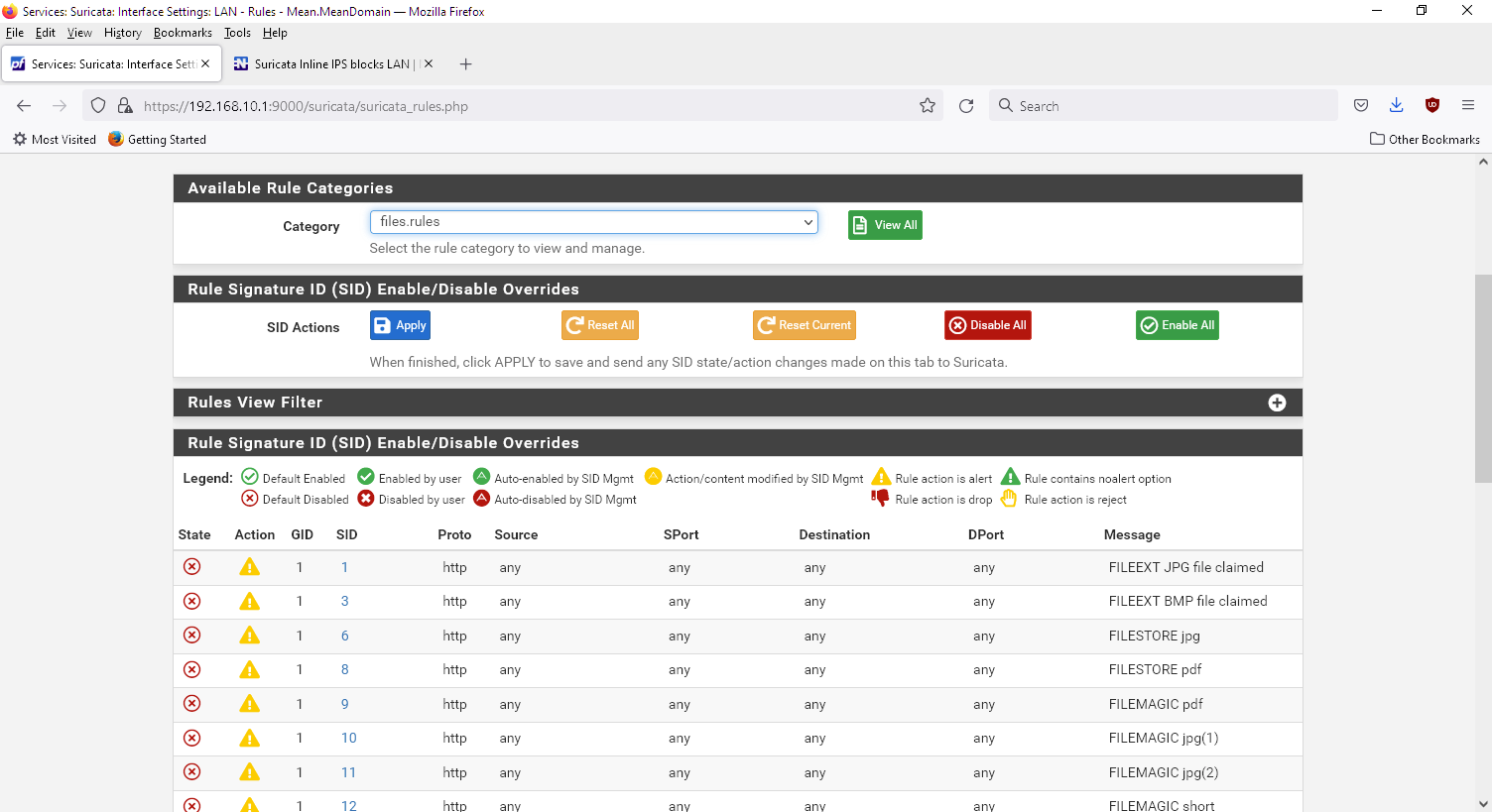
all the categories are disabled from the et open, and no other are installed -
@cobrax2 said in Suricata Inline IPS blocks LAN:
@bmeeks
look what i mean:


all the categories are disabled from the et open, and no other are installedHave you checked the
suricata.logfile again after doing this? That file is recreated with each startup of Suricata on an interface. The built-in rules are not causing your error. -
@bmeeks
yes, it's the same -
@bmeeks said in Suricata Inline IPS blocks LAN:
@cobrax2 said in Suricata Inline IPS blocks LAN:
@bmeeks said in Suricata Inline IPS blocks LAN:
@cobrax2 said in Suricata Inline IPS blocks LAN:
@bmeeks
yes, it is installed on pc directly
the nic is a Intel(R) PRO/1000 PT dual port, installed in the vga pcie slot, as it is a bit longer than the standard pcie slot. does this matter?
