Certificate does not have key usage extension
-
Hi friends!
I ran into a problem!
I have been working on PFSENSE 2.4.5 for a long time.
I had several openvpn connections configured (SSL/TLS remote access). Users connected through this connection to my network. I used self-written CA, Server, Client certificates. The server on which I am generating certificates is not PFSENSE, it is a standalone independent server that is not connected to the network.
On version PFSENSE 2.4.5 everything works fine!I decided to reinstall the PFSENSE server to the latest PFSENSE 2.6.0. The server was installed and restored using a backup.
I found that users can no longer connect to my network.
Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 UDPv4 READ [22] from [AF_INET]91.203.115.5:42662: P_ACK_V1 kid=0 [ 0 ] Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 UDPv4 READ [187] from [AF_INET]91.203.115.5:42662: P_CONTROL_V1 kid=0 [ ] pid=1 DATA len=173 Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 UDPv4 WRITE [1200] to [AF_INET]91.203.115.5:42662: P_CONTROL_V1 kid=0 [ 1 ] pid=1 DATA len=1174 Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 UDPv4 WRITE [1060] to [AF_INET]91.203.115.5:42662: P_CONTROL_V1 kid=0 [ ] pid=2 DATA len=1046 Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 UDPv4 READ [22] from [AF_INET]91.203.115.5:42662: P_ACK_V1 kid=0 [ 1 ] Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 UDPv4 READ [1200] from [AF_INET]91.203.115.5:42662: P_CONTROL_V1 kid=0 [ 2 ] pid=2 DATA len=1174 Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 UDPv4 WRITE [22] to [AF_INET]91.203.115.5:42662: P_ACK_V1 kid=0 [ 2 ] Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 UDPv4 READ [943] from [AF_INET]91.203.115.5:42662: P_CONTROL_V1 kid=0 [ ] pid=3 DATA len=929 Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 VERIFY WARNING: depth=0, unable to get certificate CRL: C=US, ST=CA, L=CA, O=CA, OU=CA, CN=Mob-1299 Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 VERIFY WARNING: depth=1, unable to get certificate CRL: C=CA, ST=CA, L=CA, O=CA, OU=CA, CN=CA Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 VERIFY SCRIPT OK: depth=1, C=CA, ST=CA, L=CA, O=CA, OU=CA, CN=CA Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 VERIFY OK: depth=1, C=CA, ST=CA, L=CA, O=CA, OU=CA, CN=CA Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 Certificate does not have key usage extension Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 VERIFY KU ERROR Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 OpenSSL: error:1417C086:SSL routines:tls_process_client_certificate:certificate verify failed Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 TLS_ERROR: BIO read tls_read_plaintext error Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 TLS Error: TLS object -> incoming plaintext read error Apr 22 13:45:48 openvpn 12909 91.203.115.5:42662 TLS Error: TLS handshake failedI rebooted the server, disabled and enabled the VPN, but it did not work!
But when I went into the OPENVPN settings and made changes (changing the port or changing the encryption type or setting the log verbosity level) - any change. After that, having returned this change back, my OPENVPN starts working!!!
Users can connect again.But when I rebooted the server, I ran into the same problem again.
I made changes to the configuration again, then returned it back. Users are connected.
If I stop the OPENVPN service and start it back it doesn't work. Only a change in the OPENVPN configuration works.I read a lot of forums, one of them recommends disabling "Certificate Depth"
I turned it off but it still doesn't work for me.
