Remote Access / TLS + User Auth - Connection up but no LAN
-
@bingo600 I switched my connection to a cheap VPS to wireguard because it is heavily cpu constrained.
I also wonder with OpenVPN, you can set the "IPv4 Tunnel Network" to a /30, but also there is the option "Client Settings - Topology" where you can set subnet. Does this make sense? I don't know but would like to see a performant OpenVPN anyway. -
@bob-dig said in Remote Access / TLS + User Auth - Connection up but no LAN:
@bingo600
I also wonder with OpenVPN, you can set the "IPv4 Tunnel Network" to a /30, but also there is the option "Client Settings - Topology" where you can set subnet. Does this make sense? I don't know but would like to see a performant OpenVPN anyway.I think the first "IPv4 Tunnel Network" , sets the IP-Connect net , used for server & client(s).
The 2'nd : "Client Settings - Topology" /30
Specifies the "Topology" ... Aka. The way the first net is used.
And a /30 is "hardcoded" to give first ip to the server , and the 2'nd to the client.So in a "bit" cryptic way, they both make sense.
Ps: Read my Edit's in the previous post.
/Bingo
-
@bingo600 and the others
I have on the server side:
Client side:
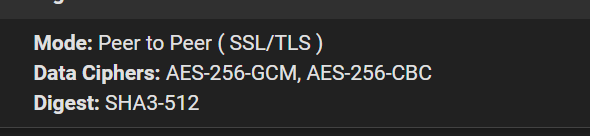
Because of the mode i'm not sure if this can work?
Client Ovverrides Server
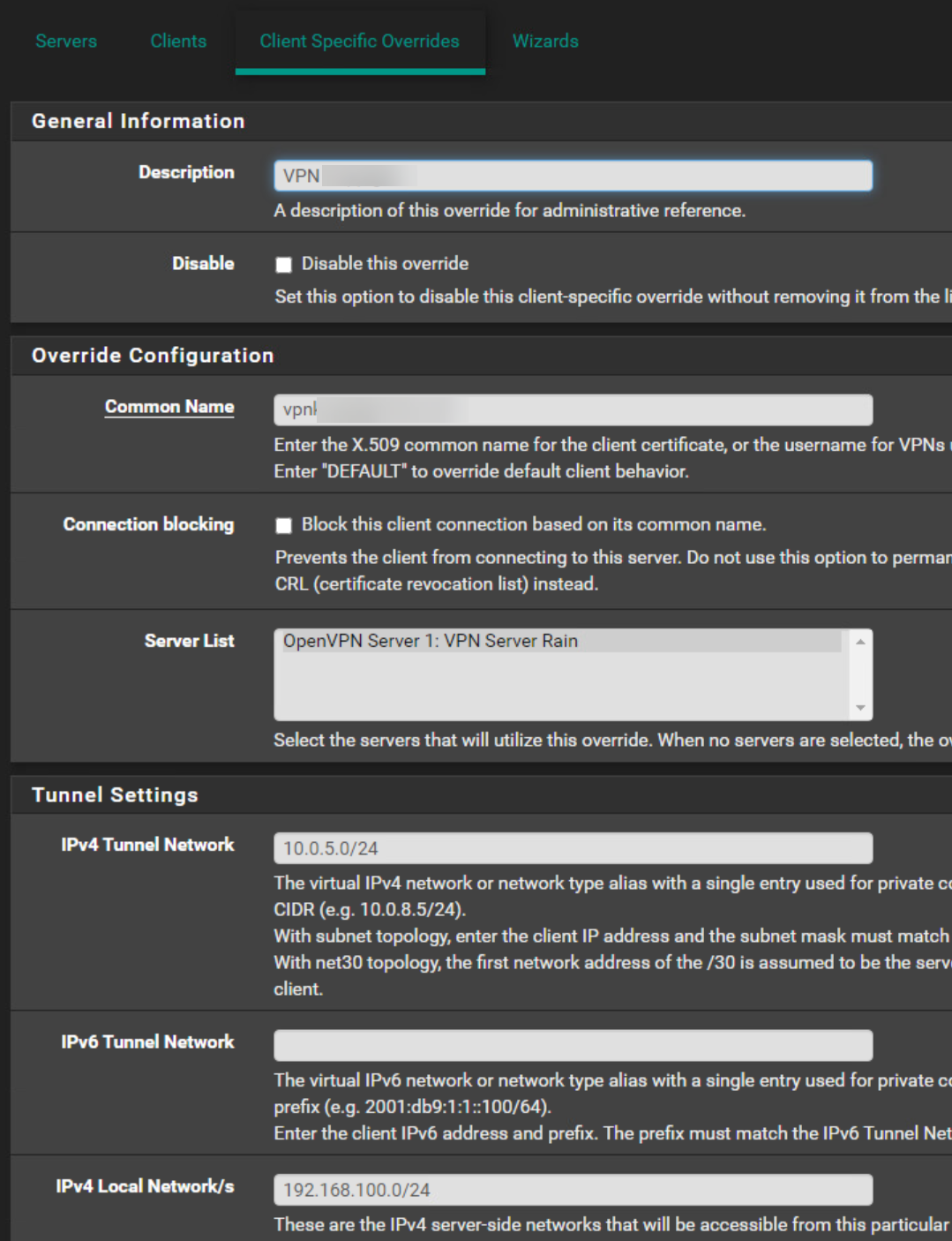
I have added it also on the client side.
-
@hispeed
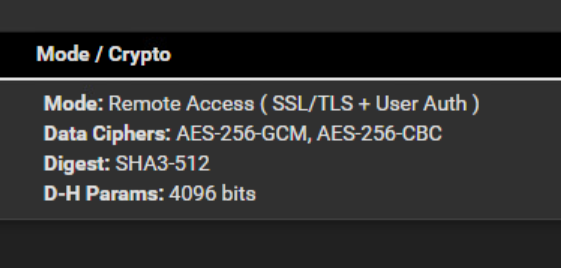
That seems a bit strange. To use SSL+TLS+Userauth on Server side , and not the same on client side (only SSL + TLS)Is this the client a Person logging in or a PC (like another pfSense) ?
Userauth would not be feasible if it's not a person logging in.If it's a S2S connection made by 2 PC's , i'd just use SSL/TLS.
/Bingo
-
@hispeed
Also in the CSO you must not use a /24 tunnel.
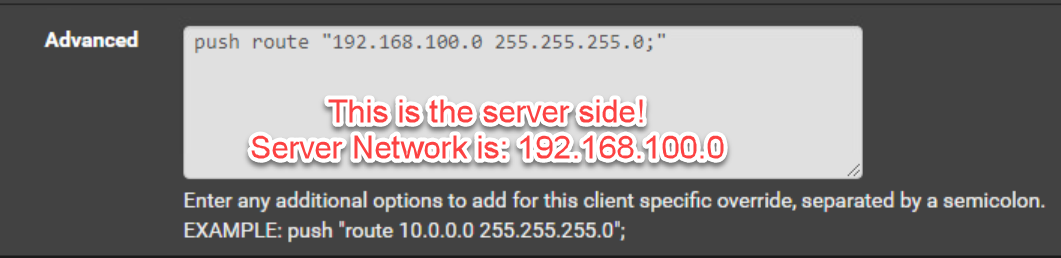
How to set the tunnel, depends on the server topology. If it uses a /30 set also a /30 subnet in the CSO. If the server uses subnet topology set a single IP out of the tunnel.Also the "push route" in the advanced settings is superfluous. This is already done by the "Local Networks" field.
-
The client is also a Pfsense so both are Pfsense (+ version).
Ok I haven't changed that yet concerning the mode because I would like to have 2 security steps (TLS Key + Username Password).@viragomann
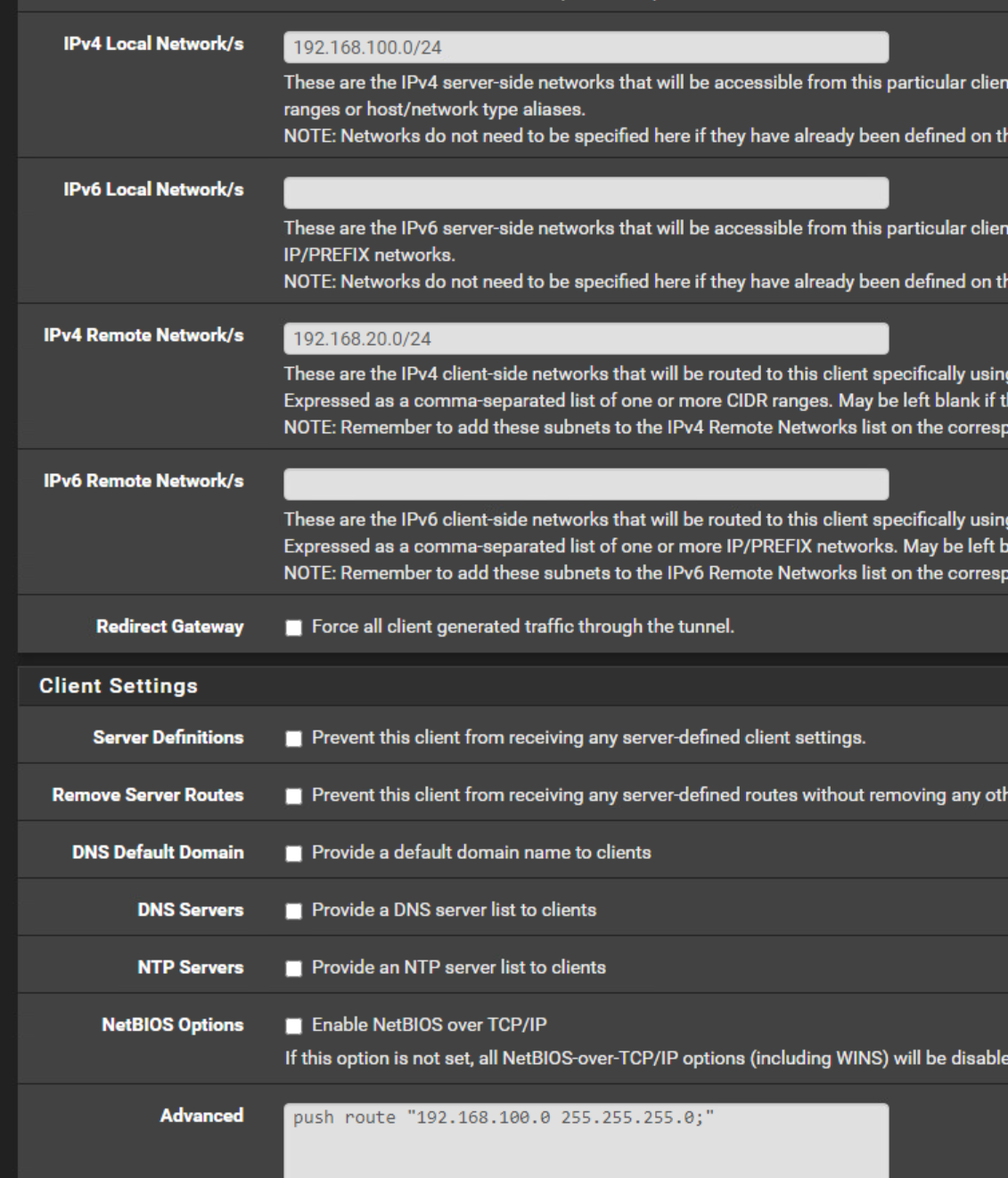
Ok I removed the push route.Server:
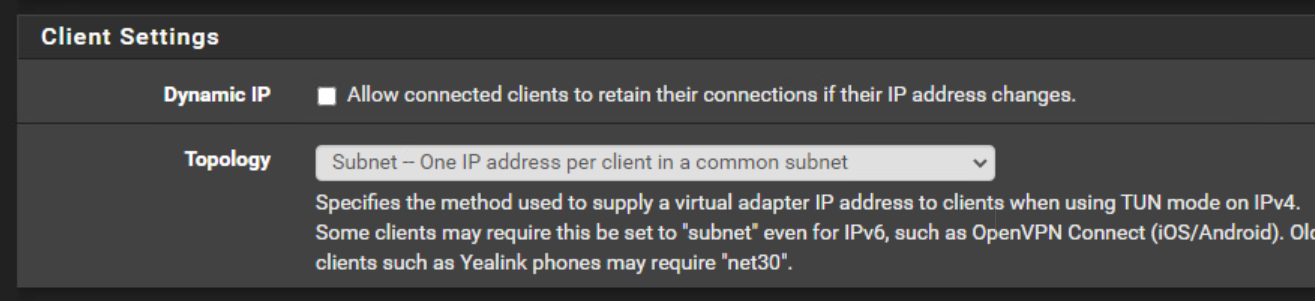
So I use at the moment subnet.