the mb is an asus prime, cpu intel celeron G5905, 8GB ram
i will deactivate all the rules again, so it won't generate that error anymore
thanksThat NIC is a plain-vanilla older Intel card. It should not be using the Mellanox driver. Not sure where that boot message is coming from. But that Mellanox driver has been included in pfSense since 2.4.5 or perhaps even earlier.
maybe that mellanox doesnt relate to the nic?
did i use the right command to check?
thanksRunning this command will list all the active PCI devices:
pciconf -lvhostb0@pci0:0:0:0: class=0x060000 card=0x86941043 chip=0x9b738086 rev=0x03 hdr=0x00 vendor = 'Intel Corporation' class = bridge subclass = HOST-PCI pcib1@pci0:0:1:0: class=0x060400 card=0x86941043 chip=0x19018086 rev=0x03 hdr=0x01 vendor = 'Intel Corporation' device = '6th-9th Gen Core Processor PCIe Controller (x16)' class = bridge subclass = PCI-PCI vgapci0@pci0:0:2:0: class=0x030000 card=0x86941043 chip=0x9ba88086 rev=0x03 hdr=0x00 vendor = 'Intel Corporation' class = display subclass = VGA xhci0@pci0:0:20:0: class=0x0c0330 card=0x86941043 chip=0x06ed8086 rev=0x00 hdr=0x00 vendor = 'Intel Corporation' device = 'Comet Lake USB 3.1 xHCI Host Controller' class = serial bus subclass = USB none0@pci0:0:20:2: class=0x050000 card=0x86941043 chip=0x06ef8086 rev=0x00 hdr=0x00 vendor = 'Intel Corporation' device = 'Comet Lake PCH Shared SRAM' class = memory subclass = RAM none1@pci0:0:22:0: class=0x078000 card=0x86941043 chip=0x06e08086 rev=0x00 hdr=0x00 vendor = 'Intel Corporation' device = 'Comet Lake HECI Controller' class = simple comms ahci0@pci0:0:23:0: class=0x010601 card=0x86941043 chip=0x06d28086 rev=0x00 hdr=0x00 vendor = 'Intel Corporation' class = mass storage subclass = SATA pcib2@pci0:0:29:0: class=0x060400 card=0x86941043 chip=0x06b08086 rev=0xf0 hdr=0x01 vendor = 'Intel Corporation' device = 'Comet Lake PCI Express Root Port' class = bridge subclass = PCI-PCI isab0@pci0:0:31:0: class=0x060100 card=0x86941043 chip=0x06848086 rev=0x00 hdr=0x00 vendor = 'Intel Corporation' class = bridge subclass = PCI-ISA none2@pci0:0:31:4: class=0x0c0500 card=0x86941043 chip=0x06a38086 rev=0x00 hdr=0x00 vendor = 'Intel Corporation' device = 'Comet Lake PCH SMBus Controller' class = serial bus subclass = SMBus none3@pci0:0:31:5: class=0x0c8000 card=0x86941043 chip=0x06a48086 rev=0x00 hdr=0x00 vendor = 'Intel Corporation' device = 'Comet Lake PCH SPI Controller' class = serial bus em0@pci0:1:0:0: class=0x020000 card=0x135e8086 chip=0x105e8086 rev=0x06 hdr=0x00 vendor = 'Intel Corporation' device = '82571EB/82571GB Gigabit Ethernet Controller D0/D1 (copper applications)' class = network subclass = ethernet em1@pci0:1:0:1: class=0x020000 card=0x135e8086 chip=0x105e8086 rev=0x06 hdr=0x00 vendor = 'Intel Corporation' device = '82571EB/82571GB Gigabit Ethernet Controller D0/D1 (copper applications)' class = network subclass = etherneti guess that line with Mellanox in dmesg | grep Ethernet does not relate to em1?
-
@cobrax2 said in Suricata Inline IPS blocks LAN:
@bmeeks said in Suricata Inline IPS blocks LAN:
@cobrax2 said in Suricata Inline IPS blocks LAN:
@bmeeks said in Suricata Inline IPS blocks LAN:
@cobrax2 said in Suricata Inline IPS blocks LAN:
@bmeeks
yes, it is installed on pc directly
the nic is a Intel(R) PRO/1000 PT dual port, installed in the vga pcie slot, as it is a bit longer than the standard pcie slot. does this matter?
the mb is an asus prime, cpu intel celeron G5905, 8GB ram
i will deactivate all the rules again, so it won't generate that error anymore
thanksThat NIC is a plain-vanilla older Intel card. It should not be using the Mellanox driver. Not sure where that boot message is coming from. But that Mellanox driver has been included in pfSense since 2.4.5 or perhaps even earlier.