Help solve the problem!Server:
dev ovpns3 verb 6 dev-type tun dev-node /dev/tun3 writepid /var/run/openvpn_server3.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 auth SHA1 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown client-connect /usr/local/sbin/openvpn.attributes.sh client-disconnect /usr/local/sbin/openvpn.attributes.sh local 187.XX.XX.XX tls-server server 10.10.15.0 255.255.255.0 client-config-dir /var/etc/openvpn/server3/csc tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'SERVER-PHONE-MOB' 1" lport 11956 management /var/etc/openvpn/server3/sock unix push "dhcp-option DNS 192.168.120.1" push "dhcp-option DNS 8.8.8.8" push "dhcp-option DNS 8.8.8.8" push "redirect-gateway def1" remote-cert-tls client capath /var/etc/openvpn/server3/ca cert /var/etc/openvpn/server3/cert key /var/etc/openvpn/server3/key dh /etc/dh-parameters.1024 data-ciphers AES-128-GCM:BF-CBC data-ciphers-fallback BF-CBC allow-compression asym topology subnetClient:
persist-tun persist-key cipher BF-CBC auth SHA1 tls-client client remote 187.XX.XX.XX 11956 udp verify-x509-name "SERVER-PHONE-MOB" name auth-nocache tls-version-min 1.2 <ca> -
@testsia
Seems to be this issue: https://redmine.pfsense.org/issues/13056There is already a patch available for it: https://redmine.pfsense.org/projects/pfsense/repository/1/revisions/48cf54f850c5bf4fe26a8e33deb449807e71c204/diff
-
@viragomann said in Certificate does not have key usage extension:
@testsia
Seems to be this issue: https://redmine.pfsense.org/issues/13056There is already a patch available for it: https://redmine.pfsense.org/projects/pfsense/repository/1/revisions/48cf54f850c5bf4fe26a8e33deb449807e71c204/diff
Maybe this will help solve my problem!
I will try to make changes to the code, but this must be done outside of business hours. Thank you friend. -
@testsia
Install the System_Patches package. It patches the code automatically for you, by stating the patch ID. -
@viragomann
I thought that I would be able to solve the problem, but it's not.
I applied the patch, checked the vpn_openvpn_client.php and vpn_openvpn_server.php files, indeed the changes were made to the file.
But after applying the patch, users cannot connect, I rebooted the VPN, but there is no connection.
I made changes to the VPN configuration but that didn't help either. I removed the patch. The users have reconnected. Perhaps a reboot of Pfsense is needed? -
@testsia said in Certificate does not have key usage extension:
Perhaps a reboot of Pfsense is needed?
I'd try it. Otherwise some hints in the logs?
-
@viragomann said in Certificate does not have key usage extension:
@testsia said in Certificate does not have key usage extension:
Perhaps a reboot of Pfsense is needed?
I'd try it. Otherwise some hints in the logs?
I enable debug . Verbosity level 8
```openvpn 76521 91.203.115.5:57167 ACK reliable_send ID 1 (size=1178 to=2) Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 ACK reliable_send_timeout 2 [2] 1 Apr 22 16:30:00 openvpn 76521 PO_CTL rwflags=0x0002 ev=7 arg=0x002b7428 Apr 22 16:30:00 openvpn 76521 PO_CTL rwflags=0x0000 ev=6 arg=0x002b6724 Apr 22 16:30:00 openvpn 76521 PO_CTL rwflags=0x0001 ev=5 arg=0x002b6728 Apr 22 16:30:00 openvpn 76521 PO_CTL rwflags=0x0001 ev=11 arg=0x002b672c Apr 22 16:30:00 openvpn 76521 I/O WAIT Tr|Tw|Sr|SW [1/15005] Apr 22 16:30:00 openvpn 76521 PO_WAIT[0,0] fd=7 rev=0x00000004 rwflags=0x0002 arg=0x002b7428 Apr 22 16:30:00 openvpn 76521 I/O WAIT status=0x0002 Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 UDPv4 WRITE [1188] to [AF_INET]91.203.115.5:57167: P_CONTROL_V1 kid=0 [ ] pid=1 DATA len=1174 Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 ACK reliable_can_send active=1 current=0 : [2] 1 Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 BIO read tls_read_ciphertext 1174 bytes Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 ACK mark active outgoing ID 2 Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 ACK reliable_can_send active=2 current=1 : [3] 1 2 Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 ACK reliable_send ID 2 (size=1178 to=2) Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 ACK reliable_send_timeout 2 [3] 1 2 Apr 22 16:30:00 openvpn 76521 PO_CTL rwflags=0x0002 ev=7 arg=0x002b7428 Apr 22 16:30:00 openvpn 76521 PO_CTL rwflags=0x0000 ev=6 arg=0x002b6724 Apr 22 16:30:00 openvpn 76521 PO_CTL rwflags=0x0001 ev=5 arg=0x002b6728 Apr 22 16:30:00 openvpn 76521 PO_CTL rwflags=0x0001 ev=11 arg=0x002b672c Apr 22 16:30:00 openvpn 76521 I/O WAIT Tr|Tw|Sr|SW [1/14912] Apr 22 16:30:00 openvpn 76521 PO_WAIT[0,0] fd=7 rev=0x00000004 rwflags=0x0002 arg=0x002b7428 Apr 22 16:30:00 openvpn 76521 I/O WAIT status=0x0002 Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 UDPv4 WRITE [1188] to [AF_INET]91.203.115.5:57167: P_CONTROL_V1 kid=0 [ ] pid=2 DATA len=1174 Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 ACK reliable_can_send active=2 current=0 : [3] 1 2 Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 BIO read tls_read_ciphertext 14 bytes Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 ACK mark active outgoing ID 3 Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 ACK reliable_can_send active=3 current=1 : [4] 1 2 3 Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 ACK reliable_send ID 3 (size=18 to=2) Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 ACK reliable_send_timeout 2 [4] 1 2 3 Apr 22 16:30:00 openvpn 76521 PO_CTL rwflags=0x0002 ev=7 arg=0x002b7428 Apr 22 16:30:00 openvpn 76521 PO_CTL rwflags=0x0000 ev=6 arg=0x002b6724 Apr 22 16:30:00 openvpn 76521 PO_CTL rwflags=0x0001 ev=5 arg=0x002b6728 Apr 22 16:30:00 openvpn 76521 PO_CTL rwflags=0x0001 ev=11 arg=0x002b672c Apr 22 16:30:00 openvpn 76521 I/O WAIT Tr|Tw|Sr|SW [1/14822] Apr 22 16:30:00 openvpn 76521 PO_WAIT[0,0] fd=7 rev=0x00000004 rwflags=0x0002 arg=0x002b7428 Apr 22 16:30:00 openvpn 76521 I/O WAIT status=0x0002 Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 UDPv4 WRITE [28] to [AF_INET]91.203.115.5:57167: P_CONTROL_V1 kid=0 [ ] pid=3 DATA len=14 Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 ACK reliable_can_send active=3 current=0 : [4] 1 2 3 Apr 22 16:30:00 openvpn 76521 91.203.115.5:57167 ACK reliable_send_timeout 2 [4] 1 2 3 Apr 22 16:30:00 openvpn 76521 PO_CTL rwflags=0x0001 ev=7 arg=0x002b7428 Apr 22 16:30:00 openvpn 76521 PO_CTL rwflags=0x0001 ev=6 arg=0x002b6724 Apr 22 16:30:00 openvpn 76521 PO_CTL rwflags=0x0001 ev=5 arg=0x002b6728 Apr 22 16:30:00 openvpn 76521 PO_CTL rwflags=0x0001 ev=11 arg=0x002b672c Apr 22 16:30:00 openvpn 76521 I/O WAIT TR|Tw|SR|Sw [1/14756] Apr 22 16:30:01 openvpn 76521 PO_WAIT[0,0] fd=7 rev=0x00000001 rwflags=0x0001 arg=0x002b7428 Apr 22 16:30:01 openvpn 76521 I/O WAIT status=0x0001 Apr 22 16:30:01 openvpn 76521 MULTI: REAP range 80 -> 96 Apr 22 16:30:01 openvpn 76521 GET INST BY REAL: 91.203.115.5:57167 [ok] Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 UDPv4 READ [22] from [AF_INET]91.203.115.5:57167: P_ACK_V1 kid=0 [ 1 ] Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK received for pid 1, deleting from send buffer Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 TIMER: coarse timer wakeup 1 seconds Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK reliable_can_send active=2 current=0 : [4] 2 3 Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK reliable_send_timeout 1 [4] 2 3 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=7 arg=0x002b7428 