pfBlockerNG block traffic
-
On my network I have Raspberry Pi with ubuntu 20.04
When I try to update the system it blocked and the connection fail.
after disable the pfBlockerNG the connection success.pfBlockerNG Enabled:
ubuntu@k8s-controller:~/kubeedge/keadm-v1.9.1-linux-arm64/keadm$ sudo apt-get update
Err:1 http://ports.ubuntu.com/ubuntu-ports focal InRelease
Could not connect to ports.ubuntu.com:80 (91.189.88.152). - connect (111: Connection refused) Cannot initiate the connection to ports.ubuntu.com:80 (2001:67c:1360:8001::23). - connect (101: Network is unreachable) Could not connect to ports.ubuntu.com:80 (91.189.88.142). - connect (111: Connection refused) Cannot initiate the connection to ports.ubuntu.com:80 (2001:67c:1360:8001::24). - connect (101: Network is unreachable)
Err:2 http://ports.ubuntu.com/ubuntu-ports focal-updates InRelease
Cannot initiate the connection to ports.ubuntu.com:80 (2001:67c:1360:8001::23). - connect (101: Network is unreachable) Cannot initiate the connection to ports.ubuntu.com:80 (2001:67c:1360:8001::24). - connect (101: Network is unreachable)
Err:3 http://ports.ubuntu.com/ubuntu-ports focal-backports InRelease
Cannot initiate the connection to ports.ubuntu.com:80 (2001:67c:1360:8001::23). - connect (101: Network is unreachable) Cannot initiate the connection to ports.ubuntu.com:80 (2001:67c:1360:8001::24). - connect (101: Network is unreachable)
Err:4 http://ports.ubuntu.com/ubuntu-ports focal-security InRelease
Cannot initiate the connection to ports.ubuntu.com:80 (2001:67c:1360:8001::23). - connect (101: Network is unreachable) Cannot initiate the connection to ports.ubuntu.com:80 (2001:67c:1360:8001::24). - connect (101: Network is unreachable)
Hit:5 https://download.docker.com/linux/ubuntu focal InRelease
Get:6 https://packages.cloud.google.com/apt kubernetes-xenial InRelease [9383 B]
Get:7 https://packages.cloud.google.com/apt kubernetes-xenial/main arm64 Packages [51.6 kB]
Fetched 61.0 kB in 1s (56.1 kB/s)
Reading package lists... Done
W: Failed to fetch http://ports.ubuntu.com/ubuntu-ports/dists/focal/InRelease Could not connect to ports.ubuntu.com:80 (91.189.88.152). - connect (111: Connection refused) Cannot initiate the connection to ports.ubuntu.com:80 (2001:67c:1360:8001::23). - connect (101: Network is unreachable) Could not connect to ports.ubuntu.com:80 (91.189.88.142). - connect (111: Connection refused) Cannot initiate the connection to ports.ubuntu.com:80 (2001:67c:1360:8001::24). - connect (101: Network is unreachable)
W: Failed to fetch http://ports.ubuntu.com/ubuntu-ports/dists/focal-updates/InRelease Cannot initiate the connection to ports.ubuntu.com:80 (2001:67c:1360:8001::23). - connect (101: Network is unreachable) Cannot initiate the connection to ports.ubuntu.com:80 (2001:67c:1360:8001::24). - connect (101: Network is unreachable)
W: Failed to fetch http://ports.ubuntu.com/ubuntu-ports/dists/focal-backports/InRelease Cannot initiate the connection to ports.ubuntu.com:80 (2001:67c:1360:8001::23). - connect (101: Network is unreachable) Cannot initiate the connection to ports.ubuntu.com:80 (2001:67c:1360:8001::24). - connect (101: Network is unreachable)
W: Failed to fetch http://ports.ubuntu.com/ubuntu-ports/dists/focal-security/InRelease Cannot initiate the connection to ports.ubuntu.com:80 (2001:67c:1360:8001::23). - connect (101: Network is unreachable) Cannot initiate the connection to ports.ubuntu.com:80 (2001:67c:1360:8001::24). - connect (101: Network is unreachable)
W: Some index files failed to download. They have been ignored, or old ones used instead.pfBlockerNG disabled:
ubuntu@k8s-controller:~/kubeedge/keadm-v1.9.1-linux-arm64/keadm$ sudo apt-get update
