Redesign pfBlockerNG to Run DNSBLs Using Unbound in Both Resolver and Forwarder Modes
-
@Gertjan, I came to the same conclusion as you did regarding the use of the DNSBL UT1_Adult. It is imprudent to try running it on anything but a very powerful computer. This is the reason I want to forward DNS queries to a "family" service that blocks adult content for me.
I would like to see your results when you forward DNS queries to Cloudflare's family servers, 1.1.1.3 and 1.0.0.3.
After making the proper changes, let me know if you can see porn sites such as xnxx.com and xvideos.com while using Unbound in the forwarding mode.
I can't get this to work on my Netgate 1100 running the latest software versions using Unbound in the forwarding mode. However, it does work correctly using DNSmasq.
-
@mpfrench said in Redesign pfBlockerNG to Run DNSBLs Using Unbound in Both Resolver and Forwarder Modes:
Steve, if you would please, set your forwarded DNS to 1.1.1.3 and 1.0.0.3. Then try to browse to xnxx.com and xvideos.com. If you can see those sites, your system is NOT using those two DNS servers.
It returns 0.0.0.0 which is also what I get if I query them directly. Ensure there are no other servers listed on your System/General tab?
As above, you're testing with nslookup or dig, and not a browser?
-
@SteveITS , you did not answer the question I asked. Did you see the content of the sites xnxx.com and xvideos.com when you browsed to them after using 1.1.1.3 and 1.0.0.3?
You asked about my DNS settings. Here they are:
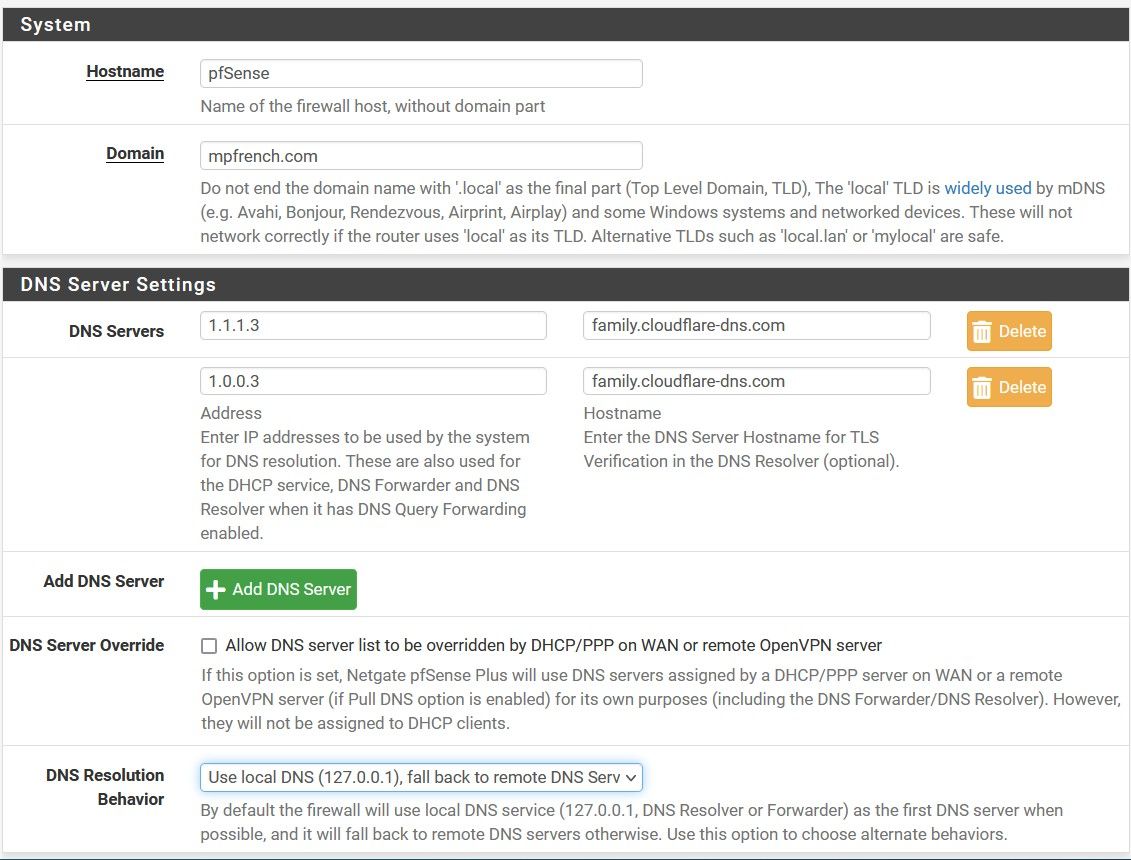
Thanks for your help.
Mike -
@mpfrench I did not test a web browser; I was using our office router.