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=6 arg=0x002b6724 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=5 arg=0x002b6728 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=11 arg=0x002b672c Apr 22 16:30:01 openvpn 76521 I/O WAIT TR|Tw|SR|Sw [0/905546] Apr 22 16:30:01 openvpn 76521 PO_WAIT[0,0] fd=7 rev=0x00000001 rwflags=0x0001 arg=0x002b7428 Apr 22 16:30:01 openvpn 76521 I/O WAIT status=0x0001 Apr 22 16:30:01 openvpn 76521 GET INST BY REAL: 91.203.115.5:57167 [ok] Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 UDPv4 READ [22] from [AF_INET]91.203.115.5:57167: P_ACK_V1 kid=0 [ 2 ] Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK received for pid 2, deleting from send buffer Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK reliable_can_send active=1 current=0 : [4] 3 Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK reliable_send_timeout 1 [4] 3 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=7 arg=0x002b7428 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=6 arg=0x002b6724 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=5 arg=0x002b6728 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=11 arg=0x002b672c Apr 22 16:30:01 openvpn 76521 I/O WAIT TR|Tw|SR|Sw [0/900672] Apr 22 16:30:01 openvpn 76521 PO_WAIT[0,0] fd=7 rev=0x00000001 rwflags=0x0001 arg=0x002b7428 Apr 22 16:30:01 openvpn 76521 I/O WAIT status=0x0001 Apr 22 16:30:01 openvpn 76521 GET INST BY REAL: 91.203.115.5:57167 [ok] Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 UDPv4 READ [1276] from [AF_INET]91.203.115.5:57167: P_CONTROL_V1 kid=0 [ 3 ] pid=2 DATA len=1250 Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK received for pid 3, deleting from send buffer Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK read ID 2 (buf->len=1250) Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK RWBS rel->size=8 rel->packet_id=00000002 id=00000002 ret=1 Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK mark active incoming ID 2 Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK acknowledge ID 2 (ack->len=1) Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK reliable_can_send active=0 current=0 : [4] Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 BIO write tls_write_ciphertext 1250 bytes Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK reliable_can_send active=0 current=0 : [4] Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK write ID 2 (ack->len=1, n=1) Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK reliable_send_timeout 604800 [4] Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0002 ev=7 arg=0x002b7428 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0000 ev=6 arg=0x002b6724 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=5 arg=0x002b6728 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=11 arg=0x002b672c Apr 22 16:30:01 openvpn 76521 I/O WAIT Tr|Tw|Sr|SW [0/889734] Apr 22 16:30:01 openvpn 76521 PO_WAIT[0,0] fd=7 rev=0x00000004 rwflags=0x0002 arg=0x002b7428 Apr 22 16:30:01 openvpn 76521 I/O WAIT status=0x0002 Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 UDPv4 WRITE [22] to [AF_INET]91.203.115.5:57167: P_ACK_V1 kid=0 [ 2 ] Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK reliable_can_send active=0 current=0 : [4] Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK reliable_send_timeout 604800 [4] Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=7 arg=0x002b7428 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=6 arg=0x002b6724 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=5 arg=0x002b6728 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=11 arg=0x002b672c Apr 22 16:30:01 openvpn 76521 I/O WAIT TR|Tw|SR|Sw [0/889660] Apr 22 16:30:01 openvpn 76521 PO_WAIT[0,0] fd=7 