maybe that mellanox doesnt relate to the nic?
did i use the right command to check?
thanksRunning this command will list all the active PCI devices:
pciconf -lvhostb0@pci0:0:0:0: class=0x060000 card=0x86941043 chip=0x9b738086 rev=0x03 hdr=0x00 vendor = 'Intel Corporation' class = bridge subclass = HOST-PCI pcib1@pci0:0:1:0: class=0x060400 card=0x86941043 chip=0x19018086 rev=0x03 hdr=0x01 vendor = 'Intel Corporation' device = '6th-9th Gen Core Processor PCIe Controller (x16)' class = bridge subclass = PCI-PCI vgapci0@pci0:0:2:0: class=0x030000 card=0x86941043 chip=0x9ba88086 rev=0x03 hdr=0x00 vendor = 'Intel Corporation' class = display subclass = VGA xhci0@pci0:0:20:0: class=0x0c0330 card=0x86941043 chip=0x06ed8086 rev=0x00 hdr=0x00 vendor = 'Intel Corporation' device = 'Comet Lake USB 3.1 xHCI Host Controller' class = serial bus subclass = USB none0@pci0:0:20:2: class=0x050000 card=0x86941043 chip=0x06ef8086 rev=0x00 hdr=0x00 vendor = 'Intel Corporation' device = 'Comet Lake PCH Shared SRAM' class = memory subclass = RAM none1@pci0:0:22:0: class=0x078000 card=0x86941043 chip=0x06e08086 rev=0x00 hdr=0x00 vendor = 'Intel Corporation' device = 'Comet Lake HECI Controller' class = simple comms ahci0@pci0:0:23:0: class=0x010601 card=0x86941043 chip=0x06d28086 rev=0x00 hdr=0x00 vendor = 'Intel Corporation' class = mass storage subclass = SATA pcib2@pci0:0:29:0: class=0x060400 card=0x86941043 chip=0x06b08086 rev=0xf0 hdr=0x01 vendor = 'Intel Corporation' device = 'Comet Lake PCI Express Root Port' class = bridge subclass = PCI-PCI isab0@pci0:0:31:0: class=0x060100 card=0x86941043 chip=0x06848086 rev=0x00 hdr=0x00 vendor = 'Intel Corporation' class = bridge subclass = PCI-ISA none2@pci0:0:31:4: class=0x0c0500 card=0x86941043 chip=0x06a38086 rev=0x00 hdr=0x00 vendor = 'Intel Corporation' device = 'Comet Lake PCH SMBus Controller' class = serial bus subclass = SMBus none3@pci0:0:31:5: class=0x0c8000 card=0x86941043 chip=0x06a48086 rev=0x00 hdr=0x00 vendor = 'Intel Corporation' device = 'Comet Lake PCH SPI Controller' class = serial bus em0@pci0:1:0:0: class=0x020000 card=0x135e8086 chip=0x105e8086 rev=0x06 hdr=0x00 vendor = 'Intel Corporation' device = '82571EB/82571GB Gigabit Ethernet Controller D0/D1 (copper applications)' class = network subclass = ethernet em1@pci0:1:0:1: class=0x020000 card=0x135e8086 chip=0x105e8086 rev=0x06 hdr=0x00 vendor = 'Intel Corporation' device = '82571EB/82571GB Gigabit Ethernet Controller D0/D1 (copper applications)' class = network subclass = etherneti guess that line with Mellanox in dmesg | grep Ethernet does not relate to em1?
No, that line is a red herring.
-
@cobrax2 said in Suricata Inline IPS blocks LAN:
@bmeeks
yes, it's the sameYou have something unusual going on, then. You can look at the error message in the log and see those rules are coming from a "Black list checksum match" rule. That is not part of any built-in rules.
I suspect you may have some custom rules defined for the interface. And the action keyword for those rules is DROP. No built-in rule is ever shipped with DROP as the action.