Hit:1 https://download.docker.com/linux/ubuntu focal InRelease
Hit:2 http://ports.ubuntu.com/ubuntu-ports focal InRelease
Get:3 http://ports.ubuntu.com/ubuntu-ports focal-updates InRelease [114 kB]
Hit:4 https://packages.cloud.google.com/apt kubernetes-xenial InRelease
Get:5 http://ports.ubuntu.com/ubuntu-ports focal-backports InRelease [108 kB]
Get:6 http://ports.ubuntu.com/ubuntu-ports focal-security InRelease [114 kB]
Get:7 http://ports.ubuntu.com/ubuntu-ports focal-updates/main arm64 Packages [1063 kB]
Get:8 http://ports.ubuntu.com/ubuntu-ports focal-updates/main arm64 c-n-f Metadata [14.3 kB]
Get:9 http://ports.ubuntu.com/ubuntu-ports focal-updates/universe arm64 Packages [844 kB]
Get:10 http://ports.ubuntu.com/ubuntu-ports focal-backports/universe arm64 Packages [20.7 kB]
Get:11 http://ports.ubuntu.com/ubuntu-ports focal-backports/universe Translation-en [14.3 kB]
Get:12 http://ports.ubuntu.com/ubuntu-ports focal-security/main arm64 Packages [771 kB]
Get:13 http://ports.ubuntu.com/ubuntu-ports focal-security/main arm64 c-n-f Metadata [8780 B]
Fetched 3071 kB in 3s (1205 kB/s)
Reading package lists... DoneI noticed that many other things blocked when its enabled.
How can I find what rule or option in the pfBlockerNG block the connections?
-
 S stephenw10 moved this topic from General pfSense Questions on
S stephenw10 moved this topic from General pfSense Questions on
-
All ip and dns blocks preformed by pgblocker are logged and can be seen in the "Reports" section of pfblocker (Firewall/pfblockerng/Reports). From there you can add blocked IPs and DNS to a whitelist.
-
In the report section I don't see anything about this block. but I found something in the logs tab under ip_block.log
Jan 27 09:07:09,1700000010,em1,LAN,block,4,17,UDP,192.168.5.157,91.189.89.198,56322,123,out,GB,pfB_Top_v4,91.189.88.0/23,GB_v4,chilipepper.canonical.com,raspberrypi,null,+
Jan 27 09:07:19,1700000010,em1,LAN,block,4,17,UDP,192.168.5.157,91.189.89.199,45416,123,out,GB,pfB_Top_v4,91.189.88.0/23,GB_v4,golem.canonical.com,raspberrypi,null,+
Jan 27 09:07:29,1700000010,em1,LAN,block,4,17,UDP,192.168.5.157,91.189.94.4,56345,123,out,GB,pfB_Top_v4,91.189.92.0/22,GB_v4,pugot.canonical.com,raspberrypi,null,+
Jan 27 09:04:10,1700000010,em1,LAN,block,4,17,UDP,192.168.5.157,91.189.94.4,46080,123,out,GB,pfB_Top_v4,91.189.92.0/22,GB_v4,pugot.canonical.com,raspberrypi,null,+as you can see from this few records the destination IP and port changed so I'm not sure how can I whitelist it.
and why it was blocked from the first place as it access from the inside the network to the outside. -
@sbh Those blocks should show up in the pfblocker Reports. Do you have the "Force Global IP Logging" option enabled in Firewall/pfblockerng/IP?
Also do you have the firewall rule that blocks the pfb_Top_v4 ailias set to log?
-
I don't have "Force Global IP Logging" enabled but the logging enabled in each of the tabs IPv4/GeoIP.
all IPv6 on my system disabled so no log's for it.
"The global logging option is only used to force logging for all IP Aliases, and not to disable the logging of all IP Aliases.
This overrides any logging settings in the GeoIP/IPv4/v6 tabs."No, I don't have firewall rule for pfb_Top_v4.
-
@sbh In your geo IP settings (Firewall/Pfblockerng/Ip/GeoIP/) what do you have for the "Action" setting and do you have "Logging" enabled?
Are you sure there is no firewall rule for pfb_Top_v4? Maybe in a floating rule?
In the dashboard widget for pfblocker look for the pfb_Top_v4 alias. What are the corresponding numbers in the Count and Packets columns? And does the arrow on the last column point up or down?
Are there any IP or DNS items showing up in the "Reports" in pfblocker?