Client:
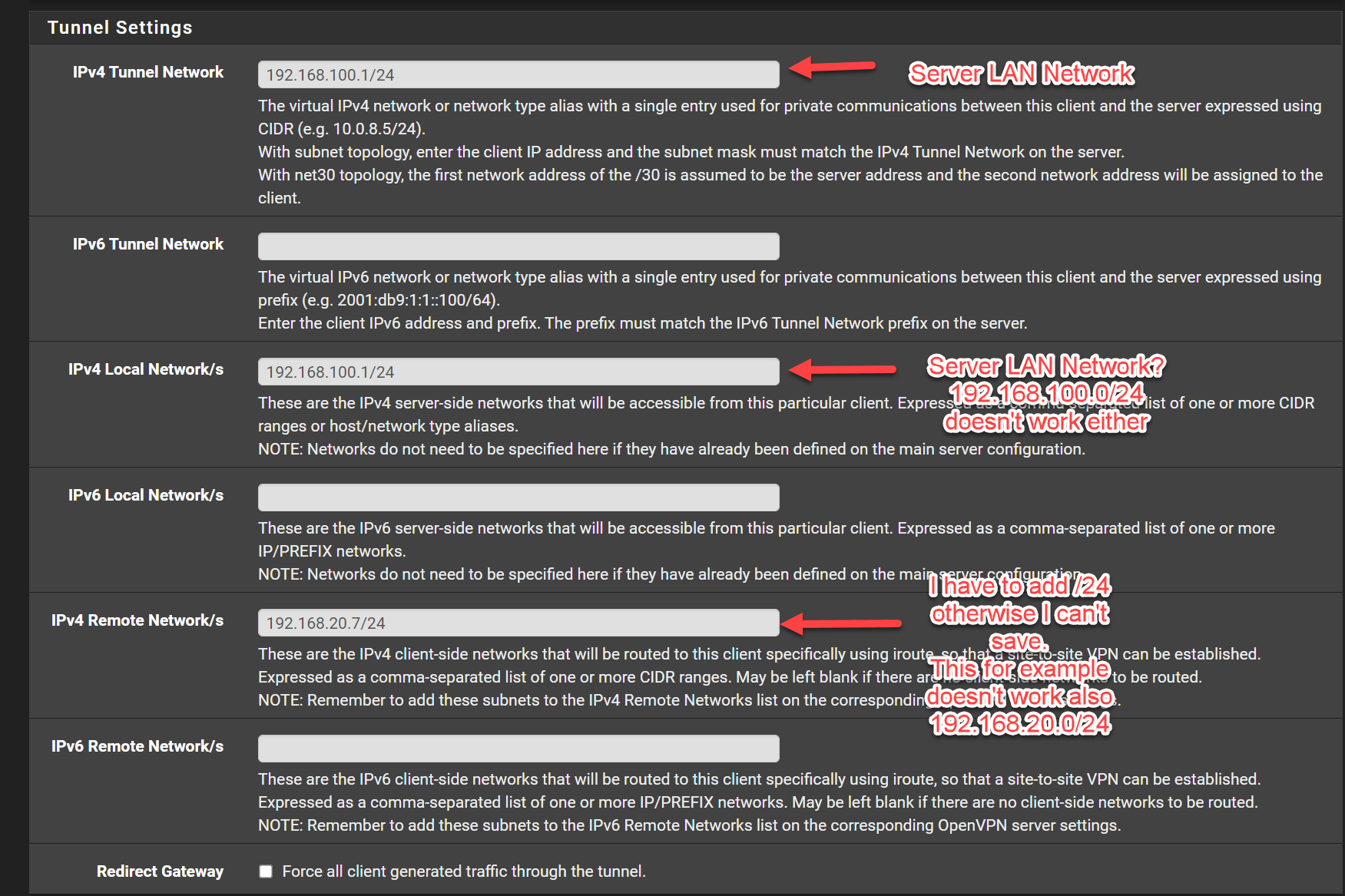
Maybe I have something else wrong in my configuration?
-
@hispeed said in Remote Access / TLS + User Auth - Connection up but no LAN:
Client:
This looks rather like the client specific override page. However, it's the right place to do your settings.
But you have something to correct:In IPv4 Tunnel Network you have to state the clients virtual IP. This must be part of the servers tunnel network, when using subnet topology, as mentioned.
So since your server is 10.0.5.0/24, enter here "10.0.5.222/24".IPv4 Local / Remote Networks must be network addresses! Yours are IPs, but not networks.
So into the IPv4 Local Network/s box enter "192.168.100.0/24",
and into IPv4 Remote Network/s (clients side LAN) enter "192.168.20.0/24", if that's the proper network, you didn't mention. -
@hispeed What rules do you have on the OpenVPN interface?
-
I set up your settings, tunnel is up but still i can't reacht the remote network.
On both side I have this rule as the first rule.
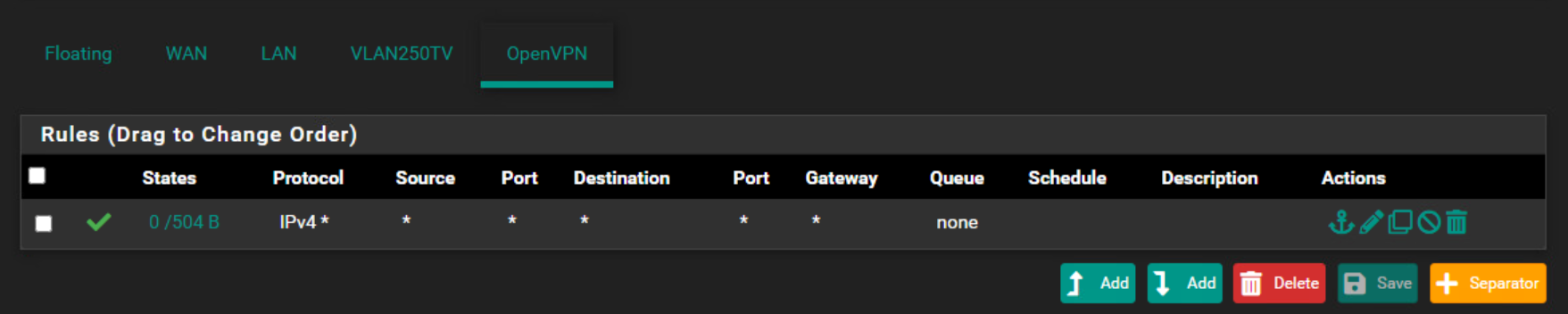
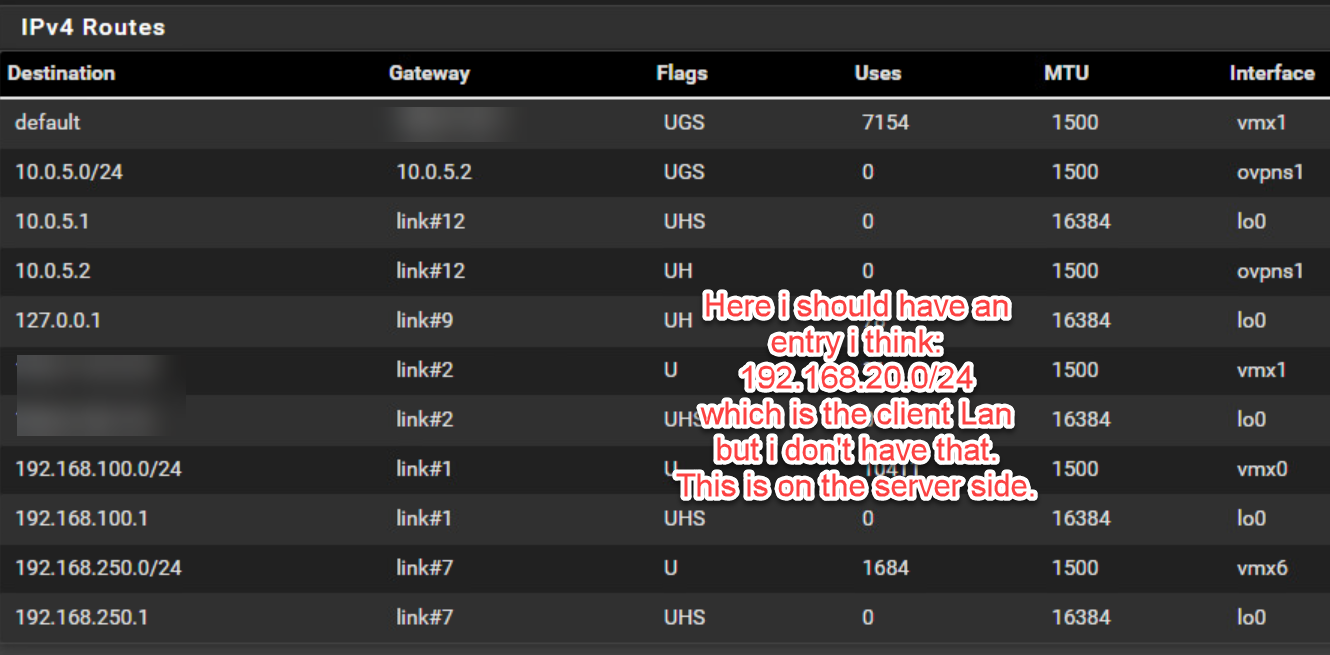
I'm pretty sure this is because I don't see the IPv4 Routes entries in Diagnostic Routes belonging to the remote network from the client when I look on the server side.
