New OpenVPN server, can connect but can't get to LAN subnet.
-
Hello,
I'm still new and learning and I'm hoping for a little help. I have been banging my head for days now and can't figure this one out. I have been looking over the forms for a while and haven't found anyone with my problem. I have setup a OpenVPN server in the past but my old Netgate died and had to start over. I'm trying to setup a new OpenVPN server with with some luck I get it to sort of work. I get connected just fine. What I can't get is connected to any devices on my LAN subnet. I can ping them and tracert them just fine. I looked over the logs and can't see anything that stands out to my untrained eyes. I looked at the firewall rules and everything looks good to me there as well. I have a very simple setup that just allows me to learn and grow. Any help would be very grateful.Things I have tried,
Removed server and reran wizard.
Changed ports.
Removed firewall rules and reapplied them.
Removed certs and reapplied them
Changed Server mode from "SSL/TLS + User Auth" to just "User Auth".
Disabled almost all other firewall rules.
Remade User.
Looked at OpenVPN logs and did a packet capture.
Tried to connect a number of devices.I normally learn by trying things over and over. I'm just now sure what else to try. Any help point me in the right direction would be very welcome.
-
@fatman032 said in New OpenVPN server, can connect but can't get to LAN subnet.:
What I can't get is connected to any devices on my LAN subnet. I can ping them and tracert them just fine.
This might be an indication for asymmetric routing.
