Site-to-Site OpenVPN only works for a short time after factory reset + reconfigure
-
And it happen again after a few days.....
-
@nazelus said in No Site-to-Site VPN after upgrading CE from 2.6.0 to 2.7.0:
And it happen again after a few days.....
Reset Factory default on all Server and Client without backup config
For a few days prob is back again suddenly, Client and PC behind can ping and connect anything to server. Server can ping to client but None of the PC behind server can ping and connect to client. -
I'm So Done with this, I'll Rollback to 2.6 and update everyone later if it working or not.
If Netgate not clarify anything about this mean i wont be able to upgrade and might have to throw away 1000$ netgate box and move to something else.
that box is the way I showing respect to Netgate team and i really hope i dont waste it. -
@nazelus said in No Site-to-Site VPN after upgrading CE from 2.6.0 to 2.7.0:
I'm So Done with this, I'll Rollback to 2.6 and update everyone later if it working or not.
If Netgate not clarify anything about this mean i wont be able to upgrade and might have to throw away 1000$ netgate box and move to something else.
that box is the way I showing respect to Netgate team and i really hope i dont waste it.If something worked and then stopped, and then worked again after a factory reset, it's still probably something in your settings. Not much changes dynamically like that, but if something messes with your routing after some kind of event (e.g. WAN failure/DHCP renew, VPN disconnect/reconnect) then it's most likely something else that needs set right to recover properly, or an invalid setting that only becomes apparent later.
That's not the same as OPs problem, though. So far no two people in this thread have had the same problem, each of these should really be separate threads, it's getting very confusing to follow.
-
@jimp said in No Site-to-Site VPN after upgrading CE from 2.6.0 to 2.7.0:
And so far I haven't seen anyone that has followed my troubleshooting suggestions from earlier in the thread:
Please. I even did this before you've told. these information and solution are available via netgate documents and i've go through all of them repeat for a week now.
I can't roll thing back right now due to its a working day, i'll Plan to do it later ASAP
I've been using PFsense MORE THAN 10 years. Everything seem to work last weekend and it just start to not work on the Monday morning.
Its something trigger some other thing here and everything really look normal all the route are there and etc.
I can even ping some behind the box some time and then a hour later it gone!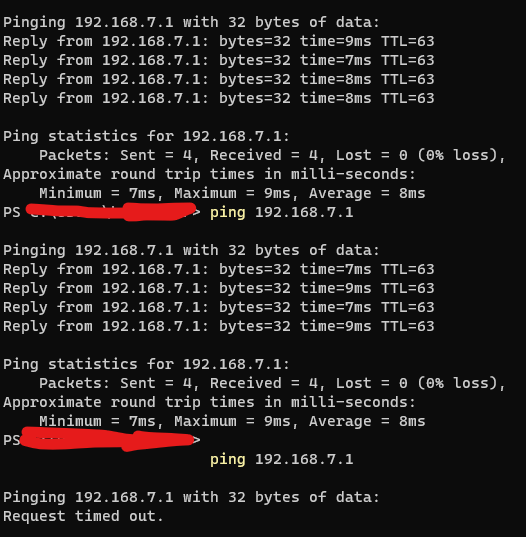
It Really Frustrating.If you need any information Please just ask and i'll provide them if you willing to help.
-
If you have an ongoing case with TAC then you can keep handling it there -- again your situation is not the same as the OP and mixing your info in here is only leading to confusion. The thread is already huge and trying to track multiple different problems and conversations is only resulting in frustration to all involved.
If you are submitting info via TAC, take a status report (from
/status.phpin the GUI) while trying to ping both when it works and again when it doesn't work, and submit both to TAC. The differences in the status report should reveal what is happening in your case. We don't suggest posting those publicly in forum threads because of the potential for sensitive info inside, but TAC is private so those concerns do not apply there. -
I forked this off into a new thread so it would all be together since it's likely a different issue than the post it was on before.
Something else I thought of that might kick in after it's been running a while is that it may have downloaded a bogons update. A fresh install may not have bogons content yet, and then if any of your interfaces have "Block bogon networks" enabled that may kick in later once the firewall downloads the bogons data. Similar results may come about from packages like pfBlocker or snort downloading updates.
But I still think comparing the contents of the status output when it works vs when it doesn't work would be the most helpful.
I asked TAC about your case but they didn't see anything under this name, but that would make sense if your account isn't using the same name/alias/e-mail as the forum.
-
FYI, Just To update you to know that i seem to able to find all the reason behind this now but i need a few more test to confirm and will get back to you later this week.
-
After keep on going research for the issue I found some topic that Jimp Mention to someone with some other issue that they should try to lock the package and only send them to destinated location only.
My issue seem to be the to be this behaveWith 2.6
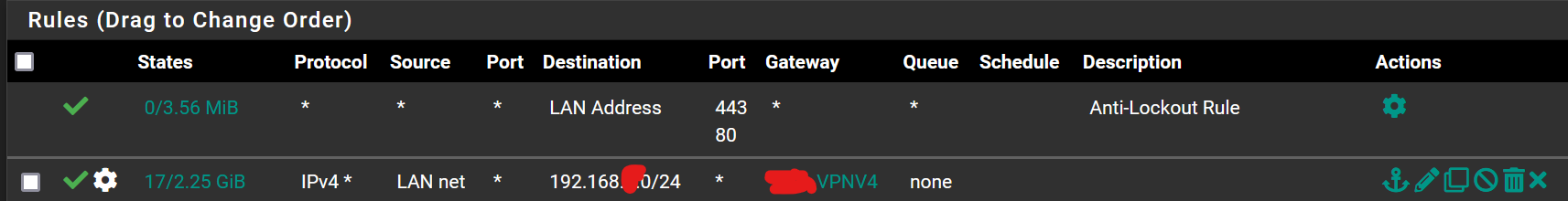
Source Lan Net >> Destination Address >> Any available gateway that is correct automatic = Result is a pingBut 2.7
Source Lan Net >> Destination Address >> Any available gateway that is available automatic = Result is not able to pingI Got Multi Wan and Multi Lan here so that is the reason that the package was send out to wrong interface gateway.
I'm not found any document of these available in Netgate but found them in some Youtube channel, It is to create Interface Gateway from VPN so i did Create a Gateway by adding VPN interface on both side But still not able to ping.
After i read Jimp comment so i adapt it to my use bySource Lan Net >> Destination VPN Lan Net >> Force to use VPN Gateway
and keep this on Top of any Rule from both client and server siteAnd Yet, Everything is Work again like 2.6 now
I'm not sure anyone else will have the same issue as i did or not since we have a bit complicated setup here with 4 VPN server for 4 client with Site to Site Setup and Remote for Client connection Plus 2 Wireguard Gateway Interface.
Thank you and Kind Regard
-
@nazelus Could you please be so kind to add a screenshot showing where you made the key changes? In how far is outbound NAT involved? Which network are the firewall rules in question assigned to - source LAN net?
-
@michaelschefczyk
I Did not touch any NAT Here.- Simply add a Interface gate way from the Interface Assignments Menu first and add Then Select and add a VPN, Enable it without any setting here you will get a new Gateway.
- At Firewall Rule from your LAN, Add a new rule with S: Lan Net > D: Network VPN Address >> Specific VPN Gateway from first step.