-
@hispeed Can you post the full vpn config from both sides?
You have snippets of each and they're getting jumbled.Also, what does the openvpn logs show?
Do you have the user/pass in the clients config?
Do you have all the right cert's?Why are you opening ports on the client side?
-
Hi @Jarhead
Here are the images you requested:
Server side:
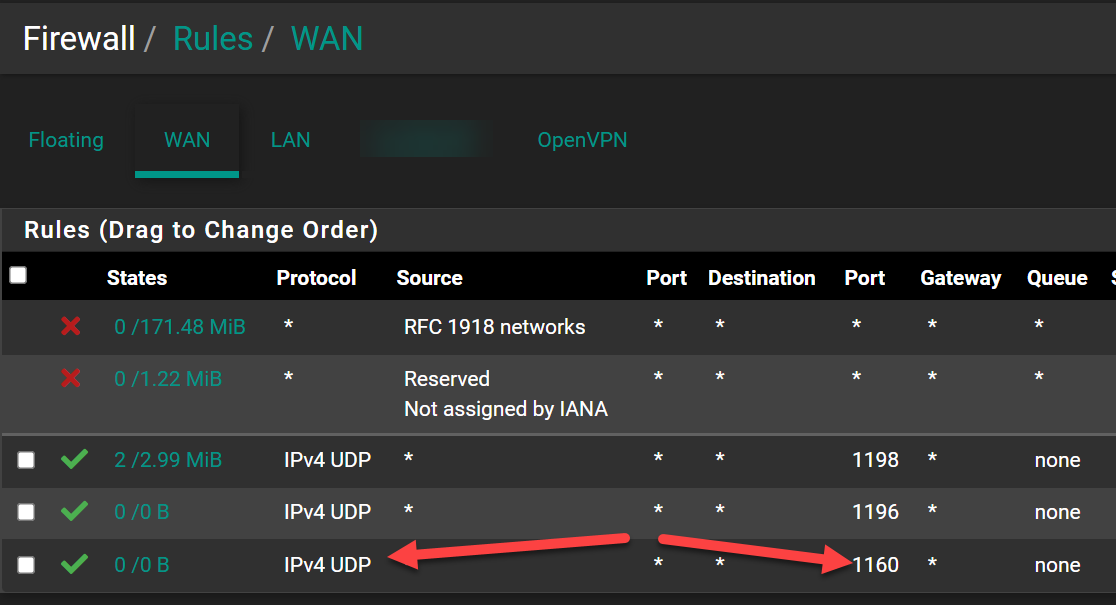