If nslookup returns 0.0.0.0 and your web browser is connecting anyway, then either:
- your PC has cached the result
- your PC has a DNS server configured besides pfSense
- your browser is using DNS over HTTPS and bypassing your local DNS
For the former, restart the DNS Cache service in Windows. For the latter, block DoH via the pfSense doc at https://github.com/jpgpi250/piholemanual.
-
@mpfrench said in Redesign pfBlockerNG to Run DNSBLs Using Unbound in Both Resolver and Forwarder Modes:
I would like to see your results when you forward DNS queries to Cloudflare's family servers, 1.1.1.3 and 1.0.0.3.
I can't.
1113 and 1003 filters without my control.
I've a company (hotel) to run with my connection. Not a bunch of curious kids ;)
And I've nothing against p0rn sites. It's that, or reeving strange ladies at the reception
But I don't doubt about the fact that 1113 and 1003 work well.
-
@Gertjan , @SteveITS , thanks to both for your help.
I've run some more tests which may shed some light on the root cause of my not being able to get Unbound to forward instead of resolve.
Using DNSmasq [Services - DNS Forwarder], NSLOOKUP returns 0.0.0.0 for both xnxx.com and xvideos.com. A web browser refuses to show both sites.
Using Unbound [Services - DNS Resolver], I get two different responses from NSLOOKUP.
For xnxx.com, I get 10.10.10.1 and a browser shows the pfB blocking message screen. Evidently, that site is in a DNSBL other than UT1_Adult which is not enabled on my system.
For xvideos.com, NSLOOKUP delivers the message "can't find xvideos.com: Server failed." However, a web browser actually shows the site.
When performing NSLOOKUP xnxx.com 1.1.1.3 and NSLOOKUP xvideos.com 1.1.1.3, I get the answer returned 0.0.0.0 for both.
This is proof that Unbound did not forward the DNS query to 1.1.1.3 or 1.0.0.3 per my setup settings.
I hate to give up on Unbound since the DNSBLs work with it and do not work with DNSmasq, but Unbound just isn't forwarding as it should and I'm not sure why. It appears to be a bug.
In the mean time, I'll use DNSmasq and forgo DNSBL filtering since DNSmasq forwards correctly.
-
@mpfrench said in Redesign pfBlockerNG to Run DNSBLs Using Unbound in Both Resolver and Forwarder Modes:
This is proof that Unbound did not forward the DNS query
As I've asked above did you block DoH? Because most web browsers use DoH now. Other than the browser it sounds like the DNS block is working.
re: the failed query also check if you have DNS over TLS enabled, and uncheck that. (https://forum.netgate.com/topic/178413/major-dns-bug-23-01-with-quad9-on-ssl)
-
(drums fingers) Realizing what I'm writing, it seems like a browser using DoH would use it regardless of the DNS setup on pfSense. But, it is expected nowadays that browsers do use it and go around DNS, notably Firefox. If the problem here is that DoH is being used for DNS Resolver and not DNS Forwarder that isn't normal as the browser shouldn't know the configuration on the router.
-
@SteveITS , DoH was never a cause of my problem. I made sure the browser with which I tested did not have DoH enabled.
After, meticulously reviewing every DNS setting in pfB and pfSense, rebooting everything (Netgate 1100, router, computer), and issuing a flushDNS command between every test, I think I've gotten Unbound to work as a forwarder to my "family" DNS servers, 1.1.1.3, and 1.0.0.3.
Now NSLOOKUP returns 10.10.10.1 for xnxx.com and the browser shows the pfB blocking screen, indicating that xnxx.com is on the UT1_Redirector blocking list.
NSLOOKUP returns 0.0.0.0 for xvideos.com and the browser shows the "Try again Charlie" screen.
I think the Enable DNSSEC option was interfering with Unbound's proper operation. I'm currently running without DNSSEC enabled.
I also think I was having an issue with the DNS cache not being flushed between tests which I corrected.
So far, the teenagers in my house have not figured out what DoH is good for, but if they do, it would seem that I could set pfB to block the exact web sites DoH uses. But I'll cross this bridge when I need to -- another day.
I appreciate your help. I think it is safe to close this topic.
Mike -
@mpfrench said in Redesign pfBlockerNG to Run DNSBLs Using Unbound in Both Resolver and Forwarder Modes:
and the browser shows the "Try again Charlie" screen.
They won't. They'll understand.
They have Google. They will do what you would do.
.... 5 minutes later ....
They stop using 'your network', and take another one, like a SIM 4G/5G data card from their phone.
Case 'solved'.I say this because " I've been there - seen it - thought I needed to do something with a tool ".
All you can do is explaining, and showing the right example.
It has been written somewhere : everybody has the right to dig its own hole, and then fall into it.
I bought a rope, so I can help, if asked or needed ;)