If this could be the case depends on your network setup. Maybe you can provide some details.
You should also see it in the firewall log. Enable logging of default denies and try to access a LAN device. Then check the log. -
@fatman032 Did you setup your TUNNEL network with a different IP address range than you internal LAN network?
-
@akuma1x I did. My tunnel IP is 192.168.193.0/24 and the LAN Ip is 192.168.192.0/24.
-
@viragomann I know how to setup logging by each rule in the firewall but I'm not sure how to do it on all denies. Is that what you mean?
-
@fatman032
Status > System Logs > Settings > Log firewall default blocks -
@viragomann Thanks. I found it and I guess I was already doing that. I don't see any blocks that have OpenVPN tunnel IPs.
-
@fatman032 said in New OpenVPN server, can connect but can't get to LAN subnet.:
I don't see any blocks that have OpenVPN tunnel IPs.
Check also the destination address. This is what I'm talking about.
Are there any blocks on the internal interface.
If you post a screenshot, I could check it myself.
-
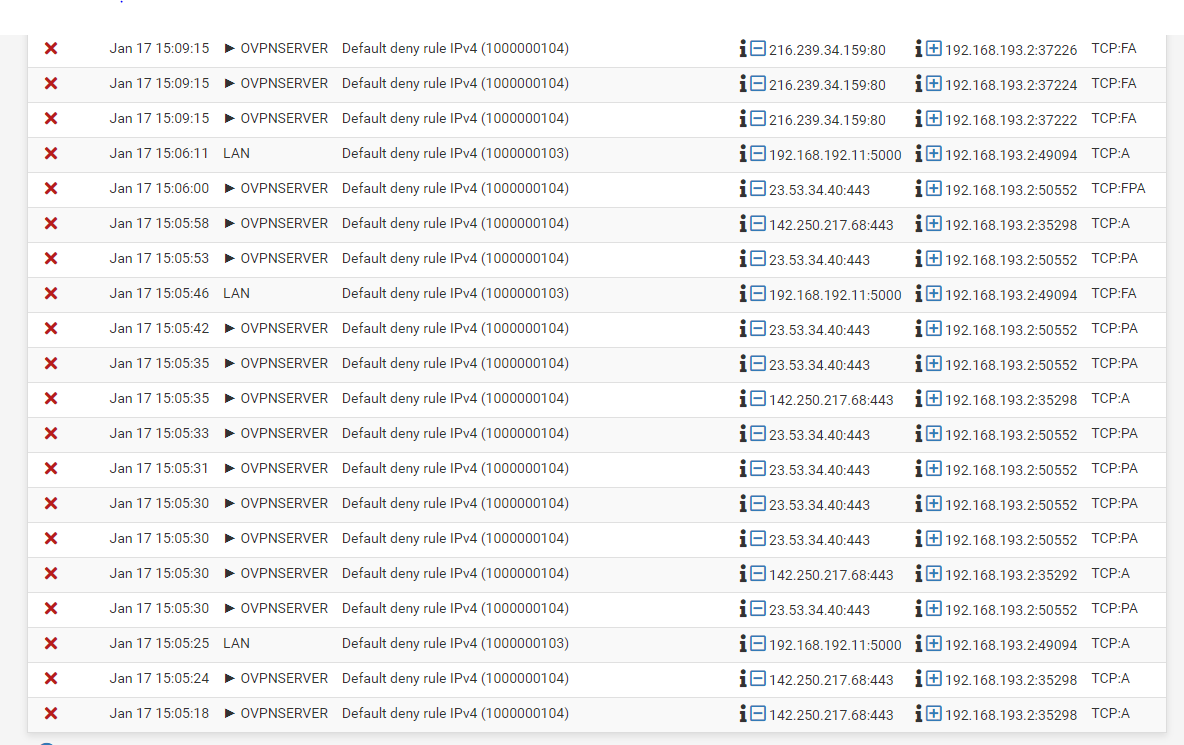
@viragomann Thanks I hope this is what you are asking for. I turned on Log Pass also. Filter By Lan
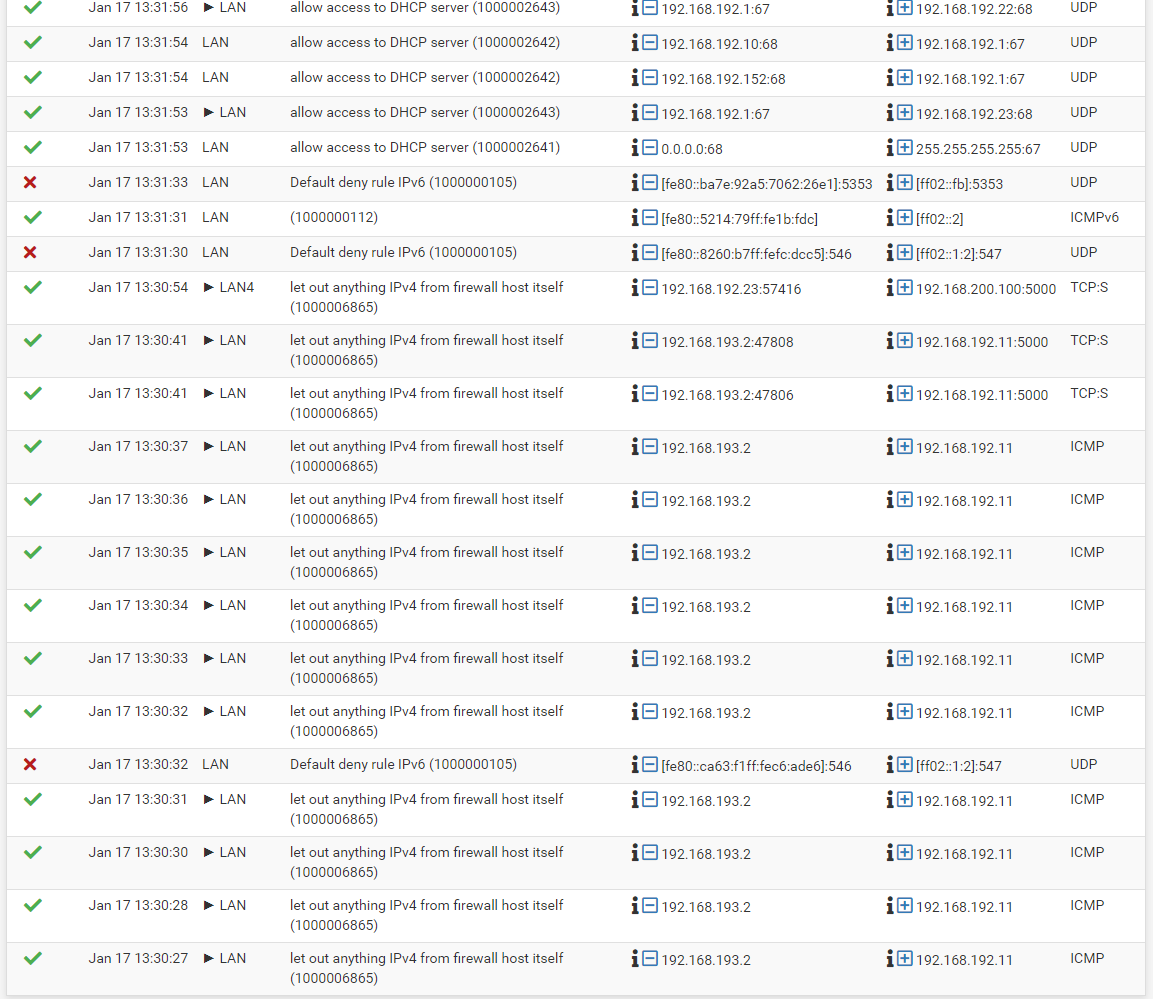
Filter by the IP Tunnel IP address
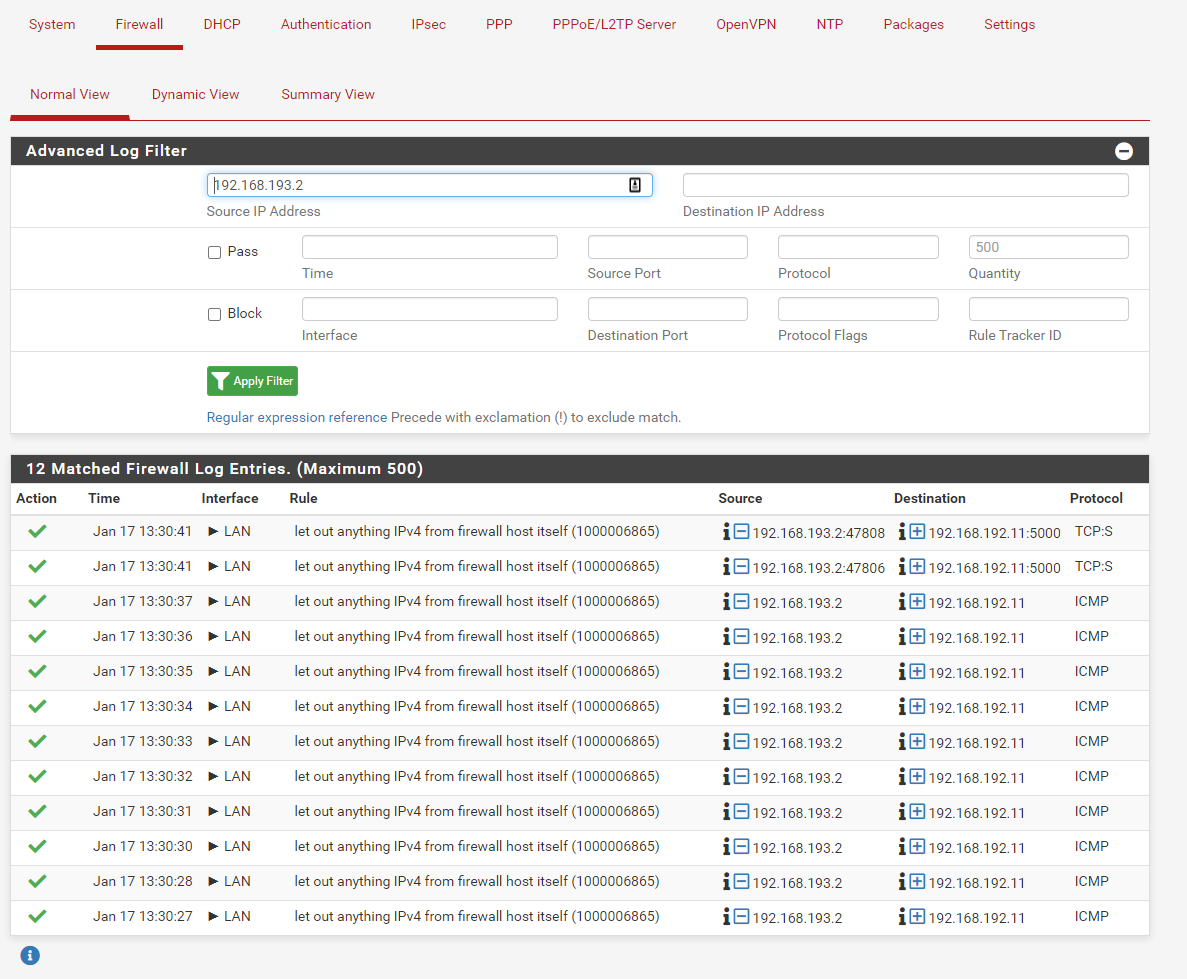
-
@fatman032
The logs only show ICMP access. You mentioned ICMP (pings) are working.
Initiate some TCP traffic which is not working. -
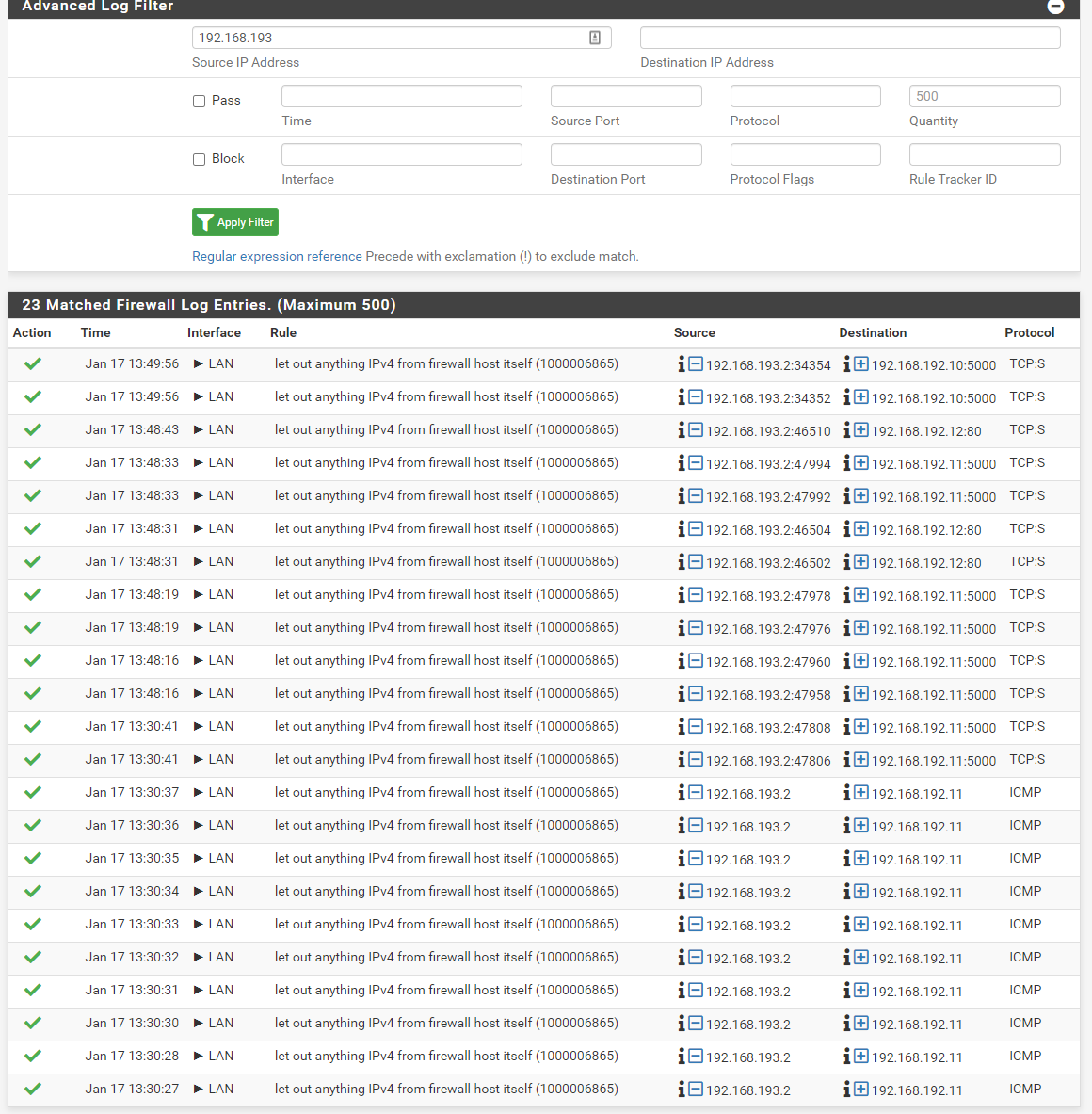
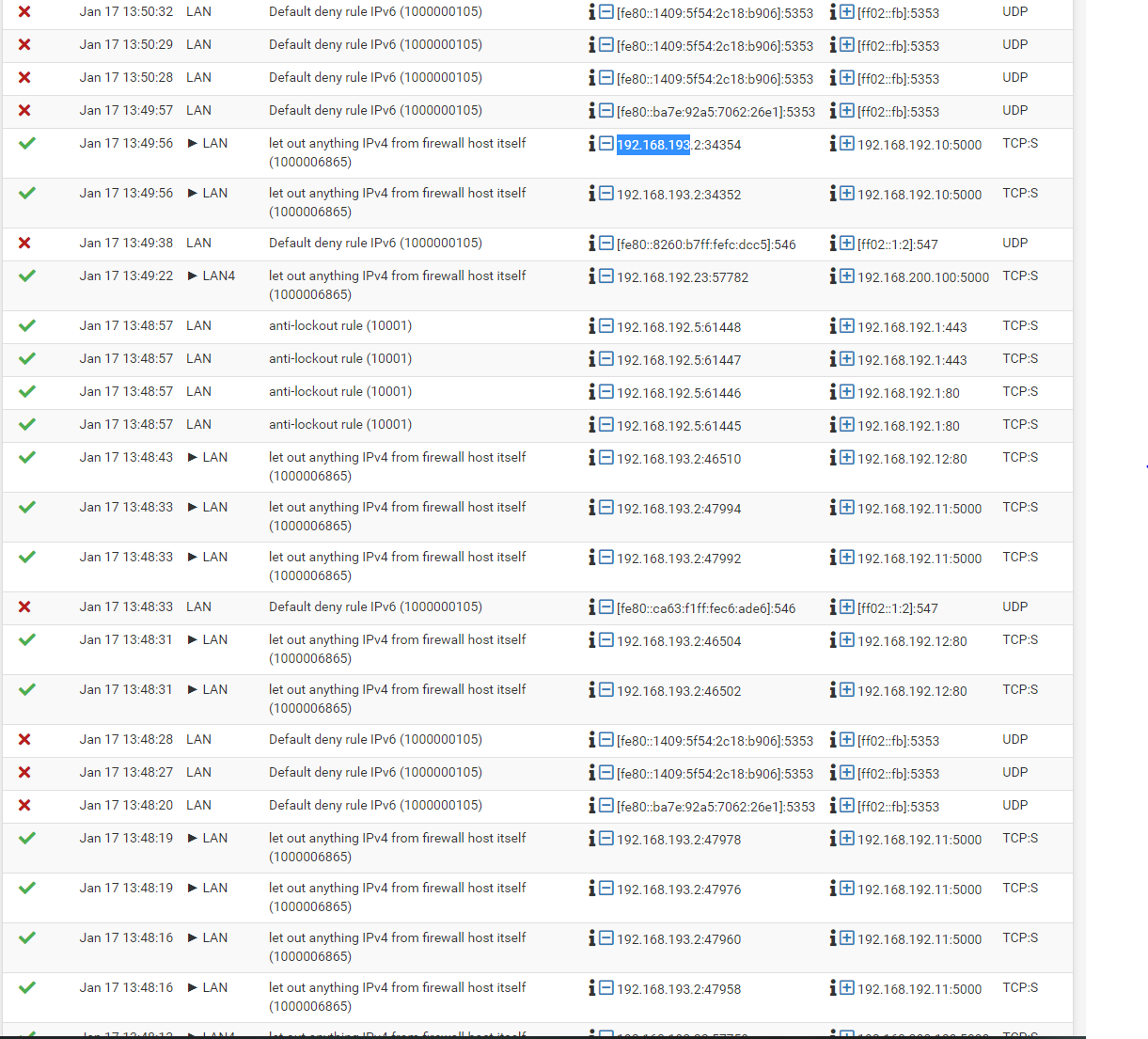
@viragomann I only tried one IP at the top of the filter. Here are some more.
