Request for examples of working guest network rules
-
I would like to see the examples (screenshots) of other users’ guest network interface firewall rules. I know that those rules can make extensive use of aliases. Please explain what your aliases stand for, if your rules contain them.
Thanks much!
-
Here are my rules. My guest WiFi is on VLAN 3.
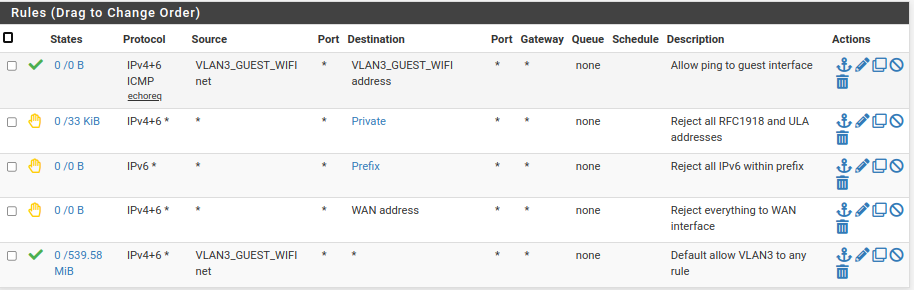
The "Private" alias is all RFC1918 IPv4 and Unique Local IPv6 addresses. "Prefix" is my entire /56 prefix.
These rules allow a guest to only access the Internet and to ping the interface.
-
@dominikhoffmann
Depends entirely on what you consider "guests".
To me, I consider them actual guests, not family, not friends, just guests. So I have my guest network pretty locked down and there was a post a while ago with someone saying "my guests won't be able to do a speedtest". Yeah, and?? I don't care if guests can test my internet speed. That's why it's a guest network.So if you consider guests anyone who doesn't live at your house but still may be able to access some LAN (etc) resources, you'll have to take that into account.
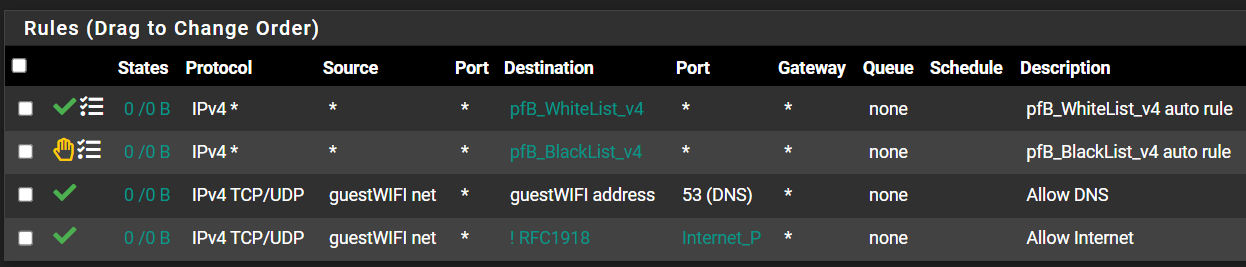
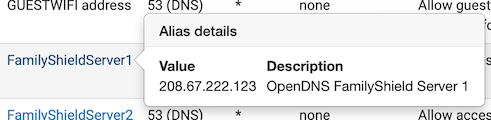
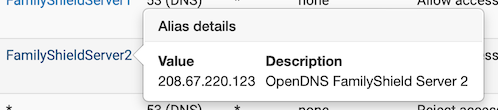
Internet_P is ports 53, 123, 80, 443 and 853.
I had to add port 53 above it because I block RFC on the Internet_P rule which would also have blocked 53. I use that Alias elsewhere so I didn't edit it to take 53 out. -
-
@dominikhoffmann "This Firewall" is an alias for all interfaces on the firewall. If you want guests to access any interface, go for it.
Probably not what you want though.My rule is a bit odd. See the !, that inverts the source/destination (source only in mine). So I'm actually blocking rfc in a pass rule.
Some frown on doing that to keep things clearer and I would agree with that, this is the only place I use it and I'll never have to change anything in that rule so it won't be confusing. So no, wouldn't be able to use "This Firewall" there and wouldn't want to because of the first paragraph. -
@dominikhoffmann said in Request for examples of working guest network rules:
Can in your first “Allow” rule the destination be replaced by “This Firewall?”
No, my rule allows ping only to the VLAN interface.
-
@jknott said in Request for examples of working guest network rules:
@dominikhoffmann said in Request for examples of working guest network rules:
Can in your first “Allow” rule the destination be replaced by “This Firewall?”
No, my rule allows ping only to the VLAN interface.
I believe, I don’t quite understand the distinction. Would you mind explaining? I am still somewhat of a newbie.