Firewall Rules OpenVPN
NAT Outbound
OpenVPN Server Configuration
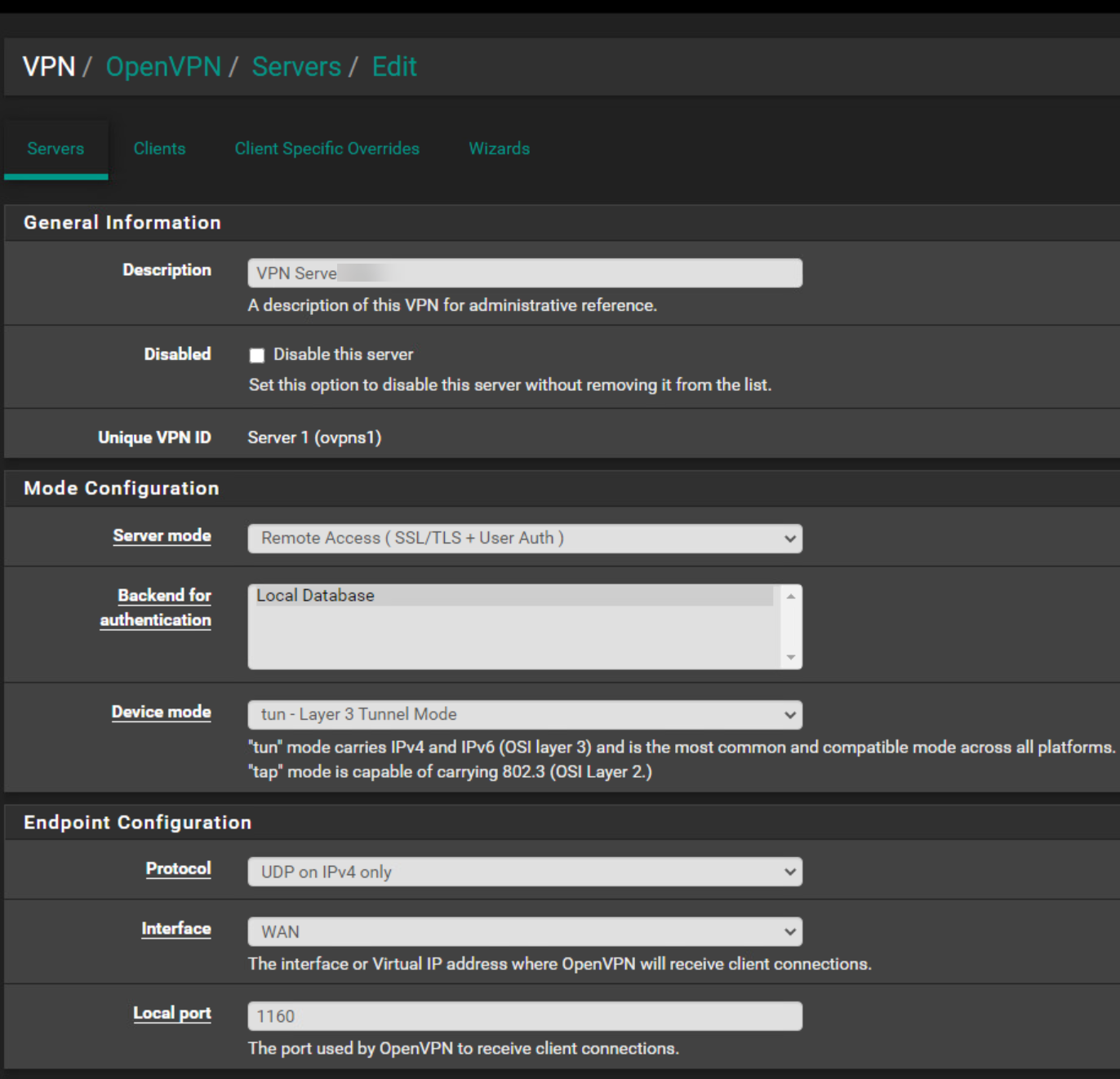
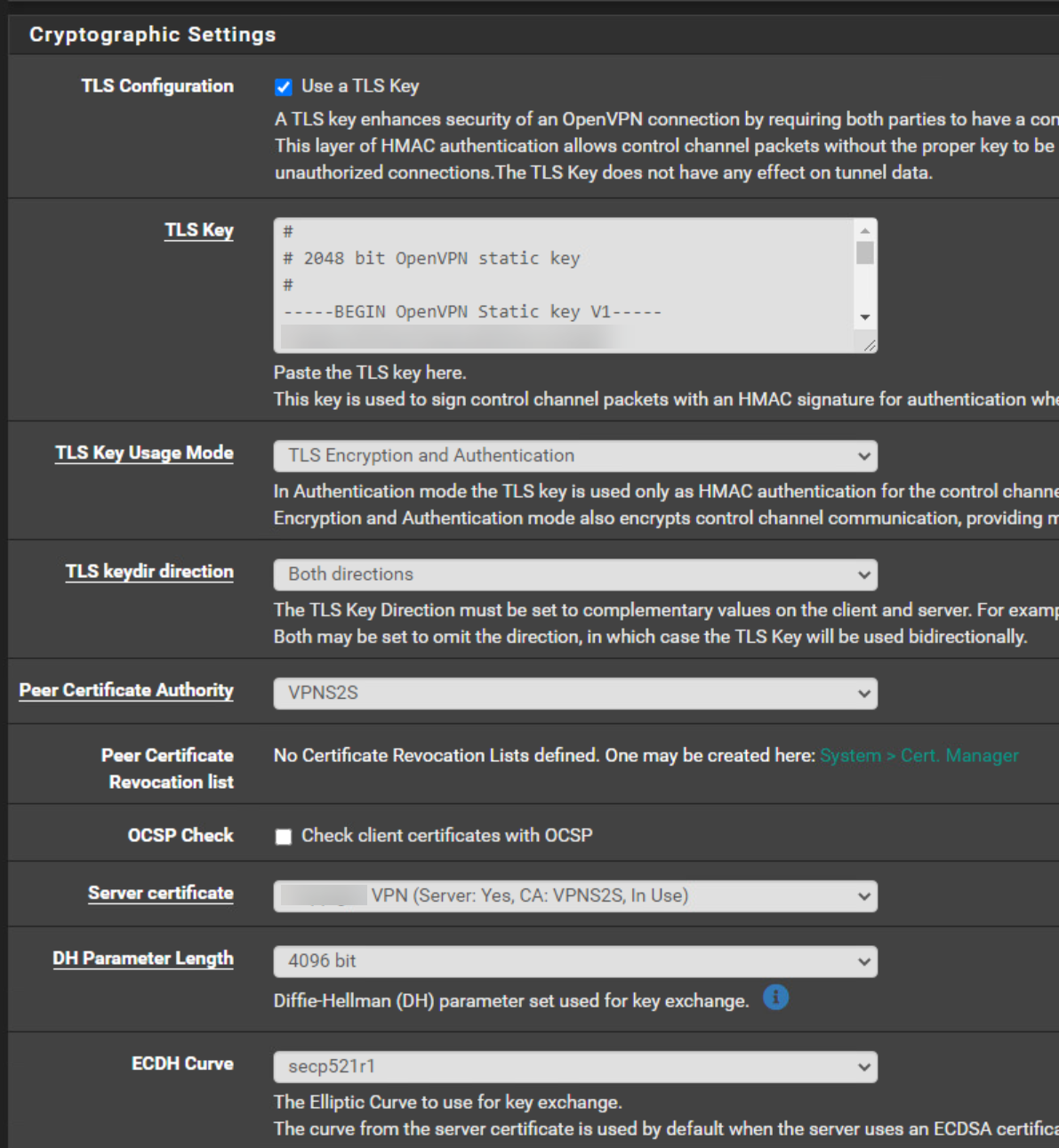
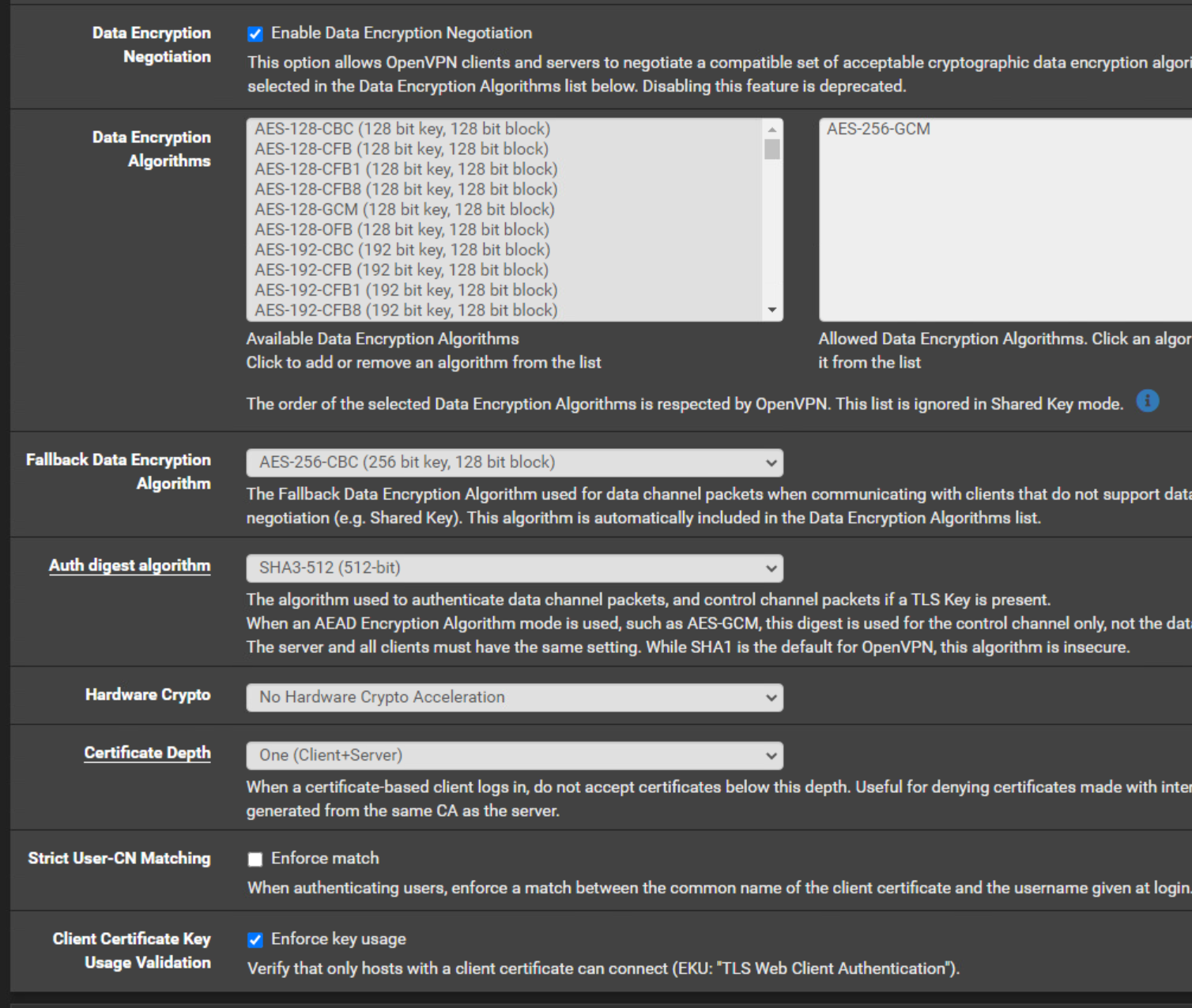
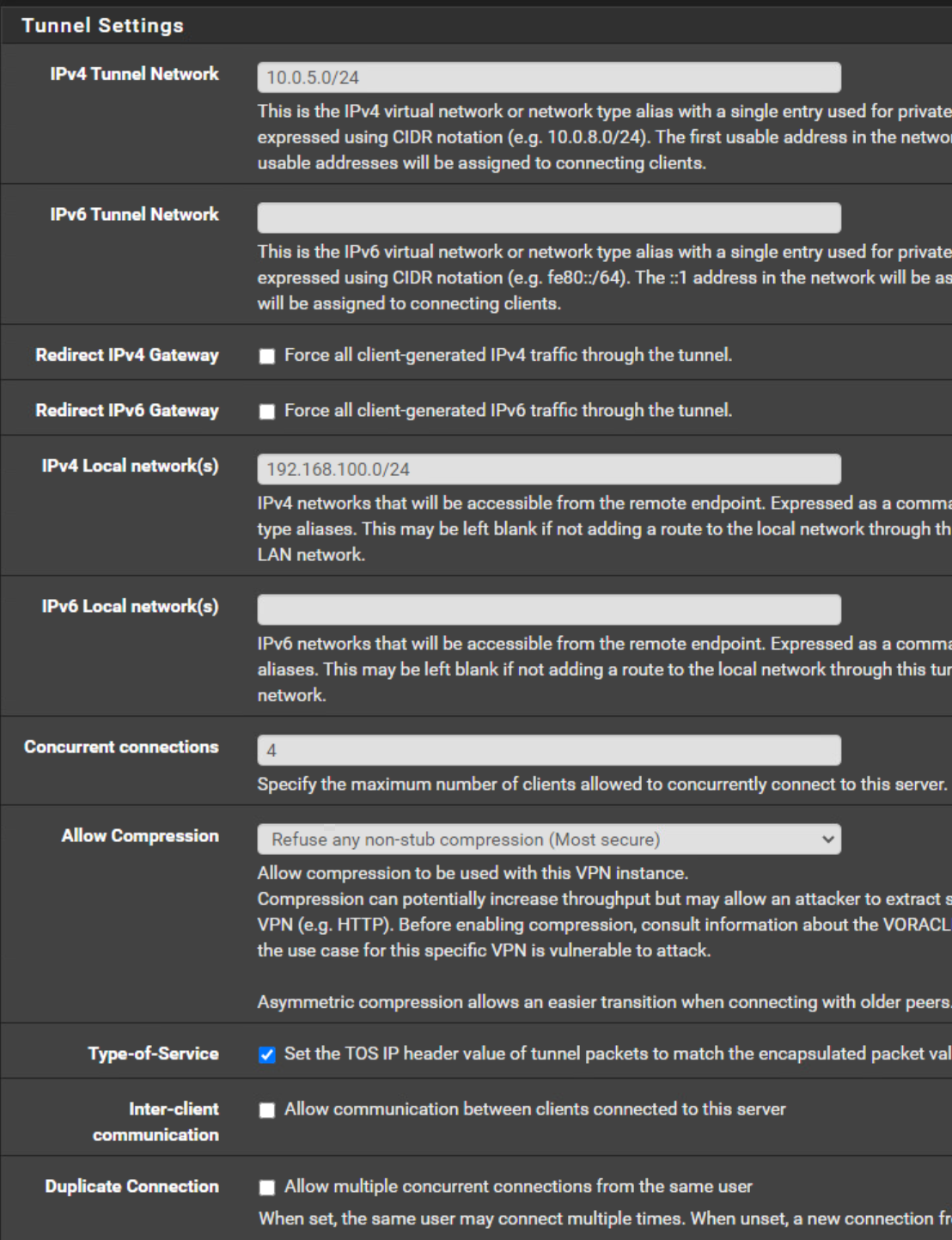
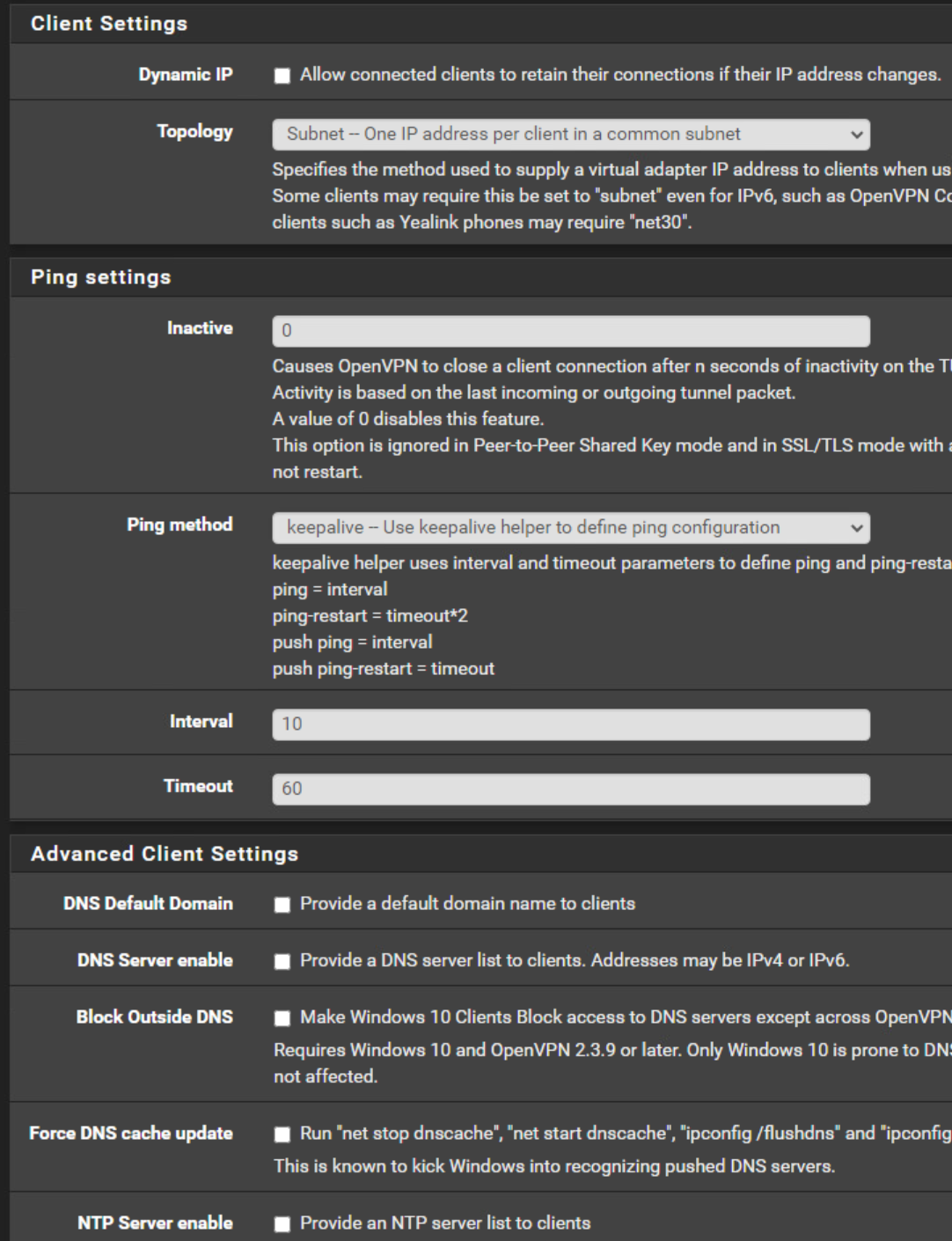
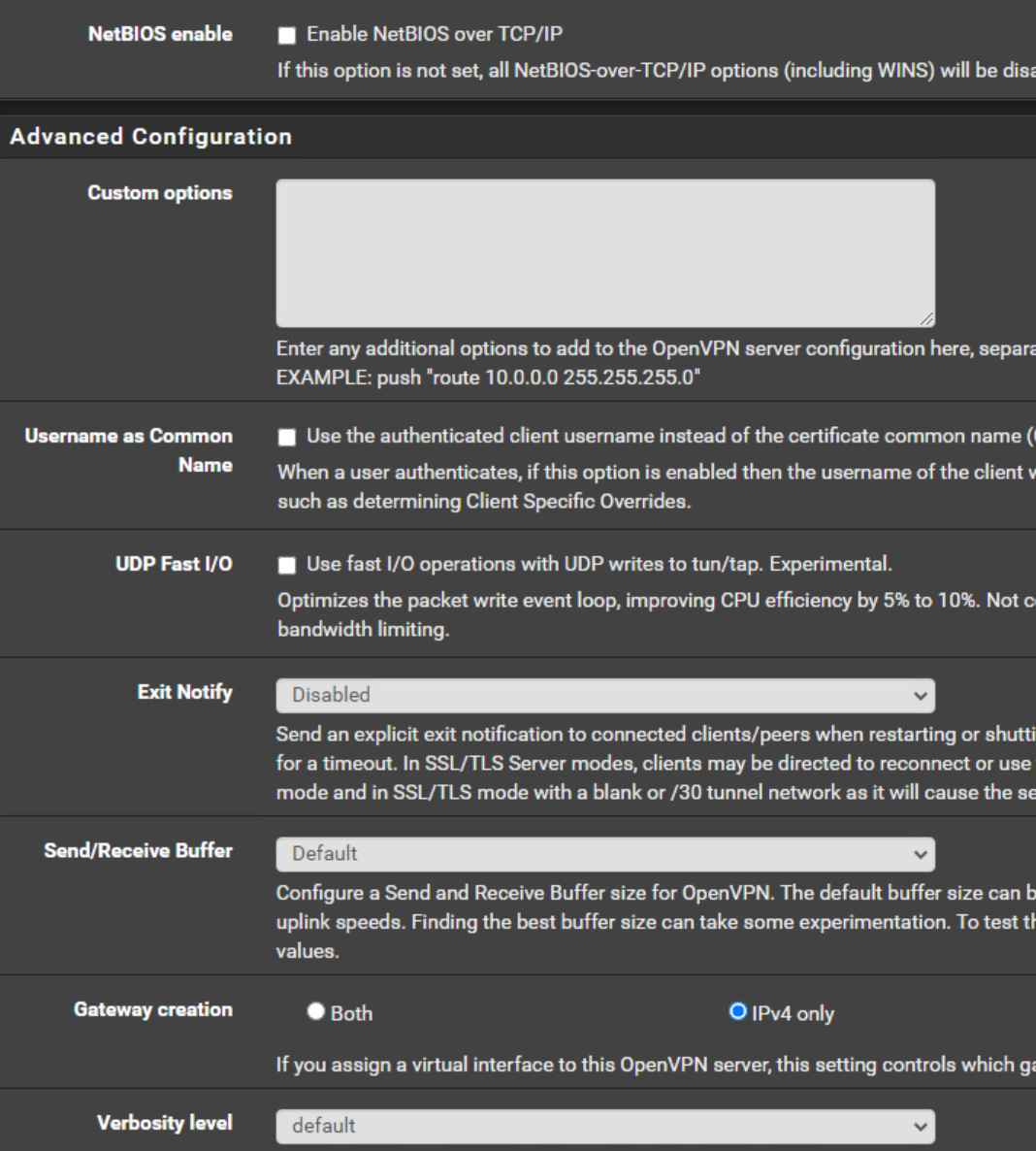
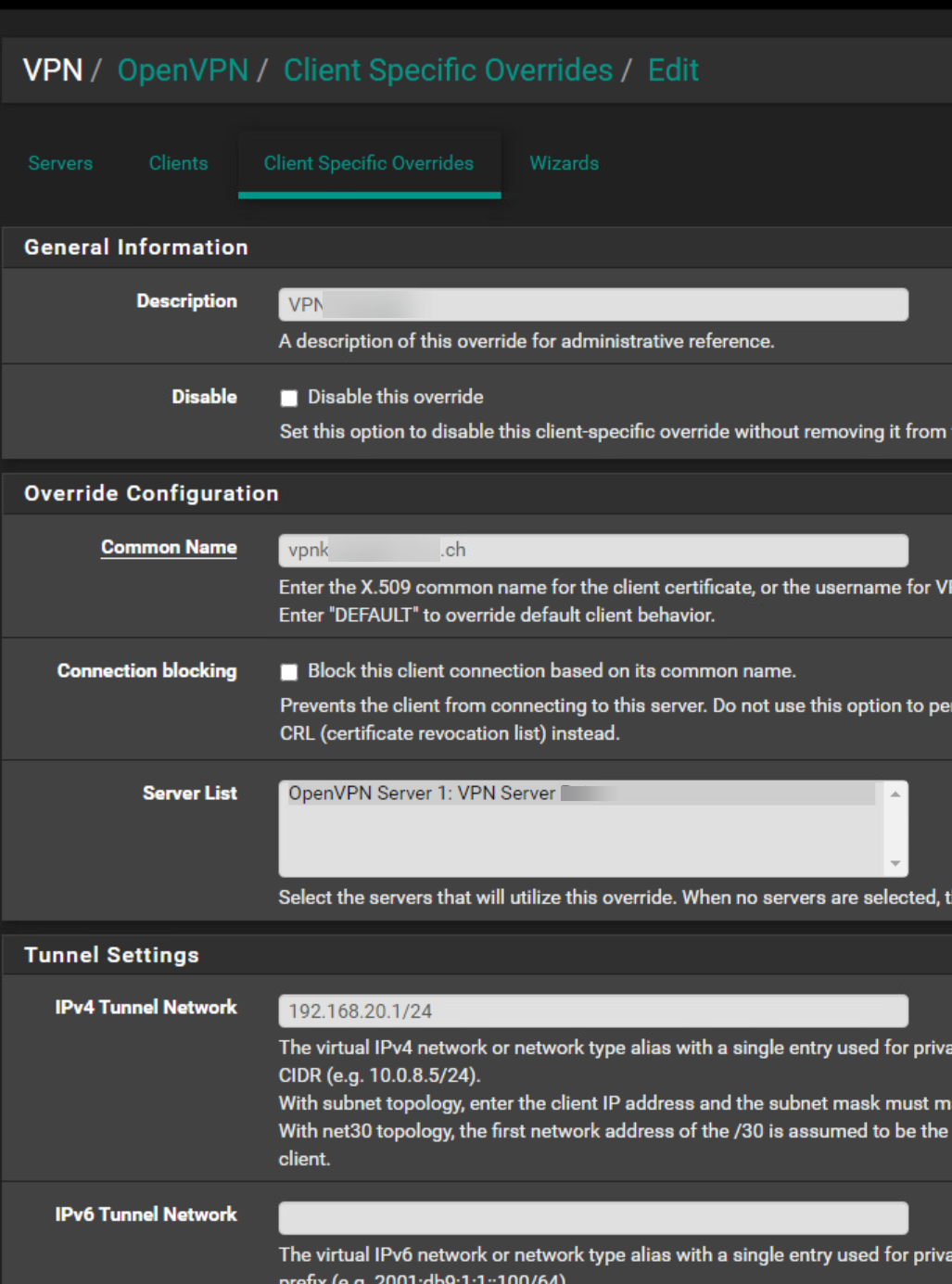
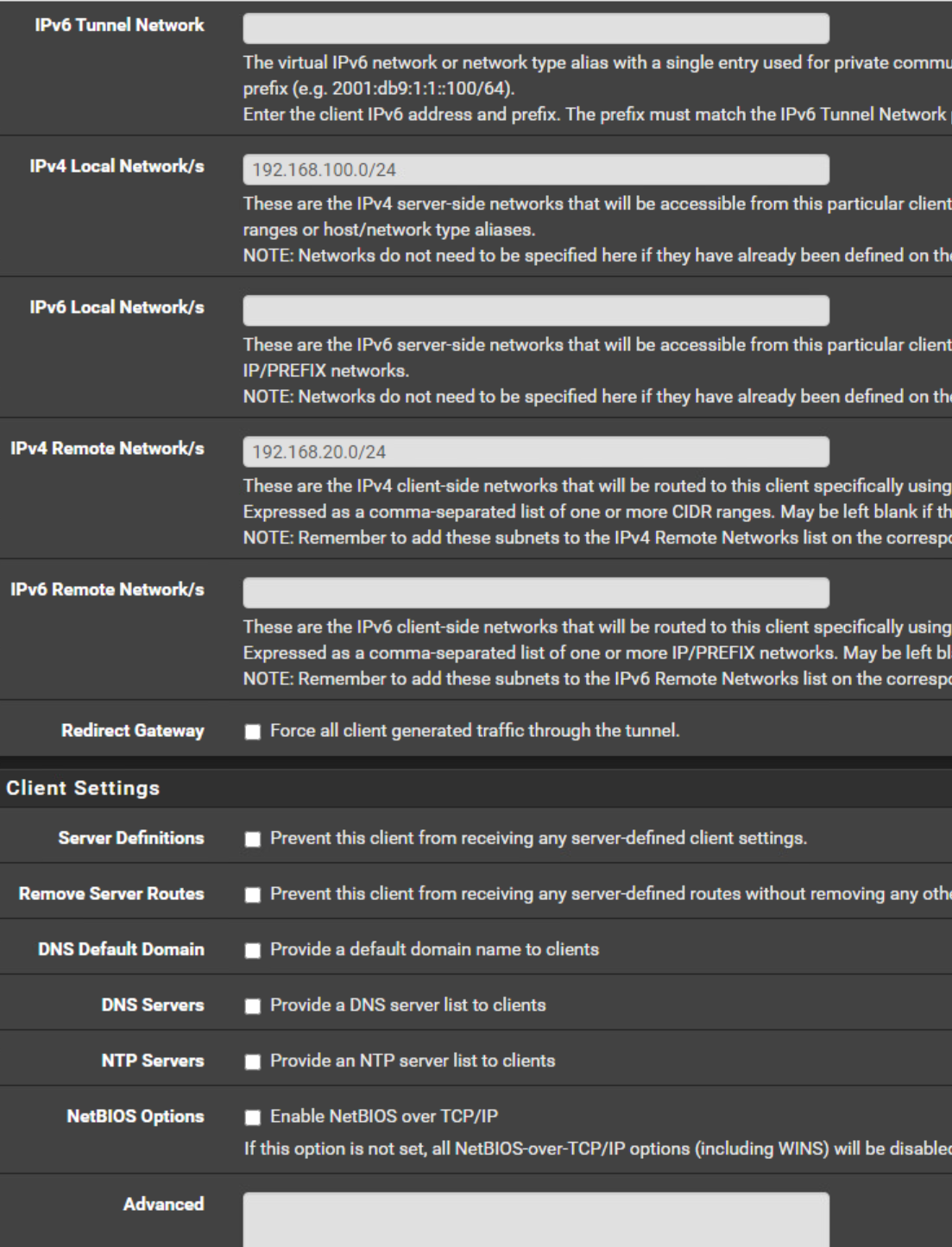