Filter Tunnel IP
Filter LAN
-
@fatman032
If you filter set the clients IP as destination. -
-
@fatman032
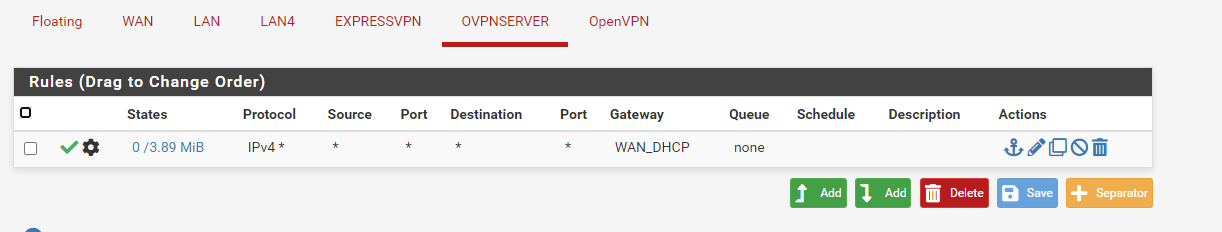
Exactly. This log shows the blocks of out of state packets, I was suspecting. However, it's not really what I was awaiting.Look at the source addresses. The most of them are public IPs and are obviously permitted by a floating rule.
We have to clean up your rules first before we can go on.You have to remove the rule from the OpenVPN tab or at least limit the source to your OpenVPN server tunnel network.
You have to know that the OpenVPN tab is an interface group and includes all OpenVPN instances you're running, servers and clients likewise. And the bad news, rules on interface groups have priority over rules on the included interfaces. So with this rule you allow access on EXPRESSVPN to your LAN as well, which might not be desired.What is OVPNSERVER? Is that the server your client we are talking about are connected to or an additional server. If yes, add the needed rule there. Otherwise you can assign an interface to the server instance first. Or even as mentioned above you can also restrict the source on the OpenVPN tab to the access server tunnel network.
What are your floating rules? You seem to have floating rule for direction out or any on the VPN interfaces. This could be dangerous. So recheck the rules.
-
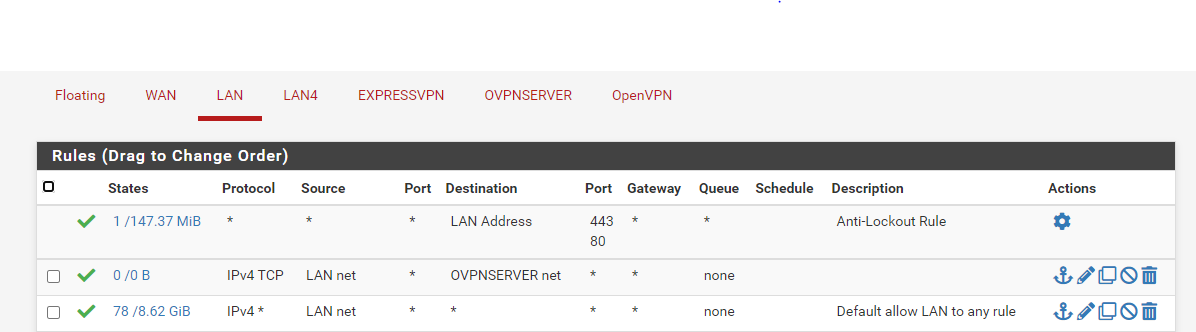
@viragomann I didn't know it was for client and server but always suspected. I added the rules Source 192.168.193.0/24 pass to destination LAN net under OpenVPN Rules. If I remove the rule any rule I can no longer ping anything on the LAN.