-
@bmeeks said in Suricata Inline IPS blocks LAN:
@cobrax2 said in Suricata Inline IPS blocks LAN:
@bmeeks
look what i mean:


all the categories are disabled from the et open, and no other are installedHave you checked the
suricata.logfile again after doing this? That file is recreated with each startup of Suricata on an interface. The built-in rules are not causing your error.this is what is in the file that gives the error /usr/local/etc/suricata/suricata_16921_em1/rules/suricata.rules
i have in sid management a pcre:. to enable all rules, if it matters# These rules are your current set of enforced rules for the protected # interface. This list was compiled from the categories selected on the # CATEGORIES tab of the Suricata configuration for the interface and/or any # chosen Snort VRT pre-defined IPS Policy. # # Any enablesid or disablesid customizations you made have been applied # to the rules in this file. drop ip any any -> any any (msg:"SURICATA Applayer Mismatch protocol both directions"; flow:established; app-layer-event:applayer_mismatch_protocol_both_directions; flowint:applayer.anomaly.count,+,1; classtype:protocol-command-decode; sid:2260000; rev:1;) drop ip any any -> any any (msg:"SURICATA Applayer Wrong direction first Data"; flow:established; app-layer-event:applayer_wrong_direction_first_data; flowint:applayer.anomaly.count,+,1; classtype:protocol-command-decode; sid:2260001; rev:1;) drop ip any any -> any any (msg:"SURICATA Applayer Detect protocol only one direction"; flow:established; app-layer-event:applayer_detect_protocol_only_one_direction; flowint:applayer.anomaly.count,+,1; classtype:protocol-command-decode; sid:2260002; rev:1;) drop ip any any -> any any (msg:"SURICATA Applayer Protocol detection skipped"; flow:established; app-layer-event:applayer_proto_detection_skipped; flowint:applayer.anomaly.count,+,1; classtype:protocol-command-decode; sid:2260003; rev:1;) drop tcp any any -> any any (msg:"SURICATA Applayer No TLS after STARTTLS"; flow:established; app-layer-event:applayer_no_tls_after_starttls; flowint:applayer.anomaly.count,+,1; classtype:protocol-command-decode; sid:2260004; rev:2;) drop tcp any any -> any any (msg:"SURICATA Applayer Unexpected protocol"; flow:established; app-layer-event:applayer_unexpected_protocol; flowint:applayer.anomaly.count,+,1; classtype:protocol-command-decode; sid:2260005; rev:1;) drop pkthdr any any -> any any (msg:"SURICATA IPv4 packet too small"; decode-event:ipv4.pkt_too_small; classtype:protocol-command-decode; sid:2200000; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv4 header size too small"; decode-event:ipv4.hlen_too_small; classtype:protocol-command-decode; sid:2200001; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv4 total length smaller than header size"; decode-event:ipv4.iplen_smaller_than_hlen; classtype:protocol-command-decode; sid:2200002; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv4 truncated packet"; decode-event:ipv4.trunc_pkt; classtype:protocol-command-decode; sid:2200003; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv4 invalid option"; decode-event:ipv4.opt_invalid; classtype:protocol-command-decode; sid:2200004; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv4 invalid option length"; decode-event:ipv4.opt_invalid_len; classtype:protocol-command-decode; sid:2200005; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv4 malformed option"; decode-event:ipv4.opt_malformed; classtype:protocol-command-decode; sid:2200006; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv4 with ICMPv6 header"; decode-event:ipv4.icmpv6; classtype:protocol-command-decode; sid:2200092; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv4 option end of list required"; decode-event:ipv4.opt_eol_required; classtype:protocol-command-decode; sid:2200008; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv4 duplicated IP option"; decode-event:ipv4.opt_duplicate; classtype:protocol-command-decode; sid:2200009; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv4 unknown IP option"; decode-event:ipv4.opt_unknown; classtype:protocol-command-decode; sid:2200010; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv4 wrong IP version"; decode-event:ipv4.wrong_ip_version; classtype:protocol-command-decode; sid:2200011; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6 packet too small"; decode-event:ipv6.pkt_too_small; classtype:protocol-command-decode; sid:2200012; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6 truncated packet"; decode-event:ipv6.trunc_pkt; classtype:protocol-command-decode; sid:2200013; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6 truncated extension header"; decode-event:ipv6.trunc_exthdr; classtype:protocol-command-decode; sid:2200014; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6 duplicated Fragment extension header"; decode-event:ipv6.exthdr_dupl_fh; classtype:protocol-command-decode; sid:2200015; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6 useless Fragment extension header"; decode-event:ipv6.exthdr_useless_fh; classtype:protocol-command-decode; sid:2200080; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6 duplicated Routing extension header"; decode-event:ipv6.exthdr_dupl_rh; classtype:protocol-command-decode; sid:2200016; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6 duplicated Hop-By-Hop Options extension header"; decode-event:ipv6.exthdr_dupl_hh; classtype:protocol-command-decode; sid:2200017; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6 duplicated Destination Options extension header"; decode-event:ipv6.exthdr_dupl_dh; classtype:protocol-command-decode; sid:2200018; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6 duplicated Authentication Header extension