-
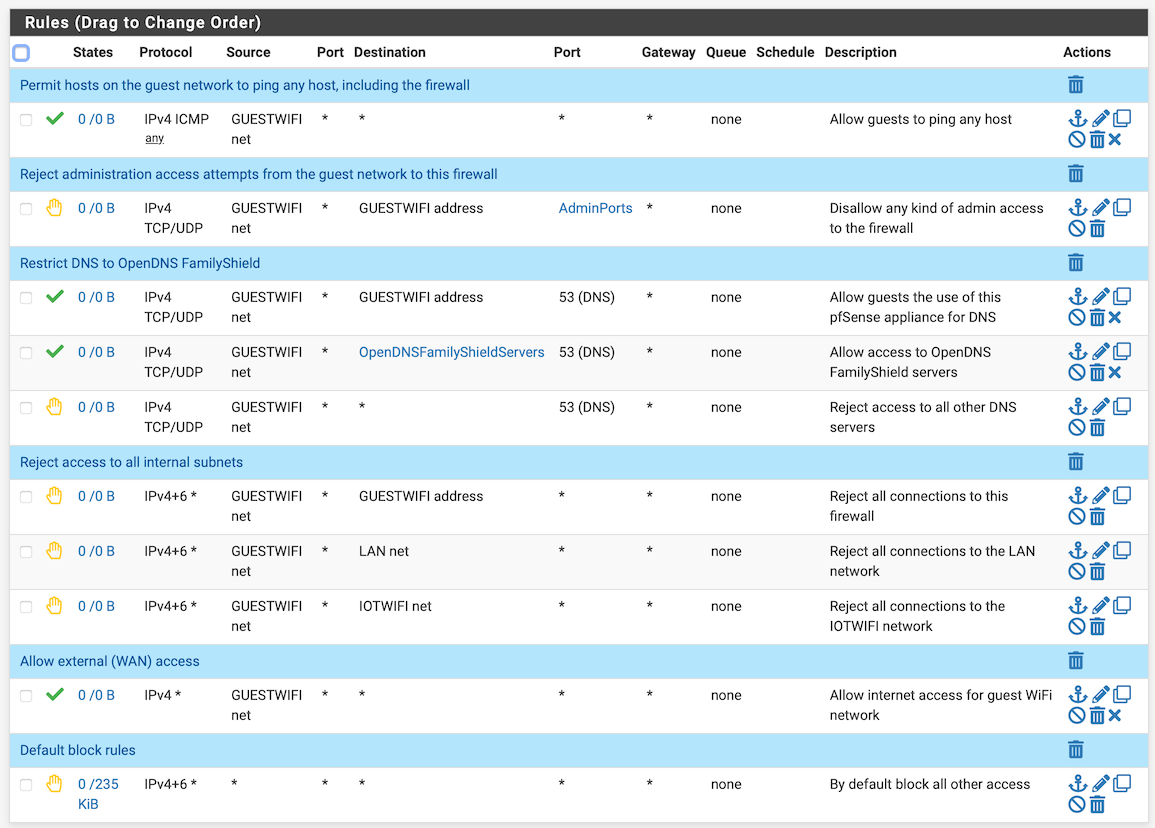
Based on you guys’ input, this is what I have come up with:
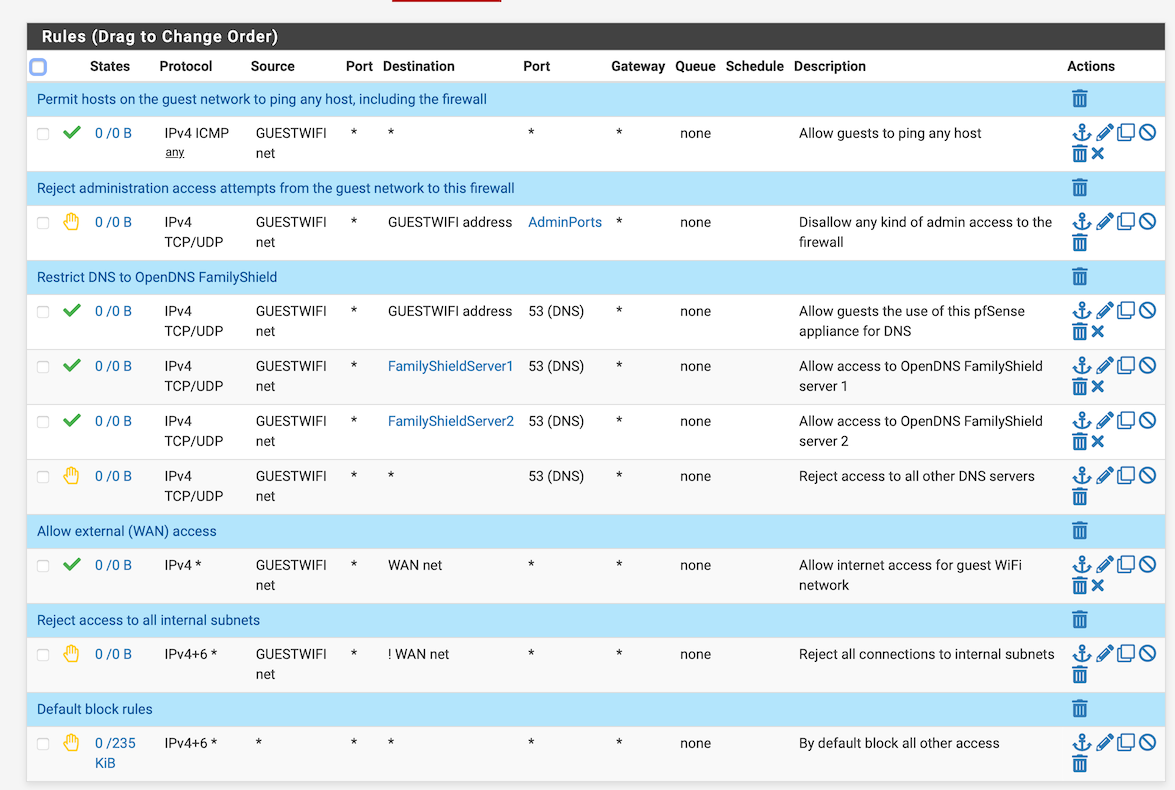
Do these look right?
-
@dominikhoffmann This Firewall is all IPs on all interfaces. This is important if, say, you are trying to block access to pfSense. Say you do something like:
block Guest to GuestIP:443
allow Guest to any...now you have allowed Guest to connect to LANIP:443. Looks like that's what you've done with your second rule. :) So a better block rule would be to block Guest to This Firewall:AdminPorts.