-
Firewall/Pfblockerng/Ip/GeoIP - Logging for all of them Enabled, action all Deny Inbound. only Top Spammers Deny Both
inside North America it include all the countries beside United States.I have no rules at all in the floating rules, and no pfb_Top_v4 rule in the WAN
I checked the Aliases as well and nothing for pfb_Top_v4in the dashboard of pfBlockerNG I found this line: "[ pfB_PRI1_v4 - DShield_v4 ] Download FAIL [ 01/27/22 10:04:10 ]" and this is the only place that I found with pfB in it.
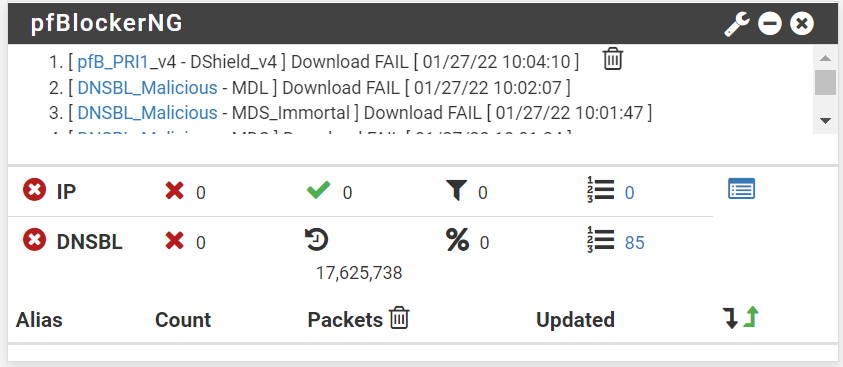
-
Something in your setup seems to be messed up. I can help you try to get it straighten out but I'm going to need some more help from you. Can you please post a screenshot of your firewall rules for LAN, WAN any any other interfaces you might have? Also a screenshot of Firewall/Aliases/URL's.
-
firewall-lan
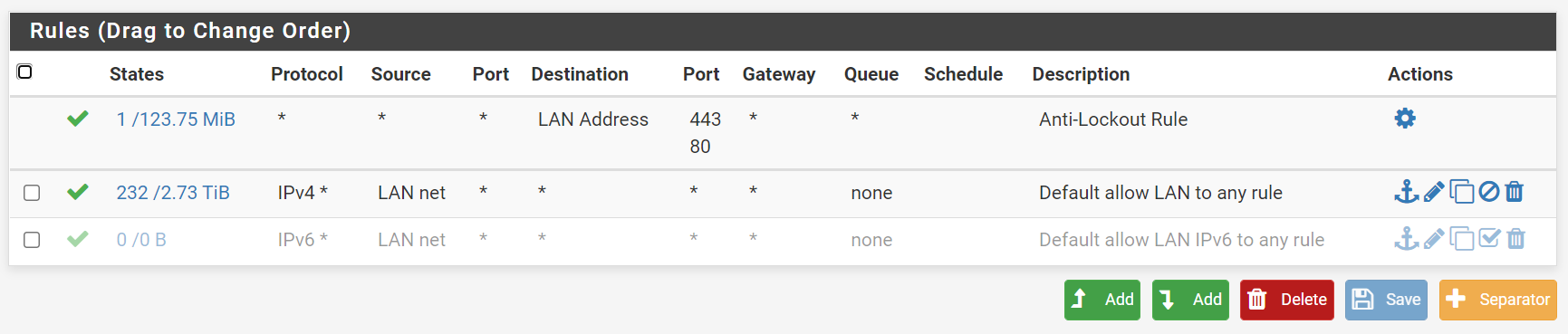
firewall-wan
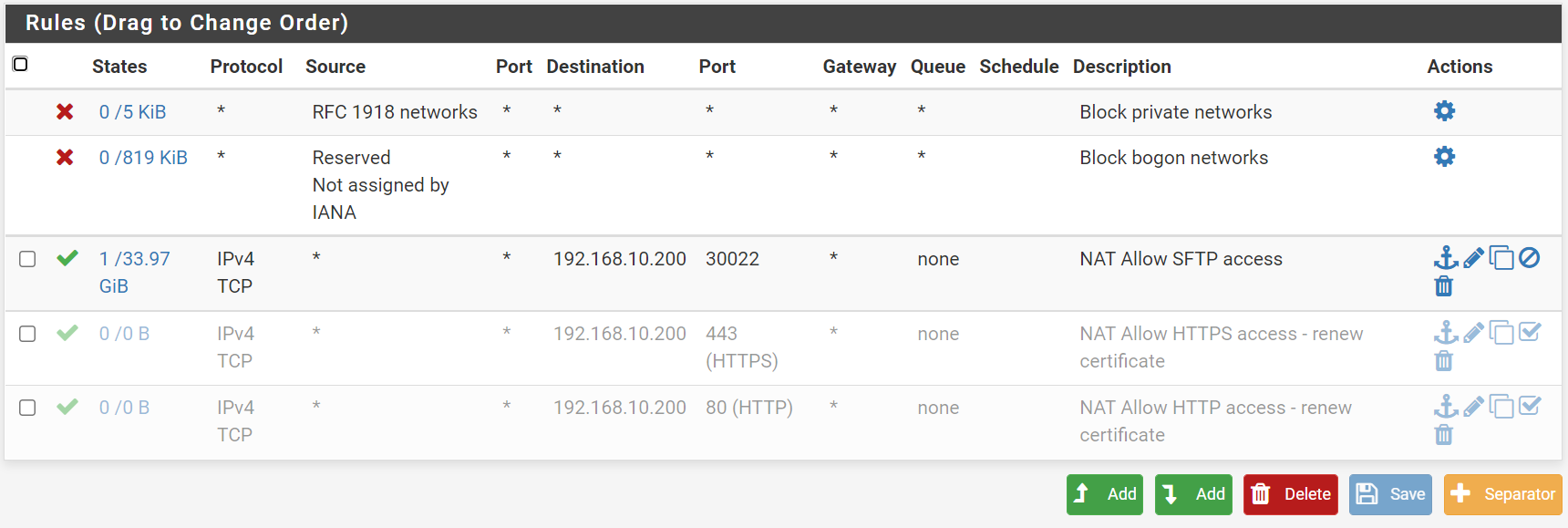
firewall-aliases-all
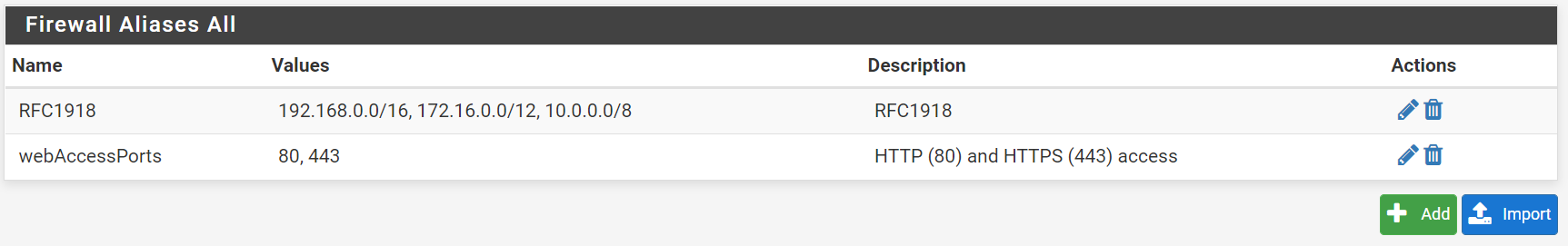
the Aliases URL's empty
I have few more vlan's but they have no relation to this issue.
the connection issue is on the lan network (if it will be needed I can add screen shots too) -
@sbh I don't see any evidence of IP block rules from pfblocker. Is pfblocker shutdown? I see above that you were using Deny Inbound and Deny Both rules. Those would be auto-generated rules. I'm not sure how pfblocker handles the removal of those rules if you shut it off or what it does with the Reports and the logs. That probably explains why on the dasbboard widget there are no aliases, or any traffic in the IP, or blocks in for either IP or DNSBL.
If pfblocker IP is shutdown I would suggest restarting it, then trying to update your Ubuntu machine again. I'm expecting that it will fail again. Once that happens repost new screen shots of the LAN, WAN, Floating, Alises, and dashboard widget if they have changes from the ones you posted. Also post a screenshot of the Reports, and IP, IPv4 and GeoIp in pfbocker.
-
What you expect to see that you don't see in the firewall rules?
