Cannot connect with RDP via openVPN
-
How can I have secondary LAN other than existing one?
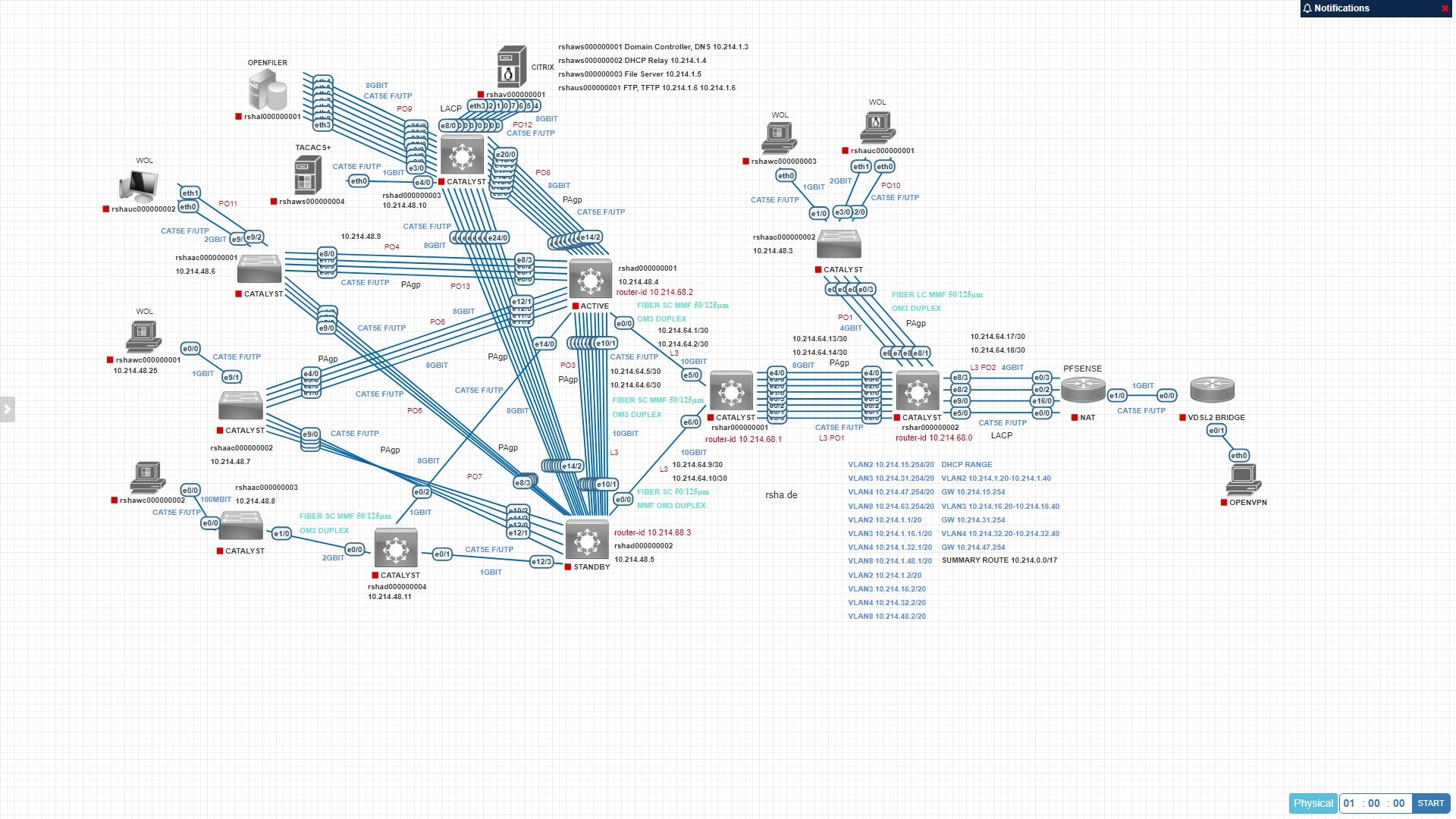
The LAGG is currently configured into OPT with an IP 10.216.64.21/30, the port channel works, can ping but I don't know yet if it connects to the internet over the portchannel.
Can you explain further what I must do?
Thank you,
-
@IrixOS use another interface.. that your not going to put into the lagg.. Are you saying you only have 2 interfaces and you want both of them in the lagg?
As to secondary lan? I have 6 different interfaces I could config it from.. How many interfaces does the device your running pfsense have? Or as mentioned as well come in from the wan interface if you don't have any other lan side interfaces that you don't want in the lagg.
-
igc0 -> WAN (ppoe)
igc1-> LAN (10.216.64.16/30 subnet)
igc2,igc3 -> LAGG -
@IrixOS so connect on your wan igc0 ? This isn't rocket science..
-
Yes? Why?
I know this is not rocket science, the manual says, shuffle around and I did that and it didn't work. First the speak of a free port, then they come up with the LAN interface who is already assigned,...
I want to get over with this, because the most interesting part is yet to come, that is the internal cisco traffic and programming.
There is still over 10 cisco port channels to configure, it is straightforward, but that pfsense stuff is not painless.Yes, igc0 is the WAN port connected with a VDSL2 modem in bridged mode.
I tried to find what you mentioned another LAN, couldn't find or how to create it.
I want the port channel to get working first.