Also WAN Net is not "the Internet"...it is the WAN subnet, normally the WAN IP and its gateway, and maybe some nearby customers of your ISP.
A general "guest" ruleset would be something like:
allow Guest to GuestIP:53 (TCP and UDP)
allow Guest to GuestIP (ICMP, if you want to ping it)
block Guest to This Firewall (prevents 80/443/22/etc on any IP)
block Guest to LAN Net
(any other blocks)
allow Guest to any -
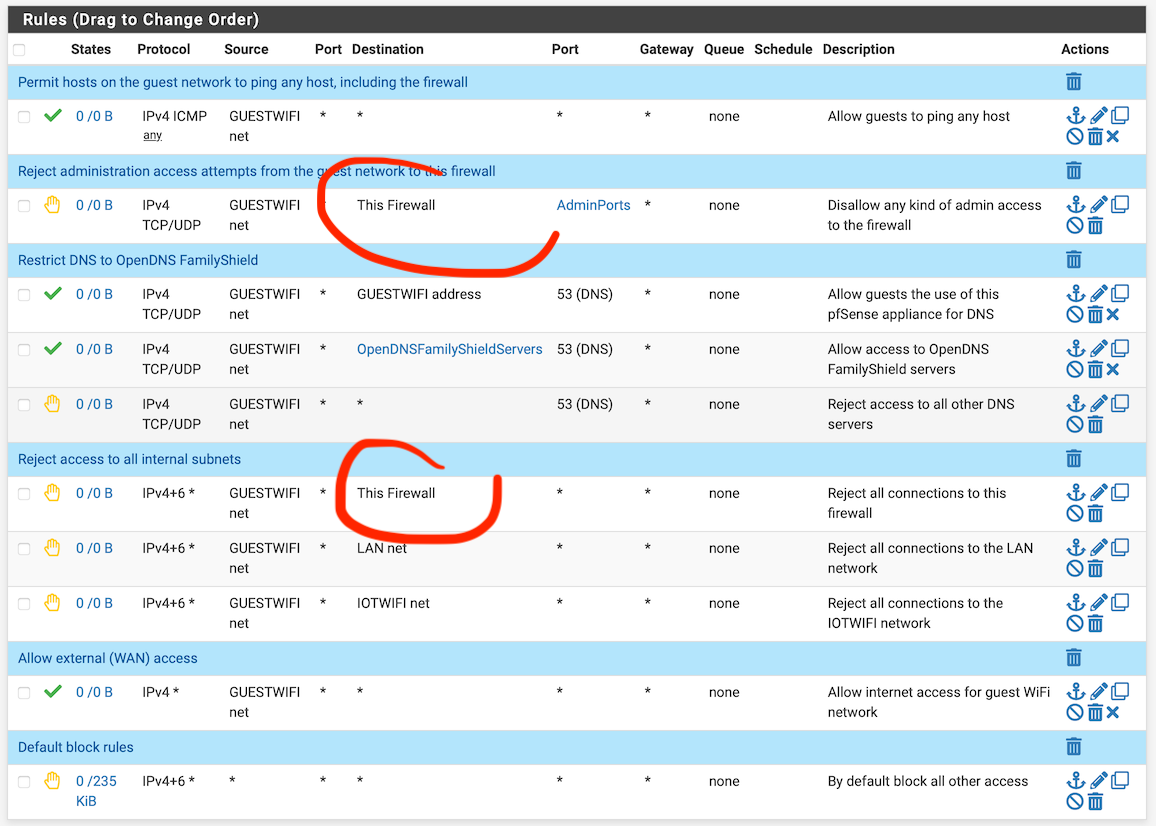
@steveits: Does this look better?