-
I noticed I get this message:
There were error(s) loading the rules: /tmp/rules.debug:27: cannot define table pfB_Top_v4: Cannot allocate memory - The line in question reads [27]: table <pfB_Top_v4> persist file "/var/db/aliastables/pfB_Top_v4.txt"
@ 2022-01-28 12:48:13it may related?
by disabling and enabling the floating rules check box, I get now all the rules.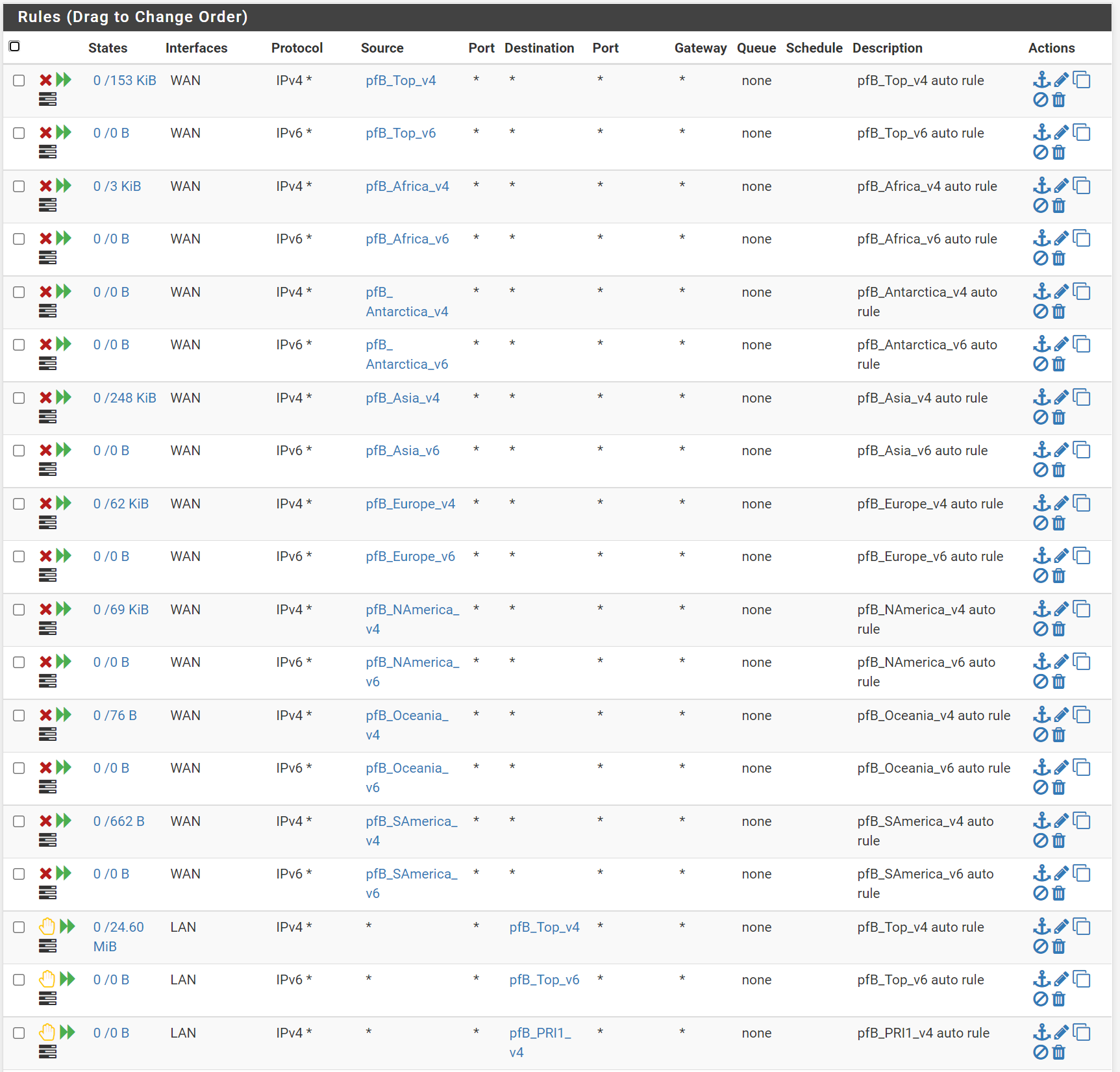
-
Not sure about the error message that you have and will think about it a bit. I take it that the rules you are showing are all floating rule?
The first thing I notice is that you do not need any of the rules for the WAN. The WAN has a default (hidden) rule on it that prohibits any packets coming into pfsense. So those rules you have on the WAN are already being handled by the default rule. You don't need to block the world from coming into pfsense.....it's done by default. :)
It's best practice to apply rules manually to each interface as needed. So the next thing I would do is change the "Action" of each of the pfb_Top_v4, pfB_Top_v6, and pfB_PRI aliases to "Alias Native". This will then create that aliases but will not create any firewall rules. You can manually create rules on each of the interfaces where you need them. It's best to not put them in floating rules.