rev=0x00000001 rwflags=0x0001 arg=0x002b7428 Apr 22 16:30:01 openvpn 76521 I/O WAIT status=0x0001 Apr 22 16:30:01 openvpn 76521 GET INST BY REAL: 91.203.115.5:57167 [ok] Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 UDPv4 READ [1264] from [AF_INET]91.203.115.5:57167: P_CONTROL_V1 kid=0 [ ] pid=3 DATA len=1250 Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK read ID 3 (buf->len=1250) Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK RWBS rel->size=8 rel->packet_id=00000003 id=00000003 ret=1 Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK mark active incoming ID 3 Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK acknowledge ID 3 (ack->len=1) Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 ACK reliable_can_send active=0 current=0 : [4] Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 BIO write tls_write_ciphertext 1250 bytes Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 SSL state (accept): TLSv1.3 early data Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 VERIFY WARNING: depth=0, unable to get certificate CRL: C=US, ST=CA, L=CA, O=CA, OU=CA, CN=Mob-1244 Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 VERIFY WARNING: depth=1, unable to get certificate CRL: C=CA, ST=CA, L=CA, O=CA, OU=CA, CN=CA Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 VERIFY SCRIPT OK: depth=1, C=CA, ST=CA, L=CA, O=CA, OU=CA, CN=CA Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 VERIFY OK: depth=1, C=CA, ST=CA, L=CA, O=CA, OU=CA, CN=CA Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 Certificate does not have key usage extension Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 VERIFY KU ERROR Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 SSL alert (write): fatal: unknown CA Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 OpenSSL: error:1417C086:SSL routines:tls_process_client_certificate:certificate verify failed Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 TLS_ERROR: BIO read tls_read_plaintext error Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 TLS Error: TLS object -> incoming plaintext read error Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 TLS Error: TLS handshake failed Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 PID packet_id_free Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 PID packet_id_free Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 PID packet_id_free Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 PID packet_id_init seq_backtrack=64 time_backtrack=15 Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 PID packet_id_init seq_backtrack=64 time_backtrack=15 Apr 22 16:30:01 openvpn 76521 91.203.115.5:57167 SIGUSR1[soft,tls-error] received, client-instance restarting Apr 22 16:30:01 openvpn 76521 MULTI: multi_close_instance called Apr 22 16:30:01 openvpn 76521 PID packet_id_free Apr 22 16:30:01 openvpn 76521 PID packet_id_free Apr 22 16:30:01 openvpn 76521 PID packet_id_free Apr 22 16:30:01 openvpn 76521 PID packet_id_free Apr 22 16:30:01 openvpn 76521 PID packet_id_free Apr 22 16:30:01 openvpn 76521 PID packet_id_free Apr 22 16:30:01 openvpn 76521 PID packet_id_free Apr 22 16:30:01 openvpn 76521 PID packet_id_free Apr 22 16:30:01 openvpn 76521 PID packet_id_free Apr 22 16:30:01 openvpn 76521 SCHEDULE: schedule_find_least NULL Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=7 arg=0x002b7428 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=6 arg=0x002b6724 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=5 arg=0x002b6728 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=11 arg=0x002b672c Apr 22 16:30:01 openvpn 76521 I/O WAIT TR|Tw|SR|Sw [10/0] Apr 22 16:30:01 openvpn 76521 PO_WAIT[0,0] fd=7 rev=0x00000001 rwflags=0x0001 arg=0x002b7428 