OpenVPN Server Client Specific Overrides
Server-Side Log:
OpenVPN Log
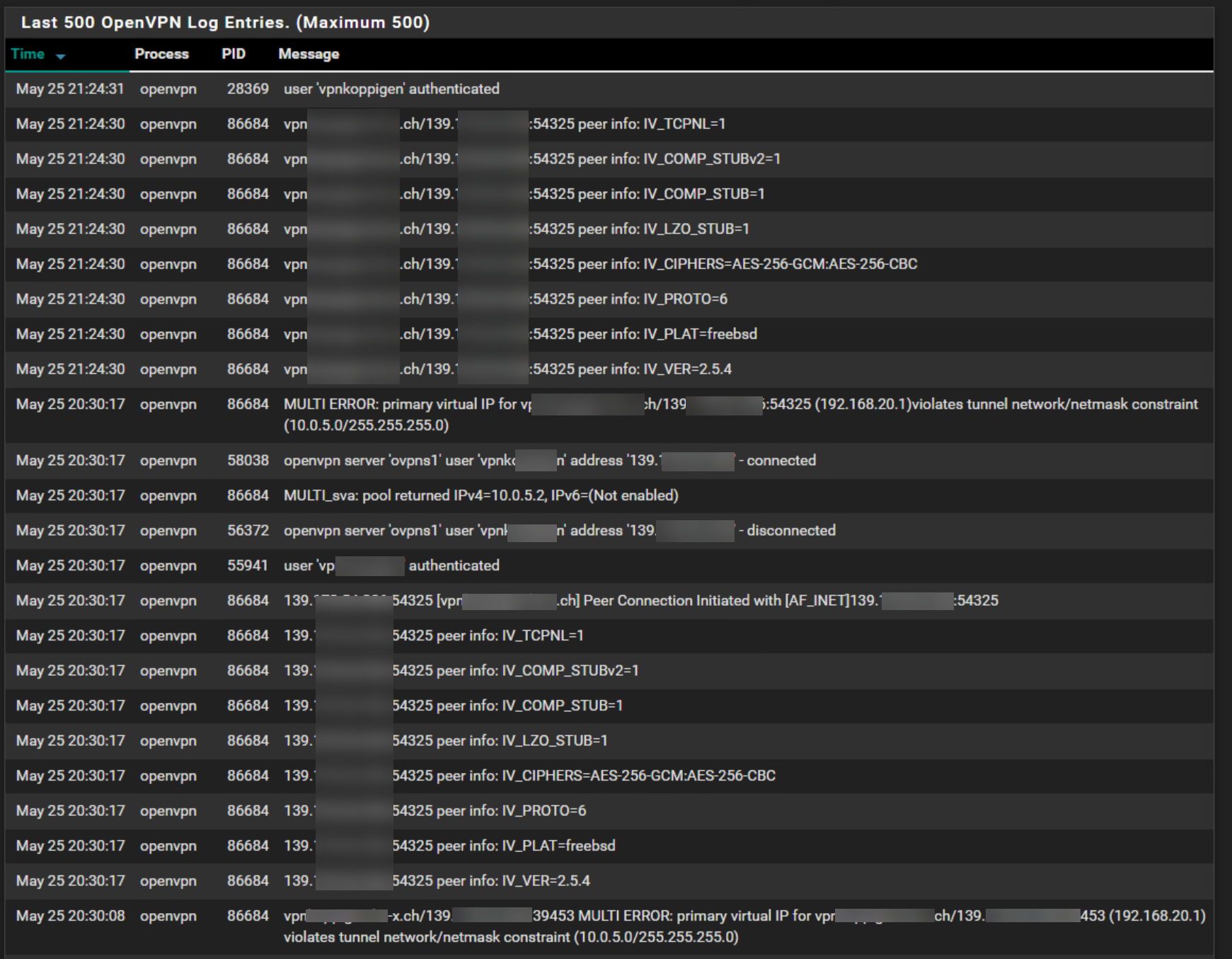
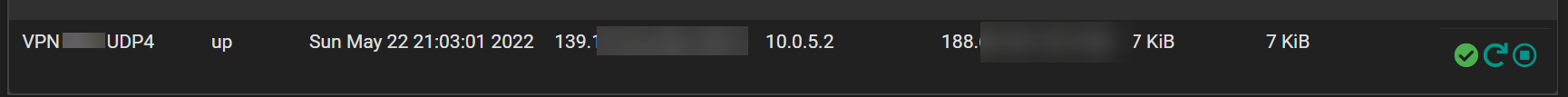
OpenVPN Status:
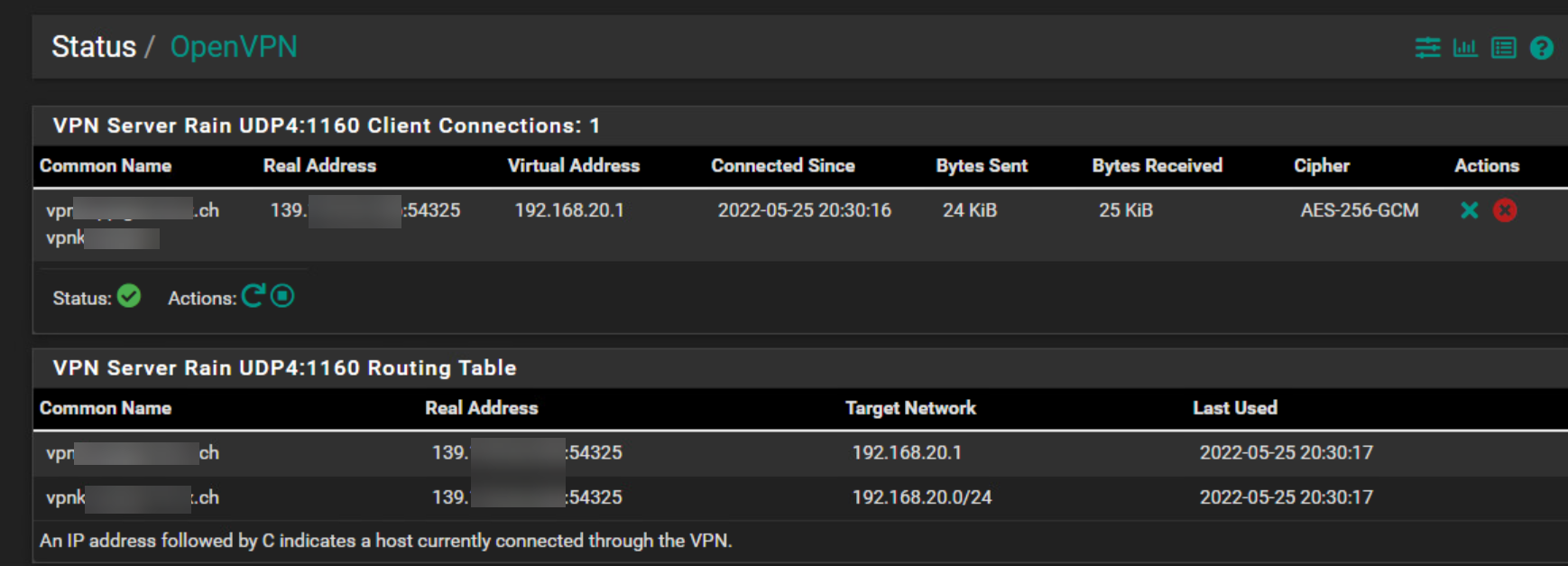
Answers for your questions:
Do you have the user/pass in the clients config?
Yes I will post in a second post the client config.Do you have all the right cert's?