Also, are you using IPv6 on your network? if not then you don't need any of the IPv6 feeds.
-
You correct, they all come from the floating rules. I didn't creating them. its look like they created by default by the pfblockerNG when I check the floating rules.
when I enable it, it all the rules popup the WAN and the LAN.
I use the geoIP as I don't want attempt to connect to my server from anyplace in the world beside North America.
If I understand it right. the default block any access from the WAN to the LAN. but if I did a port forward then now they can access from the WAN to the LAN via this port
the blocking of the world is to block based on location so only someone from inside the US can access this port. anyone from any other place will be blocked from accessing it.If I wrong let me know as I tested it and it work well and I may missed something there.
-
@sbh said in pfBlockerNG block traffic:
I use the geoIP as I don't want attempt to connect to my server from anyplace in the world beside North America.
If I understand it right. the default block any access from the WAN to the LAN. but if I did a port forward then now they can access from the WAN to the LAN via this portHere's what you need to do to protect the server:
- Create an Alias Permit feed for North America in pfblocker.
- Create a Permit Rule on your WAN interface with the North America alias as the Source and the Server's IP and Port as the destination.
- Immediately below the rule in #2, create a block rule with a source of any and Server's IP and Port as the destination.
Connections from North America will be allowed, everything else will be blocked from reaching the server.
One other thing, do you know the IP addresses of the things that will be connecting to the server? If so, don't use a North American alias. Instead manually create an alias with the IP's of the connecting devices and use that alias.
-
In the solution above I don't need anymore the al pfBlockerNG? since it not using it any more?
There are any other benefit to use the pfBlockerNG? -
@sbh said in pfBlockerNG block traffic:
In the solution above I don't need anymore the al pfBlockerNG? since it not using it any more?
Not sure what you are asking me here. If your're going to use an alias of North America as I described above then you create that alias using pfblocker. You would pick out the countries in North America that you want in the alias from this list:
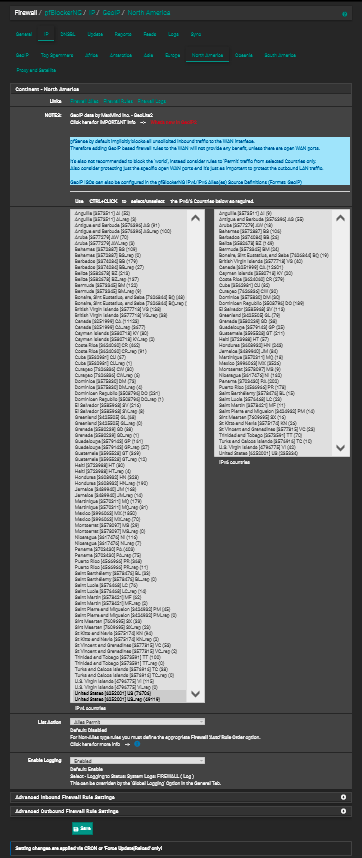
Then on this page make sure you have the Action set to "Alias Permit" for North America
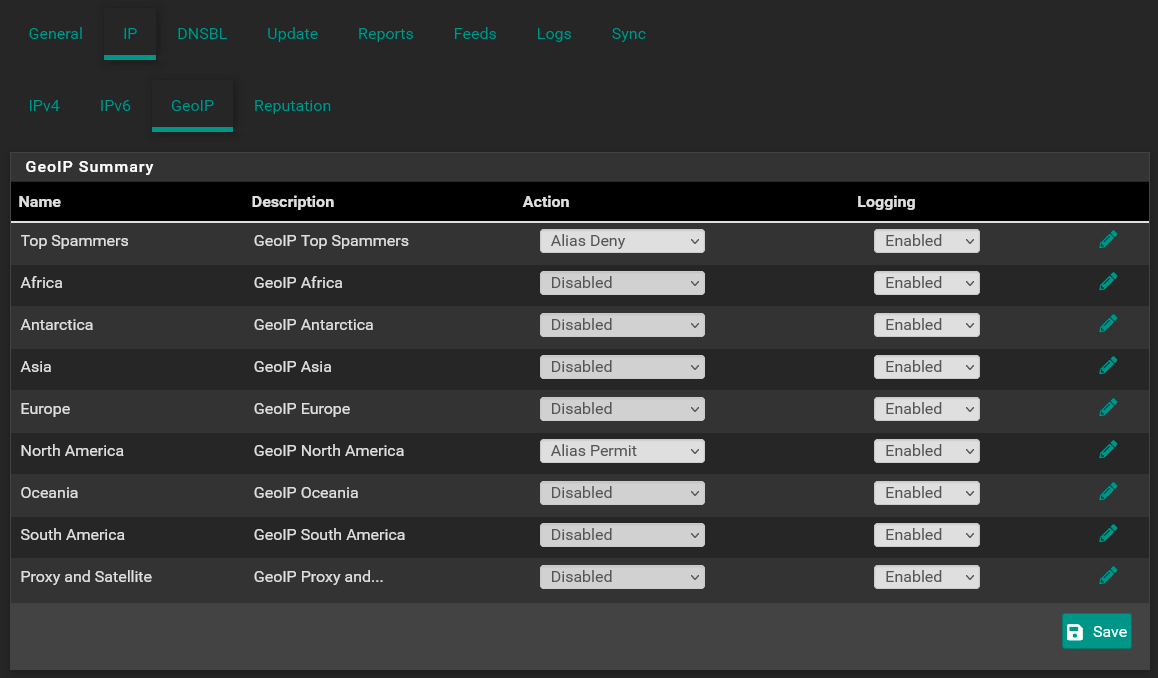