I have two subnets. One goes out ExpressVPN and the other out my ISP. I do this for a number of reason but mainly paying around and to change my location for NFL games. The LAN is my ISP and LAN4 is the ExpressVPN connection.
This is the part I get lost at. Under Interface Assignments I added OVPNSERVER and assigned what I thought was the OpenVPN server.
I might have done this for nothing and shouldn't have but I was completely lost and hoping it was something I missed. I don't remember doing this on the other Netgate but I read something online that hinted this might be the problem. Again could be way off track. Should I remove this?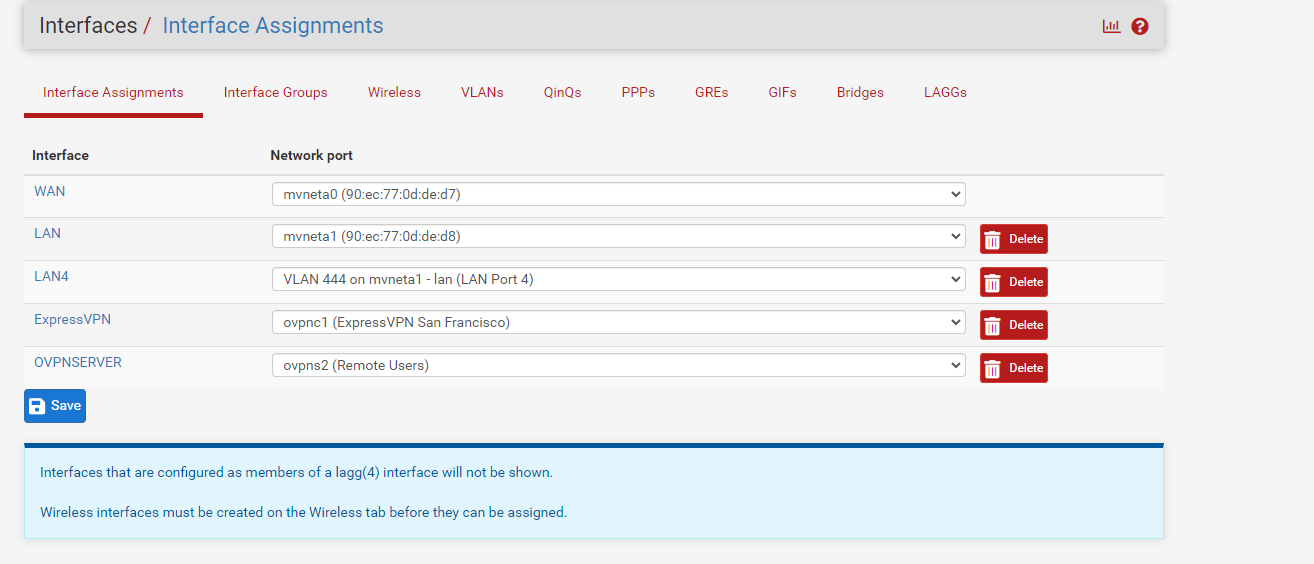
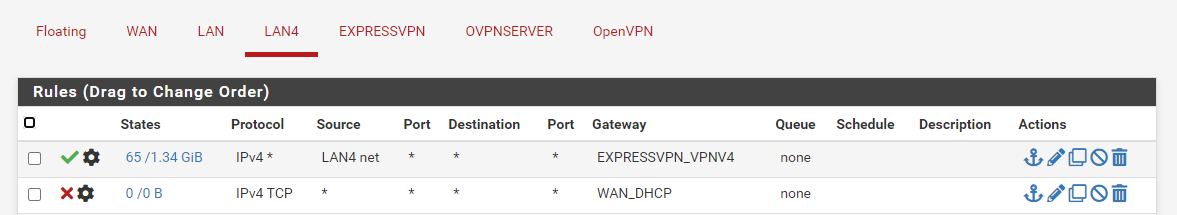
I don't have any floating rules. My expressVPN client just has an any to any rule. The only think I have under LAN4 is it can't use my WAN_DHCP gateway and to use ExpressVPN gateway. I found this to be the easy way to split the traffic.