Can you say exactly what I must do?
-
@IrixOS connect via your wan interface.. Setup your lagg how you want it, validate its working.. Then reconnect your wan to your internet connection..
If you want put a switch between your wan and your isp device.. Put your laptop on some IP your wan is on.. etc..
Another option, add another nic - if you have no slots for one - use a usb nic, use that to connect to pfsense so you can setup your lagg..
-
The ip addressing is not correct but that's not the problem.
Have look at L3 PO2 near the pfsense router, assume one link of the four is the LAN link /30 subnet (10.216.64.17) on the switch and 10.216.64.18 is the interface, the LAN of the pfsense router. (The schema respresents 4 links, in reality it is three, because one is for the WAN connection to the modem so minus -1 is three, well I want all of three (includes the LAN) or at least two links to be part of the lagg0.
-
@IrixOS none of your routing or how crazy your network is makes any matter..
Connect into the pfsense box on an interface your not putting into the lagg.. Make sure your lagg is up, put your networks you want over lagg on the lagg.. If you need to add an interface, even if usbnic to set it up.. Then do that..
Not sure what else to tell you? But trying to setup a lagg on an interface your wanting to add to the lagg could be problematic if your lagg isn't coming up.. So use another interface.. Either come in over your wan, you might have to take down the wan for internet while you do that, or just use another interface.. If you don't have one - then add one..
-
@IrixOS this has your certificate listed you should delete the post with the SSL certificate information that can be copied and pasted into something
-
@JonathanLee you mean the ones I already snipped big chunks out already, see where it says <snipped by mod> to make that info useless.
-
In this discussion post please blank this out, it is the ssl certificate, bad guys can manually copy that info.
@IrixOS said in Cannot connect with RDP via openVPN:
persist-tun
persist-key
cipher AES-128-CBC
ncp-ciphers AES-256-GCM:AES-128-GCM
auth SHA1
tls-client
client
remote rshafw000000001.ddns.net 1194 udp
verify-x509-name "www.rsha.de" name
auth-user-pass
remote-cert-tls server
compress lz4-v2<ca>
-----BEGIN CERTIFICATE---
Blank this out for please
-----END CERTIFICATE-----
</ca>
<cert>
-----BEGIN CERTIFICATE-----
blank this out please
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY——-
blank this out please
-----END PRIVATE KEY-----
</key>
<tls-auth>2048 bit OpenVPN static key
-----BEGIN OpenVPN Static key V1-----
blank this out please
-----END OpenVPN Static key V1-----
</tls-auth>
key-direction 1 -
@JonathanLee dude I rendered that info useless when he first posted it.. I snipped out big chunks of the data.. All that is there now is what amounts to random characters.
-
@johnpoz I didn't notice, I just saw SSL cert and I thought Nooooooooooooooooo don't post it

-
yeah, I have already been criticized for that, I don't think they are no valid no more, got a new box, what do you think? I will delete them later on.
-
I think I know what you mean, I have four ports in total, one for WAN, one for LAN and two free ports that I want to add to LAN in lagg, but there is no more port free, because I want all three to be part of the lagg so the manual says you can do it via VPN, so you have to configure the internal kitchen from the outside?
 That's the most stupid thing I ever heard in my entire life.
That's the most stupid thing I ever heard in my entire life. -
@IrixOS
Set up Lag on 2 of the 3 Lan NIC by connecting your laptop to the third NIC. Then- Unplug your router
- connect a laptop to your routers lan NIC to set the WAN physical port to temporary pfsense GUI access
- Connect your laptop to the routers WAN NIC
- Configure lagg on the 3 LAN physical NICs
- Connect your switch to the 3 LAN NICs now in lagg
- Connect your laptop to pfsence via your new lagg connected LAN interface
- Revet the WAN settings
- Plug back in your WAN
-
Forum doesn't allow me to delete my own posts.
Anyways thx for stripping the certificate. -
@Patch said in Cannot connect with RDP via openVPN:
to set the WAN physical port to temporary pfsense GUI access
'to set the WAN physical port to temporary pfsense GUI access'
How do you set that? In Firewall rules?
-
@IrixOS yes
There is a default anti lockout rule created for the first LAN. To access the pfsense gui from any other interface you need to add the firearm rule to allow it -
@Patch said in Cannot connect with RDP via openVPN:
To access the pfsense gui from any other interface you need to add the firearm rule to allow it
Lets clarify that a bit, if your rules on your other interface blocked access to the firewall specifically then yeah you would need to add an allow rule.. But if you just put say a any any rule on it, you would be able to access the gui.
Now the wan is a bit different.. Out of the box there are no rules, and most users unless they wanted to do some sort of port forward would never even need any rules on wan. It also defaults to blocking rfc1918 source, and bogon as a source.. If your going to use your wan to admin it, from rfc1918 you would need to disable that rfc1918 rule, and create an allow rule.
The only time "wan" defaults to allowing access is when pfsense is first setup and there is only the WAN interface setup.. If you then later setup lan then that allow rule is removed..
On a bit of side note - users wanting to block access to the web gui should prob use the "this firewall" alias because if they allow any any for internet, they prob forget about the pfsense public IP that would be allowed by a any any rule on some opt interface.. So blocking the pfsense gui ports using the "this firewall" alias makes sure clients can not get to any IP of pfsense, even though other rules below it might allow that, etc.