This will create an alias, pfB_NAmerica_v4 that you can then use in the firewall rules as I described.
@sbh said in pfBlockerNG block traffic:
There are any other benefit to use the pfBlockerNG?
Lot's! The most typical case would be to use it to block your devices on your internal networks from reaching out to bad sites on the internet. It can block advertising, known bad ip's and domains, malware sites, trackers, etc.
The default LAN rule in pfsense will allow your LAN devices to communicate with anything out in the internet. PFblockerNG creates the ability to block any of those devices from communicating with known places that you would rather they not communicate with.
-
Thank you for the info, I'll try to follow it and give you update. it will take some time as I'm still figuring out how to do things on pfsense.
-
I did it and it work very nice. Thanks
in the screenshot above you set Top Spammers as Alias Deny. it mean that you needed to create rule using the alias to block this top spammers. can you send me the rule as it something that I defiantly want to block.
Thanks so much
-
Congratulations on getting the rules set up on your WAN!
in the screenshot above you set Top Spammers as Alias Deny. it mean that you needed to create rule using the alias to block this top spammers. can you send me the rule as it something that I defiantly want to block.
This is easy. As you know now, by enabling the Top Spammers above it will create an alias for you to be able to use manually in any rule you want. So you can use it on any interface that you want. But remember that the WAN will block all unsolicited incoming traffic by default so you don't want to create a rule on the WAN for that alias. Instead, you would want to use it on your internal networks to block them from communicating the the IPs in the alias.
So let's look at a quick example of how this works. By default, all traffic initiated on the LAN is allowed into pfsense and can exit the WAN. When a data packet leaves the WAN it creates a state in the firewall. So when a computer (192.168.162.10) on your LAN initiates a request to go to a site at 111.111.111.111 a state is written into the state table 192.168.162.10 -> 111.111.111.111. (You can see all the states in Diagnostics/States.)
Now when 111.111.111.111 responds to 192.168.162.10's request the returning packet hits the WAN on pfsense. PFsense checks the State Table and sees that the packets is a response to a request initiated by 192.168.162.10 and therefore allows the packet through the WAN and to the LAN to the computer.