As far as I know i'm pretty sure I have checked it and if they wouldn't be correct the connection is not working.Why are you opening ports on the client side?
Which ports do you mean? I don't know I didn't open any ports as far as i know. -
@hispeed
So this is not, what I told you to set up. -
I hope this works since I'm doing a double post.
This is the follow up and client side configuration. The client side is also a Pfsense, so the connection will be from Pfsense to Pfsense.Client Side
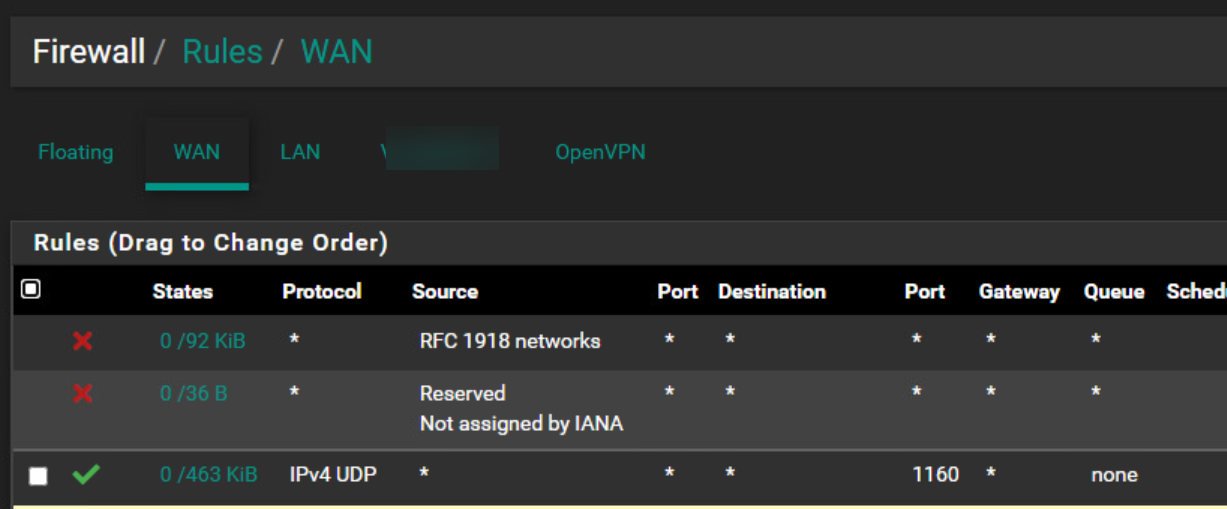
Firewall Rules OpenVpn
NAT Outbound:
OpenVPN Configuration:
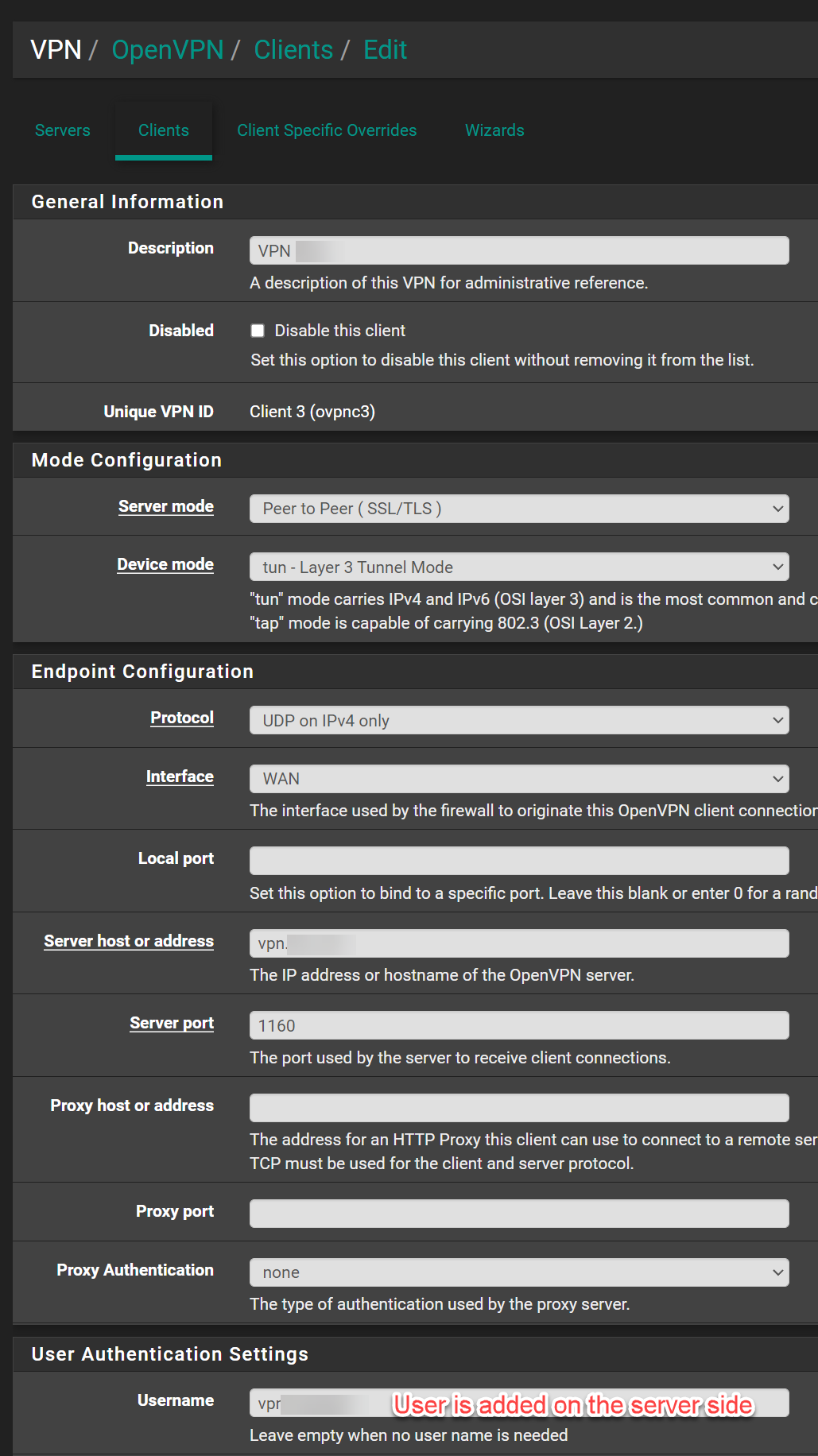
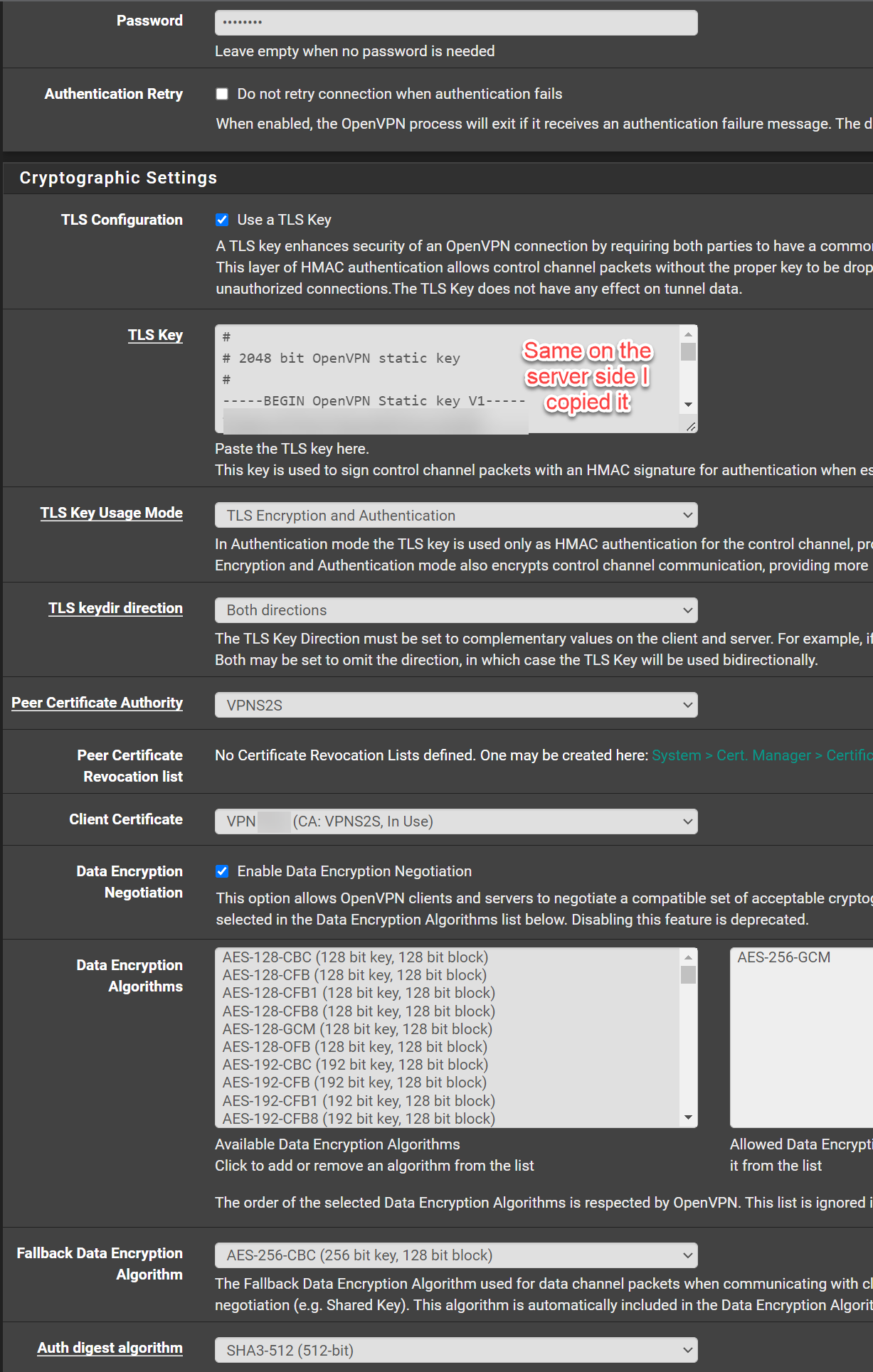
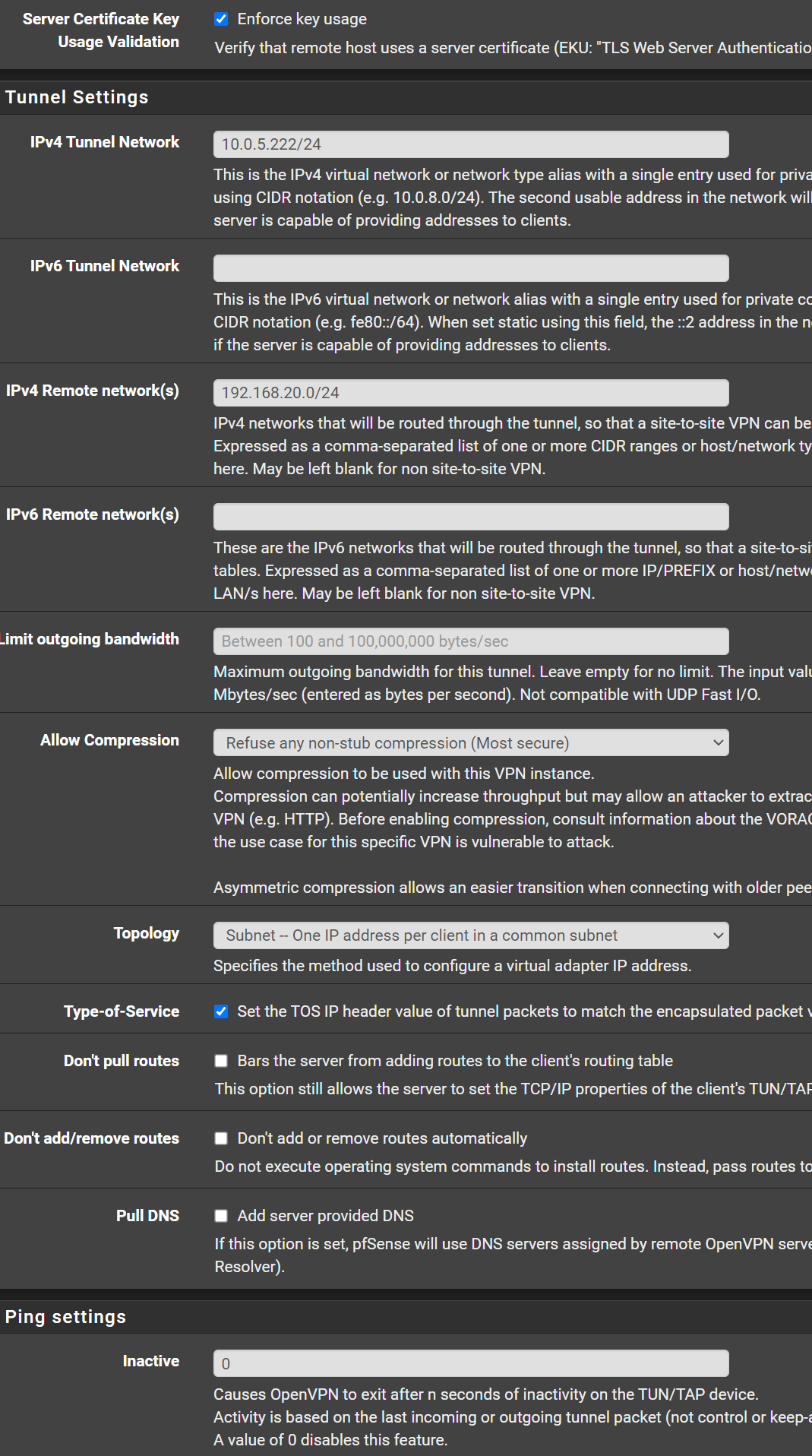
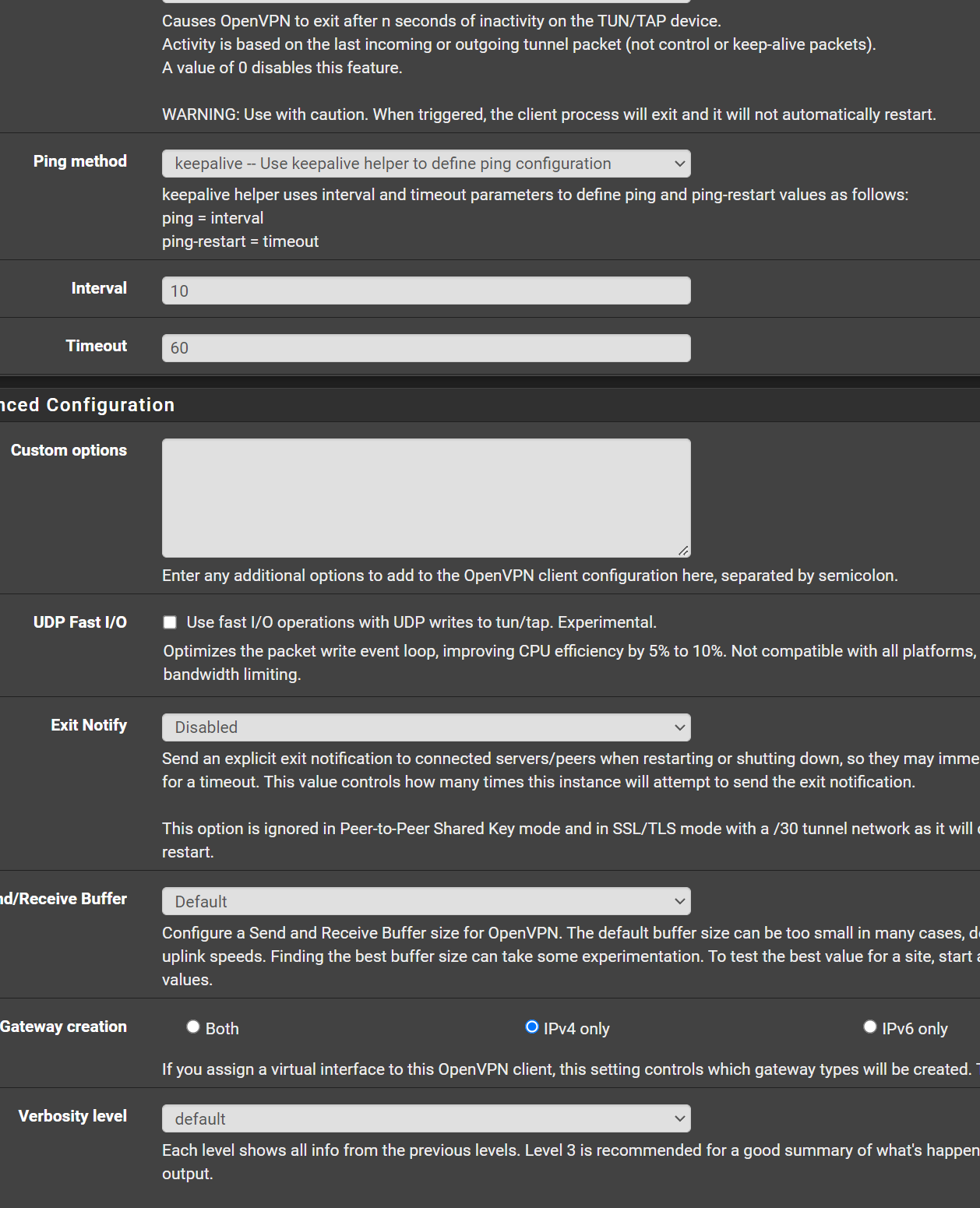
Client Log OpenVPN:
Any help is welcome.