Apr 22 16:30:01 openvpn 76521 I/O WAIT status=0x0001 Apr 22 16:30:01 openvpn 76521 TLS State Error: No TLS state for client [AF_INET]91.203.115.5:57167, opcode=4 Apr 22 16:30:01 openvpn 76521 GET INST BY REAL: 91.203.115.5:57167 [failed] Apr 22 16:30:01 openvpn 76521 SCHEDULE: schedule_find_least NULL Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=7 arg=0x002b7428 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=6 arg=0x002b6724 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=5 arg=0x002b6728 Apr 22 16:30:01 openvpn 76521 PO_CTL rwflags=0x0001 ev=11 arg=0x002b672c Apr 22 16:30:01 openvpn 76521 I/O WAIT TR|Tw|SR|Sw [10/0] Apr 22 16:30:02 openvpn 76521 PO_WAIT[0,0] fd=7 rev=0x00000001 rwflags=0x0001 arg=0x002b7428 Apr 22 16:30:02 openvpn 76521 I/O WAIT status=0x0001 Apr 22 16:30:02 openvpn 76521 MULTI: REAP range 96 -> 112Debug 3Apr 22 16:34:24 openvpn 16094 91.203.115.5:61066 TLS: Initial packet from [AF_INET]91.203.115.5:61066, sid=e6490326 26fe8805 Apr 22 16:34:24 openvpn 16094 91.203.115.5:61066 VERIFY WARNING: depth=0, unable to get certificate CRL: C=US, ST=CA, L=CA, O=CA, OU=CA, CN=Mob-1244 Apr 22 16:34:24 openvpn 16094 91.203.115.5:61066 VERIFY WARNING: depth=1, unable to get certificate CRL: C=CA, ST=CA, L=CA, O=CA, OU=CA, CN=CA Apr 22 16:34:24 openvpn 16094 91.203.115.5:61066 VERIFY SCRIPT OK: depth=1, C=CA, ST=CA, L=CA, O=CA, OU=CA, CN=CA Apr 22 16:34:24 openvpn 16094 91.203.115.5:61066 VERIFY OK: depth=1, C=CA, ST=CA, L=CA, O=CA, OU=CA, CN=CA Apr 22 16:34:24 openvpn 16094 91.203.115.5:61066 Certificate does not have key usage extension Apr 22 16:34:24 openvpn 16094 91.203.115.5:61066 VERIFY KU ERROR Apr 22 16:34:24 openvpn 16094 91.203.115.5:61066 OpenSSL: error:1417C086:SSL routines:tls_process_client_certificate:certificate verify failed Apr 22 16:34:24 openvpn 16094 91.203.115.5:61066 TLS_ERROR: BIO read tls_read_plaintext error Apr 22 16:34:24 openvpn 16094 91.203.115.5:61066 TLS Error: TLS object -> incoming plaintext read error Apr 22 16:34:24 openvpn 16094 91.203.115.5:61066 TLS Error: TLS handshake failed Apr 22 16:34:24 openvpn 16094 91.203.115.5:61066 SIGUSR1[soft,tls-error] received, client-instance restarting -
@testsia
That was with the patch applied? It's exactly the same error as above. -
@viragomann
Yes with a patch! I also noticed that nothing has changed in the logs. Perhaps a server restart is needed?I had never used patches before, I didn't know anything about them. Thanks for the good experience!
-
@testsia said in Certificate does not have key usage extension:
Perhaps a server restart is needed?
A restart of OpenVPN server for sure, but I don't think that rebooting the box will be needed.
-
@viragomann
Do I need to restart all the OPENVPN services or is the one "OpenVPN server: Mobil-Video-CCTV_NEW"on which I conduct experiments enough?
I reloaded one"OpenVPN server: Mobil-Video-CCTV_NEW".
-
@testsia
Yes, it's sufficient to restart a single service, but the changes only affects to the restarted services naturally. -
@viragomann
Then I don't know what to do with this problem!
I will try to restart the whole server tonight -
Hey!
I rebooted the server but my problem was not solved.
I went further in my experiments.
I have generated a new "CA" certificate. Generated a certificate for the server, specified them in my OPENVPN configuration and now it works fine. But as soon as I return certificates that were not generated on PFSENSE, my problem returns. Does anyone have any ideas how to solve the problem? -
@testsia
Hi friends!
I went further in my experiments.
I installed Pfsense version 2.5, performed a restore from a backup.And OPENVPN works as expected!
I can conclude that the problem is Pfsense version 2.6.