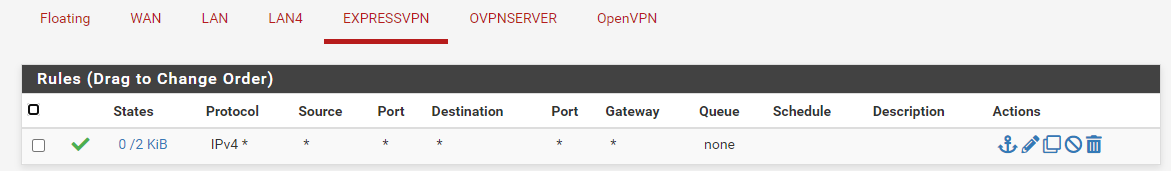
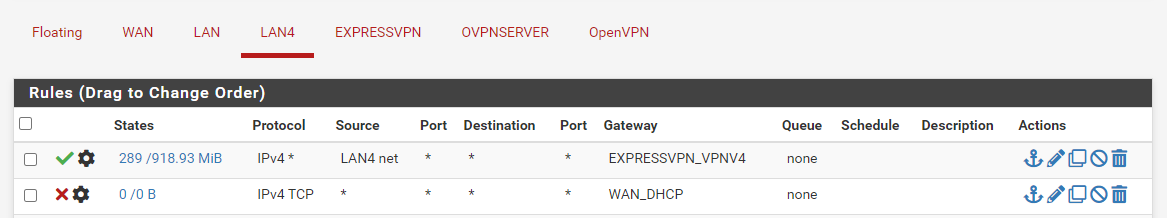
-
@fatman032
I highly recommend to remove the rule from the EXPRESSVPN interface. This rule allows incoming connections from ExpressVPN to any destination in your network!
I assume, incoming traffic is not desired at all. If not, there isn't any need to have a rule on this interface.Having the OVPNSERVER interface for the access server is not wrong. But since you have it, you can move the rules for allowing access from VPN clients from the OpenVPN tab (interface group) to the OVPNSERVER. Simply edit the rule and change the interface.
And what do you have on the floating tab? Your log shows traffic permitted by floating rules.
If the LAN4 devices use the pfSense for DNS resolution you need to allow this by a rule. The pass rule on LAN4 directs all traffic to the EXPRESSVPN gateway and doesn't allow DNS access to pfSense.
Here a floating rule can do a good job. You can add a rule with Quick option for DNS (TCP/UDP port 53) to destination "This firewall" and select all desired interfaces (LAN, LAN4, OVPNSERVER) to allow DNS for all devices with a single rule. -
@viragomann Again I can't thank you enough for the help. I'm learning a lot. I need some time to process all of this but I think I'm getting most of it.
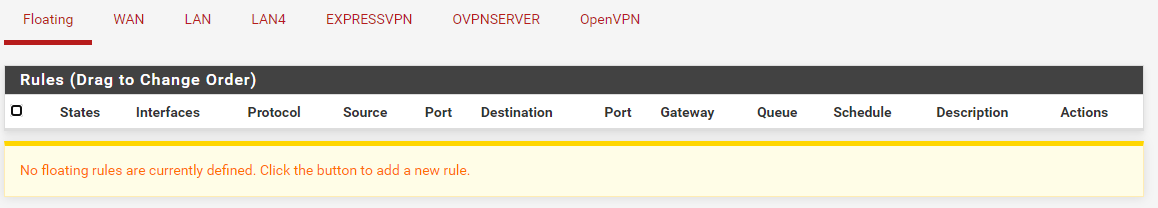
I never had anything in floating rules. In my post above you can see that. I never fully understood why you would use that rule set.