-
@hispeed Get rid of the client specific override.
The tunnel networks have to be the same. Copy the subnet from the server to the client. 10.0.5.0/24
-
@hispeed
You're messing up the settings, again and again.Configure the CSO as I suggested above, please. The tunnel network is wrong again.
In the client settings you must not state a tunnel IP. You can leave it blank or enter the tunnel network equal to the server settings.
And the Remote Network is wrong! This is your local network. In the Remote Networks box enter the server sides network! -
@hispeed Forgot, in one of your pics you showed port 1160 open on the client side
-
@Jarhead and @viragomann
I have checked it and corrected it. Yes you were right I messed it up.
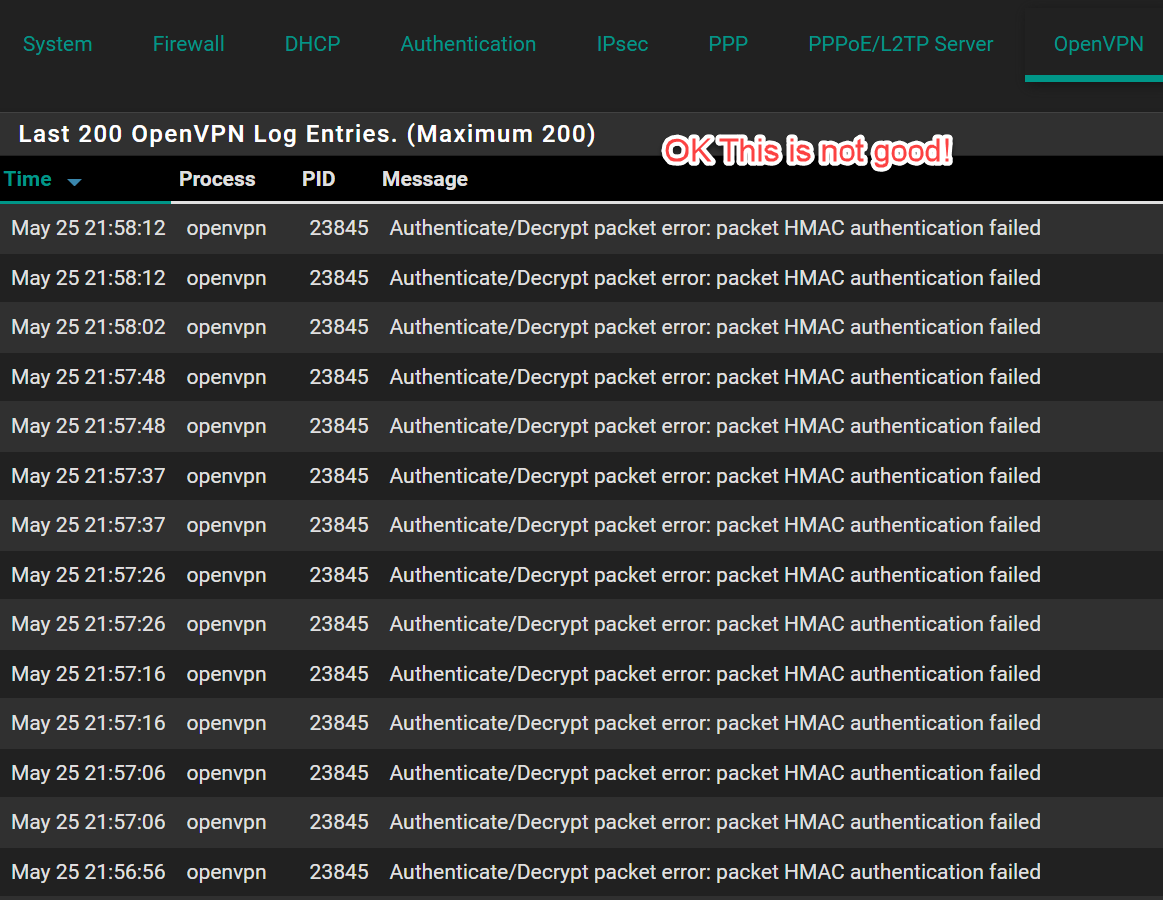
I still get on the client this "Authenticate/Decrypt packet error: packet HMAC authentication failed" error. So i exported the CA and Client certifcate new.
Could it be because I used an ECDSA?
Keytype: ECDSA
secp521r1 [IPsec][OpenVPN]
Digest Algorithn: sha512I also don't see on the server side no route to the 192.168.20.0/24 network into the tunnel: 10.0.5.0/24. So I think there is a problem. I also have to set the gateway manual on each interface on the server side because of my WAN configration which uses configuration override.
-
Breakthrough
Custom options on the server Side:
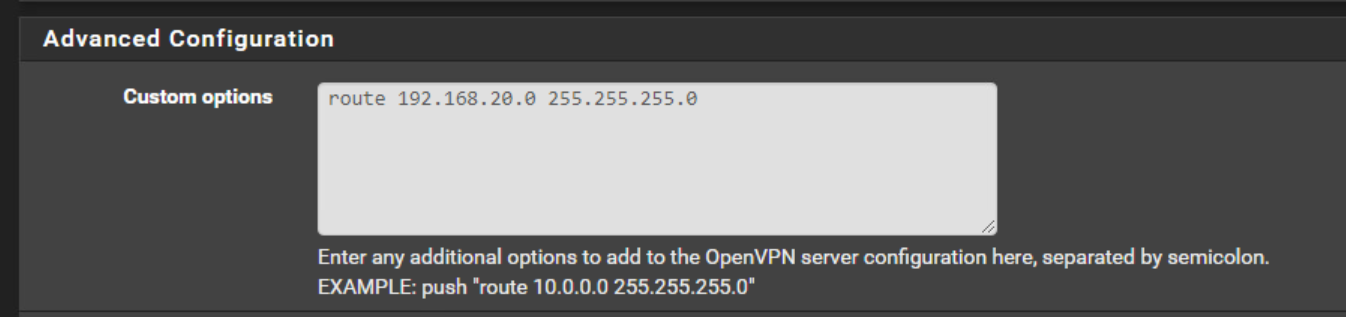
i added it but not on CSO config.
Now I can connect to the client side.
But why?
I see this has now ben created in Diagnostics / Routes:
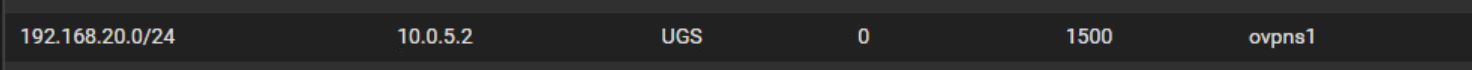
-
@hispeed said in Remote Access / TLS + User Auth - Connection up but no LAN:
I still get on the client this "Authenticate/Decrypt packet error: packet HMAC authentication failed" error. So i exported the CA and Client certifcate new.
Could it be because I used an ECDSA?I'm still on older OpenVPN versions which have no support for this. So I don't know.
Custom options on the server Side:
i added it but not on CSO config.
Now I can connect to the client side.
Yes, I think, that was the missing link, but didn't consider this.
As far as I know, the route option is necessary to add the route in pfSense to OpenVPN. But also in the CSO you need to enter the clients network into "IPv4 Remote Networks", which is needed to set the route to the proper client within OpenVPN.
-
@hispeed So I tried this in my lab last night and could not get it working although it should.
To be honest, you're wasting your time. Just do a peer to peer with a /31 and be done with it.
But if you want to keep trying....
First, you do not need a CSO with only one client connecting. As I said, get rid of it. Not doing any good.
Second, with remote access as the type, you're basically creating a "road warrior" vpn. Typically meant for one client to connect to one site. It doesn't enable other clients on the remote network access to the vpn. That's why I say just do the peer to peer as it's meant to be used. But you can configure a remote access for the entire remote LAN, see here:https://community.openvpn.net/openvpn/wiki/HOWTO#IncludingmultiplemachinesontheclientsidewhenusingaroutedVPNdevtun
Again, I tried it, it's a waste of time when there's an option made explicitly for what you want.
The biggest problem with remote access is the config doesn't give you the option to set "Remote IPv4 Networks" and peer to peer does.By the way, that error you're seeing has to do with the certificates. Did you create all certs on the server, then export the needed certs to the client, or did you create certs on server and create certs on client?