I don't know where to write to inform the developers. But the problem is exactly Pfsense version 2.6.
It does not work with certificates that were generated outside Pfsense. -
@testsia
I determined what the problem is.
My client certificates do not have serverAuth and clientAuth ExtendedKeyUSage ("EKU") attribytes.
In version 2.6 this check is mandatoryCertificate does not have key usage extension 91.203.115.5:56352 VERIFY KU ERRORWho knows how I can disable this check on the server???
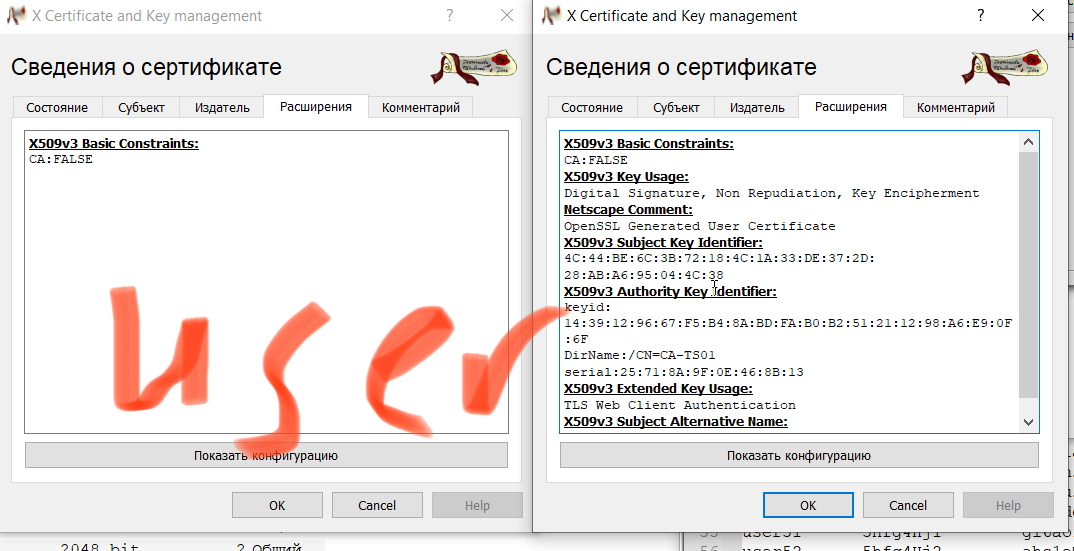
-
@testsia said in Certificate does not have key usage extension:
Who knows how I can disable this check on the server???
That was already answered upthread.
- Read https://redmine.pfsense.org/issues/13056
- Install the System Patches package
- Create entries in the System Patches package for
48cf54f850c5bf4fe26a8e33deb449807e71c204and47f2f4060d9e5b71c5c69356b61191fd2931383c - Fetch and apply both patches
- Uncheck "Client Certificate Key Usage Validation" in the OpenVPN server and Save
-
@jimp said in Certificate does not have key usage extension:
@testsia said in Certificate does not have key usage extension:
Who knows how I can disable this check on the server???
That was already answered upthread.
- Read https://redmine.pfsense.org/issues/13056
- Install the System Patches package
- Create entries in the System Patches package for
48cf54f850c5bf4fe26a8e33deb449807e71c204and47f2f4060d9e5b71c5c69356b61191fd2931383c - Fetch and apply both patches
- Uncheck "Client Certificate Key Usage Validation" in the OpenVPN server and Save
I am very grateful to you!
You helped solve my problem!
Thanks!!! -
-
@jimp said in Certificate does not have key usage extension:
Uncheck "Client Certificate Key Usage Validation" in the OpenVPN server and Save
Does this create a security issue? If so, is there a proper way within pfSense to set-up the certificate so that the EKU works?
The post at the link below indicates it does:
https://superuser.com/questions/1446201/openvpn-certificate-does-not-have-key-usage-extension