I wish, I could use an interface alias as the destination interface that would contain both LAN and IOTWIFI and any other interface to be created on that firewall in the future.
-
@dominikhoffmann Rule 2, and the other rule blocking access to the Guest interface IP, don’t block from Guest to the pfSense LAN or WAN or other interfaces. That’s where you should use This Firewall.
Re: future, that’s a common complaint especially for people with lots of VLANs or interfaces. Some people use an RFC1918 alias and then “!RFC1918” (Not RFC1918) to do the opposite though that syntax has had occasional bugs over the years IIRC. They also have note:
“Using Invert Match on <interface> Net macros such as LAN net can lead to undesired rule behavior when the interface also uses Virtual IP addresses. This is due to traffic matching against the interface network OR the VIPs. For example, given a Subnet of 192.168.1.0/24, a VIP of 10.0.0.1/32, and a rule with a negated interface macro such as pass on $LAN from any to ! $LAN_net, traffic destined to 192.168.1.100 will pass because the destination IP address does not match the VIP.” -
@dominikhoffmann said in Request for examples of working guest network rules:
I believe, I don’t quite understand the distinction. Would you mind explaining? I am still somewhat of a newbie.
"This firewall" would allow pinging to all interfaces. I allow pinging to only the VLAN interface that the guest WiFi connects to.
-
Is there a list of built in aliases anywhere? I looked in the pfSense book and didn't see one.
-
@steveits: Is this the change you are thinking I should make?
-
@dominikhoffmann said in Request for examples of working guest network rules:
@steveits: Is this the change you are thinking I should make?
Yes
-
@jknott RFC1918 is user created, just a lot of people use that name. Re default, I think it’s just This Firewall, interface IPs, and interface subnets.
-
I did like this:
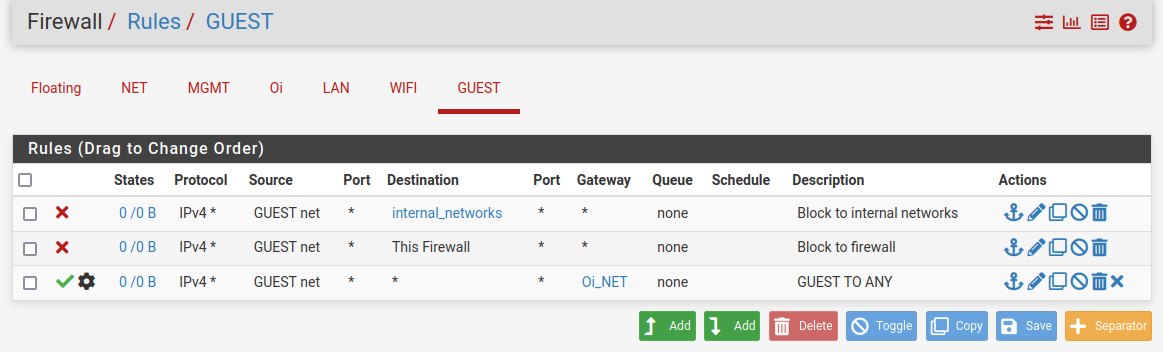
Internal networks contains all my subnets.
Just be sure to assign an external DNS to your GUEST subnet through DHCP and that is it. -
@mcury said in Request for examples of working guest network rules:
Internal networks contains all my subnets.
Is your “internal_networks” defined through Interfaces → Interface Groups? It must not be, because as far as I can tell you can’t use an interface group as a destination in a rule.
-
@dominikhoffmann Internal networks is a network alias.
Inside of it, I added all my internal networks.The second rule blocks to this firewall, so GUEST users can't access the firewall (if this rule didn't exist, GUEST users would be able to access pfsense GUI through my WAN IP, which is dynamic).
The third rule allows my users to go to the Internet, do everything they want, using a failover gateway group.
They use external DNS servers assigned by DHCP.
-
I know about user created aliases. I'm asking about aliases that are built into pfSense and available without having to create them.