Here are some changes.
I just added the rule about DNS under floating rules.
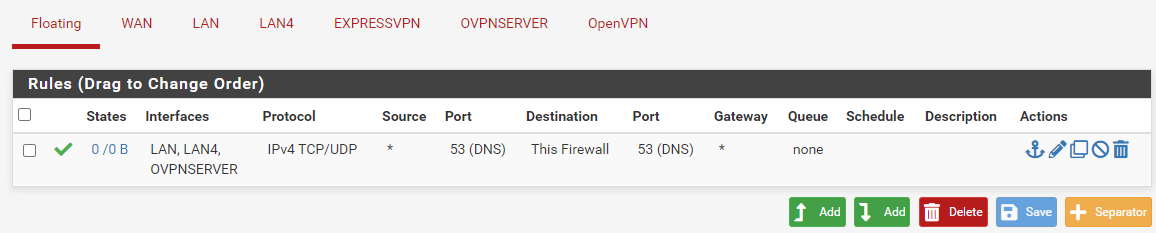
Here is my LAN rules. No changes
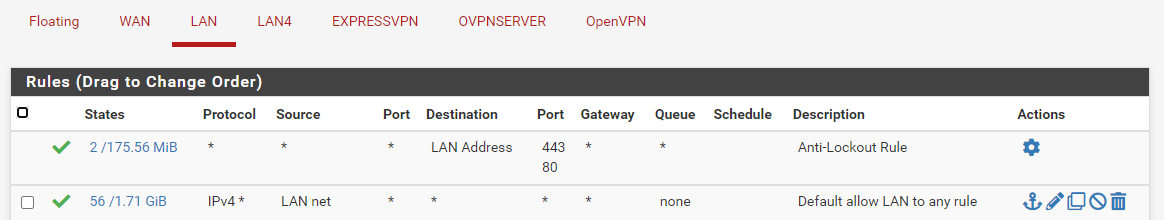
My LAN 4 interface rules. No changes
I removed the any rule on ExpressVPN
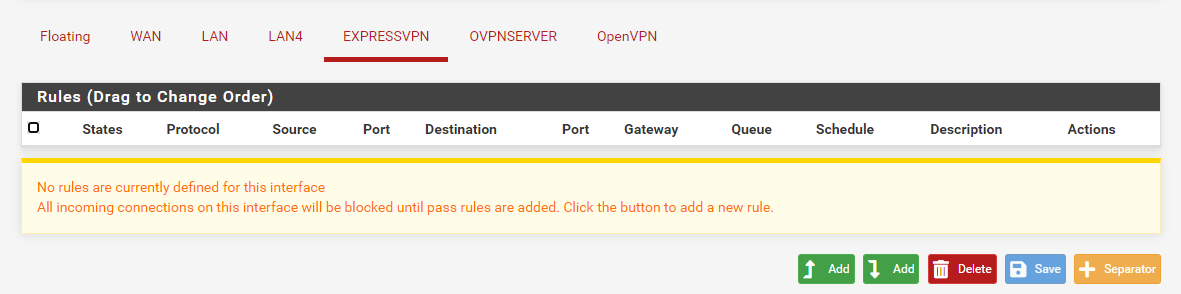
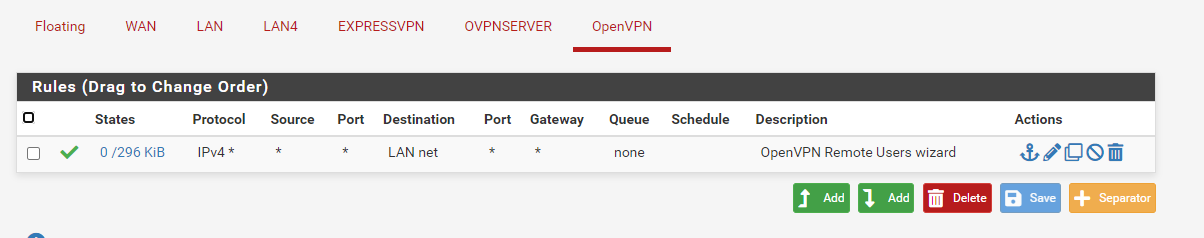
I moved the openVPN rule to OpenVPNServer interface.
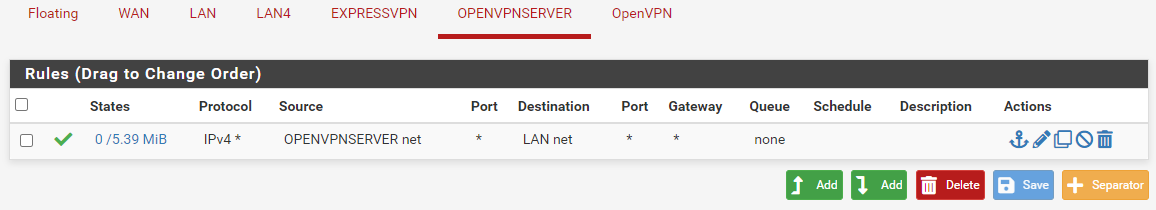
Now under openVPN I have no rules again.
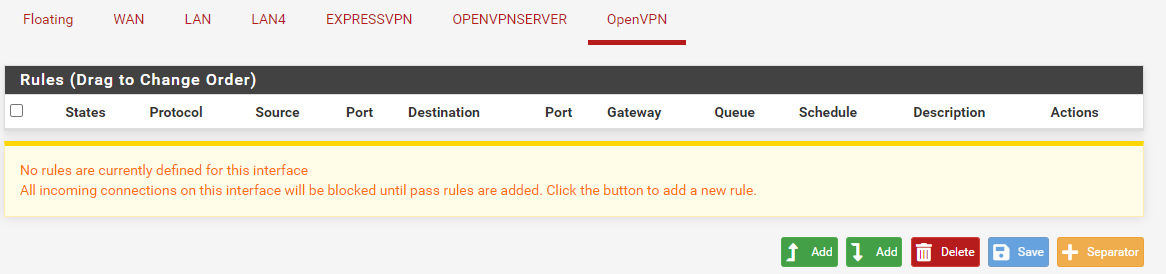
-
@fatman032
Okay. The floating rule is not correct. Two things to change:Check the "Quick" option. This ensures that the rule is applied before a matching interface rule. Without Quick your LAN4 cannot access DNS, because there is a block rule.
The source port in the rule has to be "any" as almost. The source port is dynamic, so you must not state it.
Further on LAN4 in the block rule the gateway setting is useless. The gateway only comes in if the rule matches (interface, protocol, source address and port, destination address and port), but since the rule block anything anyway, there is no use of stating a gateway.
-
@viragomann Got it. I made the changes. I just tested the VPN and I'm still getting blocked.
-
@fatman032
Fine. That was just a rule clean up as mentioned before. Now the firewall log should be better readable.
So are there news?I assume, your pfsense is the default gateway in the LAN?