So you use a list like Top Spammers to block local resources from initiating the requests to bad IPs. So in the example above, if we want to protect the LAN clients from those bad IPs the rule would be placed on the LAN and would look like this:
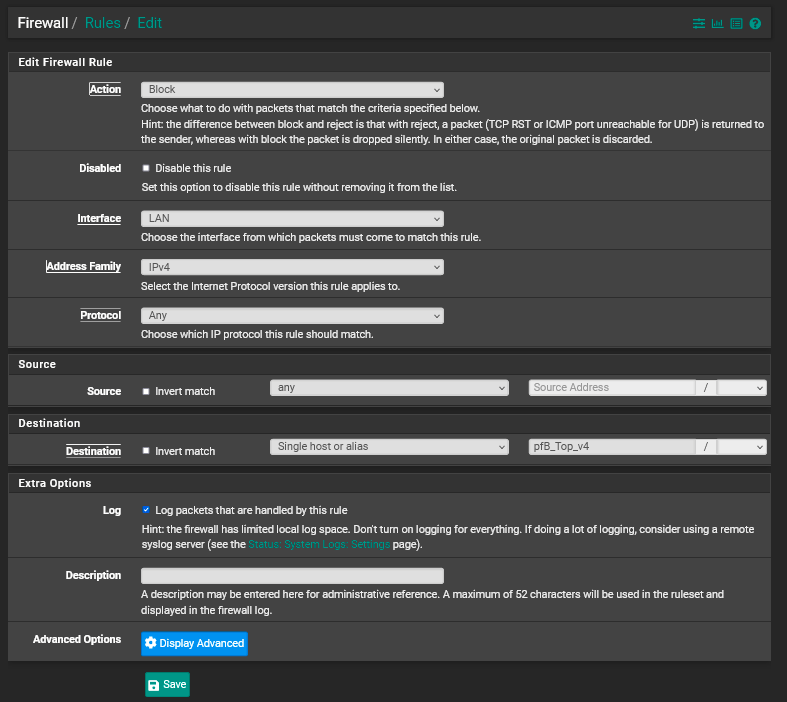
You should see the IPs that were blocked in the reports tab like this:
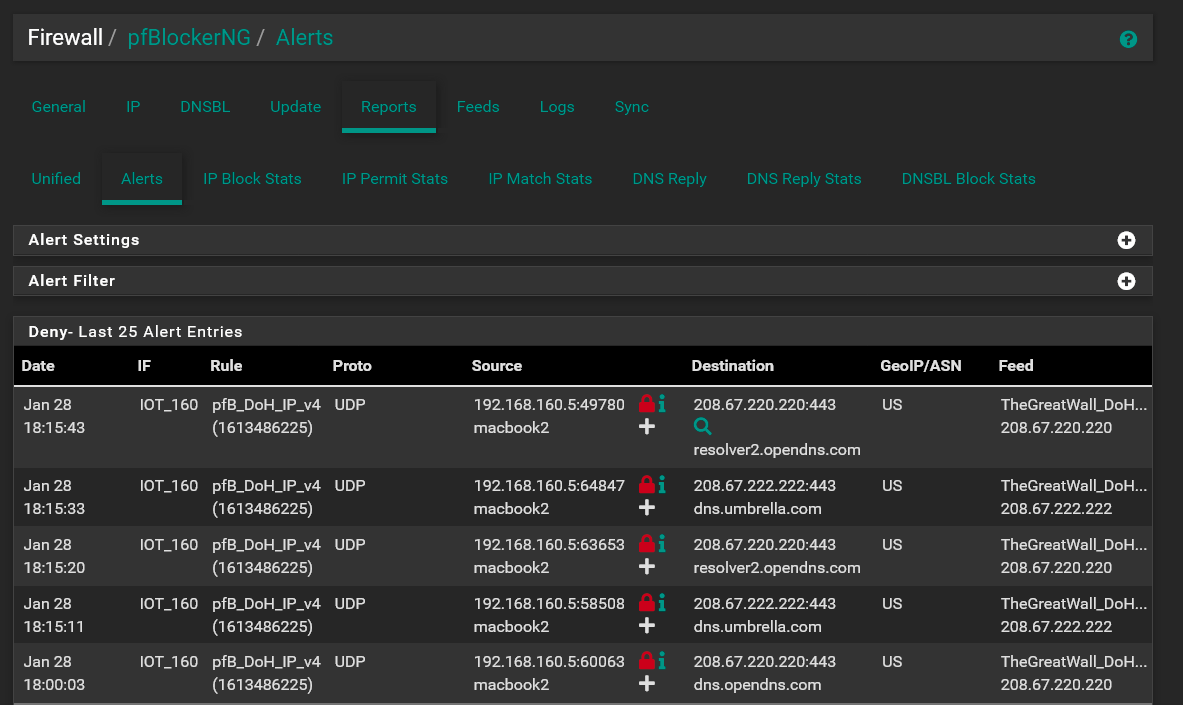
Keep in mind that none of these lists are perfect. There will be times when you will definitely get some IPs that are blocked that are legitimate places (like your Ubuntu update). When that happens you can click the red lock icon to temporarily allow the IP to be accessed, or click the "+" sign to add it to the IP whitelist.