header"; decode-event:ipv6.exthdr_dupl_ah; classtype:protocol-command-decode; sid:2200019; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6 duplicate ESP extension header"; decode-event:ipv6.exthdr_dupl_eh; classtype:protocol-command-decode; sid:2200020; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6 invalid option lenght in header"; decode-event:ipv6.exthdr_invalid_optlen; classtype:protocol-command-decode; sid:2200021; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6 wrong IP version"; decode-event:ipv6.wrong_ip_version; classtype:protocol-command-decode; sid:2200022; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6 AH reserved field not 0"; decode-event:ipv6.exthdr_ah_res_not_null; classtype:protocol-command-decode; sid:2200081; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6 HOPOPTS unknown option"; decode-event:ipv6.hopopts_unknown_opt; classtype:protocol-command-decode; sid:2200086; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6 HOPOPTS only padding"; decode-event:ipv6.hopopts_only_padding; classtype:protocol-command-decode; sid:2200087; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6 DSTOPTS unknown option"; decode-event:ipv6.dstopts_unknown_opt; classtype:protocol-command-decode; sid:2200088; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6 DSTOPTS only padding"; decode-event:ipv6.dstopts_only_padding; classtype:protocol-command-decode; sid:2200089; rev:2;) drop ipv6 any any -> any any (msg:"SURICATA RH Type 0"; decode-event:ipv6.rh_type_0; classtype:protocol-command-decode; sid:2200093; rev:2;) drop ipv6 any any -> any any (msg:"SURICATA reserved field in Frag Header not zero"; decode-event:ipv6.fh_non_zero_reserved_field; classtype:protocol-command-decode; sid:2200095; rev:2;) drop ipv6 any any -> any any (msg:"SURICATA data after none (59) header"; decode-event:ipv6.data_after_none_header; classtype:protocol-command-decode; sid:2200096; rev:2;) drop ipv6 any any -> any any (msg:"SURICATA unknown next header / protocol"; decode-event:ipv6.unknown_next_header; classtype:protocol-command-decode; sid:2200097; rev:2;) drop ipv6 any any -> any any (msg:"SURICATA IPv6 with ICMPv4 header"; decode-event:ipv6.icmpv4; classtype:protocol-command-decode; sid:2200090; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA ICMPv4 packet too small"; decode-event:icmpv4.pkt_too_small; classtype:protocol-command-decode; sid:2200023; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA ICMPv4 unknown type"; decode-event:icmpv4.unknown_type; classtype:protocol-command-decode; sid:2200024; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA ICMPv4 unknown code"; decode-event:icmpv4.unknown_code; classtype:protocol-command-decode; sid:2200025; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA ICMPv4 truncated packet"; decode-event:icmpv4.ipv4_trunc_pkt; classtype:protocol-command-decode; sid:2200026; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA ICMPv4 unknown version"; decode-event:icmpv4.ipv4_unknown_ver; classtype:protocol-command-decode; sid:2200027; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA ICMPv6 packet too small"; decode-event:icmpv6.pkt_too_small; classtype:protocol-command-decode; sid:2200028; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA ICMPv6 unknown type"; decode-event:icmpv6.unknown_type; classtype:protocol-command-decode; sid:2200029; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA ICMPv6 unknown code"; decode-event:icmpv6.unknown_code; classtype:protocol-command-decode; sid:2200030; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA ICMPv6 truncated packet"; decode-event:icmpv6.ipv6_trunc_pkt; classtype:protocol-command-decode; sid:2200031; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA ICMPv6 unknown version"; decode-event:icmpv6.ipv6_unknown_version; classtype:protocol-command-decode; sid:2200032; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA ICMPv6 MLD hop limit not 1"; decode-event:icmpv6.mld_message_with_invalid_hl; classtype:protocol-command-decode; sid:2200102; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA ICMPv6 unassigned type"; decode-event:icmpv6.unassigned_type; classtype:protocol-command-decode; sid:2200108; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA ICMPv6 private experimentation type"; decode-event:icmpv6.experimentation_type; classtype:protocol-command-decode; sid:2200109; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA TCP packet too small"; decode-event:tcp.pkt_too_small; classtype:protocol-command-decode; sid:2200033; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA TCP header length too small"; decode-event:tcp.hlen_too_small; classtype:protocol-command-decode; sid:2200034; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA TCP invalid option length"; decode-event:tcp.invalid_optlen; classtype:protocol-command-decode; sid:2200035; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA TCP option invalid length"; decode-event:tcp.opt_invalid_len; classtype:protocol-command-decode; sid:2200036; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA TCP duplicated option"; decode-event:tcp.opt_duplicate; classtype:protocol-command-decode; sid:2200037; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA UDP packet too small"; decode-event:udp.pkt_too_small; classtype:protocol-command-decode; sid:2200038; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA UDP header length too small"; decode-event:udp.hlen_too_small; classtype:protocol-command-decode; sid:2200039; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA UDP invalid header length"; decode-event:udp.hlen_invalid; classtype:protocol-command-decode; sid:2200040; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA SLL packet too small"; decode-event:sll.pkt_too_small; classtype:protocol-command-decode; sid:2200041; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA Ethernet packet too small"; decode-event:ethernet.pkt_too_small; classtype:protocol-command-decode; sid:2200042; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA PPP packet too small"; decode-event:ppp.pkt_too_small; classtype:protocol-command-decode; sid:2200043; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA PPP VJU packet too small"; decode-event:ppp.vju_pkt_too_small; classtype:protocol-command-decode; sid:2200044; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA PPP IPv4 packet too small"; decode-event:ppp.ip4_pkt_too_small; classtype:protocol-command-decode; sid:2200045; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA PPP IPv6 too small"; decode-event:ppp.ip6_pkt_too_small; classtype:protocol-command-decode; sid:2200046; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA PPP wrong type"; decode-event:ppp.wrong_type; classtype:protocol-command-decode; sid:2200047; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA PPP unsupported protocol"; decode-event:ppp.unsup_proto; classtype:protocol-command-decode; sid:2200048; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA PPPOE packet too small"; decode-event:pppoe.pkt_too_small; classtype:protocol-command-decode; sid:2200049; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA PPPOE wrong code"; decode-event:pppoe.wrong_code; classtype:protocol-command-decode; sid:2200050; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA PPPOE malformed tags"; decode-event:pppoe.malformed_tags; classtype:protocol-command-decode; sid:2200051; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA GRE packet too small"; decode-event:gre.pkt_too_small; classtype:protocol-command-decode; sid:2200052; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA GRE wrong version"; decode-event:gre.wrong_version; classtype:protocol-command-decode; sid:2200053; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA GRE v0 recursion control"; decode-event:gre.version0_recur; classtype:protocol-command-decode; sid:2200054; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA GRE v0 flags"; decode-event:gre.version0_flags; classtype:protocol-command-decode; sid:2200055; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA GRE v0 header too big"; decode-event:gre.version0_hdr_too_big; classtype:protocol-command-decode; sid:2200056; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA GRE v1 checksum present"; decode-event:gre.version1_chksum; classtype:protocol-command-decode; sid:2200057; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA GRE v1 routing present"; decode-event:gre.version1_route; classtype:protocol-command-decode; sid:2200058; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA GRE v1 strict source route"; decode-event:gre.version1_ssr; classtype:protocol-command-decode; sid:2200059; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA GRE v1 recursion control"; decode-event:gre.version1_recur; classtype:protocol-command-decode; sid:2200060; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA GRE v1 flags"; decode-event:gre.version1_flags; classtype:protocol-command-decode; sid:2200061; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA GRE v1 no key present"; decode-event:gre.version1_no_key; classtype:protocol-command-decode; sid:2200062; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA GRE v1 wrong protocol"; decode-event:gre.version1_wrong_protocol; classtype:protocol-command-decode; sid:2200063; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA GRE v1 malformed Source Route Entry header"; decode-event:gre.version1_malformed_sre_hdr; classtype:protocol-command-decode; sid:2200064; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA GRE v1 header too big"; decode-event:gre.version1_hdr_too_big; classtype:protocol-command-decode; sid:2200065; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA VLAN header too small "; decode-event:vlan.header_too_small; classtype:protocol-command-decode; sid:2200066; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA VLAN unknown type"; decode-event:vlan.unknown_type; classtype:protocol-command-decode; sid:2200067; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA VLAN too many layers"; decode-event:vlan.too_many_layers; classtype:protocol-command-decode; sid:2200091; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA VNTAG header too small"; decode-event:vntag.header_too_small; classtype:protocol-command-decode; sid:2200117; rev:1;) drop pkthdr any any -> any any (msg:"SURICATA VNTAG unknown type"; decode-event:vntag.unknown_type; classtype:protocol-command-decode; sid:2200118; rev:1;) drop pkthdr any any -> any any (msg:"SURICATA IEEE802.1AH header too small"; decode-event:ieee8021ah.header_too_small; classtype:protocol-command-decode; sid:2200112; rev:1;) drop pkthdr any any -> any any (msg:"SURICATA IP raw invalid IP version "; decode-event:ipraw.invalid_ip_version; classtype:protocol-command-decode; sid:2200068; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA FRAG IPv4 Packet size too large"; decode-event:ipv4.frag_pkt_too_large; classtype:protocol-command-decode; sid:2200069; rev:3;) drop pkthdr any any -> any any (msg:"SURICATA FRAG IPv4 Fragmentation overlap"; decode-event:ipv4.frag_overlap; classtype:protocol-command-decode; sid:2200070; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA FRAG IPv6 Packet size too large"; decode-event:ipv6.frag_pkt_too_large; classtype:protocol-command-decode; sid:2200071; rev:3;) drop pkthdr any any -> any any (msg:"SURICATA FRAG IPv6 Fragmentation overlap"; decode-event:ipv6.frag_overlap; classtype:protocol-command-decode; sid:2200072; rev:2;) alert ip any any -> any any (msg:"SURICATA IPv4 invalid checksum"; ipv4-csum:invalid; classtype:protocol-command-decode; sid:2200073; rev:2;) alert tcp any any -> any any (msg:"SURICATA TCPv4 invalid checksum"; tcpv4-csum:invalid; classtype:protocol-command-decode; sid:2200074; rev:2;) alert udp any any -> any any (msg:"SURICATA UDPv4 invalid checksum"; udpv4-csum:invalid; classtype:protocol-command-decode; sid:2200075; rev:2;) alert icmp any any -> any any (msg:"SURICATA ICMPv4 invalid checksum"; icmpv4-csum:invalid; classtype:protocol-command-decode; sid:2200076; rev:2;) alert tcp any any -> any any (msg:"SURICATA TCPv6 invalid checksum"; tcpv6-csum:invalid; classtype:protocol-command-decode; sid:2200077; rev:2;) alert udp any any -> any any (msg:"SURICATA UDPv6 invalid checksum"; udpv6-csum:invalid; classtype:protocol-command-decode; sid:2200078; rev:2;) alert icmp any any -> any any (msg:"SURICATA ICMPv6 invalid checksum"; icmpv6-csum:invalid; classtype:protocol-command-decode; sid:2200079; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv4-in-IPv6 packet too short"; decode-event:ipv6.ipv4_in_ipv6_too_small; classtype:protocol-command-decode; sid:2200082; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv4-in-IPv6 invalid protocol"; decode-event:ipv6.ipv4_in_ipv6_wrong_version; classtype:protocol-command-decode; sid:2200083; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6-in-IPv6 packet too short"; decode-event:ipv6.ipv6_in_ipv6_too_small; classtype:protocol-command-decode; sid:2200084; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA IPv6-in-IPv6 invalid protocol"; decode-event:ipv6.ipv6_in_ipv6_wrong_version; classtype:protocol-command-decode; sid:2200085; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA MPLS header too small"; decode-event:mpls.header_too_small; classtype:protocol-command-decode; sid:2200111; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA MPLS packet too small"; decode-event:mpls.pkt_too_small; classtype:protocol-command-decode; sid:2200114; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA MPLS bad router alert label"; decode-event:mpls.bad_label_router_alert; classtype:protocol-command-decode; sid:2200098; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA MPLS bad implicit null label"; decode-event:mpls.bad_label_implicit_null; classtype:protocol-command-decode; sid:2200099; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA MPLS reserved label"; decode-event:mpls.bad_label_reserved; classtype:protocol-command-decode; sid:2200100; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA MPLS unknown payload type"; decode-event:mpls.unknown_payload_type; classtype:protocol-command-decode; sid:2200101; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA NULL pkt too small"; decode-event:ltnull.pkt_too_small; classtype:protocol-command-decode; sid:2200103; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA NULL unsupported type"; decode-event:ltnull.unsupported_type; classtype:protocol-command-decode; sid:2200104; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA ERSPAN pkt too small"; decode-event:erspan.header_too_small; classtype:protocol-command-decode; sid:2200105; rev:2;) drop pkthdr any any -> any any (msg:"SURICATA ERSPAN unsupported version"; decode-event:erspan.unsupported_version; classtype:protocol-command-decode; sid:2200106; rev:2;) ..... too many chars deleted by me alert tcp any any -> any any (msg:"SURICATA STREAM reassembly overlap with different data"; stream-event:reassembly_overlap_different_data; classtype:protocol-command-decode; sid:2210050; rev:2;) alert tcp any any -> any any (msg:"SURICATA STREAM bad window update"; stream-event:pkt_bad_window_update; classtype:protocol-command-decode; sid:2210056; rev:1;) alert tcp any any -> any any (msg:"SURICATA STREAM suspected RST injection"; stream-event:suspected_rst_inject; classtype:protocol-command-decode; sid:2210058; rev:1;) alert tcp any any -> any any (msg:"SURICATA STREAM ESTABLISHED retransmission packet before last ack"; stream-event:est_pkt_before_last_ack; flowint:tcp.retransmission.count,+,1; noalert; classtype:protocol-command-decode; sid:2210021; rev:3;) alert tcp any any -> any any (msg:"SURICATA STREAM CLOSEWAIT retransmission packet before last ack"; stream-event:closewait_pkt_before_last_ack; flowint:tcp.retransmission.count,+,1; noalert; classtype:protocol-command-decode; sid:2210052; rev:3;) alert tcp any any -> any any (msg:"SURICATA STREAM reassembly segment before base seq (retransmission)"; stream-event:reassembly_segment_before_base_seq; flowint:tcp.retransmission.count,+,1; noalert; classtype:protocol-command-decode; sid:2210047; rev:2;) alert tcp any any -> any any (msg:"SURICATA STREAM Packet is retransmission"; stream-event:pkt_retransmission; flowint:tcp.retransmission.count,+,1; noalert; classtype:protocol-command-decode; sid:2210053; rev:1;) alert tcp any any -> any any (msg:"SURICATA STREAM pkt seen on wrong thread"; stream-event:wrong_thread; sid:2210059; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS invalid SSLv2 header"; flow:established; app-layer-event:tls.invalid_sslv2_header; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230000; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS invalid TLS header"; flow:established; app-layer-event:tls.invalid_tls_header; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230001; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS invalid record version"; flow:established; app-layer-event:tls.invalid_record_version; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230015; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS invalid record type"; flow:established; app-layer-event:tls.invalid_record_type; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230002; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS invalid handshake message"; flow:established; app-layer-event:tls.invalid_handshake_message; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230003; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS invalid certificate"; flow:established; app-layer-event:tls.invalid_certificate; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230004; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS certificate invalid length"; flow:established; app-layer-event:tls.certificate_invalid_length; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230007; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS error message encountered"; flow:established; app-layer-event:tls.error_message_encountered; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230009; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS invalid record/traffic"; flow:established; app-layer-event:tls.invalid_ssl_record; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230010; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS heartbeat encountered"; flow:established; app-layer-event:tls.heartbeat_message; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230011; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS overflow heartbeat encountered, possible exploit attempt (heartbleed)"; flow:established; app-layer-event:tls.overflow_heartbeat_message; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; reference:cve,2014-0160; sid:2230012; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS invalid heartbeat encountered, possible exploit attempt (heartbleed)"; flow:established; app-layer-event:tls.invalid_heartbeat_message; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; reference:cve,2014-0160; sid:2230013; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS invalid encrypted heartbeat encountered, possible exploit attempt (heartbleed)"; flow:established; app-layer-event:tls.dataleak_heartbeat_mismatch; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; reference:cve,2014-0160; sid:2230014; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS multiple SNI extensions"; flow:established,to_server; app-layer-event:tls.multiple_sni_extensions; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230016; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS invalid SNI type"; flow:established,to_server; app-layer-event:tls.invalid_sni_type; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230017; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS invalid SNI length"; flow:established,to_server; app-layer-event:tls.invalid_sni_length; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230018; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS handshake invalid length"; flow:established; app-layer-event:tls.handshake_invalid_length; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230019; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS too many records in packet"; flow:established; app-layer-event:tls.too_many_records_in_packet; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230020; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS certificate invalid version"; flow:established; app-layer-event:tls.certificate_invalid_version; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230021; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS certificate invalid serial"; flow:established; app-layer-event:tls.certificate_invalid_serial; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230022; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS certificate invalid algorithm identifier"; flow:established; app-layer-event:tls.certificate_invalid_algorithmidentifier; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230023; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS certificate invalid x509 name"; flow:established; app-layer-event:tls.certificate_invalid_x509name; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230024; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS certificate invalid date"; flow:established; app-layer-event:tls.certificate_invalid_date; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230025; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS certificate invalid extensions"; flow:established; app-layer-event:tls.certificate_invalid_extensions; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230026; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS certificate invalid der"; flow:established; app-layer-event:tls.certificate_invalid_der; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230027; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS certificate invalid subject"; flow:established; app-layer-event:tls.certificate_invalid_subject; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230028; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS certificate invalid issuer"; flow:established; app-layer-event:tls.certificate_invalid_issuer; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230029; rev:1;) drop tls any any -> any any (msg:"SURICATA TLS certificate invalid validity"; flow:established; app-layer-event:tls.certificate_invalid_validity; flowint:tls.anomaly.count,+,1; classtype:protocol-command-decode; sid:2230030; rev:1;)in custom.rules there is nothing
-
@cobrax2 said in Suricata Inline IPS blocks LAN:
this is what is in the file that gives the error /usr/local/etc/suricata/suricata_16921_em1/rules/suricata.rules
i have in sid management a pcre:. to enable all rules, if it mattersDuh!
Yes it does matter. There is a huge, huge difference in saying "I have disabled all rules except built-in rules" and "I have in SID MGMT a pcre to enable all rules" ...
 .
.Some of the rules you are enabling are expecting some pre-existing md5 checksum hashes to be present, and those are not there. That's the error. What you do in SID MGMT overrides anything you select or unselect on the CATEGORIES tab.